Hi everyone!
Greetings and welcome to my first bug bounty write-up. I’ve entered bug bounties in November 2020. This bug was an unauthenticated Kibana server exposed to the internet. Kibana is an open-source data visualization dashboard for Elasticsearch. It providers visualization capabilities on top of the content indexed on an Elasticsearch cluster.
I was excited that I’ve found my first bug. I know, this bog is not a technical feat, but it gives me the confidence to continue to search for bugs in (web) applications and in the networks of organizations that are exposed on the internet. Without further reduce let’s jump into this write-up. For this write-up, we call the target redacted.com.
Enumeration
I started with the basic enumeration; looking for subdomains and services running behind those subdomains and IP-addresses. Along the way, I found an IP-address connected to the target. Let’s say, it’s the IP-address: 10.11.12.13. I initiated a port scan with Nmap, I discovered an open port 5601/tcp.
Unauthenticated Kibana
I was still looking at my Nmap scan output and decided to send a curl request to this port and find out whats’s happening.
1
2
3
4
5
6
7
8
9
10
~$ curl 10.11.12.13:5601
<script>var hashRoute = '/app/kibana';
var defaultRoute = '/app/kibana';
var hash = window.location.hash;
if (hash.length) {
window.location = hashRoute + hash;
} else {
window.location = defaultRoute;
} </script>
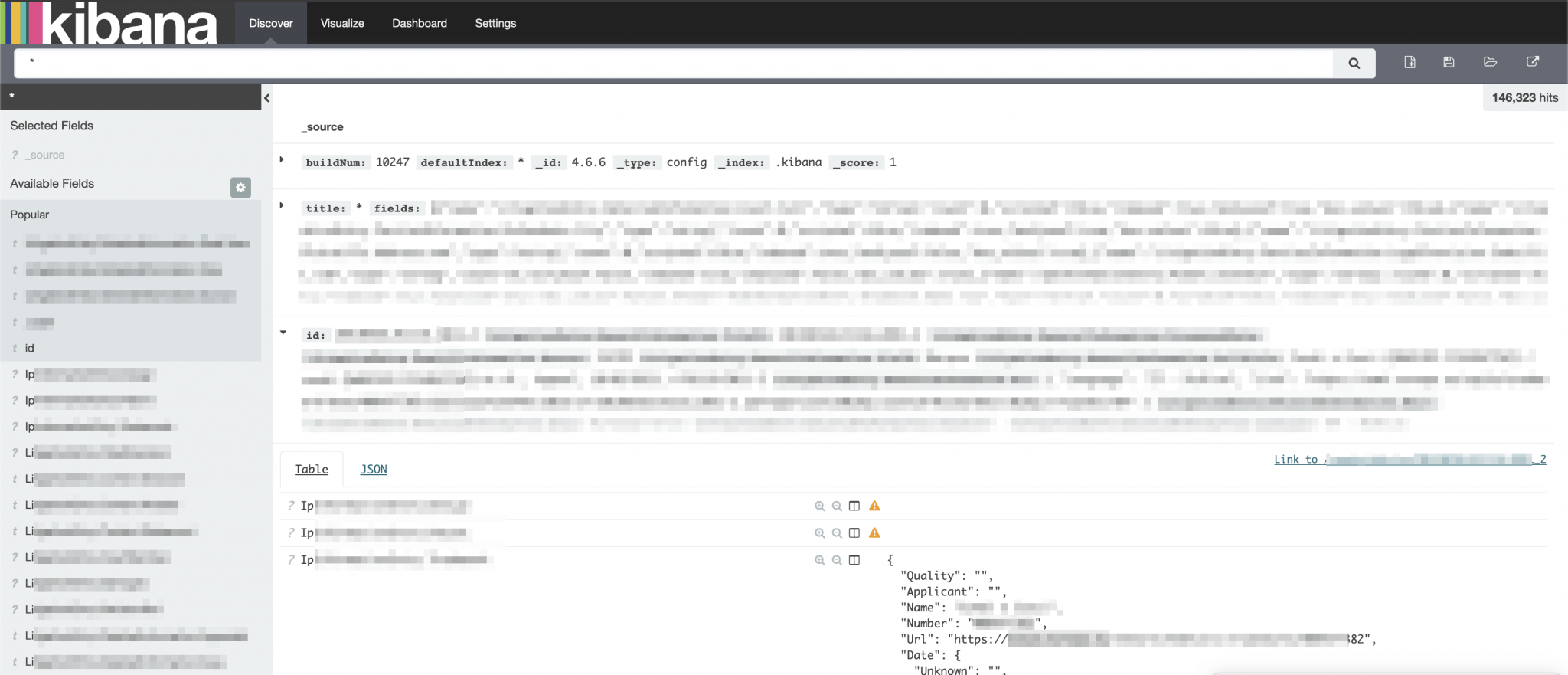
So, there is a Kibana server running behind this port. Through the internet browser I tried to access this port, and actually got redirected to a Kibana server, without the need for any authentication. I noticed that there is an older version running of Kibana and that important information is visible. I also noticed that this Kibana is leaking private information…
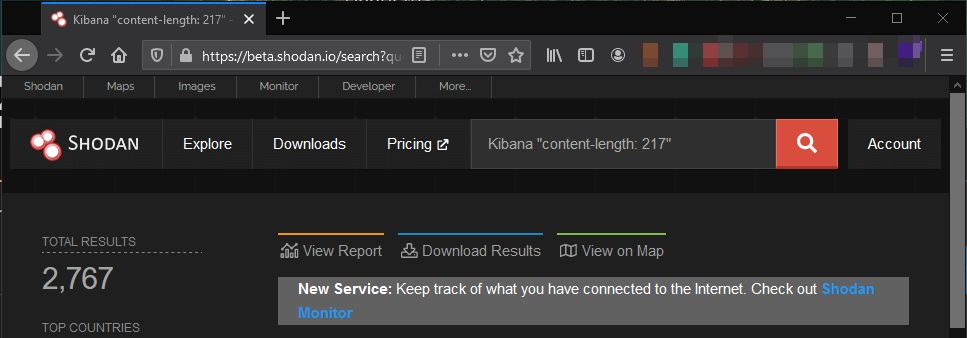
After further searching, I found that Kibana returns a content length of 217 when it’s publicly open without any authentication. This means, that with a rather simple query through Shodan, you can find more unauthenticated Kibana Servers exposed to the internet. At this moment there is at least 2,767 Kibana Lag server exposed to the internet without authentication. You can do this search query: Kibana "content-lenght: 217".
There is only one challenge. It’s impossible to identify the company to where this Kibana server belongs to because there is no company or something visible in the application. You can try to identify it through a certificate on port 443/tcp.
Back to our Kibana server. This Kibana was connected to an Elasticsearch database and through the log files I could filter out a hostname of the organization (redacted.com). So, I could link the IP address to my target, but now I also have confirmation from this IP address that it belongs to my target.
I reported this vulnerability to the security team. This target has a bug bounty program through HackerOne but pays no bounty. I have been added to the Hall of Fame of that company.
- 4 December 2020: Vulnerability reported
- 6 January 2021: Vulnerability confirmed by the security team
- 7 January 2021: Added to the Hall of Fame
- 2 February 2021: Vulnerability solved
Thanks for reading this write-up!