About Crimediggers
Crimediggers is an online CTF game created by the Dutch Police. By playing this game, players can challenge themselves to test if they have the right skills to join the Dutch Police to fight cybercriminals. The Crimediggers can be played online for free through the website: https://crimediggers.nl.
Crimediggers #2
Test your technical networking skills, analytical skills, and hacker skills in six individual challenges. The challenge is to find all flags. This CTF game has the challenges as stated below. I have the challanges completed when they are marked as done.
- Malware
- Geo
- Reverse
- TCP/IP
- OSINT
- Crypto
- Pentesting
GEO
Task
From two suspects, we confiscated the phones. We think they met. Can you find out where exactly?
We can download the file GEO.zip to complete this challenge. After unzipping this ZIP file, we are left with the files GPS 1.gpx and GPS 1.gpx. GPX, or GPS Exchange Format, is an XML schema designed as a common GPS data format for software applications. It can be used to describe waypoints, tracks, and routes. It is an open format and can be used without the need to pay license fees.
Solution
To solve this challenge, I have used Visual Studio Code with the Geo Data Viewer extension. This challenge can also be solved by using Google Earth Pro. In my experience, Google Earth Pro is more convenient to solve this challenge. I had done it with VScode, so here are my steps:
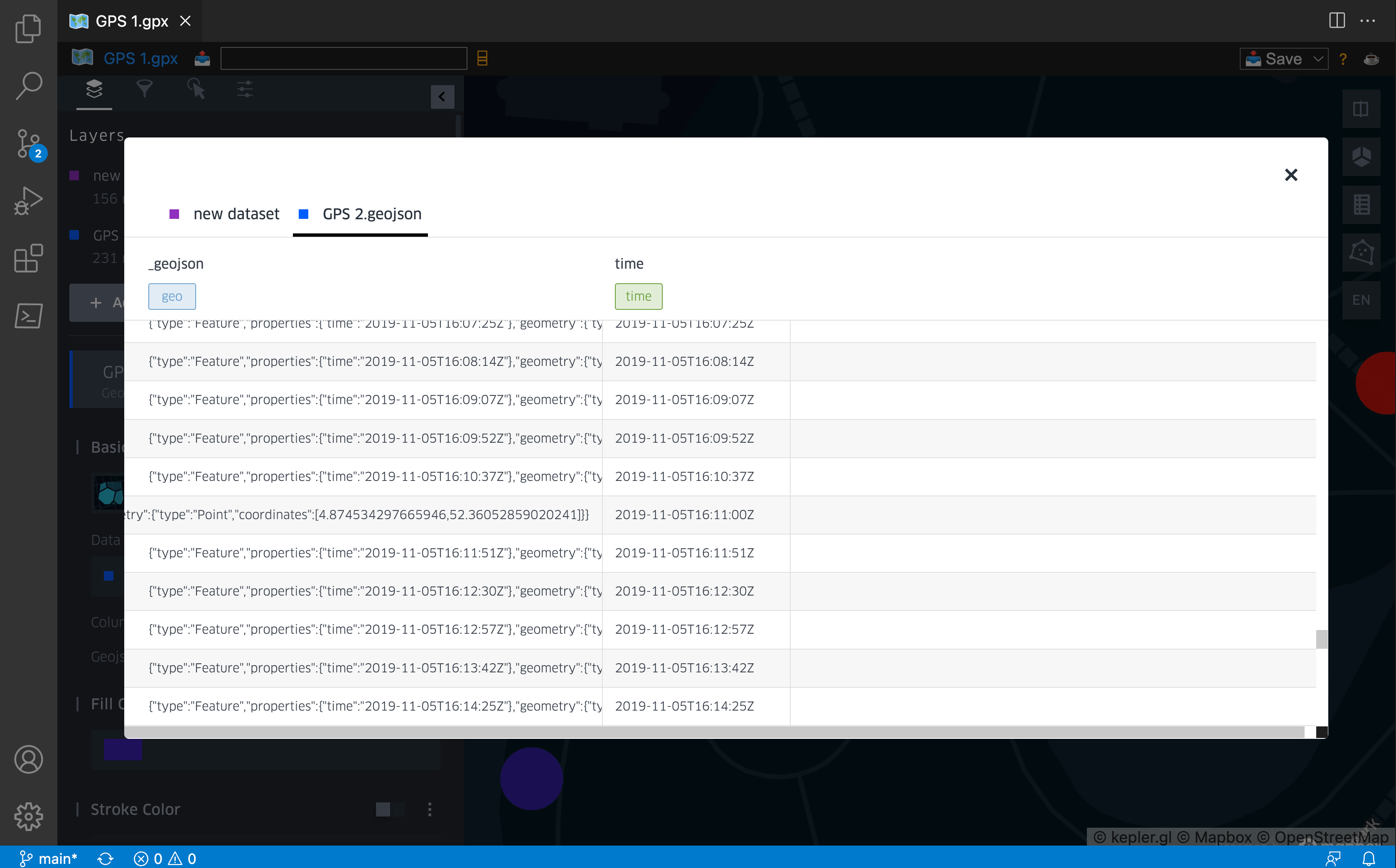
I have opened the files in VSCode, and as result; two geojson files are being created in the same directory. I have imported the GPS 2.geojson file in the same project as GPS 1. To separate the tracks of the two suspects, I gave them different colors. This makes the analysis easier.
