Recently, I received a message from a very concerned customer. He was afraid of a mailbox breach on one of their email servers. Some of his clients had receive email messages on behalf of his company, with the contents that there are overdue Invoices, which needs to be paid. He didn’t send the email messages by himself. What worried my customer the most was the fact that the mails contained a message that the bank account, of his company, had changed and that the money had to be deposited into the new bank account. However, our customer hadn’t changed the bank account at all. He asked me to investigate this case.
What is email spoofing?
Before we go any further into this subject, I want to answer this question first. E-mail spoofing is part of Social Engineering. I know there’s some discussion as to whether or not this form of cybercrime is part of Social Engineering. However, because the attacker sends an email message from a forged domain, it seems that the email comes from a reliable source.
In this way, the attacker tries to spread ransomware or other viruses. It also happens that the attacker tries to entice his victim to fill in sensitive information, by placing a hyperlink in the mail, which redirects the victim to a malicious website.
How to detect a spoofed email or phishing mail in general?
It’s not easy to recognize a spoofed email message or a phishing email in general. Before we jump into the step-by-step guide on how you can detect those mails, it’s important to know the structure of an email message. An email message consists of three sections:
- The envelope
- The message header
- The message body
Envelope: This part is not visible to the recipient. It is the actual communication between the SMTP Server and the client.
1
2
3
4
5
6
7
8
9
10
11
12
13
S: 220 contoso.com Service Ready
C: HELO contoso.com
S: 250 OK
C: MAIL FROM:[email protected]
S: 250 OK
C: RCPT TO:[email protected]
S: 250 OK
C: DATA
S: 354 Start mail input;
C: Actual email is sent here
C: .
S: 250 OK
C: QUIT
As you see it is similar to a traditional letter sent by post. With email, we do not send the message by post but with the use of the Simple Mail Transport Protocol (SMTP). Unlike traditional mail, the envelope of an email message is not visible to the recipient. The email was invented back in 1982 and was last updated in 2008 to the standard we’re all comfortable with. Because the use of email messages originally wasn’t built for security, it can be abused so easily these days.
Step-by-step how you can recognize a spoofed email message or spam in general.
- Are you expecting this mail?
Were you expecting this email message? Is it logical that you receive an email with this subject from this sender? If the answer, on those two questions is ‘No’, there is a very good chance that you are the victim of a phishing mail.
- Check the sender
Check the sender’s address. The sender’s name may be exactly the same as the name of your bank or online store, but often the email address used is vague or resembles the version of a real company name. Section: Message Header
- Check the domain name
The domain name is the part after the @ symbol, like @binsec.nl. Is this domain name correct? Does this domain name match the name of the sender? Take your time for this step. It can be very difficult to distinguish a fake domain name from the real thing. For example, compare these domain names and find the difference: [email protected] and [email protected]. Not easy huh? Section: Message Header
- Check the website
In most cases the domain name, you have checked in step 3, is also the domain name used for the company’s website. Check this website, is the site existing or does this company exist?
- Check the Reply-To address
Is the reply-to address the same as the sender’s address? If not, Chances are very high that the email message has been spoofed. You can easily check this by answer the email message and check the To field. Section: Message Header
- Check the contents
How is the actual email look like? Concerns compelling language or check spelling. Does the use of language correspond to the company from which the mail originates? For example, a bank uses more elevated language than a car garage company. Section: Body
