Overview
The NOVI University Of Applied Sciences is offering an Advent CTF challenge for December 2020. The CTF is created by our community member of the Hackdewereld.nl and Chief Lecturer for Cyber Security at the NOVI University, Arjen Wiersma. If you want to participate in these CTF challenges, you can create an account on the website https://www.adventofctf.com/.
Challenge 11
- Description: Santa’s book of secrets has upgraded its security. All should be fine now. The flag is in flag.php.
- Points 1100
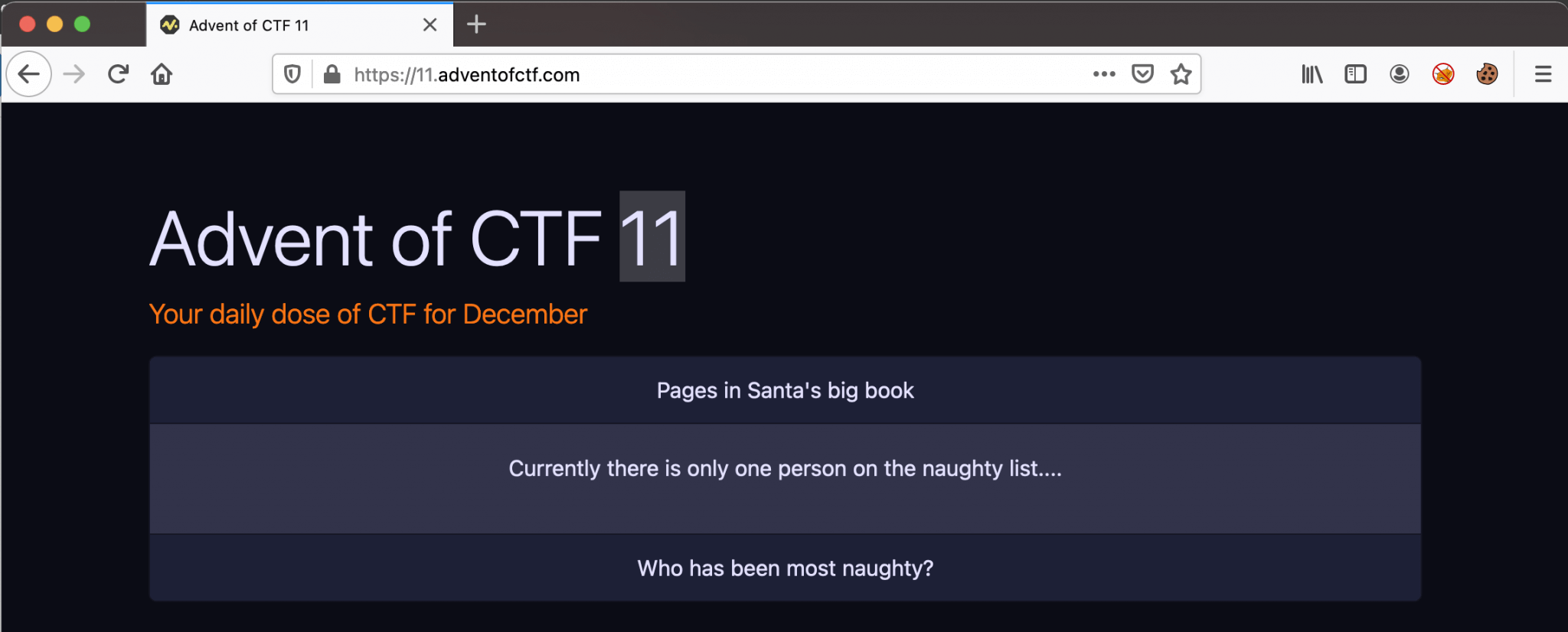
Let’s start with the challenge! As always we first go to the challenge website, we navigate to the URL https://11.adventofctf.com. We are landing on the Pages in Santa's big book website. This page has a message for us: Currently there is only one person on the naughty list.....
