The threat landscape is constantly changing. Cybercriminals are resourceful and try every time to find new entrances to their victims for taking over the user account. Multi-Factor Authentication plays a major role in this and the risk of a compromised user account by 99.9 percent, according to Alex Weinert. To get Multi-Factor Authentication more effective, you also need to block legacy authentication. The best way to achieve this is to disable legacy authentication.
Microsoft is going to disable basic/legacy authentication for Exchange Online in October 2022.
What is legacy authentication?
Legacy Authentication, or in short legacy auth, are the protocols which are not supporting Multi-Factor Authentication (MFA). Legacy authentication is also known as “basic authentication. Legacy authentication refers to applications or protocols which are not supporting modern authentication, like the Microsoft Outlook 2010 or older, IMAP, POP, POP3, and so on. There is a full list of protocols further down in this article. Before you turn off legacy authentication in your Microsoft 365-environment you need to make sure that people in your organization are not using legacy authentication. But, why the need for disabling legacy authentication?
Why disable legacy authentication?
Well, there is no need, unless you want to secure your Microsoft 365-environment. In February 2020 Microsoft gave a presentation in San Fransisco. There is a recording of this presentation on YouTube. In this presentation Alexander Weinert explains the need of turn off legacy authentication. A small overview of the figures that came along during this presentation:
- More then 99% of the password spray attacks use legacy authentication, through IMAP or SMTP.
- More than 97% of the replay attacks use legacy authentication.
If you turn off legacy authentication, you will achieve this:
- 67% reduction in compromises in tenants who disable legacy authentication.
So, my strongly advice is to invest your time in disabling legacy authentication in your Microsoft 365-environment. It’s better to invest your time in preventing an account compromise, rather than doing a Incident Response because you haven’t disable legacy auth or even not adviced your clients to do so.
Before we dive-in the process to turn off legacy authentication in your environment, you need to know which protocols are using legacy authentication. The protocols shown in the table below are using legacy authentication.
| Protocol or service | **Description ** |
| Exchange | Active Sync (EAS) This protocol is being used by native email applications on smartphones. |
| Autodiscover | Used by Microsoft Outlook and EAS to connect with Exchange Online. |
| IMAP4 | Used by IMAP-clients to read your email messages. |
| MAPI | over HTTP (MAPI/HTTP) Used by Microsoft Outlook 2020 and later. |
| Offline | Address Book (OAB) A copy of address list collections that are downloaded and used by Outlook. |
| Outlook | Service Used by the Mail and Calendar app for Windows 10. |
| POP3 | Used by email clients to pull your email from the email server through POP3. |
| Reporting Web Services | Used to retrieve report data in Exchange Online. |
| Outlook Anywhere (RPC over HTTP) | Used by Outlook 2016 and earlier. |
| Authenticated | SMTP Used by POP and IMAP clients to send email messages. |
| Exchange Online Powershell V1 | Used to connect to Exchange Online with remote PowerShell. |
| Exchange Web Services (EWS) | A programming interface that’s used by Outlook, Outlook for Mac, and third-party apps. |
Turn off Legacy Authentication
Determine if Legacy Authentication is being used
Before turning off legacy authentication, make sure that your users are not using legacy authentication. The place to look if legacy authentication is still being used is in the sign-ins option in the Azure Active Directory admin center. You can check the use of legacy auth by following the following steps:
First open the Azure Active Directory admin center and navigate to Sign-ins and filter the Date on Last 1 month and set the status to Success and configure the last filter Client app and select all the Legacy Authentication Clients.
Is your overview completely empty? Well done! Legacy Authentication is not used within Microsoft 365, so not in Exchange Online either. If you do see successful sign-ins, Legacy Authentication is still being used. You can export this overview to a CSV file and analyze which services or users are still using Legacy Authentication.
Block Legacy Authentication with Conditional Access policy
|
Information To use conditional access policies, your Microsoft Azure tenant must be licensed with either an Azure AD Premium P1 license or Azure AD Premium P2 license. Do you not meet these requirements, then disable legacy authentication through the Microsoft 365 admin enter on a per-protocol basis</a>. |
After you have analyzed the users and product using Legacy Authentication, you can migrate them to either modern authentication or keep them on controlled Legacy Authentication. It’s not always possible to directly disable Legacy Authentication for every application or employee.
Through the steps below, we are going to use conditional access policies to block legacy authentication and only allow it for users or software applications that need it. In addition, we configure conditional access policies for the use of modern authentication.
- Login into
Azure Active Direcory admin center. - Navigate to
Azure AD Conditional Accessand select+ New Policy, to create a new conditional access policy.
In the next screen we are configuring the policy.
