Overview
The NOVI University Of Applied Sciences is offering an Advent CTF challenge for December 2020. The CTF is created by our community member of the Hackdewereld.nl and Chief Lecturer for Cyber Security at the NOVI University, Arjen Wiersma. If you want to participate in these CTF challenges, you can create an account on the website https://www.adventofctf.com/.
Challenge 7
- Description: Santa has a naughty list, I wonder who is on it? I hope it is not the blind mice!
- 700 points
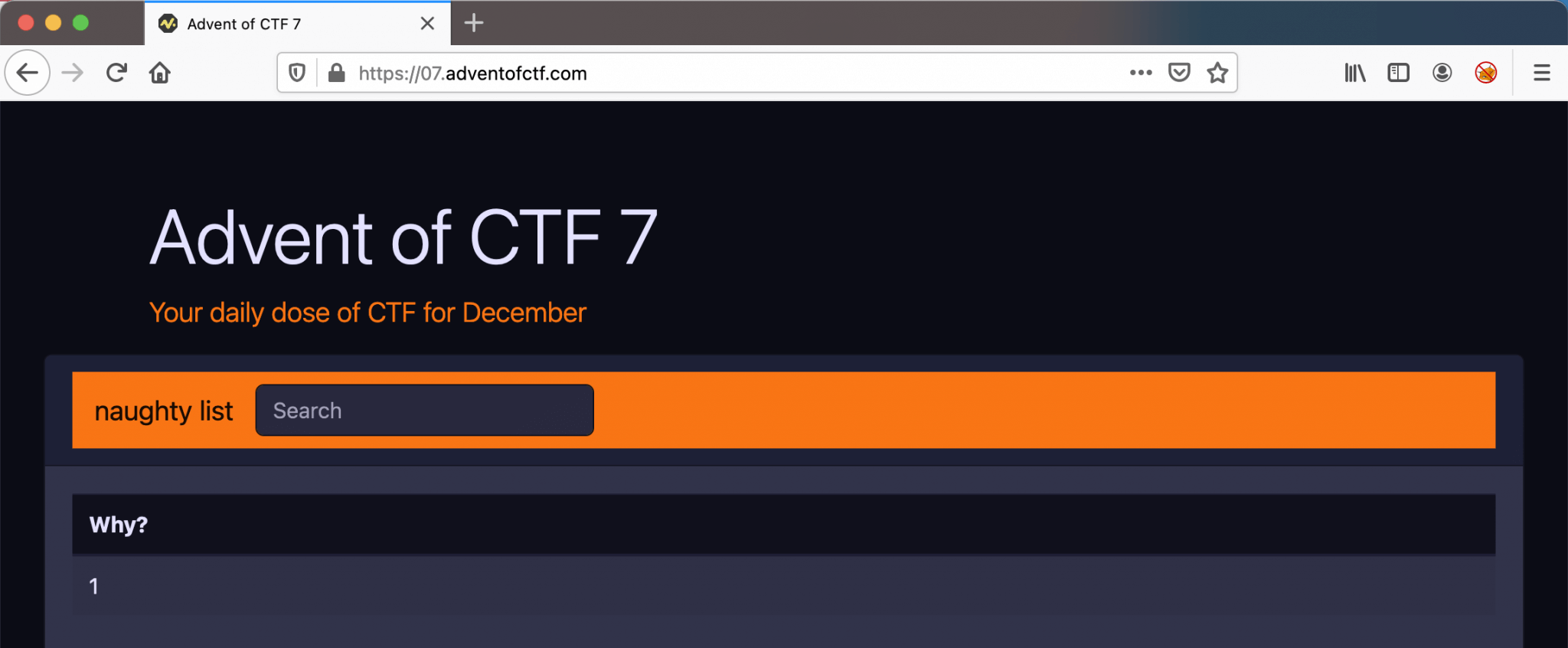
Let’s start the challenge! After visiting the challenge URL https://07.adventofctf.com/, I’m landing on this page below. There is only a search bar visible.
Let’s start by putting in a single quote ' in the search field. But got no luck, no SQL error is popping up. The next step to test if this search bar is vulnerable to Blind SQL Injection. Unlike the ‘normal’ SQL Injection, Blind SQL injection leaves no error messages. To test if this search bar is vulnerable is looking at how the page behaves according to the statements are being given to the search bar. If we give a True (Ex. 1=1) statement it gives me a valid page and when a False (Ex. 1=2) statement is being given, it shows an invalid page. And by an invalid page, we mean that something is different on the page, a page which something we do not expect.