- Still not sure?
Give the sender a call and ask if he has sent this mail. Of course, do not use the phone number in the mail but look up the number online or use the known phone number from your CRM system;)
The case of our client
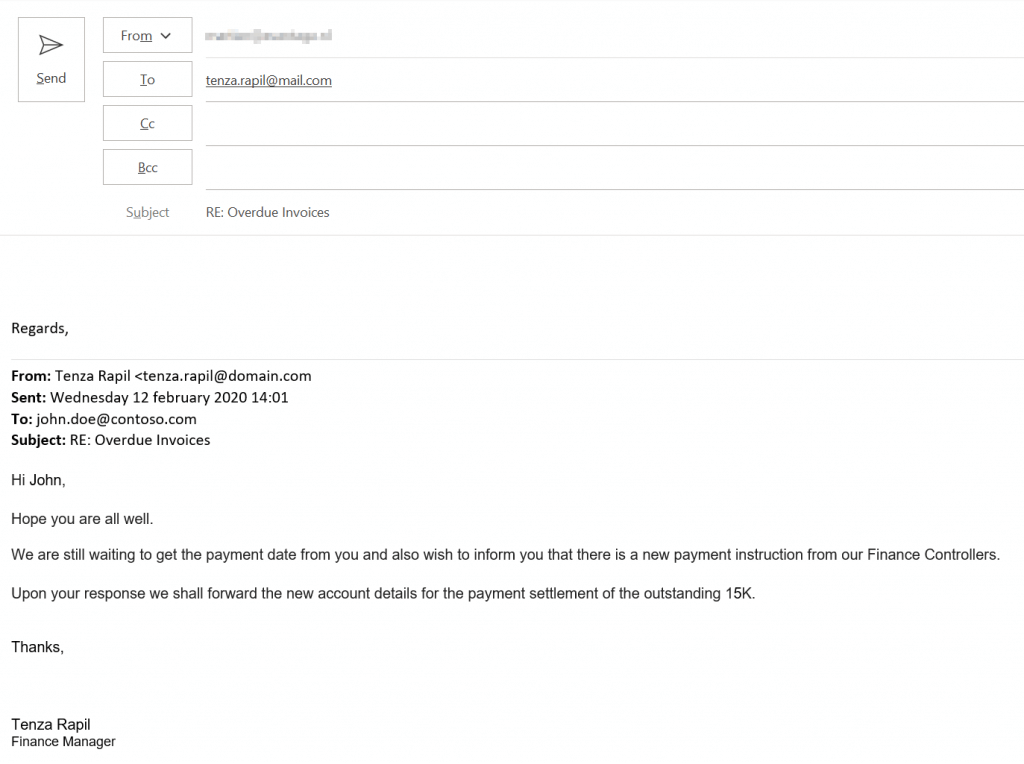
I’ve requested our client to send the mails as an attachment to my email address for further investigation. It seems that the Finance Manager has sent this mail below. From this mail, it is very difficult to see that this contains a spoofed email message. All of the names and email addresses are valid. This email message does not contain any hyperlinks to any malicious website. Also, the sender domain is a valid domain and our customer’s customer receives mail from this domain more often and did not immediately suspect that it could be a spoofed email message.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
From: Tenza Rapil <[email protected]>
Sent: woensdag 12 februari 2020 14:01
To: [email protected]
Subject: RE: Overdue Invoices
Hi John,
Hope you are all well.
We are still waiting to get the payment date from you and also wish to inform you that there is a new payment instruction from our Finance Controllers.
Upon your response we shall forward the new account details for the payment settlement of the outstanding 15K.
Thanks,
Tenza Rapil
Finance Manager
He had even replied to this message. After some emailing back and forth, he noticed that the Reply-To address did not match the sender. From this moment on the alarm bells went off.
Analyzing the email header
There are several tools available on the internet for analyzing the email headers. Just copy and paste the email header in the tool and you can start analyzing. There are two specific tools I use:
- MxToolbox: https://mxtoolbox.com/EmailHeaders.aspx
- Microsoft: https://mha.azurewebsites.net/
I have requested this email in a separate attachment so that I can examine the metadata of the email message in question. I can confirm this is a spoofed email message, even when the envelope fields are correct. Most of the email clients support, that the recipient can open the email headers. By reading the email headers there is a lot of useful information to catch.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
Received: from HE1PR01MB0939.eurprd01.prod.exchangelabs.com (ns5071.webempresa.eu [10.162.25.11])
by aspectex-2.vps.host-it.co.uk (Postfix) with ESMTPS id 3254F4BE9 for
<[email protected]>; Wed, 12 Feb 2020 16:32:28 +0000 (GMT)
Received: from [10.163.24.11] (port=59531 helo=[10.198.0.34]) by
HE1PR01MB0939.eurprd01.prod.exchangelabs.com with esmtpsa (TLSv1.2:ECDHE-RSA-AES128-GCM-SHA256:128)
(Exim 4.92) (envelope-from <[email protected]>) id 1j1uw5-00FLzw-QI for
[email protected]; Wed, 12 Feb 2020 17:32:27 +0100
From: Tenza Rapil <[email protected]>
To: "[email protected]" <[email protected]>
Subject: RE: Overdue Invoices
Thread-Topic: Overdue Invoices
Thread-Index: AQI1IiWGjkhPImEDZ9bW7rxNi4ZG8Q==
Date: Wed, 12 Feb 2020 16:30:36 +0000
Message-ID: <[email protected]>
Reply-To: "[email protected]" <[email protected]>
Content-Language: en-US
X-MS-Has-Attach: yes
X-MS-TNEF-Correlator:
Content-Type: multipart/related;
boundary="_004_036e050b71d7130ee10d6d36a8ad1215jmtcouk_";
type="multipart/alternative"
MIME-Version: 1.0
As can be seen in this header, the Reply-To e-mail address is different from the sender and the mail server does not match our customer’s mail server, that’s why an SPF soft fail occurs. I will cover SPF/DMARC and DKIM in another blog post.
Conclusion
In this case, we are definitely dealing with a spoofed email message. There are many more variations of an email scam. But in the core they are all the same: there are spoofing the sender’s identity and try to gain the victim’s trust, in order to entice the victim to share sensitive information.
Can you spot when you’re being phished? Identifying phishing can be harder than you think, take this quiz to see how you do: https://phishingquiz.withgoogle.com/
Your email environment is as safe as the awareness of their users and recipients.
T13nn3s