Context
Beginning October 2022, Microsoft started disabling basic authentication protocols (EAS, POP, IMAP, RPS, EWS, OAB, Autodiscover and Outlook) in randomly choosen Microsoft 365 tenants. The only exception is the “Authenticated SMTP” protocol. If Microsoft detects that this protocol is in us in a Microsoft 365 tenant, this protocol will remain enabled. The end goal is to have the basic authentication protocols early-January 2023 disabled on every Microsoft 365 tenant.
The reason for disabling these protocols is because they do not support Multifactor Authentication (MFA) and are therefore easily to abuse by cybercriminals, for example easy to perform a Password Spraying attacks. In particular, we have seen that the IMAP protocol is very often abused for password Spraying attacks.
The only basic authentication protocol for which support remains is the AUTH SMTP protocol. This moved the problem of Password Spraying from the IMAP protocol to the SMTP AUTH protocol.
Mitigating this threat by creating a Conditional Access Policy to block SMTP AUTH for user accounts that do not use this protocol is not enough to protect against these attacks. After all, a Conditional Access Policy only applies on to successful sign-ins. It wil not block any sign-in attempt with an incorrent password. To solve this challenge, Authentication Policies can be used to configure which user accounts are allowed to access SMTP AUTH. For the remaining user accounts, this protocol is disabled, significantly reducing the attack landscape and preventing the execution of a Password Spraying attack on these user accounts.
Conditional Access Policies
I already hear you thinking, “Then we’ll implement a Conditional Access Policy for blocking SMTP AUTH for user accounts that don’t need it.” Conditional Access Policies only apply on successful sign-in and not on failed sign-in attempts. So, this will not mitigate this threat.
Authentication Policies
Authentication Policies are configured through the Exchange Online PowerShell and apply only to the Exchange Online environment. These policies have only one function; Allow or block specific basic authentication protocols. My recommendation is to keep your setup of Authentication Policies straightforward. This is also easier now than before because Microsoft has disabled basic authentication policies. Make sure you only have two policies:
- BlockBasicAuth (tenant wide policy, applies for every user account)
- AllowSmtpAuth (user specific policy)
To configure the Authentication Policies in the right way, we follow the steps below:
- Check whether SMTP AUTH is being used.
- Via Azure Active Directory
- Via Microsoft Sentinel (or Log Analytics Workspace)
- Configuring the Authentication Policies
- BlockAllBasicAuth
- AllowSmtpAuth
- Assign the tenant wide policy
BlockAllBasicAuthas tenant default. - Assign the
AllowSmtpAuthpolicy to specific user accounts.
Check whether SMTP AUTH is being used
Via Azure Active Directory
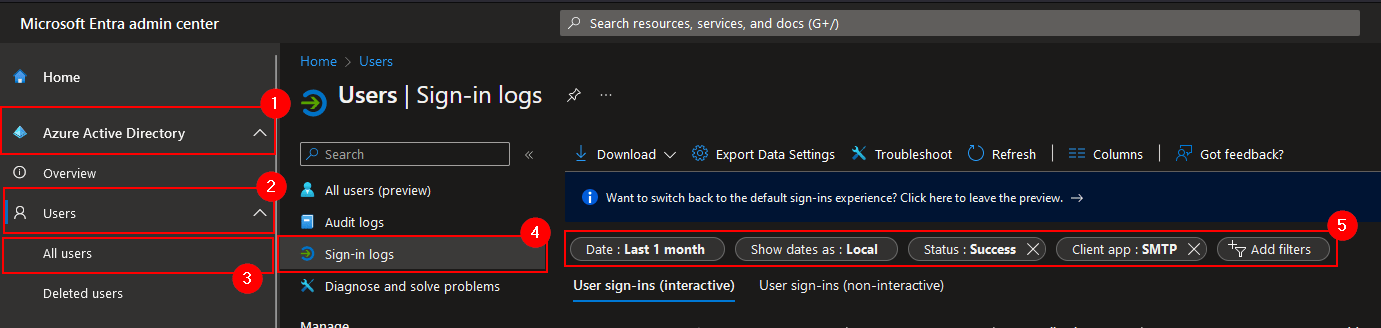
- Log in at https://entra.microsoft.com.
- Navigate to
Azure Active Directory–>All users. - Select
Sign-in logs. - Configure the filters as below:
Date: 1 month (or 7 days if 1 month is not available)Status: SuccessClient app: SMTP
Under the User sign-ins (interactive) and User sign-ins (non-interactive) tabs, analyze whether SMTP AUTH is in use. Optionally, this summary can be exported to CSV for further analysis.
 Check if SMTP AUTH is being used through Azure AD
Check if SMTP AUTH is being used through Azure AD
Via Microsoft Sentinel (or Log Analytics Workspace)
Navigate to Microsoft Sentinel or to the Log Analytics Workspace and use the following KQL query. To get a distinct view of the user accounts which are using SMTP AUTH, the following query can be used.
1
2
3
4
5
6
7
8
9
10
11
12
13
SigninLogs
| where TimeGenerated > ago(90d)
| project
TimeGenerated,
UserPrincipalName,
ClientAppUsed,
AuthenticationDetails,
CorrelationId
| where ClientAppUsed == "Authenticated SMTP"
| mv-expand todynamic(AuthenticationDetails)
| extend logonresult = tostring(parse_json(AuthenticationDetails).succeeded)
| where logonresult == "true"
| distinct UserPrincipalName
Configuring Authentication Policies
If no user account uses SMTP AUTH, then it is sufficient to create the
BlockAllBasicAuthpolicy and configure it as the tenant default via theSet-OrganizationConfigcmdlet.
- Create a connection with the Exchange Online tenant.
1
Connect-ExchangeOnline
- Create the Authentication policy
AllowAuthSmtpfor allowing AUTH SMTP.
1
New-AuthenticationPolicy -Name AllowAuthSmtp -AllowBasicAuthSmtp
- Create the second Authentication Policy
BlockAllBasicAuth.
1
New-AuthenticationPolicy -Name BlockAllBasicAuth
- Configure the
BlockAllBasicAuthas the organization’s default Authentication Policy.
1
Set-OrganizationConfig -DefaultAuthenticationPolicy BlockAllBasicAuth
- If there are user accounts that need SMTP AUTH, you can assign the
AllowAuthSmtppolicy to those user accounts with the cmdlet below.
1
Set-User <username> -AuthenticationPolicy AllowAuthSmtp -Confirm:$false
That’s all! :-)
Conslusion
With these actions, the attack surface for performing Password Spraying attacks via the SMTP AUTH protocol has been significantly reduced.

