Overview
The NOVI University Of Applied Sciences is offering an Advent CTF challenge for December 2020. The CTF is created by our community member of the Hackdewereld.nl and Chief Lecturer for Cyber Security at the NOVI University, Arjen Wiersma. If you want to participate in these CTF challenges, you can create an account on the website https://www.adventofctf.com/.
Challenge 22
- Description: We have a new service! You can view santa’s favorite pictures. Currently there is only one, but it is a very good one! You can get the flag through flag.php.
- 2200 Points
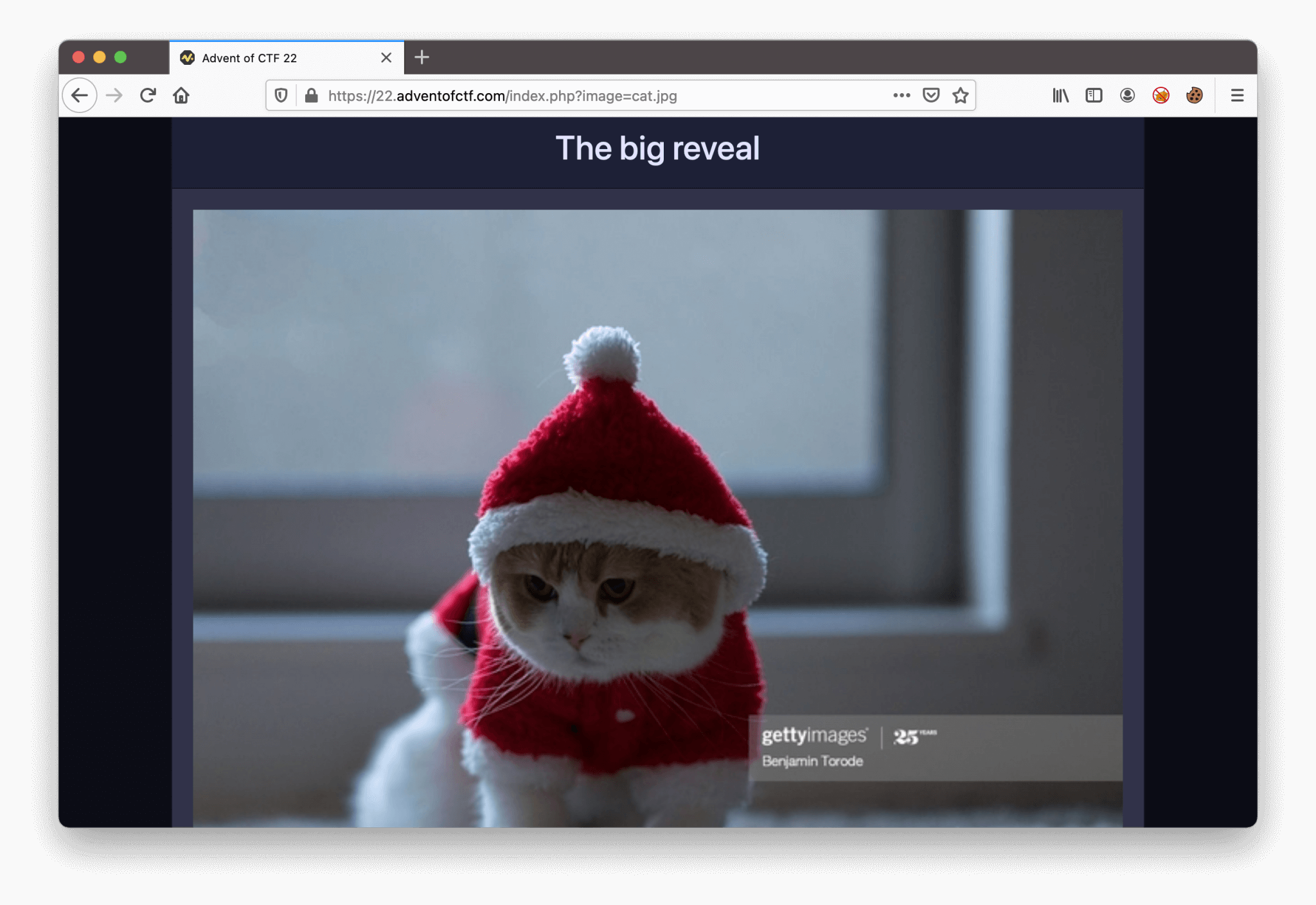
Well, Santa got a new service! Viewing Santa’s favorite pictures, let’s check what’s his favorite picture. We visit the challenge URL https://22.adventofctf.com. We are ending up on this web page.
We are have only a URL with the name Is this santa? Let’s check!
