To fast rollover the Kerberos decryption key(s), you can use this Powershell script: https://github.com/T13nn3s/microsoft/blob/main/security/SSOSeamlessKeyRollover.ps1.
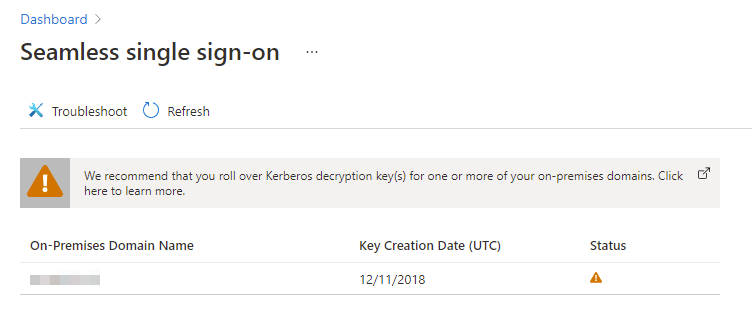
In this article, we do a quick talk about Seamless single sign-on in the Azure Active Directory. The Azure AD provides SSO to users with passthrough authentication. The user experience is most optimal on Windows 10 devices, it’s not required that these Windows 10 devices are joined to the Azure AD. The warning points to this article from Microsoft.
It is important to frequently roll over the Kerberos decryption key of the AZUREADSSO computer account. This computer account is representing the Azure AD which is created in your on-premises AD forest. Microsoft recommends that the Kerberos decryption key is being enrolled every 30 days.
⚠ Unfortunately: It is not yet possible to automate this process. Microsoft is currently working on a solution to automatically refresh Kerberos decryption keys.
With the following steps you can roll the Kerberos decryption keys:
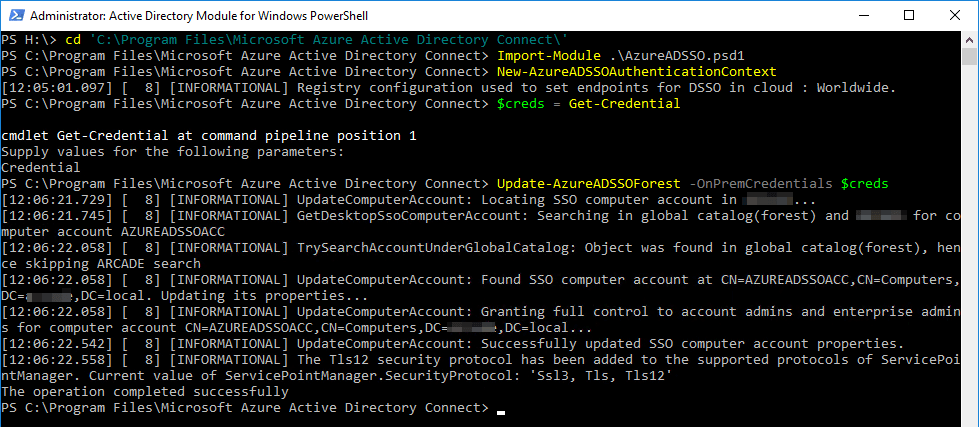
First, make sure that you have installed the Azure AD PowerShell cmdlet.
- On your on-premise AD open Windows PowerShell;
- Navigate to the
$env:programfiles\Microsoft Azure Active Directory Connectfolder; - Import the Seamless SSO PowerShell module using this command:
Import-Module .\AzureADSSO.psd1; - Run PowerShell as an Administrator. In PowerShell, call
New-AzureADSSOAuthenticationContext. This command should give you a popup to enter your tenant’s Global Administrator credentials; - Call
Get-AzureADSSOStatus | ConvertFrom-Json. This command provides you the list of AD forests (look at the “Domains” list) on which this feature has been enabled.
Now you know on wich forests ou need to roll the Kerberos decryption keys. In my environment, I have only one forest.
- Now you can call the
$creds = Get-Credentialand fill in the on-premise administrator account credentials. - Last but not least with this commando
Update-AzureADSSOForest -OnPremCredentials $credyou can roll the Kerberos decryption keys.
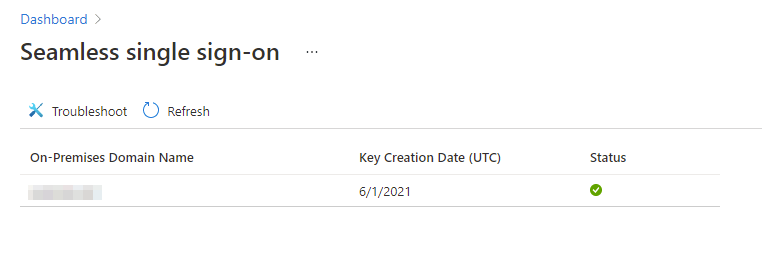
To check if the Kerberos key is changed successfully, you can check the EventID 4724 (attempt to change the account’s password) and EventID 4742 for the actual password change for the AZUREADSSOACC computer’s account. It can take a few minutes, but then you can see in the Azure AD Portal that the Kerberos keys are rolled.
Do you have any questions, please let me know! Have a secure day!