- First, you need to define the policy name, for example,
Block Legacy Authentication. - At
Users and groups, you define the scope of your policy. For whom do you want to disable Legacy Authentication, for everyone? If so, then select for example All users or if you only want to disable for specific persons or groups you need to select the users of a group.
If you do not want to disable legacy authentication immediately for everyone, it’s recommended to configure to separate groups for each of the authentication methods and assign them both to a different conditional access policy. It’s also possible to fit that configuration in one conditional access policy, by adding those users or groups to the exclusion list by the Users and groups option.
- At the
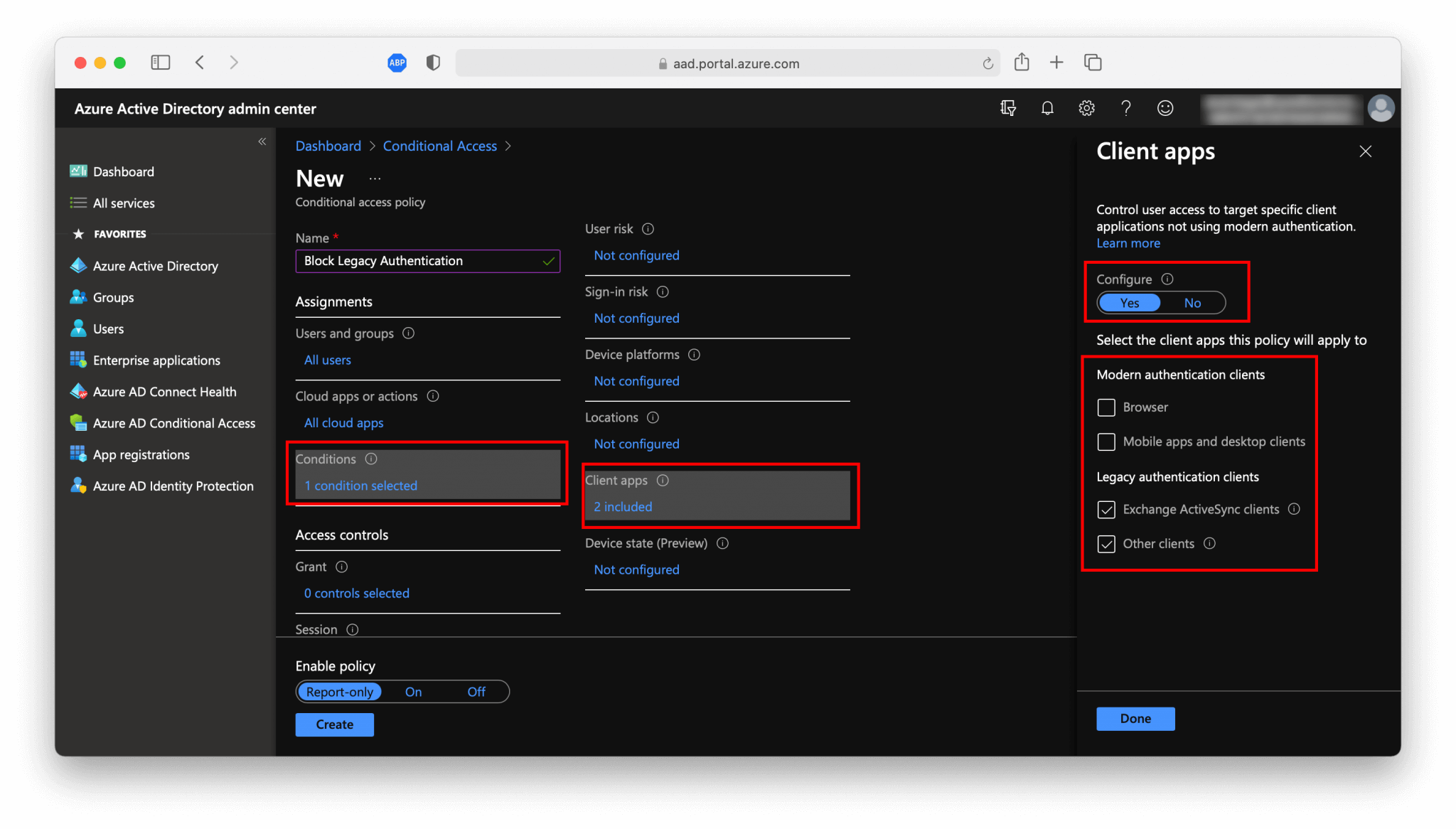
Cloud apps or actionsselectAll cloud appsto block legacy authentication for every application. It’s also possible here to exclude specific applications, configure it to what suits your needs. - On the
Conditionsgo toClient Appsand make sure that you only select theLegacy authentication clientsand setConfigureonYes.