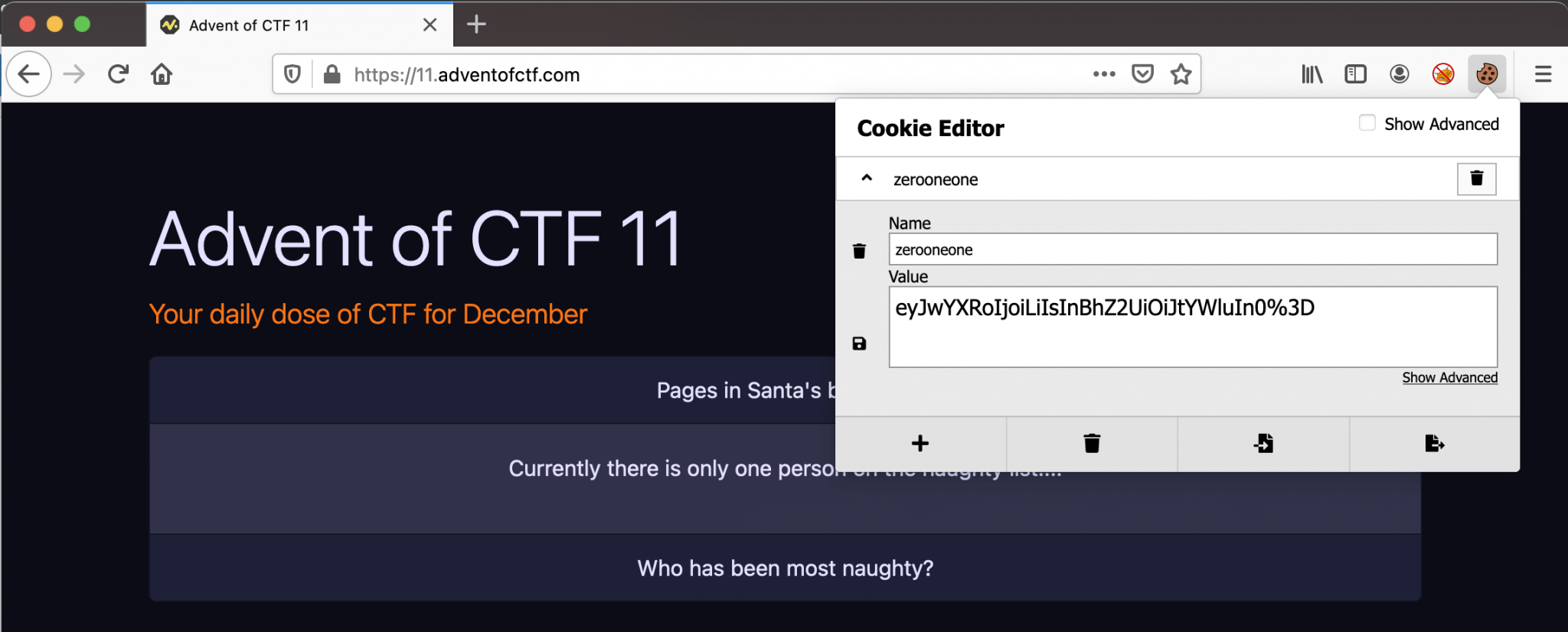
The challenge is to find who has been most naughty. Well, this is exactly the same website as the previous challenge, Advent of CTF Challenge 10. In that challenge, we modified the cookie to a specific value to see the content of the flag. So, first, we will check our current cookie in the browser.