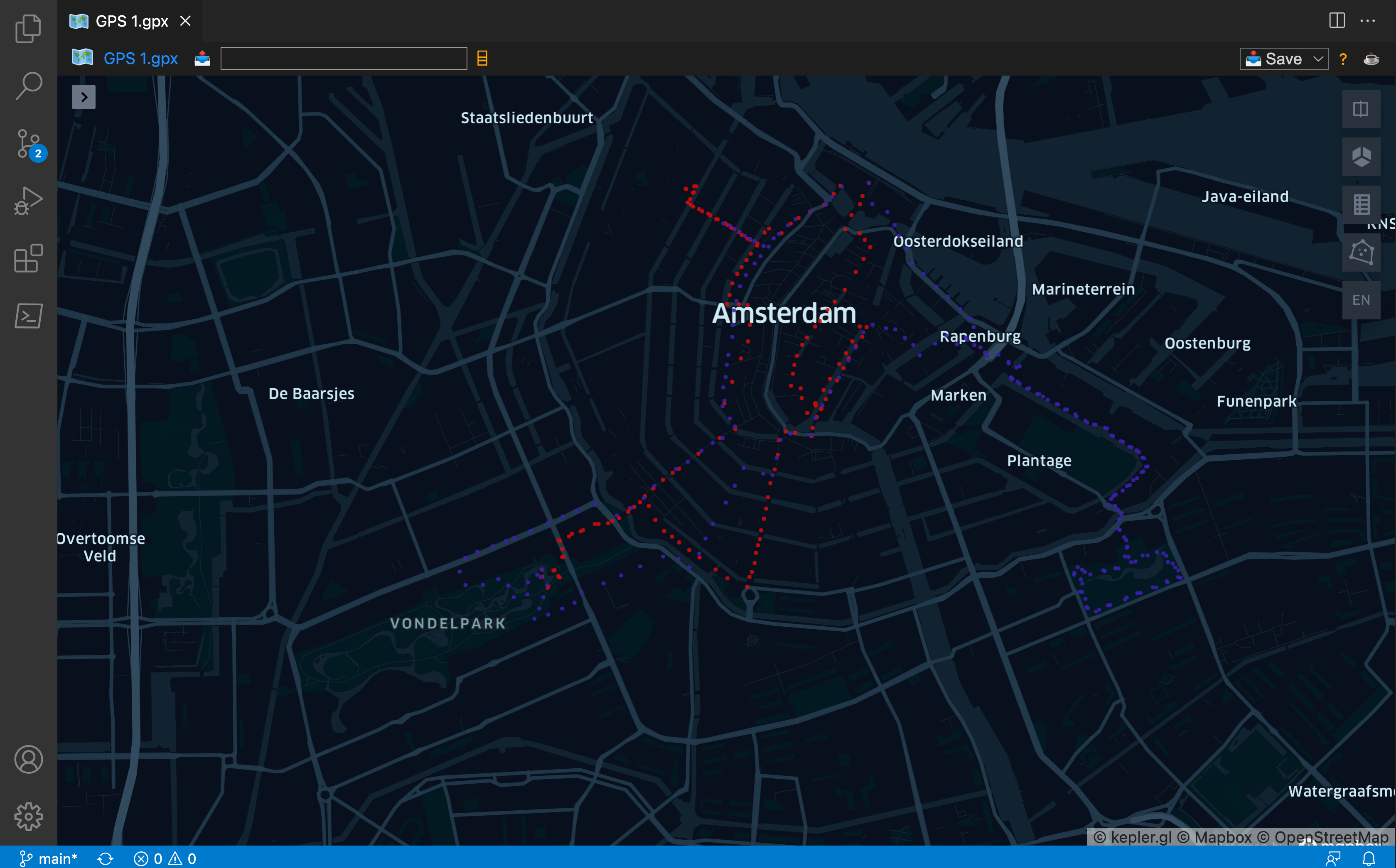
We have now this view, we can start the analysis.
The GPS data shows the map of Amsterdam with some waypoints. The track from both files are from the same date: May 5th, 2019. If we are following the waypoints, we can see the suspects traveling through the city of Amsterdam. At the Vondelpark, we see that the tracks are coming together and that the suspects are coming together on 2019-11-05T16:11:00Z.
We can look up the coordinates from the GPS 2.geojson file by looking at the time table and checking the corresponding coordinates in the geo table. After this cross check we have the following coordinates: 4.874534297665946,52.36052859020241.
Crimediggers is asking for a different format (XX.XXXX;Y.YYYY), the solution is: 52.3605;4.8745
Reverse
Task
On October 28, 2019, at 3:23 AM, the attached script was used to generate a code. Can you figure out which one? This challenge is offering the following JavaScript script:
1
2
3
4
5
6
7
8
function createPassword(t) {
for (var r = "", e = String(t + " " + (new Date).getHours() + ":" + (new Date).getMinutes()), n = Math.floor(10 * Math.random()) + 1, a = String("".substring(0, 9)), o = "", g = 0; g < e.split(" ")[1].length; g++) o = btoa(e[r]).replace("==", "") + o;
for (o.length < e.length && (o += o); a.length < 10;) {
for (var l = 0; l < e.split(" ")[0].length; l++) r += btoa(e.split(" ")[0][l] + o[l]).replace("=", "");
a += String.fromCharCode(Math.floor(25 * Math.random()) + 97)
}
return r.concat(Math.random().toString(36).substr(2, n)).slice(0, -n).substring(r.length - 16)
}
Solution
I started with the question: what is this script doing? I started with the question: what is this script doing? I started by creating an HTML webpage to get this script working. Then, after some time spend reversing this script, I noted that the parameter (t) is the key to the solution. So, this parameter matters. What could it be? a number? No, I don’t think so. The variable t is most time refered to a string. So, I assume I have to pass a string value. Maybe a word? I Tried some words, like code and password etc. But, no solution. Then I got a tip from somebody else: “Think in the easy way, do not overthink.” The most easy way is just passing a date as the parameter. I came up using different date variations, and just using this parameter createPassword('28-10-2019 3:23') is the solution.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
<!DOCTYPE html>
<html lang="en">
<head>
<link rel="icon" type="image/x-icon" href="./favicon.ico">
<title>Crimediggers CTF: Reverse</title>
</head>
<h1>Crimediggers</h1>
<h2>Reverse</h2>
<p>Op 28 oktober 2019, om 3:23 is bijgevoegd scriptje gebruikt om een code te genereren. Kun jij er achter komen welke?</p>
<p id="crimediggers"></p>
<script>
document.getElementById("crimediggers").innerHTML = createPassword('28-10-2019 3:23');
function createPassword(t) {
for (var r = "",
e = String(t + " " + (new Date).getHours() + ":" + (new Date).getMinutes()),
n = Math.floor(10 * Math.random()) + 1, a = String("".substring(0, 9)),
o = "",
g = 0; g < e.split(" ")[1].length; g++)
o = btoa(e[r]).replace("==", "") + o;
for (o.length < e.length && (o += o); a.length < 10;) {
for (var l = 0; l < e.split(" ")[0].length; l++) r += btoa(e.split(" ")[0][l] + o[l]).replace("=", "");
a += String.fromCharCode(Math.floor(25 * Math.random()) + 97)
}
return r.concat(Math.random().toString(36).substr(2, n)).slice(0, -n).substring(r.length - 16)
}
</script>
</body>
</html>
The solution: oLVcMloMHAMWIOW0
TCP/IP
Task
In a digital scam case, we intercepted network traffic. Can you find out if malware was sent?
