Overview
The NOVI University Of Applied Sciences is offering an Advent CTF challenge for December 2020. The CTF is created by our community member of the Hackdewereld.nl and Chief Lecturer for Cyber Security at the NOVI University, Arjen Wiersma. If you want to participate in these CTF challenges, you can create an account on the website https://www.adventofctf.com/.
Challenge 12
- Description: To ensure a good Christmas we implemented some diagnostic tools. This one checks that the time to a destination is within an acceptable range. The flag is in /flag.txt.
- 1200 Points.
Well, this challenge was very hard for me. It has taken me some hours to resolve this one. I was diving in a rabbit hole and it was difficult for me to get out. But, after some time I managed to solve this challenge. And, I’ve learned something from it and that’s my reason to participate in the CTF challenges. Without further redo, let’s get to work.
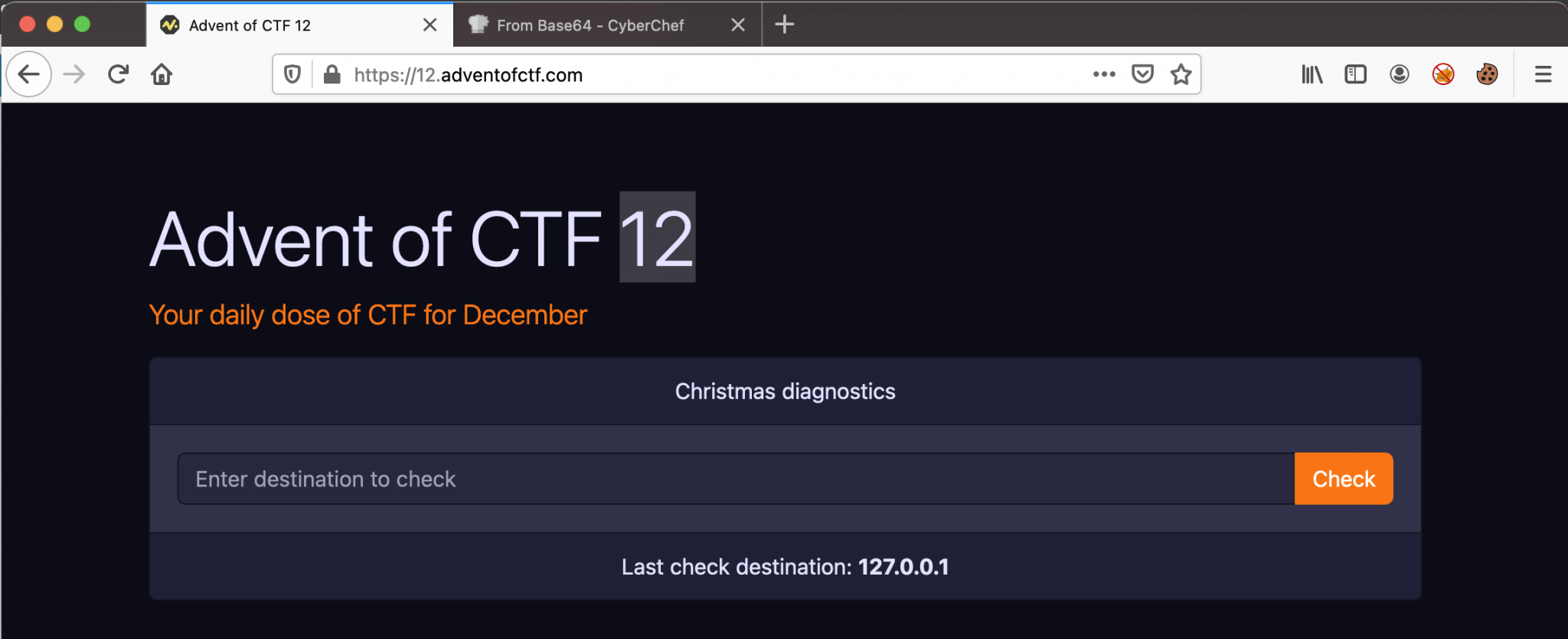
Let’s visit the challenge URL: https://12.adventofctf.com, and we got ended up on this webpage.