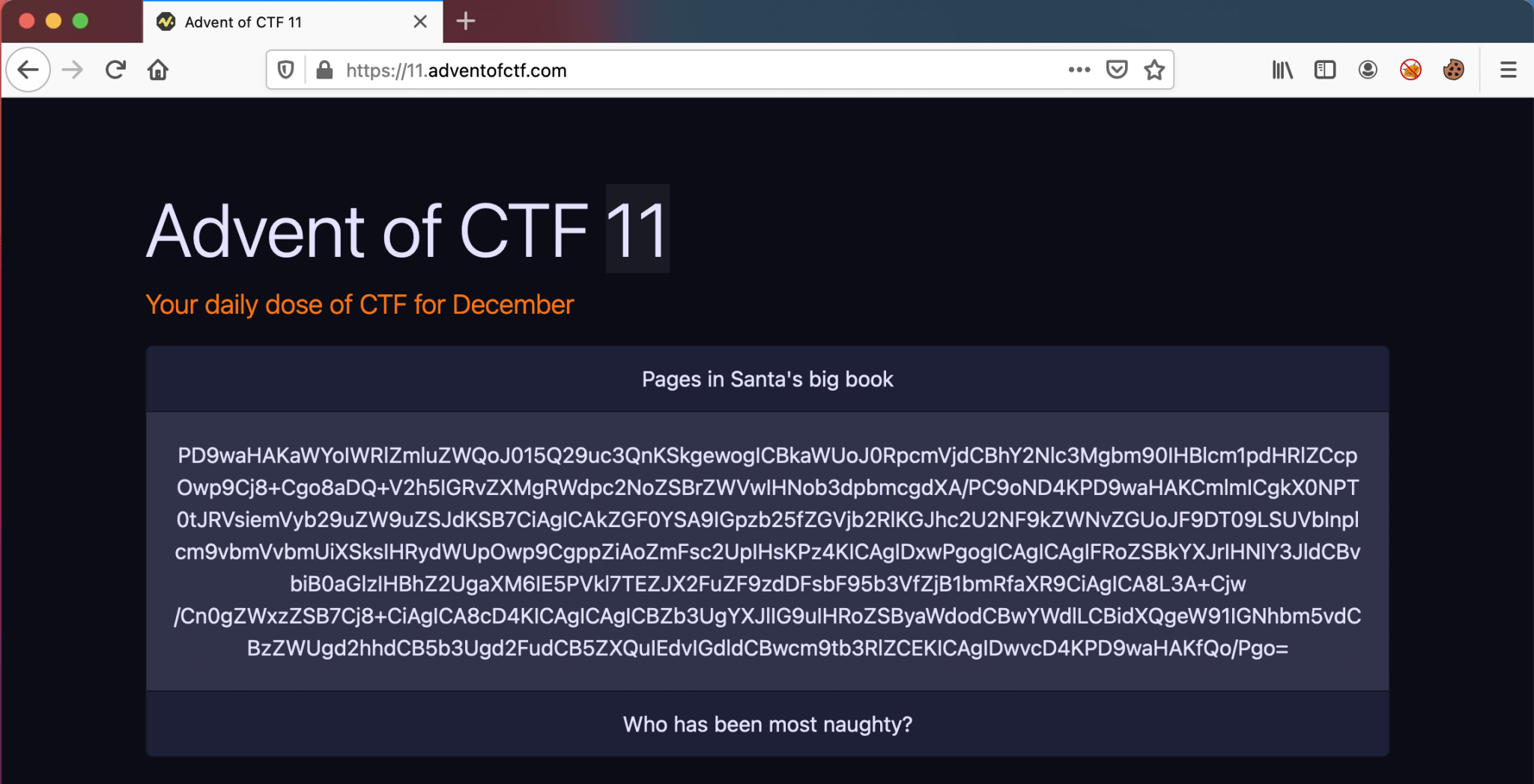
The name of the cookie zerooneone looks a lot like the cookie name of the previous challenge. We got a Base64-encoded cookie value eyJwYXRoIjoiLiIsInBhZ2UiOiJtYWluIn0%3D. With the use of CyberChef, we can decode this cookie, and we got this value inside the Base64-encoded part.
{"path":".","page":"main"}
We got again a cookie value in a JSON format. The first element of this cookie is defining a`` and the second one the page.