Solution
To accomplish this task we can download the file jim.pcapng.zip. After the extraction of this file we can analyse the file jim.pcapng with WireShark.
To analyze the network traffic, we have to open this file in Wireshark. You can download Wireshark from this link. After opening the file,we can start analyzing.
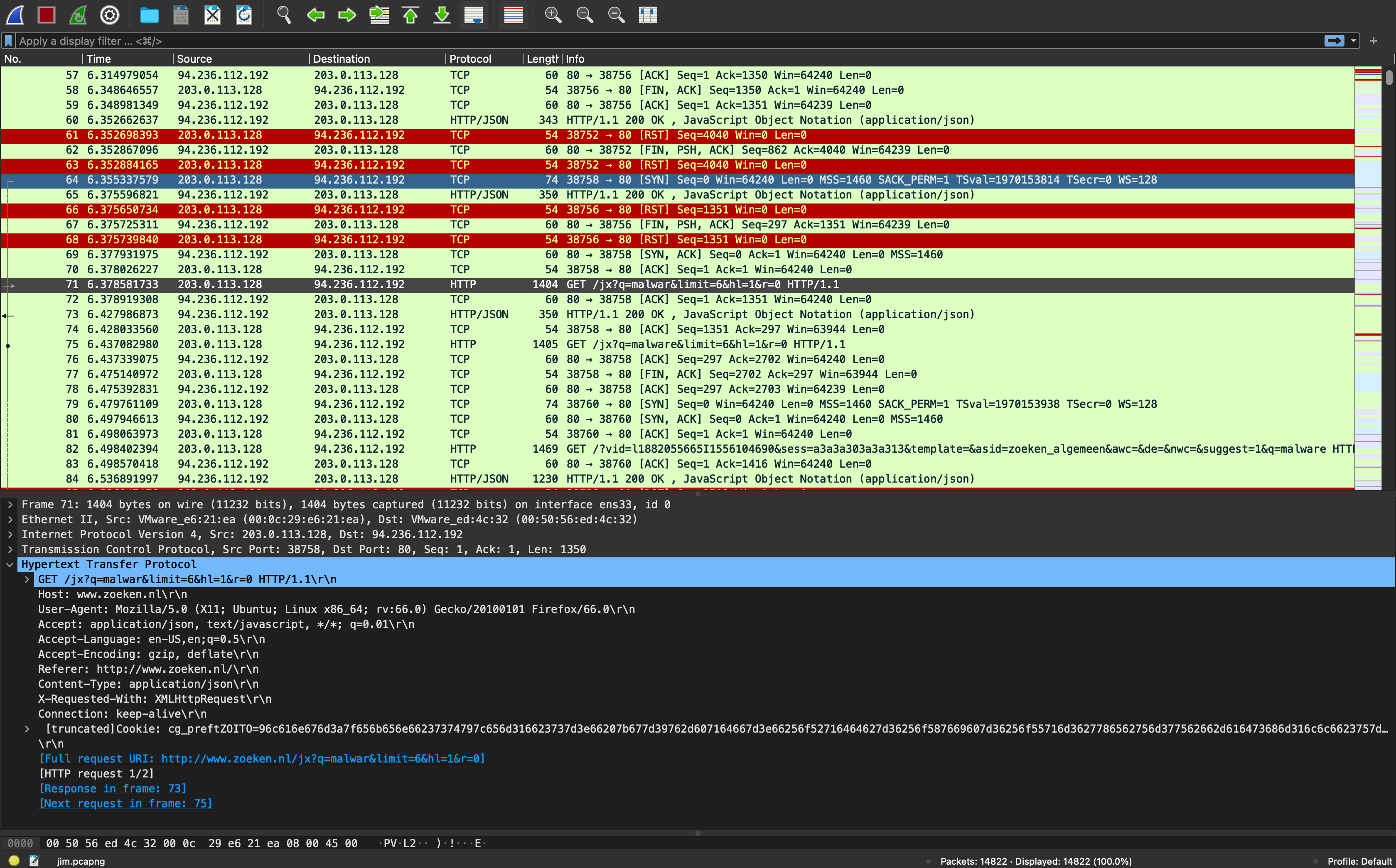
The first notable information is that the subject searches via the websitehttps://zoeken.nl for various keywords, such as malware, ransomware kopen, and darkweb. The subject is looking for malware in the form of ransomware and hopes the malware can be bought on the dark web.
If we are looking further into the capture network traffic, we can find an email conversation with our subject. Our subject is using the name jimhendraxx and sending email messages from the email address [email protected] to a ransomware seller with the email address [email protected]. We can find this information in the network packets with the numbers 4656 up to 14816.