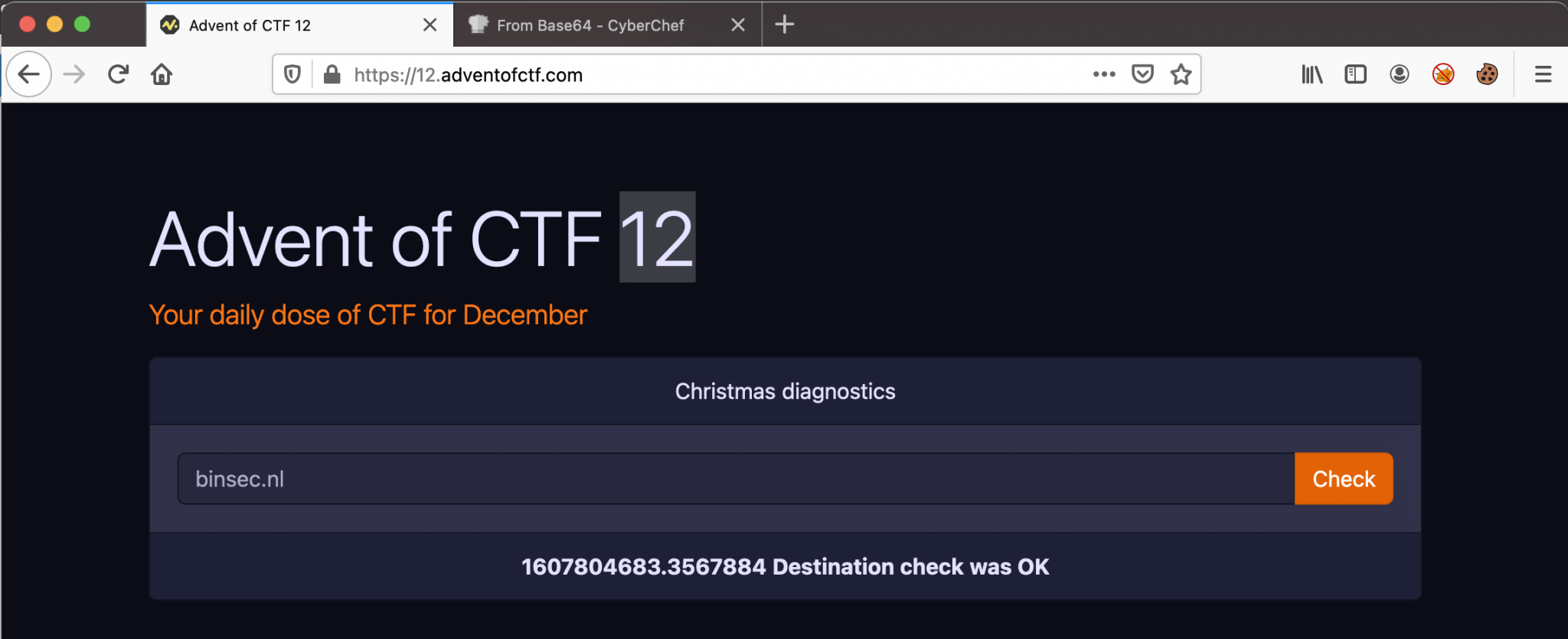
As we can see, we can enter a destination to check. I’ve filled in my own domain binsec.nl. Let’s see what’s happening, and there is some output. Some numbers, which are representing the resolve time? And that the destination is reachable.