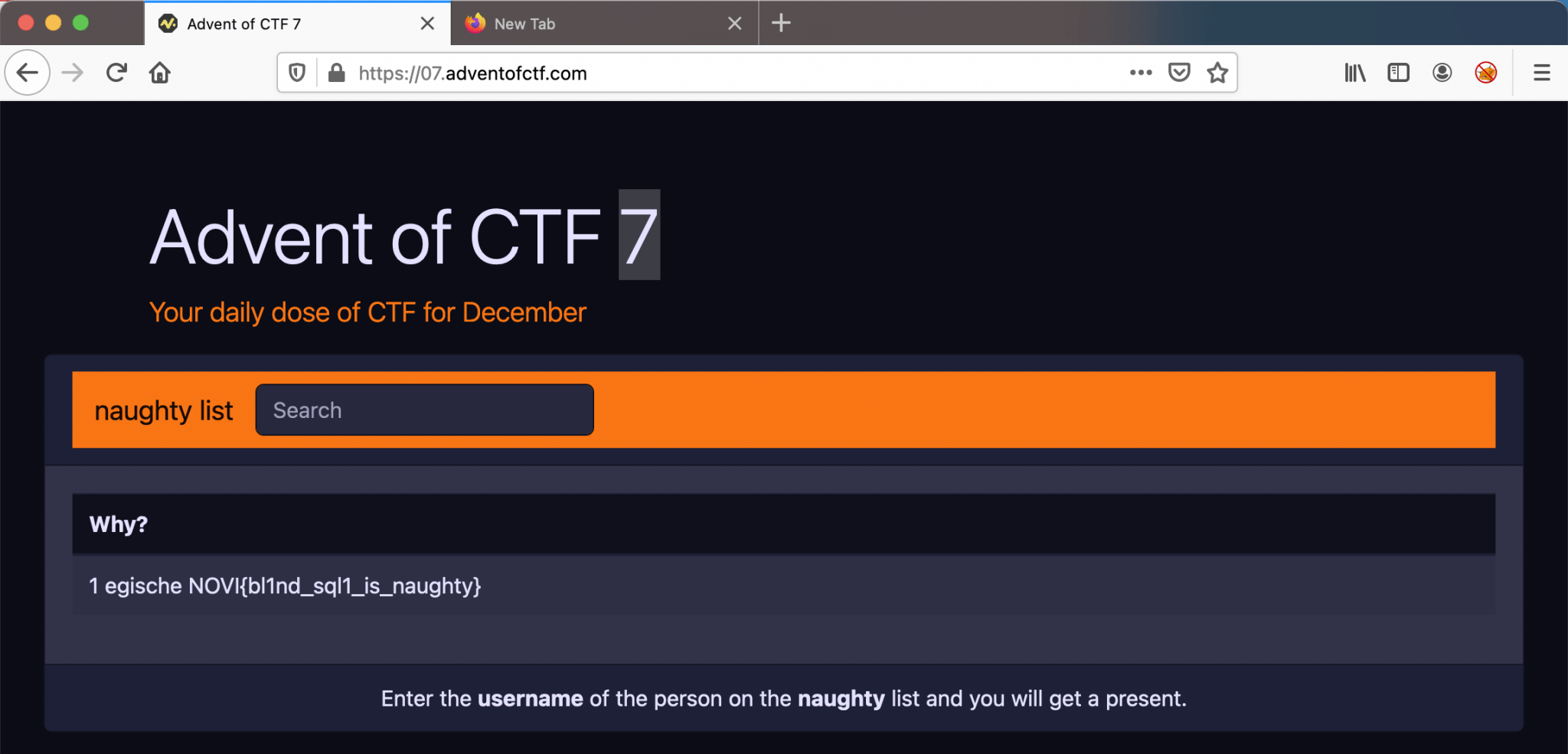
So, I start by sending a username' or'1'='1, and got directly the flag! This was totally not expected. The flag: NOVI{bl1nd_sql1_is_naughty}.
This was very easy. Was this intended? I don’t think so. The CTF creator had created an another additional challenge.
(Additional) Challenge 7
- Challenge 7 had a very unintended easy solution. This was my mistake and it did not surface during playtesting. In order to make it worth your while to solve the challenge in the intended way, please enter the username of the user on the naughty list to receive some additional (possibly very important) points.