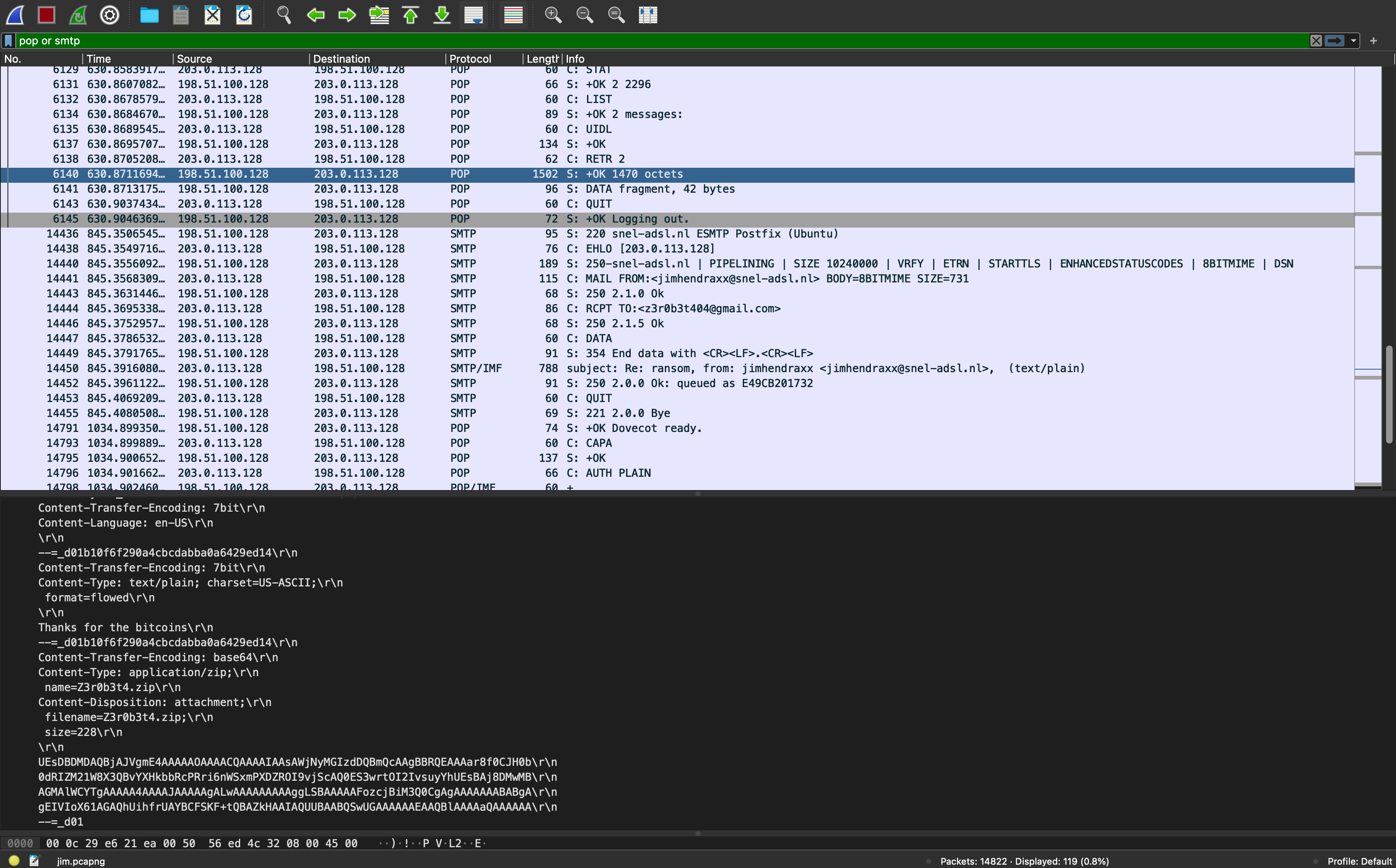
In the network package numbered 6140 we see a ZIP file exchange between the seller and buyer. The ZIP file containing the possible malware is password protected. Before the transfer, we see that the buyer has paid for the malware in Bitcoin (BTC).
In the network packet with the number 14450, our subject asks for the password to open the received ZIP file. In number 14843, our subject received the password 5Jsg23Po%q12.
We can extract the ZIP-file from the trace, with the following steps:
- Select packet number
6410. - Copy the Base64 encoded attachement to your clipboard.
- With the following command, decode the attachement to the file
attachement.zip:
1
echo "UEsDBDMDAQBjAJVgmE4AAAAAOAAAACQAAAAIAAsAWjNyMGIzdDQBmQcAAgBBRQEAAAar8f0CJH0b0dRIZM21W8X3QBvYXHkbbRcPRri6nWSxmPXDZROI9vjScAQ0ES3wrtOI2IvsuyYhUEsBAj8DMwMBAGMAlWCYTgAAAAA4AAAAJAAAAAgALwAAAAAAAAAggLSBAAAAAFozcjBiM3Q0CgAgAAAAAAABABgAgEIVIoX61AGAQhUihfrUAYBCFSKF+tQBAZkHAAIAQUUBAABQSwUGAAAAAAEAAQBlAAAAaQAAAAAA" | base64 -d > attachement.zip
Now the ZIP file can be opened with the password.
1
Thanks voor de bitcoins! #SUCKAHHHH
We see that the buyer has been dealing with a scammer. He paid in Bitcoins (BTC) to the selling party and did not and did not receive any malware. This is immediately a wise lesson; distrust a person who wants to sell you malware via the dark web.
The flag: #SUCKAHHHH
Pentesting
Task
We seized a computer on which cryptoware was probably being developed. Can you find the corresponding bitcoin address?
Solution
To solve this challenge, we have to download the ova-file ubuntu_jenkins.ova. I have created a new virtual machine on my MacBook with VMware Fusion. After booting the machine up, we see three user accounts Jenkins, Josh, and Guest.