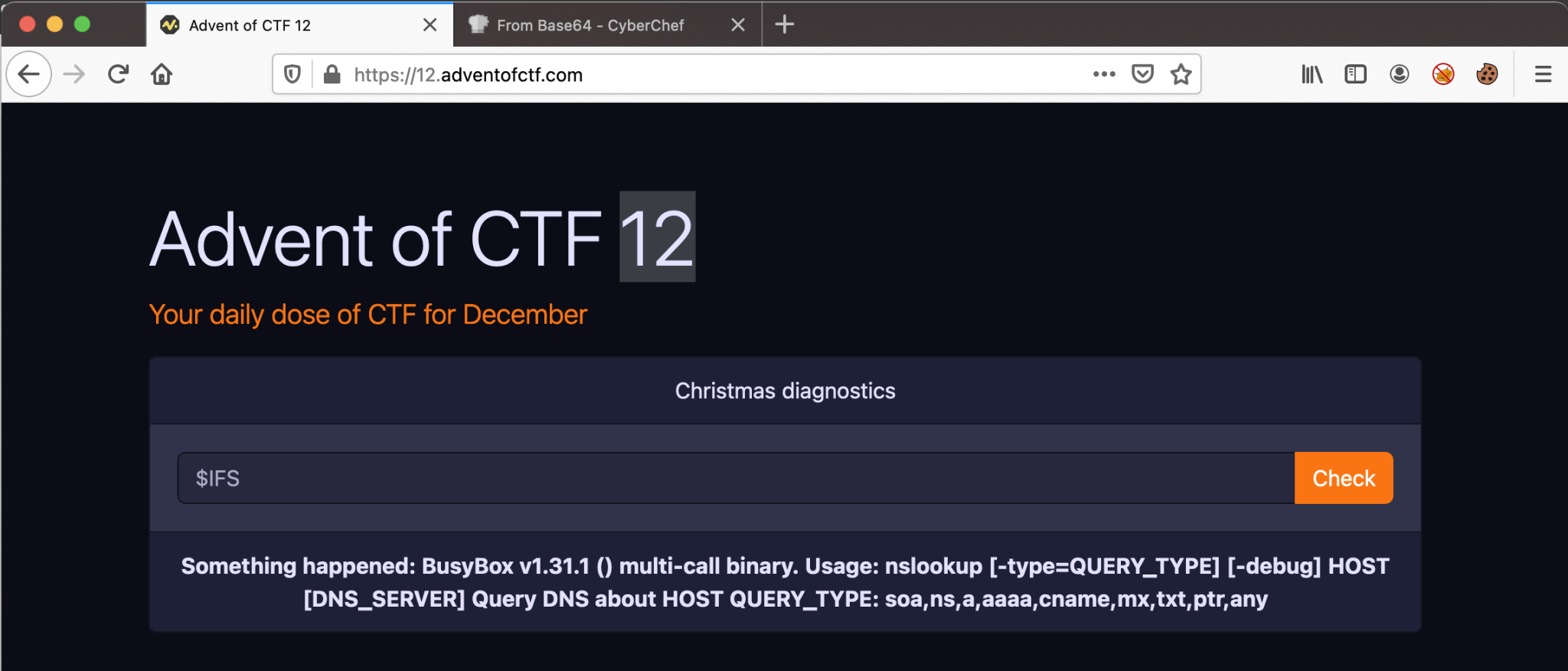
Well, I think that the time is not relevant to this challenge. Let’s add a special character to the website and let’s see how the back-end is acting. For some reason, most times, I’m using the IFS special shell variable for testing, I do not know why, it’s just my way of working.
As we can see, Where are currently in the BusyBox and the input is sent as a variable to nslookup. From this point, I got stuck for a long time. I was searching for vulnerabilities for BusyBox and nslookup, because I thought in the first place I need to break out of a restricted shell or something. It turned out that I was thinking very hard. After a while, the creator of the CTF challenge came up with two hints to come to the solution.
The two hints from the CTF creator in Twitter
Hint: do you know stderr is a device on Linux?
— adventofctf (@adventofctf) December 12, 2020
After these hints I totally lost it and started to find out exactly what stderr means.
Stdin, stdout and stderr on Linux
For Linux (and Unix) operating systems, are stdin, stdout and stderr are three standard streams that are being established after a command is executed. With a stream, we mean that data is being transferred, from one place to another. By a command execution, the data is in text. In Linux stdin is the standard input stream, it accepts text as input. The output of the command got’s delivered via the stdout (standard out) stream. Error messages from the command are sent through the stderr (standard error) stream. So as you can see, there are two output streams, stdout and stderr, and one input stream, stdin. This makes sense, right?
Now it gets interesting because now we come back to the challenge. The streams are handled if they are files. We can read content from files and we can write content to files. Well, the second hint is to point us to a device. Devices in Linux are located in the /dev directory.
