Overview
The NOVI University Of Applied Sciences is offering an Advent CTF challenge for December 2020. The CTF is created by our community member of the Hackdewereld.nl and Chief Lecturer for Cyber Security at the NOVI University, Arjen Wiersma. If you want to participate in these CTF challenges, you can create an account on the website https://www.adventofctf.com/.
Challenge 3
- Description: For this challenge you will, again, need to bypass the login mechanism.
- 300 points
As always, I visited the URL of the challenge: https://03.adventofctf.com, and again I’m landing on a web page with a login form. Not so surprising because the challenge description already talked about bypassing the login.
The is (again) a message visible, that I do not try too hard. As I know, in that case, you have to read the source code. So, let’s read the source code.
In the source code, I see a reference to a Javascript file, named login.js. I checked this file, and the contents show how the username and password combination for the authentication.
1
2
3
4
5
6
7
8
9
10
11
12
13
function checkPass()
{
var username = document.getElementById('username').value;
var password = document.getElementById('password').value;
var novi = '-NOVI';
if (password == btoa(username + novi)) {
window.setTimeout(function() {
window.location.assign('inde' + 'x.php?username='+ username +'&password=' + password);
}, 500);
}
}
The username is being read from the HTML element with the ID username. This means that there is no database lookup and I can use every username I want. The second part shows that the password is a combination of the username and the -NOVI string. This string is being stored in the variable novi. This combination needs to be passed to the password field as a base64 encoded password. Because btoa means that the value needs to be encoded. So, for successful authentication. My username and password are as follows:
1
2
username = username
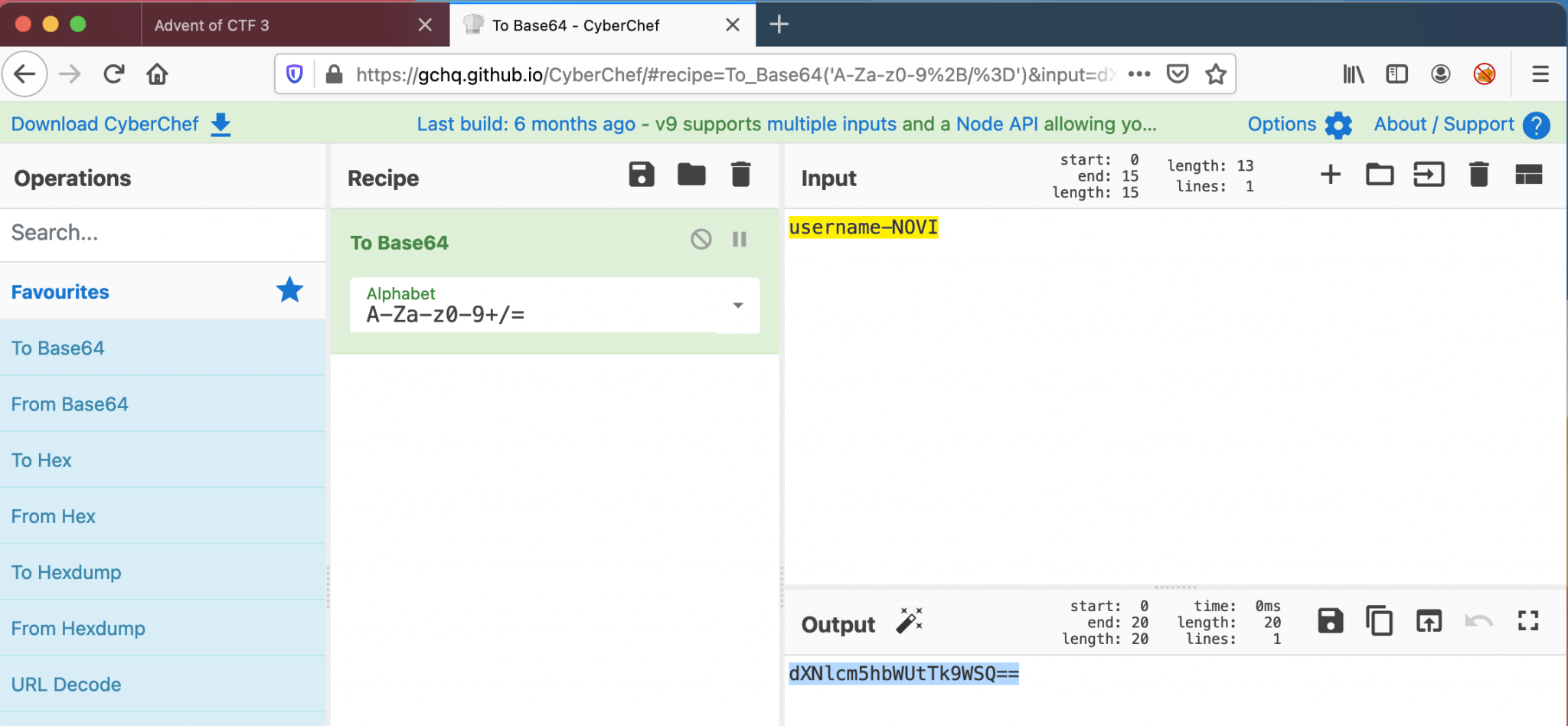
password = dXNlcm5hbWUtTk9WSQ== (username-NOVI)
I used CyberChef to encode the password to a base64 string.
Now, I can use this username and password combination to authenticate on the login form. After the authentication I’m able to read the flag: NOVI{javascript_is_not_s@fe}.
Thanks for reading!