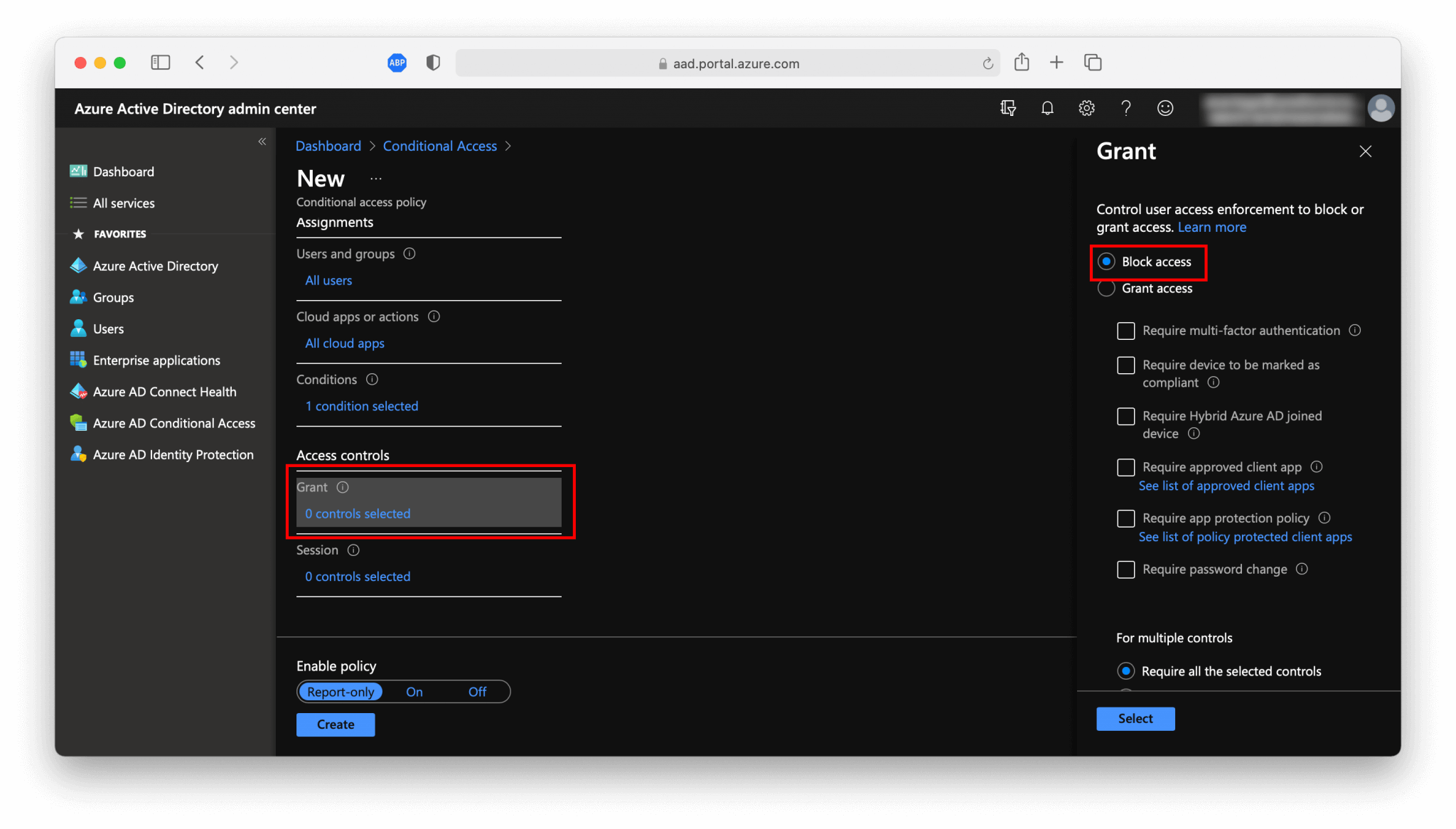
- The last the
Access controlsand selectBlock access.
- The last step is whether you want to enable this policy or first try the
Report-onlymethod. This state allows you to evaluate the impact of theConditional Accesspolicy before enabling them. Results from theReport-onlystate are logged in the Conditional Access and Report-only tabs of the Sign-in log details.
Congratulations! You have now disabled Legacy Authentication through a Conditional Access policy. There is a second method to disable legacy authentication on a per-protocol basis.
Disable Legacy Authentication per protocol
The second method for blocking legacy authentication is by disabling the use of legacy authentication for all protocols or only for selected protocols. This can be done through the Microsoft 365 admin center in the Organization Settings. If your tenant is not licensed with an Azure Premium P1 or P2 license, you cannot use Conditional Access policies. In that case, you can turn off legacy authentication on a per-protocol basis.