Solution
Ok, now we can put things together. I know, it sounds easier than it is. Because with this knowledge, I now know that I only see the stderr stream. We have to send the output of the flag to this stream. As we know, from the challenge description, the flag is located in /flag.txt.
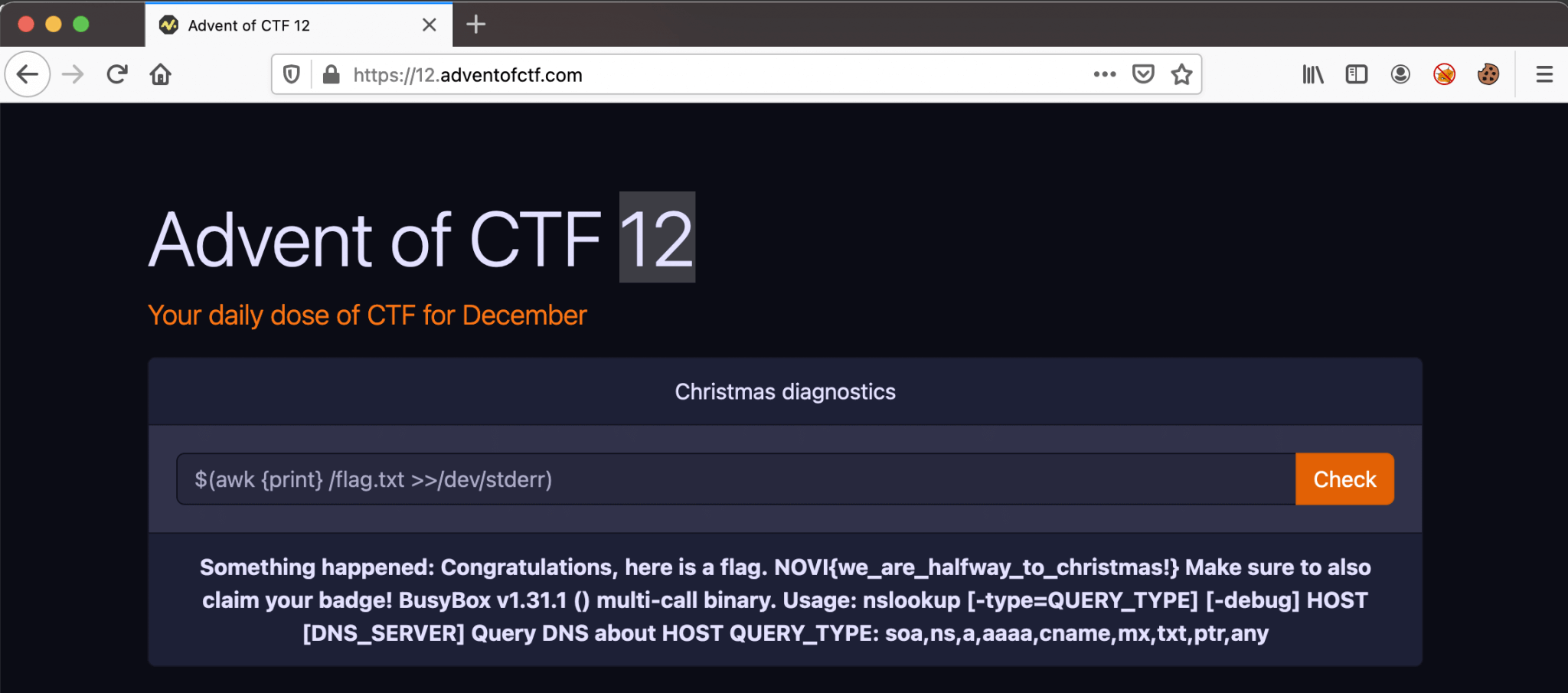
After some trying, I managed to read the flag with this payload:
$(awk {print} /flag.txt >>/dev/stderr)
The flag: NOVI{we_are_halfway_to_christmas!}.
I’ve reached out to the community and asked how they managed to solve this challenge. And I’ve learned I had could it done it witan easier payload, like this:
$(cat /flag.txt > /dev/stderr)
Or done it with Burp Suite 🙂
Thanks for reading!!