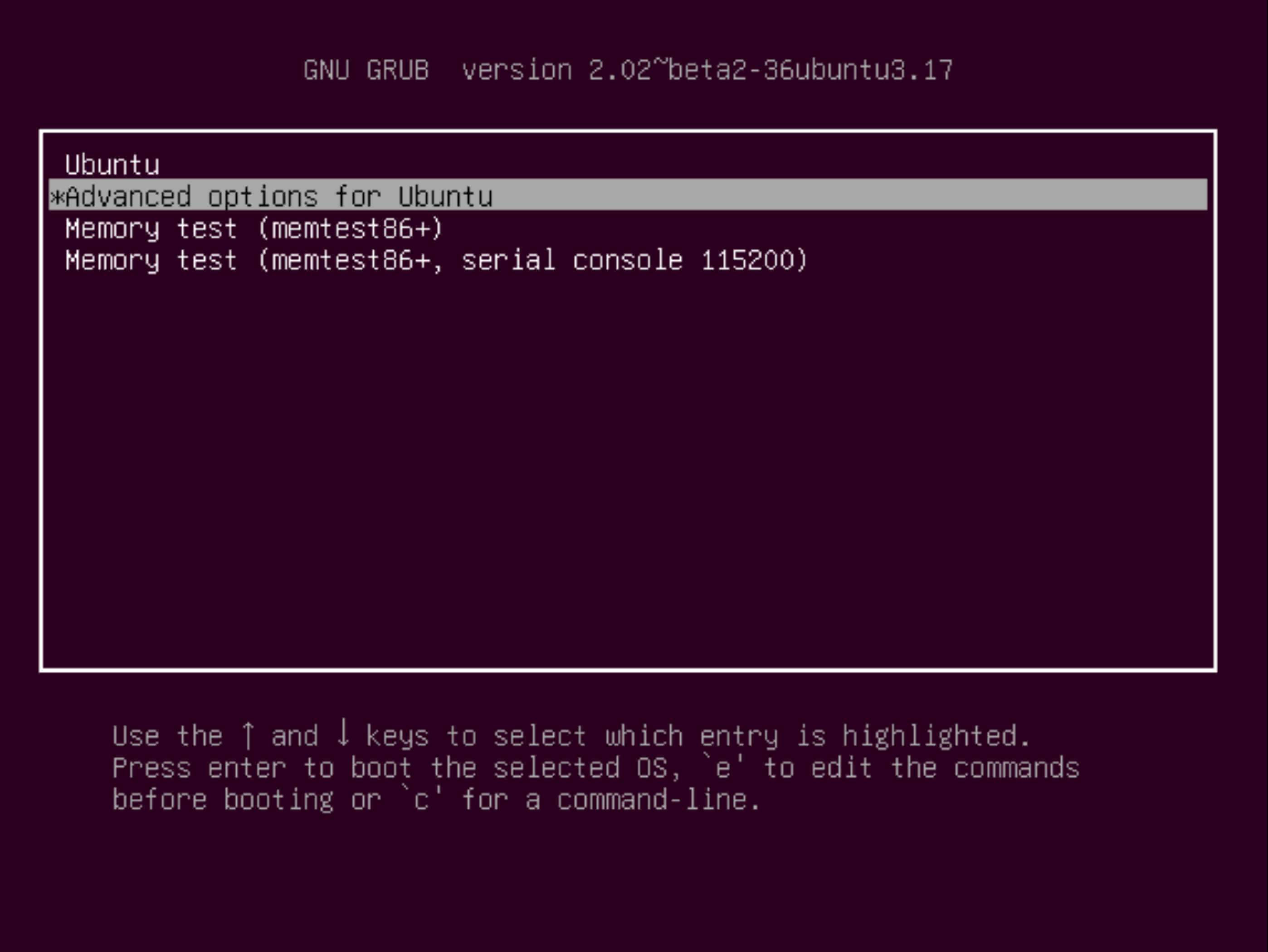
I have first tried some passwords on the user accounts Jenkins and Josh. I have also tried to break out the Guest session. But, after some time spent in this phase. I came up with a totally different idea to solve this challenge: the GRUB boot menu. From the GRUB menu, we have access to the command line, and from the command line, we have access to the filesystem, without having a password.
So, I rebooted the virtual machine and pressed the Shift key during the boot process to access the GRUB boot menu.
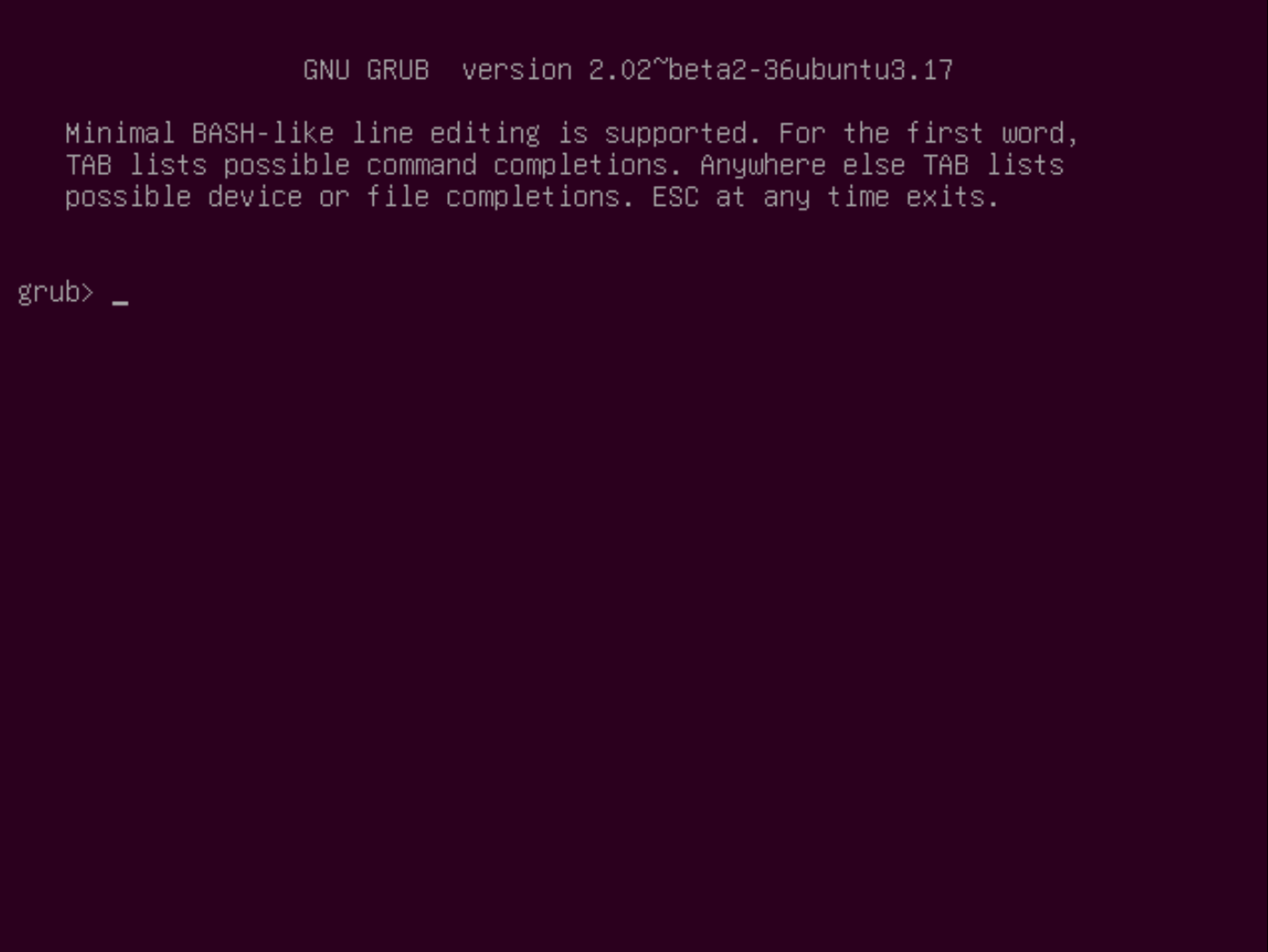
I pressed ‘c’ to access the command line.
