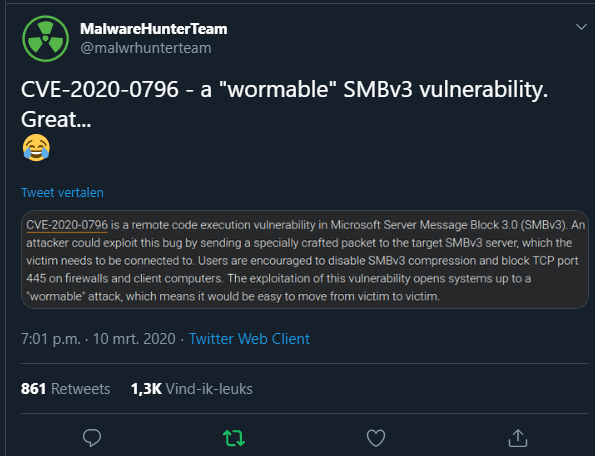
CVE-2020-0796 is a remote code execution vulnerability in SMBv3. An attacker could exploit this bug by sending a specially crafted package to the target SMBv3 server, which the victim needs to connect to. Users are encouraged to SMBv3 compression and block TCP port 445 on firewalls and client computers. The exploitation of this vulnerability opens systems up to a “wormable” attack, which means it would be easy to move from victim to victim.
I just want to share with you this article. In the evening on the 10th of March 2020, I saw in my twitter feed a message from MalwareHunterTeam about a “wormable” SMBv3 vulnerability.
After this announcement, Microsoft has released a security advisory for a Remote Code Execution vulnerability that has been found in the SMBv3 (SMBv3.1.1) protocol. By sending a specially crafted package to the target SMBv3 server, an attacker can exploit this Buffer Overflow Vulnerability, from the context of an application to execute random code on the server. More technical details have been disclosed, we have only some information which has been shared by the security company’s Cisco and Fortinet. It seems that this vulnerability was leaked accidentally.
According to some reports, this is a “worm” that could easily move from victim to victim as we have seen before with WannaCry and NotPetya. Unlike WannaCry and NotPetya, CVE-2020-0796 is limited to SMBv3 and has no effect on Windows Server 2008 R2 and Windows 7 systems.
Affected Products
According to Microsoft, this vulnerability exists in a newly added feature to Windows 10 version 1903. Older versions of Windows do not support SMBv3.1.1 compression.
| Product | Impact | Severity |
| Windows 10 Version 1903 for 32-bit Systems | Remote Code Execution | Critical |
| Windows 10 Version 1903 for ARM64-based Systems | Remote Code Execution | Critical |
| Windows 10 Version 1903 for x64-based Systems | Remote Code Execution | Critical |
| Windows 10 Version 1909 for 32-bit Systems | Remote Code Execution | Critical |
| Windows 10 Version 1909 for ARM64-based Systems | Remote Code Execution | Critical |
| Windows 10 Version 1909 for x64-based Systems | Remote Code Execution | Critical |
| Windows Server, version 1903 (Server Core installation) | Remote Code Execution | Critical |
| Windows Server, version 1909 (Server Core installation) | Remote Code Execution | Critical |
Proof Of Concept (POC)
There is also not a Proof Of Concept published yet. SophosLabs has developed a proof-of-concept exploit for the scenario that the attacker is already inside the network. SophosLabs has released a video demonstrating the exploit for this scenario.
Mitigations
Microsoft has not identified any mitigation for this vulnerability. On 12 march Microsoft has released the update KB4551762. This update would solve the vulnerability in SMBv3.
Workaround
Microsoft has released a workaround for CVE-2020-0796. The workaround is to disable SMBv3 compression to block unauthenticated attackers from exploiting the vulnerability against an SMBv3 server. I have written a Powershell script that can be used for this workaround. I have published this script on Github: https://github.com/T13nn3s/CVE-2020-0976.
Scan HOST/CIDR with nmap script
nikallass has placed a script on Github which can determine if the target has the vulnerable SMB version and whether compression is enabled or not by using Nmap. Repository on Github: https://gist.github.com/nikallass/40f3215e6294e94cde78ca60dbe07394.
CVE-2020-0976 vulnerability checker
dickens88 has released a Python script on Github which can determine if the target is been vulnerable for CVE-2020-0976. Repository on Github: https://github.com/dickens88/cve-2020-0796-scanner/.
Microsoft patched CVE-2020-0976 (KB4551762)
On 12 March Microsoft has released out of band updates to fix the SMBv3 vulnerability. The update is available through the Windows Update or through direct download: https://www.catalog.update.microsoft.com/Search.aspx?q=KB4551762.
Timeline
March 10, 2020
- Vulnerability got leaked
- Fortinet Threat Lookup => CVE-2020-0796 is added to the Threath Lookup from FortiGuard Labs.
March 11, 2020
- Microsoft Security Advisory => Microsoft has released the ADV200005.
- T13nn3s created workaround script. According to ADV200005, T13nn3s has build and uploaded a Powershell Script with the workaround to Github.
- nikallass released SMBv3.1.1 CVE-2020-0796 checker. The bash script checks if target has SMBv3.1.1 with compression. This script is using
nmapto perform the check. - Dickens88 released a CVE-2020-0976 vulnerability scanner => Python script which determines if the target host is vulnerable for CVE-2020-0976.
March 12, 2020
- Microsoft has released out of band update KB4551762 and is available through Windows Update or through direct download.
- SophosLabs has developed a POC. SophosLabs’ Offensive Research has developed a proof-of-concept exploit for the ‘attacker already inside’ scenario.
- T13nn3s updated workaround script. Script now also checking whether the required Windows Update is installed or not.
Microsoft has patched this vulnerability, any other details regarding this vulnerability are not yet revealed, so there is still no test if the vulnerability is fixed by installing the KB4551762 update. As long as the exploit is not publicly available, I do not expect active attacks and abuse of this vulnerability.
References
- MalwareHunterTeam @Twitter: https://mobile.twitter.com/malwrhunterteam/status/1237438376032251904?s=09
- Microsoft Security Advisory: https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/adv200005
- Fortinet: https://fortiguard.com/encyclopedia/ips/48773
- Workaround: https://github.com/T13nn3s/CVE-2020-0976
- Microsoft CVE-2020-0976 patch: https://www.catalog.update.microsoft.com/Search.aspx?q=KB4551762
- SophosLabs: https://news.sophos.com/en-us/2020/03/12/patch-tuesday-for-march-2020-fixes-the-serious-smb-bug-cve-2020-0796/