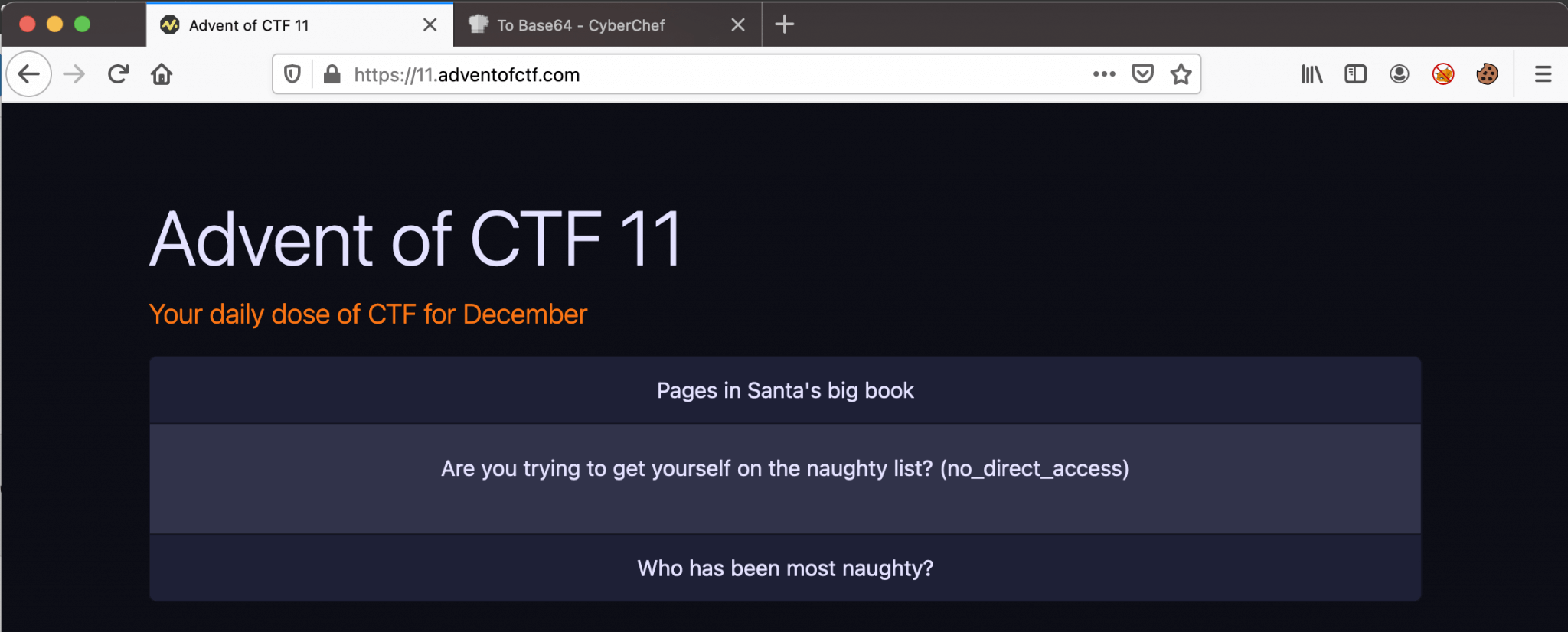
We need to understand how these elements in the cookie work together. Let’s change the page element from``` to flag, because we want to see the page which is holding the flag. After changing the cookie with the new Base64-encoded value, I got a new message on the webpage: Are you trying to get yourself on the naughty list? (no_direct_access).
Next, we can change the path, to perform a path traversal attack through the cookie. We can change the cookie to this value and maybe we can grab the flag.