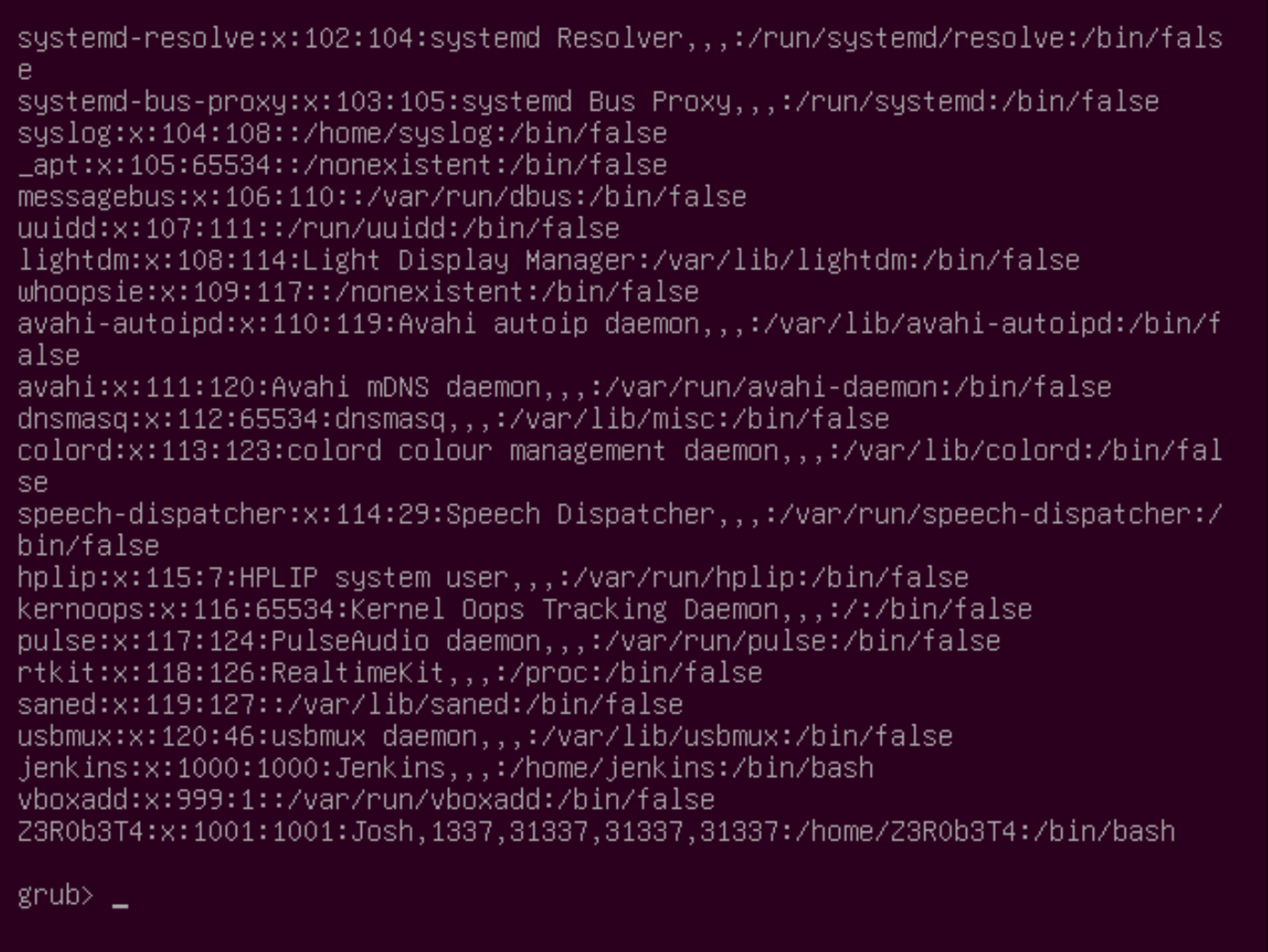
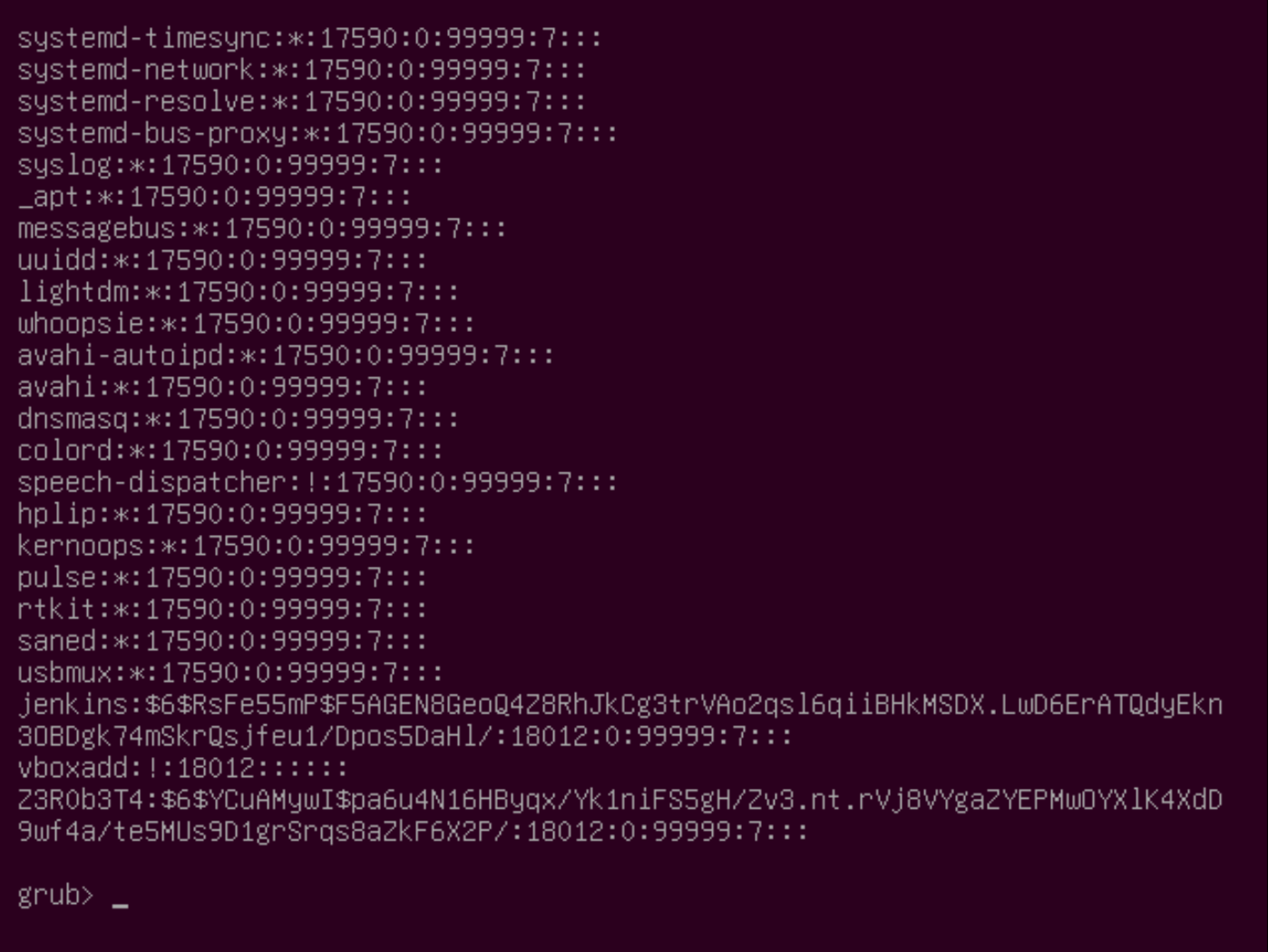
Now. let’s try if I can access the passwd file. This file holds every user account that exists in Ubuntu.
1
grub> cat /etc/passwd
Nice! We can access the file system. Let’s check if we also have access to the shadow file. This file