- 250 points.
It’s the same website. We have already found the vulnerability. Let’s take this a step further and try to get the naughty username. First, we enumerate the number of columns with this SQL Injection 1' union select 1-- , according to the output, this statement is true.
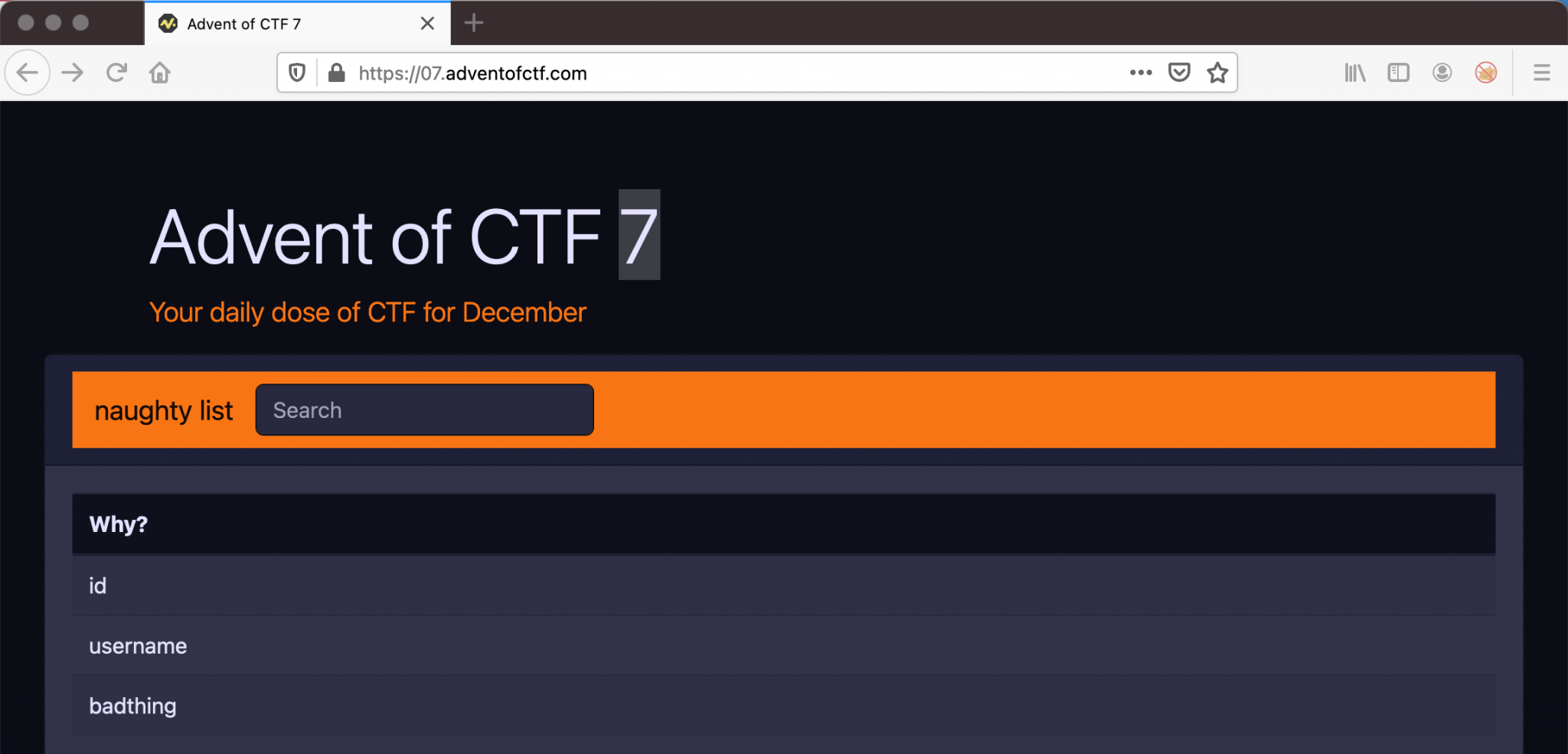
The next step is to enumerate the names of the tables. I came up with this SQL Injection 1' union select table_name from information_schema.tables-- .
The table naughty got three columns with the names id, username, and badthing. We can now build our last query to retrieve the information from this table. ' UNION SELECT group_concat(id,char(32),username,char(32),badthing) from naughty-- .
Thanks for reading!