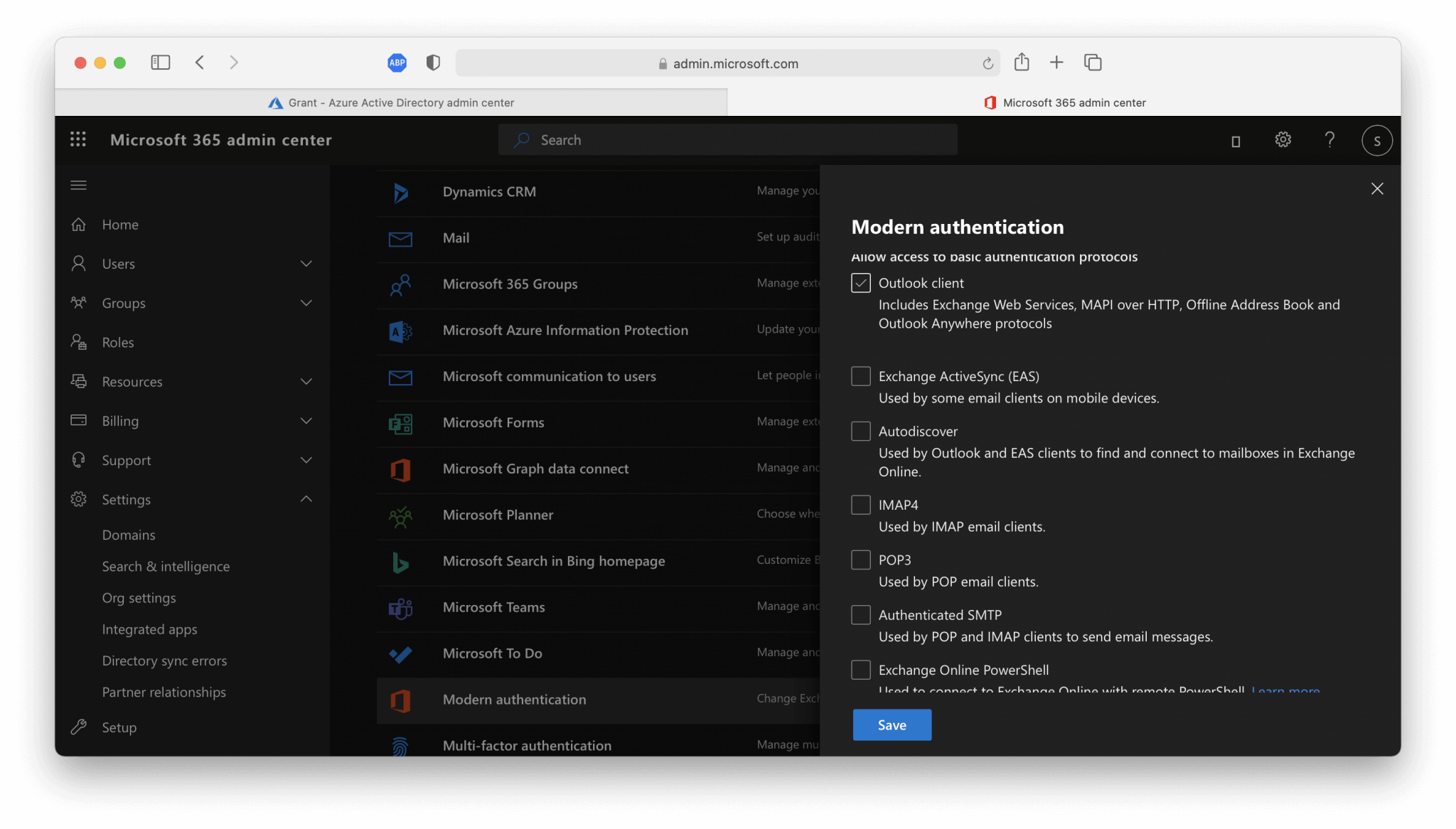
- In the
Microsoft 365 admin centergo toSettingsand thenOrg settings. - Here you can specify for which protocols you want to disable legacy authentication. Make sure that you leave Modern Authentication enabled.
Conlusion
Disabling Legacy Authentication for the Microsoft 365 tenant, in conjunction with enabling Multi-Factor Authentication for every user account, Is the first precaution to take, in order to prevent compromised user accounts. Thus, only enabling Multi-Factor Authentication is not enough Also, support for legacy authentication must be disabled otherwise user accounts remain vulnerable to password-spraying attacks.
Most of the time effort is going to figure auth if legacy authentication is still being used, and to inform and instruct the users to switch from the native email application on their phones to the Outlook app. But ultimately, a major security risk is mitigated and the organization runs a smaller risk of account compromise through Microsoft 365 if you block the use of legacy authentication in conjunction with enabling MFA.