holds all encrypted passwords of the user accounts.
1
grub> cat /etc/shadow
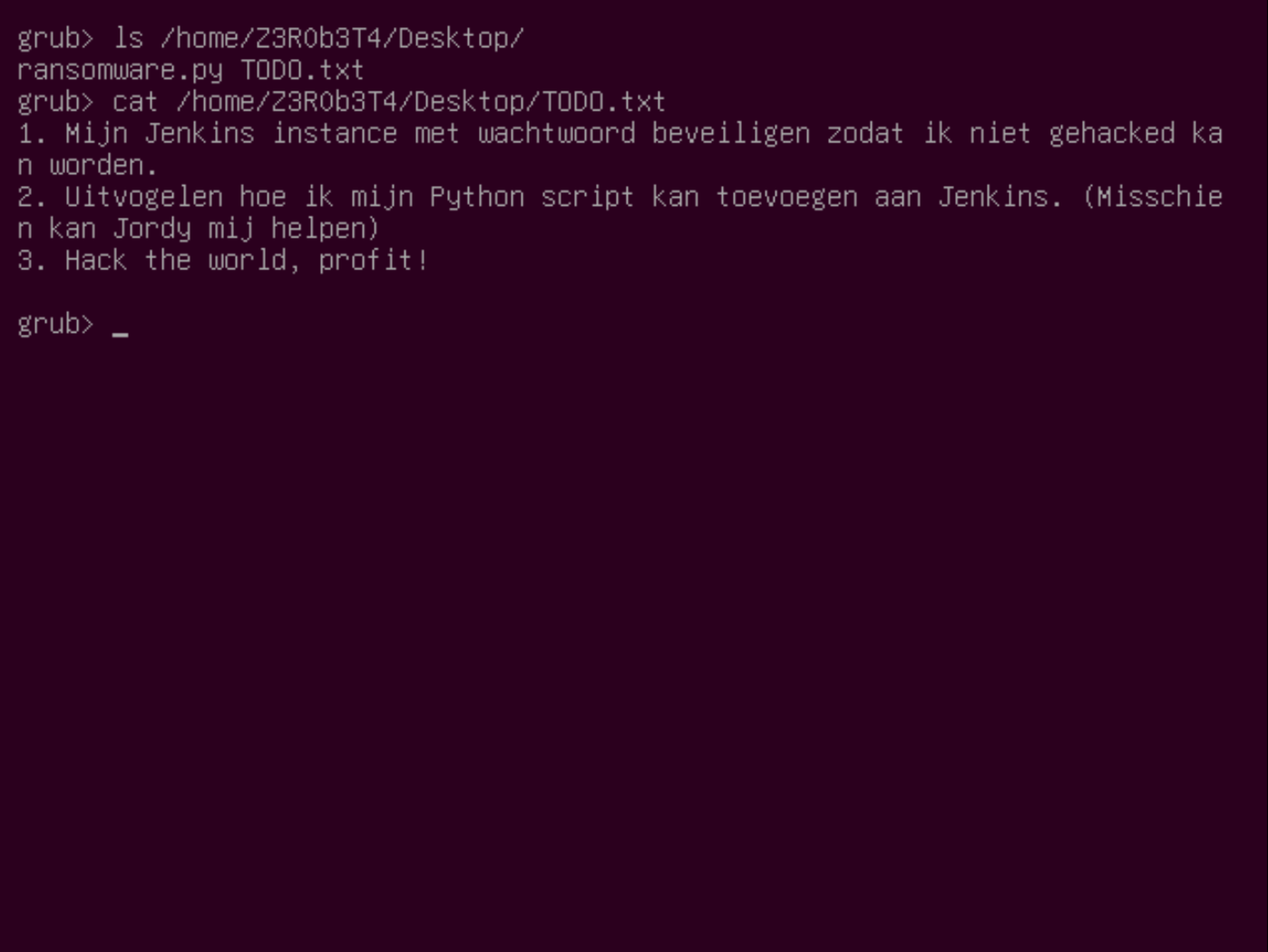
We can start enumerating the user accounts. After checking the folders in the /home/ directory, we can find the user profile of the user Z3R0b3T4. On the Desktop, there are two interesting files.