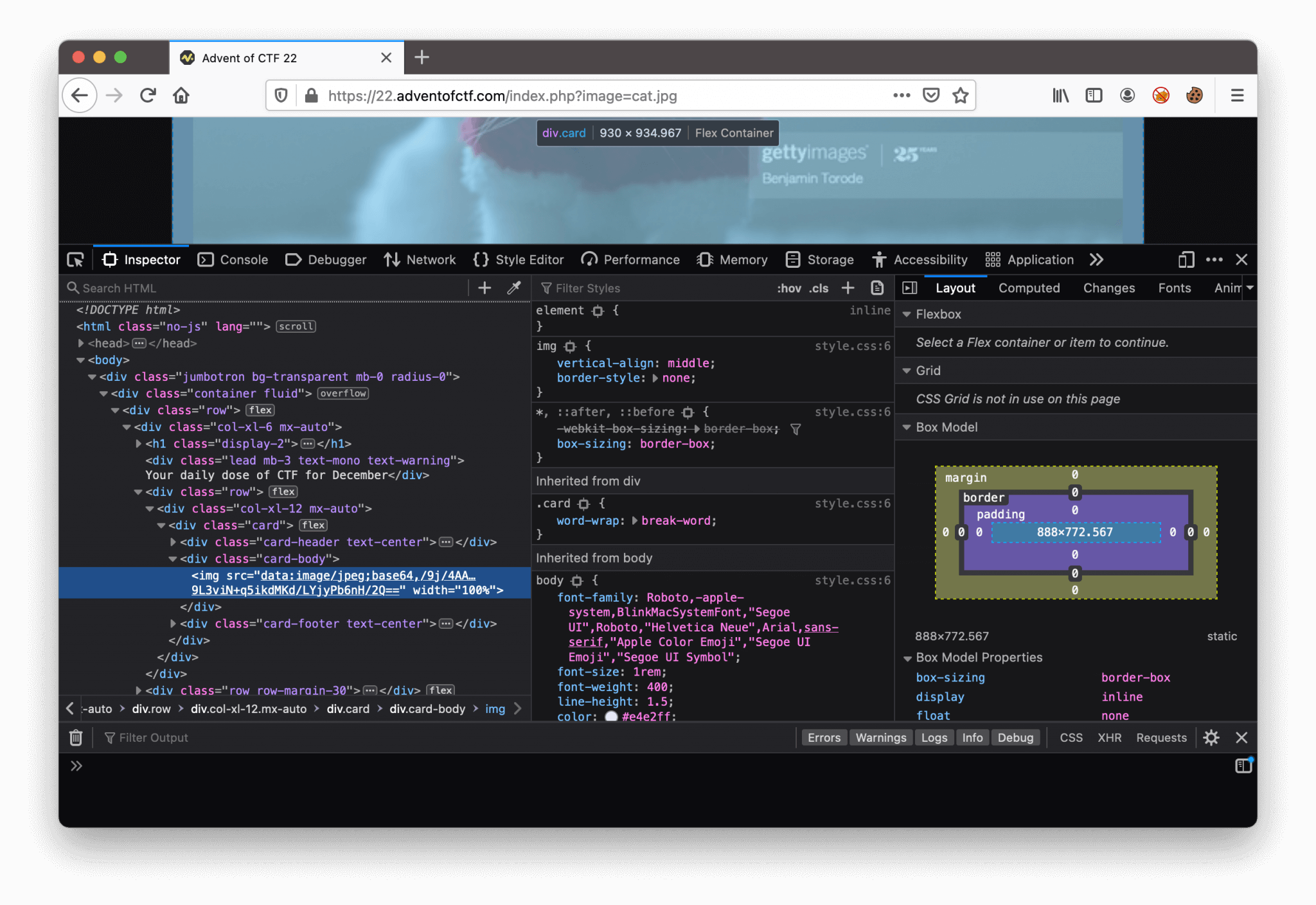
Haha, Santa is adorable. For now, we’ve had enough fun, we need to complete this challenge. According to the URL, we can see te image parameter. This parameter is including the file image cat.jpg. From the previous challenge, we have some experience with file inclusion. We need to keep this in mind, it can be useful. Let’s start this easy by checking the source code. We can see that the image is not a standard URL, but a data URL.
<img src="data:image/jpeg:base64,(base64 string)
From the description of this challenge, we know that the flag is in flag.php. Let’s try to include the flag in the image parameter. We are ending up with this URL: https://22.adventofctf.com/index.php?image=flag.php.
Unfortunately the flag is not yet visible. More is needed to read the flag. We can see that there is sort of a file included in our request. When we are reading the source code, we can notice that there is again a data URL visible with a base64 encoded string.
After decoding this string, it’s revealing his contents.
1
2
3
4
5
6
7
8
<?php
include("secret.php");
if (strpos(check_secret(), "allow") !== false) {
echo get_flag();
}
?>
From this file, we can see that the flag is protected by the file secrets.php. But, we are not allowed to include this file. If we try to include this file, we got redirected to the index.php. So, we need to find a way to get around this protection. If we try a path traversal attack to get the flag with this URL https://22.adventofctf.com/index.php?image=../flag.php, the website is returning the error message: Warning: file_get_contents(../flag.php): failed to open stream: No such file or directory in /var/www/html/index.php on line 46.
This message is an interesting one. It tries to include a file, but it’s not finding the file. This makes sense, because flag.php is probably in the current directory and not in a directory deeper. We are not authorized to call secrets.php directly. Let’s see if we can play a bit with the URL parameter image and if we can read the file secrets.php in a different way. After trying several URLs for a while I come up with the following payload for reading secrets.php: https://22.adventofctf.com/index.php?image=http://127.0.0.1/flag.php.
Through the source code, I can see this data URL:
data:image/jpeg;base64,Tk9WSXthc2tpbmdfZm9yX2FfZnJpZW5kfQ==
After decoding the base64 string, we get the flag!
1
2
~$ echo "Tk9WSXthc2tpbmdfZm9yX2FfZnJpZW5kfQ==" | base64 -d
NOVI{asking_for_a_friend
Thanks for reading!