{"path":"../../../../../","page":"flag.php"}
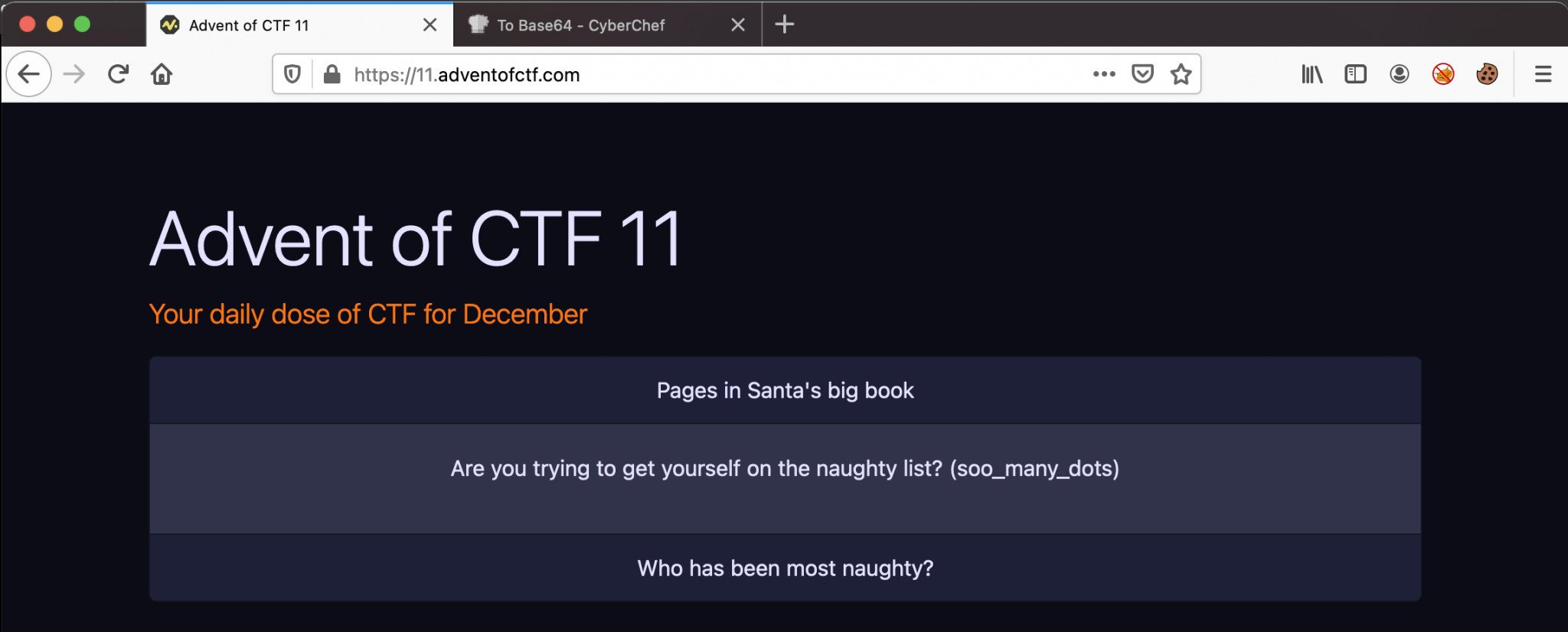
Again, the page is changing with a new message: soo_many_dots.
From this page, we have to do some investigation on the internet. Through this write-up on Medium, we can learn the solution to solve this challenge. As this website is detecting the ../, we need to replace our current payload with a new one. The write-up is talking about the technique PHP-wrapper.
Solution
We first can try this payload:
{"path":"php://filter/convert.base64-encode/resource=","page":"flag"}
Again, the webpage is changing and now we got a blacklist message on our screen.
It seems that some values in the cookie elements are not allowed. After trying and changing the cookie multiple times, we found that we are able to read the flag with this cookie value:
{"path":"php://filter/","page":"convert.base64-encode/resource=flag"}
Of course, every time you need to base64-encode the cookie and replace your current cookie with it. We are now able to read the flag.
After decoding this Base64-encoded content, we got the flag: NOVI{LFI_and_st1ll_you_f0und_it}.
Thanks for reading!