1
2
grub> ls /home/Z3R0b3T4/Desktop
grub> cat /home/Z3R0b3T4/Desktop/TODO.txt
1
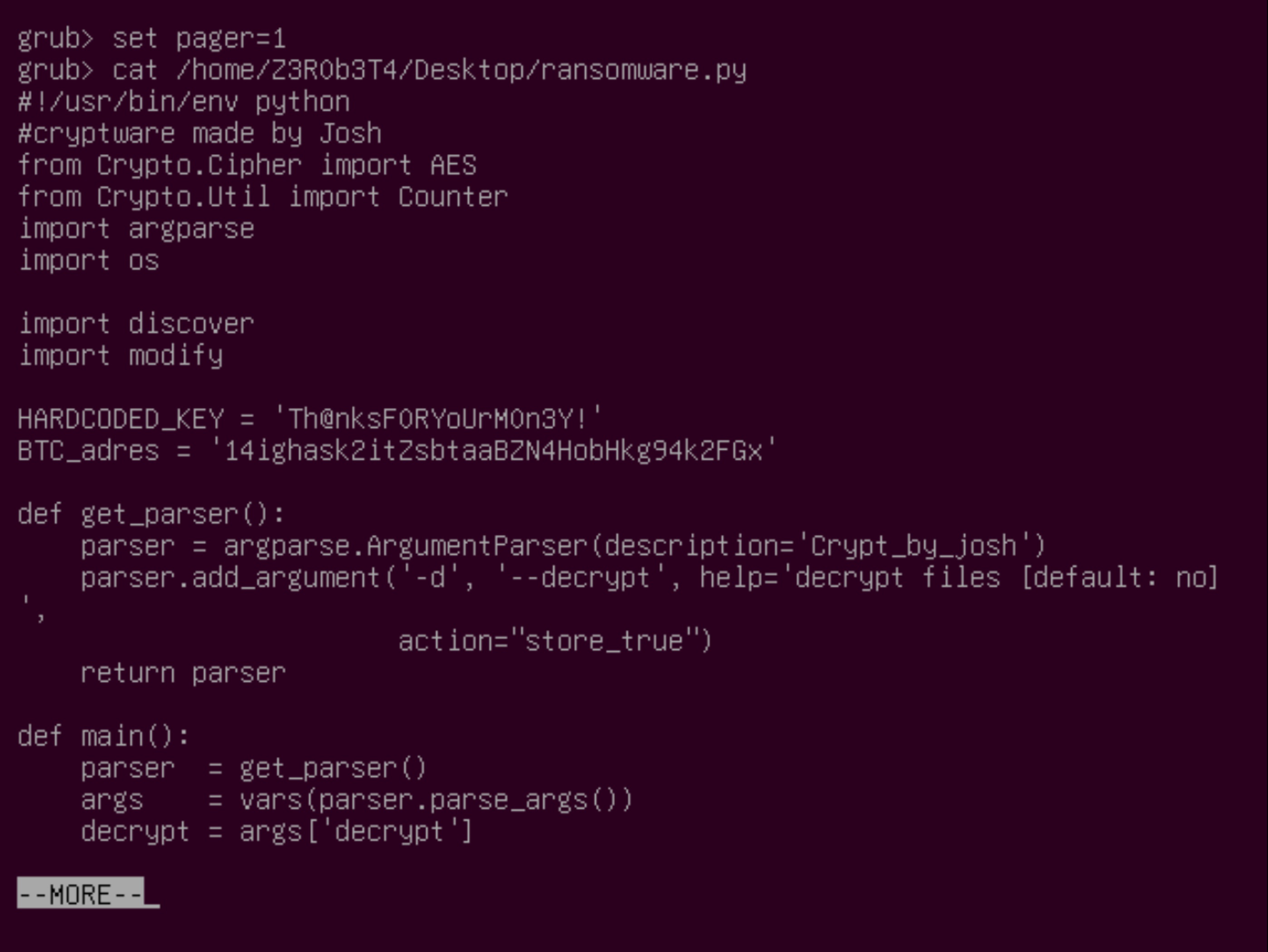
grub> cat /home/Z3R0b3T4/Desktop/ransomware.py
We have found the bitcoin address: 14ighask2itZsbtaaBZN4HobHkg94k2FGx
The flag: 14ighask2itZsbtaaBZN4HobHkg94k2FGx